准备
基本yum源
yum install -y epel-releaseyum install -y wget bash-com* gityum update -y
yum -y install gcc bc gcc-c++ ncurses ncurses-devel cmake elfutils-libelf-devel openssl-devel flex* bison* autoconf automake zlib* fiex* libxml* ncurses-devel libmcrypt* libtool-ltdl-devel* make cmake pcre pcre-devel openssl openssl-devel jemalloc-devel tlc libtool vim unzip wget lrzsz bash-comp* ipvsadm ipset jq sysstat conntrack libseccomp conntrack-tools socat curl wget git conntrack-tools psmisc nfs-utils tree bash-completion conntrack libseccomp net-tools crontabs sysstat iftop nload strace bind-utils tcpdump htop telnet lsof
关闭防火墙,swap,selinux
#关闭防火墙systemctl disable --now firewalld#关闭swapswapoff -ased -ri '/^[^#]*swap/s@^@#@' /etc/fstab#关闭selinuxsetenforce 0sed -ri '/^[^#]*SELINUX=/s#=.+$#=disabled#' /etc/selinux/config
安装wireguard
需要公网ip
node01,node02,node03安装wireguard
echo "net.ipv4.ip_forward = 1" >> /etc/sysctl.conf
echo "net.ipv4.conf.all.proxy_arp = 1" >> /etc/sysctl.conf
sysctl -p /etc/sysctl.conf
curl -Lo /etc/yum.repos.d/wireguard.repo https://copr.fedorainfracloud.org/coprs/jdoss/wireguard/repo/epel-7/jdoss-wireguard-epel-7.repo
yum install https://www.elrepo.org/elrepo-release-7.el7.elrepo.noarch.rpm -y
yum install kmod-wireguard wireguard-tools wireguard-dkms yum-plugin-elrepo -y
重启
reboot
