0x01 Metasploit5主要更新功能
- 支持Python、Ruby、Go模块开发;
- 提升search命令搜索速度,基本秒出;
新增handler命令,快速生成一个监听;
handler -H 192.168.1.120 -P 443 -p windows/x64/meterpreter/reverse_tcp
新增两个免杀模块,据说效果不是很好;
evasion/windows/windows_defender_exeevasion/windows/windows_defender_js_hta
合并rhost、rhosts参数,都用rhosts;
指定单IP:set rhosts 192.168.1.100指定多IP:set rhosts 192.168.1.102,192.168.1.104指定IP段:set rhosts 192.168.1.100-120(192.168.1.100-192.168.1.120,192.168.1.0/24)指定IP文件:set rhosts file://root/ip.txt搜索PostgreSQL数据库中的主机IP:hosts -R
0x02 Metasploit更新到v5.0.9-dev
不知道Metasploit从哪个版本开始已经不再支持使用msfupdate命令更新了,请使用以下命令再次进行重新安装最新版本,如图2-2-1。
root@kali:~# vi /etc/apt/sources.listdeb https://mirrors.ustc.edu.cn/kali kali-rolling main non-free contribdeb-src https://mirrors.ustc.edu.cn/kali kali-rolling main non-free contribroot@kali:~# apt update && apt -y full-upgrade && apt-get install metasploit-framework
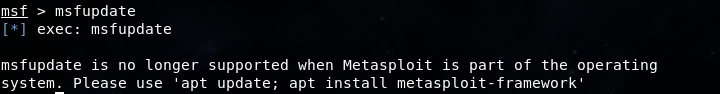
图2-2-1 不再支持msfupdate命令更新
0x03 msfconsole启动报错以及原因
使用msfconsole命令启动时出现了以下报错,这里好像是加载的模块文件名必须为小写,如图2-2-2。
root@kali:~# msfconsoleTraceback (most recent call last):ork console.../30: from /usr/bin/msfconsole:49:in `<main>'29: from /usr/share/metasploit-framework/lib/metasploit/framework/command/base.rb:82:in `start'28: from /usr/share/metasploit-framework/lib/metasploit/framework/command/console.rb:48:in `start'27: from /usr/share/metasploit-framework/lib/metasploit/framework/command/console.rb:62:in `driver'26: from /usr/share/metasploit-framework/lib/metasploit/framework/command/console.rb:62:in `new'25: from /usr/share/metasploit-framework/lib/msf/ui/console/driver.rb:161:in `initialize'24: from /usr/share/metasploit-framework/lib/msf/base/simple/framework/module_paths.rb:49:in `init_module_paths'23: from /usr/share/metasploit-framework/lib/msf/base/simple/framework/module_paths.rb:49:in `each'22: from /usr/share/metasploit-framework/lib/msf/base/simple/framework/module_paths.rb:50:in `block in init_module_paths'21: from /usr/share/metasploit-framework/lib/msf/core/module_manager/module_paths.rb:40:in `add_module_path'20: from /usr/share/metasploit-framework/lib/msf/core/module_manager/module_paths.rb:40:in `each'19: from /usr/share/metasploit-framework/lib/msf/core/module_manager/module_paths.rb:41:in `block in add_module_path'18: from /usr/share/metasploit-framework/lib/msf/core/module_manager/loading.rb:117:in `load_modules'17: from /usr/share/metasploit-framework/lib/msf/core/module_manager/loading.rb:117:in `each'16: from /usr/share/metasploit-framework/lib/msf/core/module_manager/loading.rb:119:in `block in load_modules'15: from /usr/share/metasploit-framework/lib/msf/core/modules/loader/base.rb:238:in `load_modules'14: from /usr/share/metasploit-framework/lib/msf/core/modules/loader/directory.rb:30:in `each_module_reference_name'13: from /usr/share/metasploit-framework/lib/msf/core/modules/loader/directory.rb:30:in `foreach'12: from /usr/share/metasploit-framework/lib/msf/core/modules/loader/directory.rb:40:in `block in each_module_reference_name'11: from /usr/share/metasploit-framework/vendor/bundle/ruby/2.5.0/gems/rex-core-0.1.13/lib/rex/file.rb:132:in `find'10: from /usr/share/metasploit-framework/vendor/bundle/ruby/2.5.0/gems/rex-core-0.1.13/lib/rex/file.rb:132:in `catch'9: from /usr/share/metasploit-framework/vendor/bundle/ruby/2.5.0/gems/rex-core-0.1.13/lib/rex/file.rb:133:in `block in find'8: from /usr/share/metasploit-framework/lib/msf/core/modules/loader/directory.rb:49:in `block (2 levels) in each_module_reference_name'7: from /usr/share/metasploit-framework/lib/msf/core/modules/loader/base.rb:239:in `block in load_modules'6: from /usr/share/metasploit-framework/lib/msf/core/modules/loader/base.rb:177:in `load_module'5: from /usr/share/metasploit-framework/lib/msf/core/modules/loader/base.rb:543:in `namespace_module_transaction'4: from /usr/share/metasploit-framework/lib/msf/core/modules/loader/base.rb:365:in `current_module'3: from /usr/share/metasploit-framework/lib/msf/core/modules/loader/base.rb:365:in `reduce'2: from /usr/share/metasploit-framework/lib/msf/core/modules/loader/base.rb:365:in `each'1: from /usr/share/metasploit-framework/lib/msf/core/modules/loader/base.rb:370:in `block in current_module'/usr/share/metasploit-framework/lib/msf/core/modules/loader/base.rb:380:in `rescue in block in current_module': exploit/windows/fileformat/cve-2018-8174 must be lowercase alphanumeric snake case (Msf::ModuleLoadError)
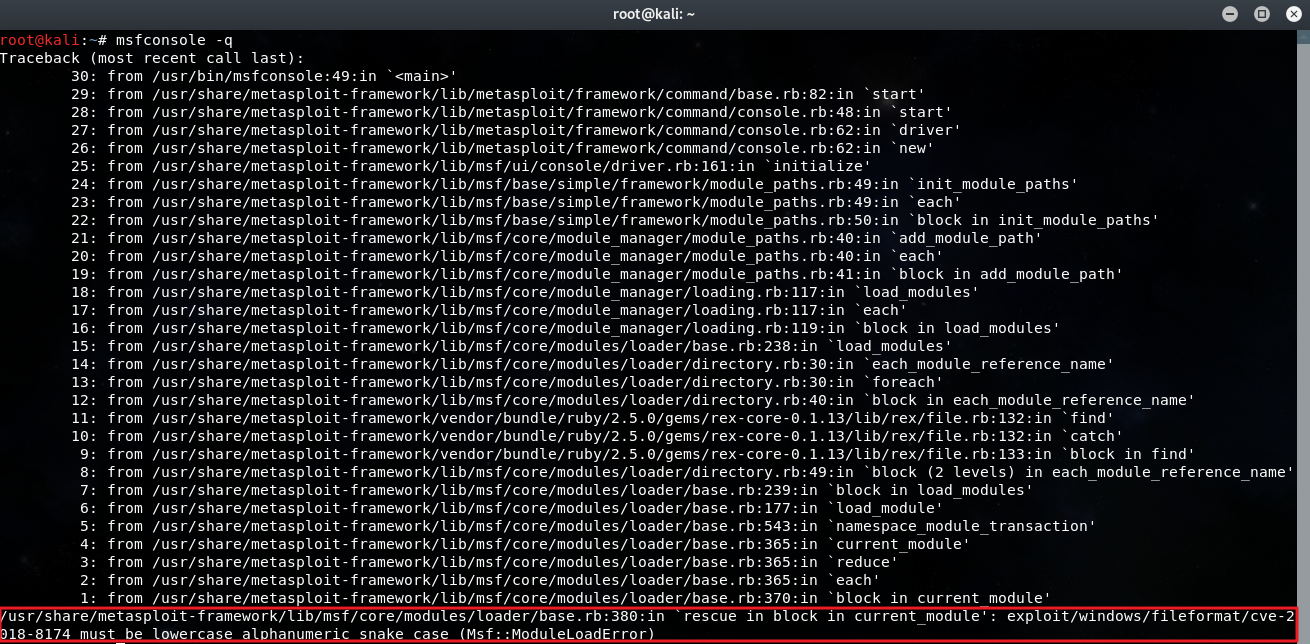
图2-2-2 msfconsole -q命令启动报错
根据上图报错信息的最后一行可以看出问题出在exploit/windows/fileformat/cve-2018-8174这个漏洞利用模块,具体原因可以看/usr/share/metasploit-framework/lib/msf/core/modules/loader/base.rb报错文件中的360-382行。
360 # @param [Array<String>] module_names a list of module names to resolve from Object downward.361 # @return [Module] module that wraps the previously loaded content from {#read_module_content}.362 # @return [nil] if any module name along the chain does not exist.363 def current_module(module_names)364 # Don't want to trigger ActiveSupport's const_missing, so can't use constantize.365 named_module = module_names.reduce(Object) do |parent, module_name|366 # Since we're searching parent namespaces first anyway, this is367 # semantically equivalent to providing false for the 1.9-only368 # "inherit" parameter to const_defined?. If we ever drop 1.8369 # support, we can save a few cycles here by adding it back.370 begin371 if parent.const_defined?(module_name)372 parent.const_get(module_name)373 else374 break375 end376 # HACK: This doesn't slow load time as much as checking proactively377 rescue NameError378 reversed_name = self.class.reverse_relative_name(module_name)379 # TODO: Consolidate this with Msftidy#check_snake_case_filename ?380 raise Msf::ModuleLoadError, "#{reversed_name} must be lowercase alphanumeric snake case"381 end382 end
0x04 Metasploit更新报错解决方案
msfconsole启动报错是因为我原来在MSF4测试的CVE-2018-8174.rb模块的文件名为大写,MSF5模块命名必须为小写,记得MSF4好像是没有模块命名大小写限制的。知道报错原因后就好解决了,只需将这个模块的文件名改为小写即可,如图2-2-3。
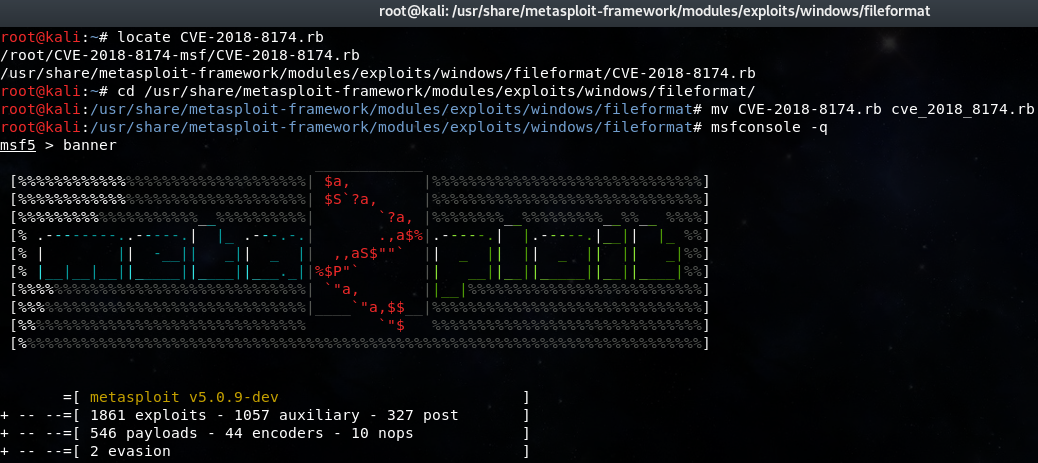
图2-2-3 成功解决Metasploit5更新报错