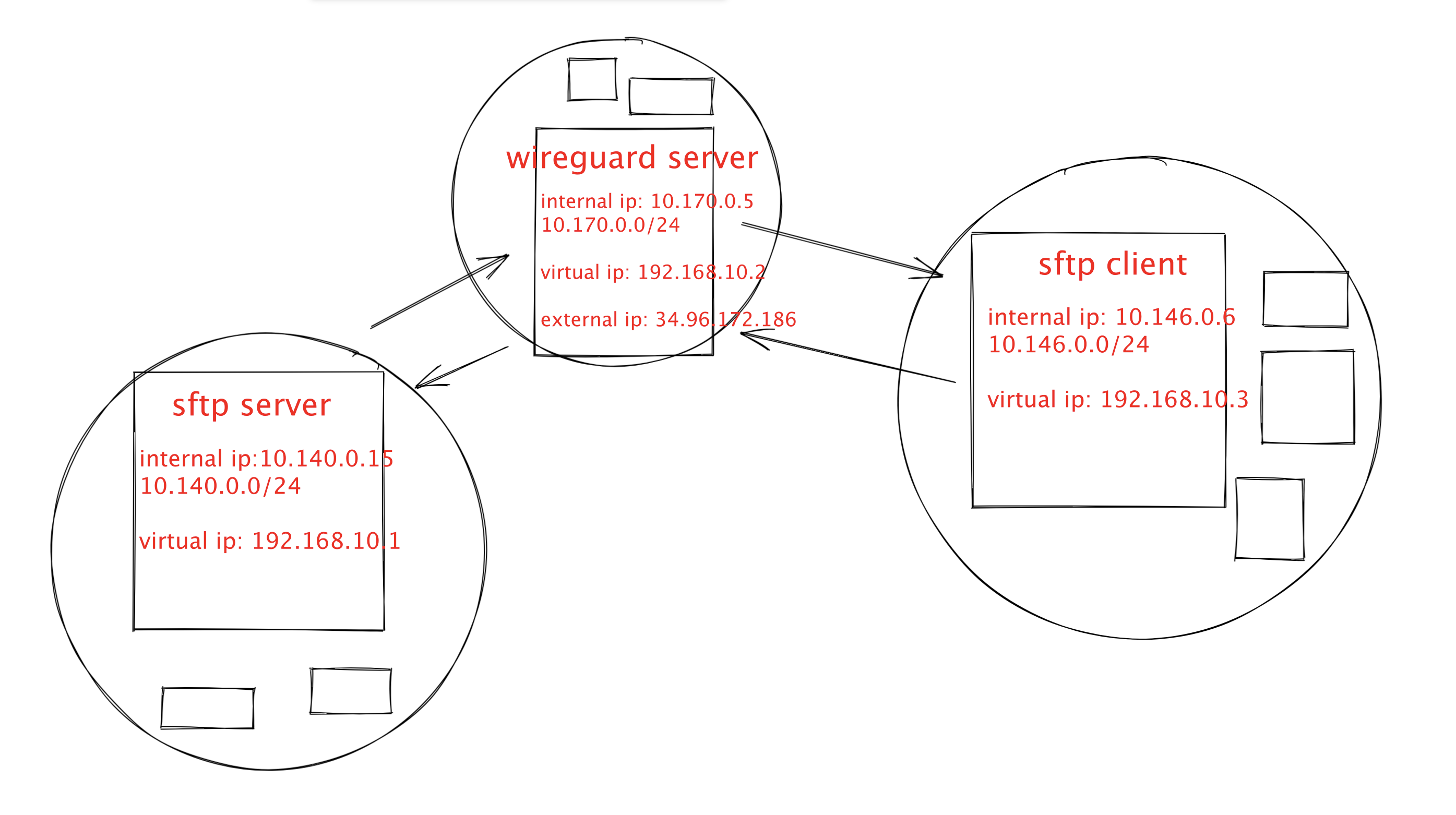
| host | app | 内网ip | 公网ip | vpc |
|---|---|---|---|---|
| node01 | sftpserver wireguard client | 10.140.0.15 | 无 | 10.140.0.0/24 |
| node02 | wireguard server | 10.170.0.5 | 34.96.172.186 | 10.170.0.0/24 |
| node03 | sftpclinet wireguard client | 10.146.0.6 | 无 | 10.146.0.0/24 |
获取私钥和公钥
wg genkey | tee server_private_key | wg pubkey > server_public_key
node01
vim /etc/wireguard/wg0.conf
[Interface]
PrivateKey=UAHNSPP9xAYH5GbxX+uMOieMxPjq8rGefxp8i1OJZmg=
Address=192.168.10.1/24
PostUp=iptables -A FORWARD -i %i -j ACCEPT; iptables -A FORWARD -o %i -j ACCEPT; iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
PostDown=iptables -D FORWARD -i %i -j ACCEPT; iptables -D FORWARD -o %i -j ACCEPT; iptables -t nat -D POSTROUTING -o eth0 -j MASQUERADE
[Peer]
PublicKey=gAYr+3DcM8oU3iLbIm65HzZZNIXZbfyHKK/yY2oDUSU=
AllowedIPs=192.168.10.0/24,10.140.0.0/24,10.170.0.0/24,10.146.0.0/24
Endpoint=34.96.172.186:10443
PersistentKeepalive=25
node02
vim /etc/wireguard/wg0.conf
[Interface]
Address=192.168.10.2/24
SaveConfig=true
PostUp=iptables -A FORWARD -i %i -j ACCEPT; iptables -A FORWARD -o %i -j ACCEPT; iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
PostDown=iptables -D FORWARD -i %i -j ACCEPT; iptables -D FORWARD -o %i -j ACCEPT; iptables -t nat -D POSTROUTING -o eth0 -j MASQUERADE
ListenPort=10443
PrivateKey=mMbrC5DiK7bqC3RpovBVbyIoPIwLJU4Xm/xF2ZgFG14=
[Peer]
PublicKey=RHofJanA1YBUxz/ZYvPwZ0brj9Vz39OyrGnx/ses2AY=
AllowedIPs=192.168.10.1/32,10.140.0.0/24
[Peer]
PublicKey=Ho6+QD/fqcGqvh6M8fZ7jE9qIUnlmNgLmrjiy8uOzCk=
AllowedIPs=192.168.10.3/32,10.146.0.0/24
node03
vim /etc/wireguard/wg0.conf
[Interface]
PrivateKey=KPoB09xEFR++okdJLNFi+BkoGsGcPzgSsPgqD9xStFY=
Address=192.168.10.3/24
PostUp=iptables -A FORWARD -i %i -j ACCEPT; iptables -A FORWARD -o %i -j ACCEPT; iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
PostDown=iptables -D FORWARD -i %i -j ACCEPT; iptables -D FORWARD -o %i -j ACCEPT; iptables -t nat -D POSTROUTING -o eth0 -j MASQUERADE
[Peer]
PublicKey=gAYr+3DcM8oU3iLbIm65HzZZNIXZbfyHKK/yY2oDUSU=
AllowedIPs=192.168.10.0/24,10.140.0.0/24,10.170.0.0/24,10.146.0.0/24
Endpoint=34.96.172.186:10443
PersistentKeepalive=25
启动wg
wg-quick up wg0
wg show
测试
node01 ping node02 node03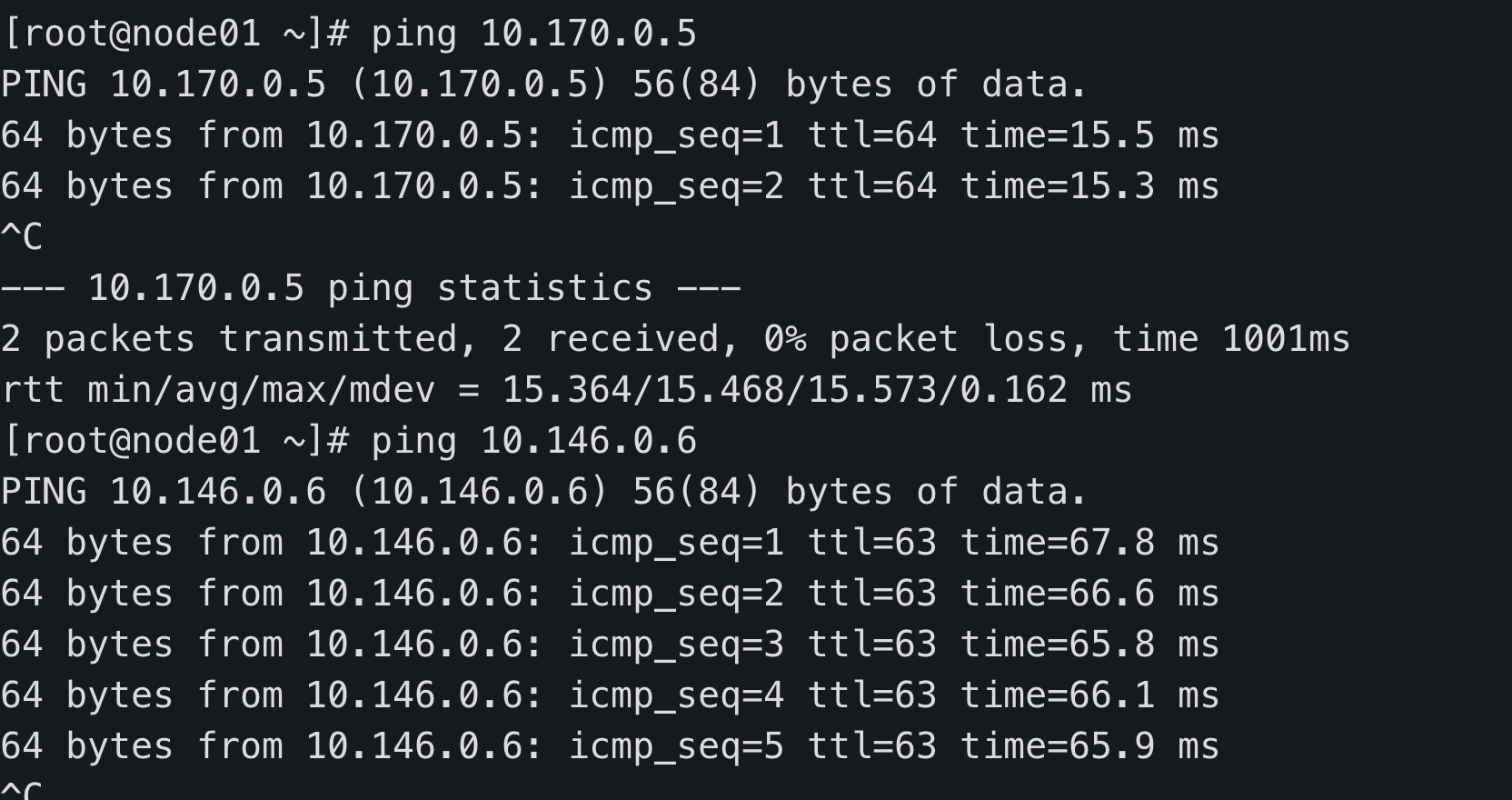
node02 ping node01 node03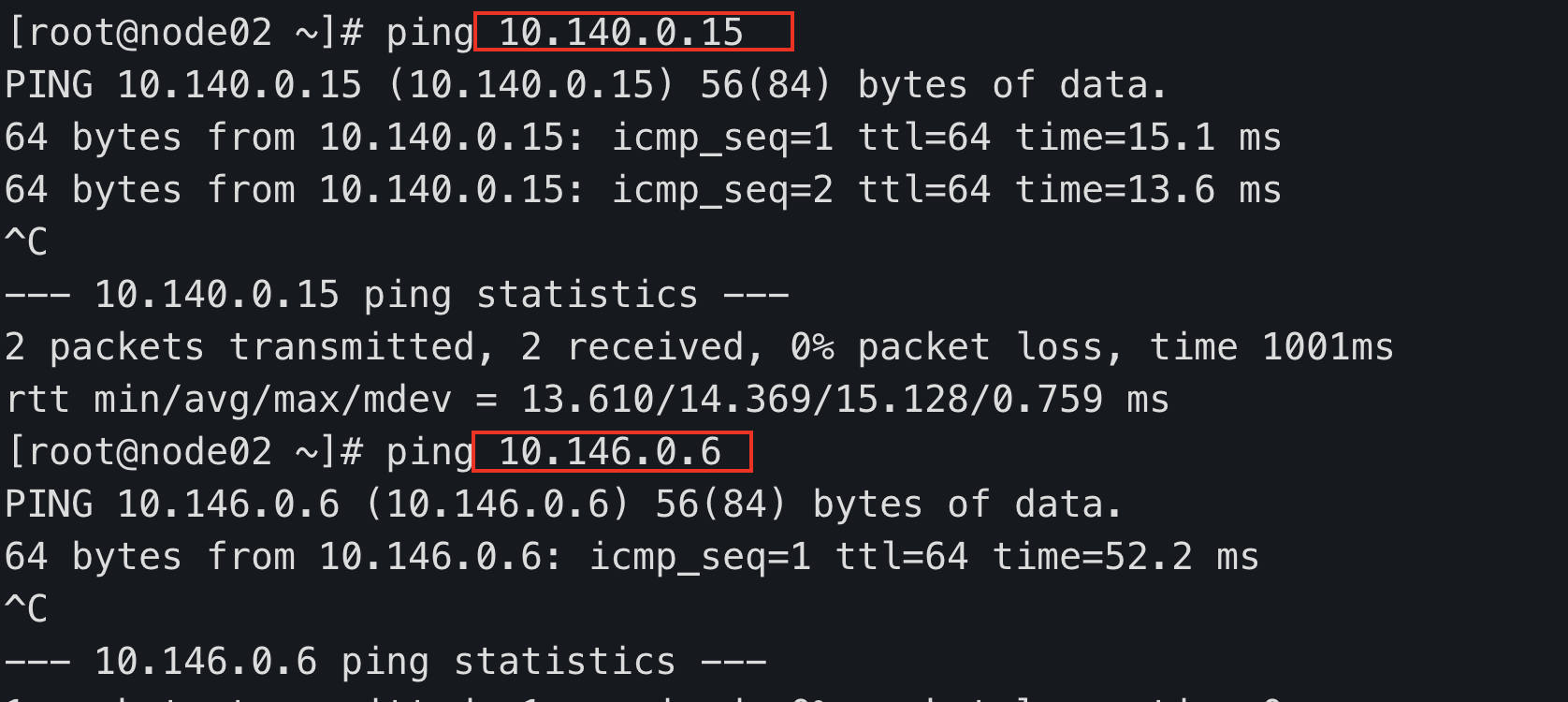
node03 ping node01 node02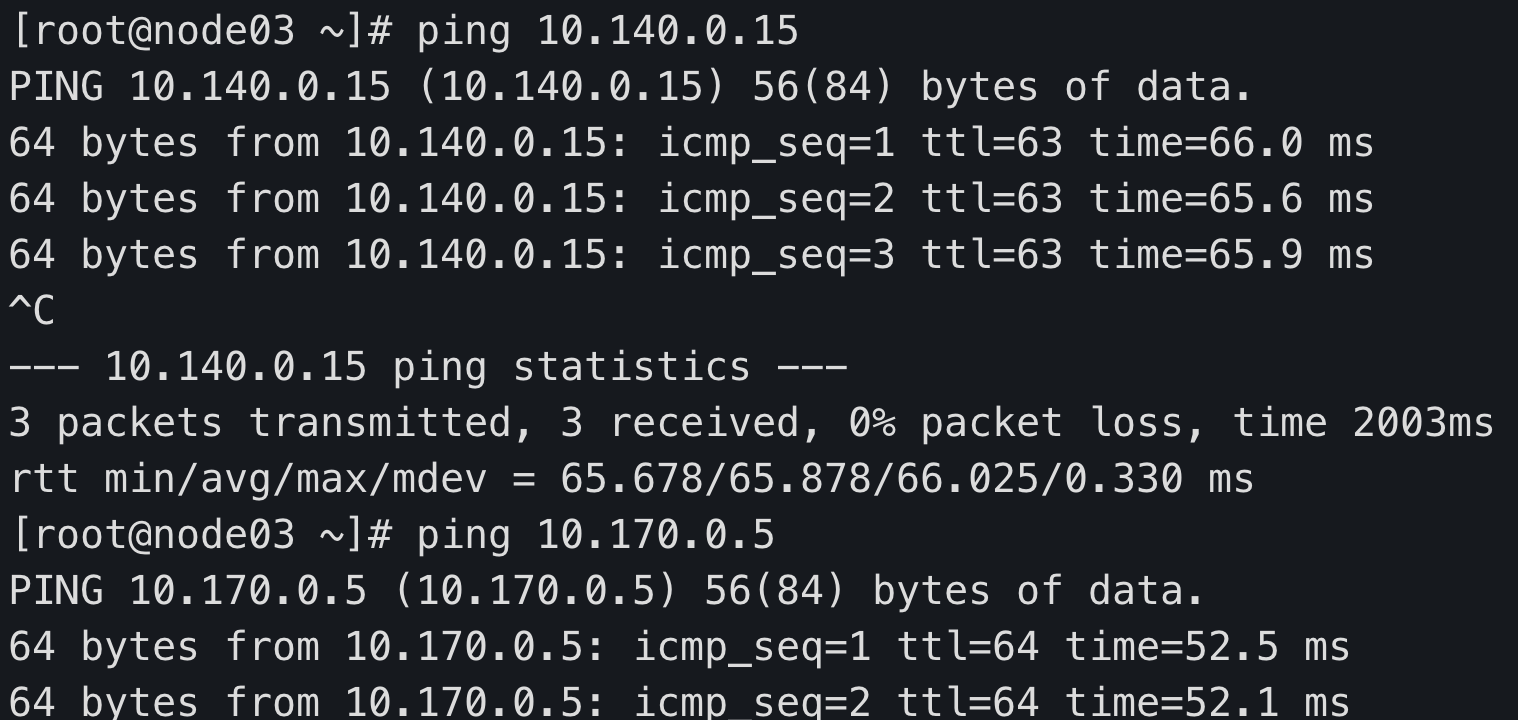
node01 install sftpsever
创建sftp的用户组
groupadd sftpgroup
创建sftp⽤户账号并指定用户组和拒绝⽤户登录
useradd -g sftpgroup -s /bin/flase sftpadmin
passwd sftpadmin
创建⼀个⽂件夹作为sftp账户的home⽬录
mkdir -p /data/sftp/sftpadmin
usermod -d /data/sftp/sftpadmin/ sftpadmin
修改linux服务器的sftp配置
vim /etc/ssh/sshd_config
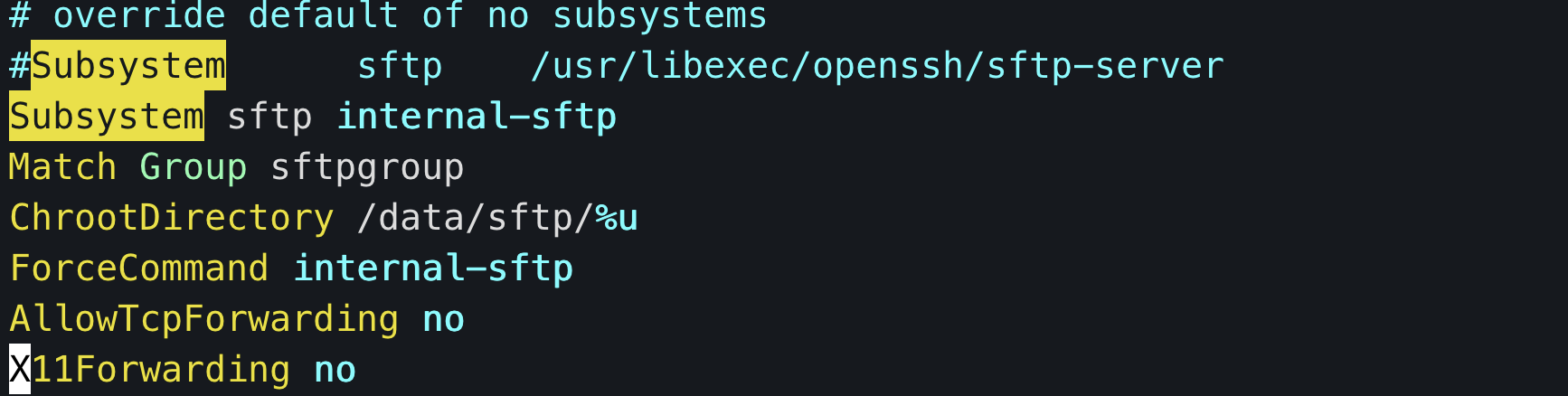
注释其中的
#Subsystem sftp /usr/libexec/openssh/sftp-server
添加配置
# sftp setting
Subsystem sftp internal-sftp
Match Group sftpgroup
ChrootDirectory /data/sftp/%u
ForceCommand internal-sftp
AllowTcpForwarding no
X11Forwarding no
chown root ~sftpadmin
chmod 755 /data/sftp/sftpadmin/
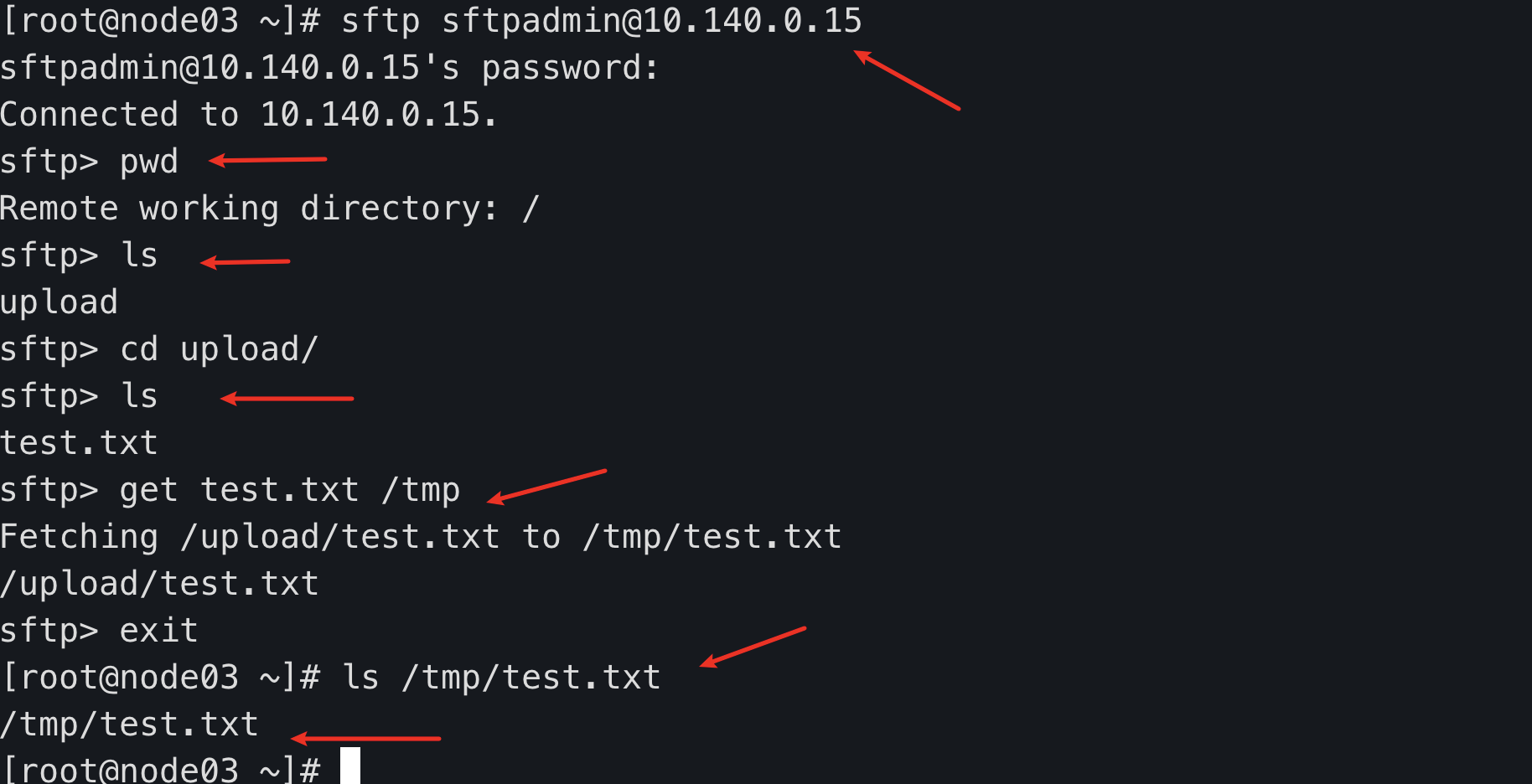
mkdir /data/sftp/sftpadmin/upload
chown sftpadmin:sftpgroup /data/sftp/sftpadmin/upload/
chmod 755 /data/sftp/sftpadmin/upload/
systemctl restart sshd
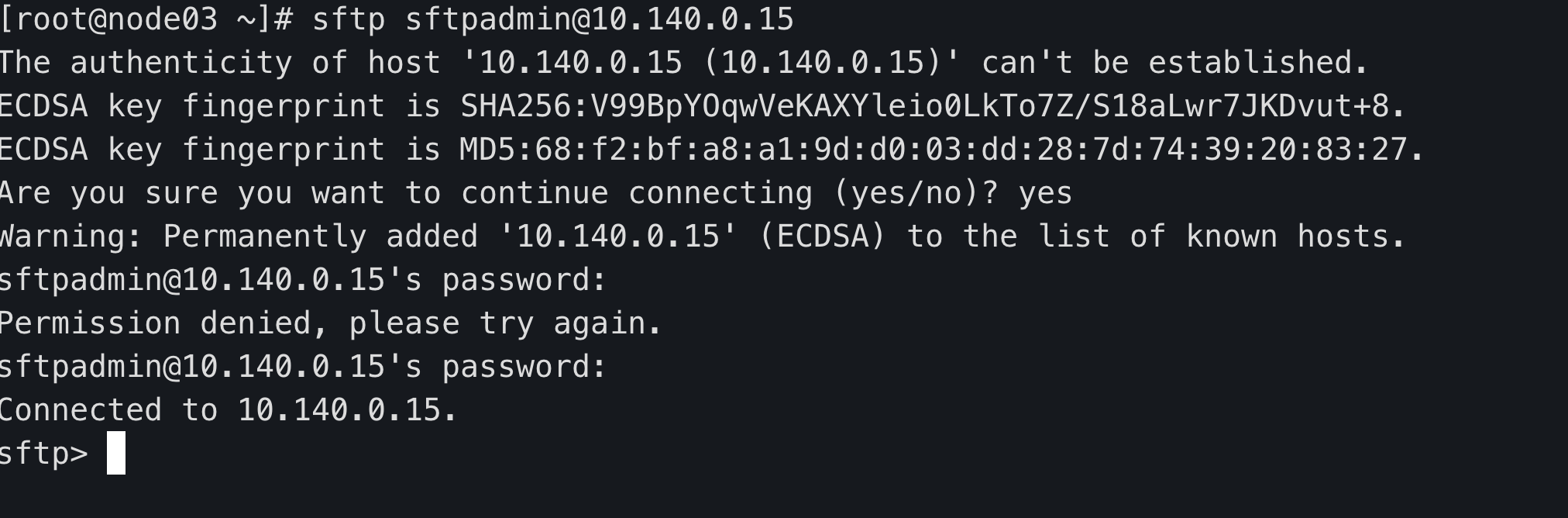
node03 sftp client
sftp sftpadmin@10.140.0.15