docker run -d --restart=unless-stopped -p 80:80 -p 443:443 --privileged rancher/rancher
1 使用docker 部署rancher
使用root特权模式部署 —privileged
docker run -d --restart=unless-stopped -p 80:80 -p 443:443 --privileged rancher/rancher
[root@node01 ~]# docker psCONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMESbf46c0fa30b2 rancher/rancher "entrypoint.sh" 2 minutes ago Up 2 minutes 0.0.0.0:8882->80/tcp, 0.0.0.0:8444->443/tcp unruffled_vaughan[root@node01 ~]#[root@node01 ~]#

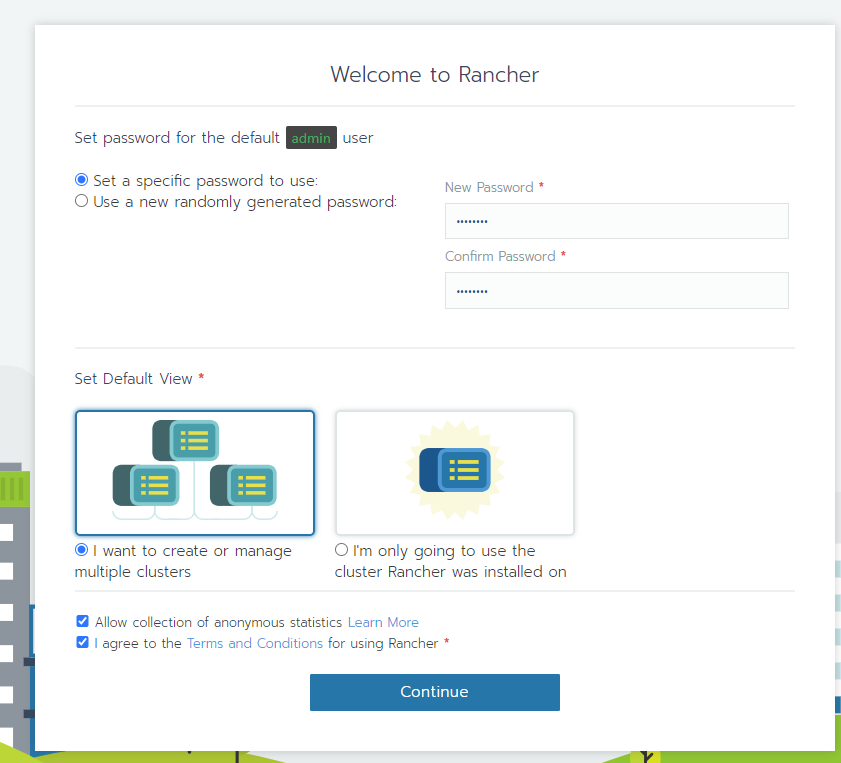
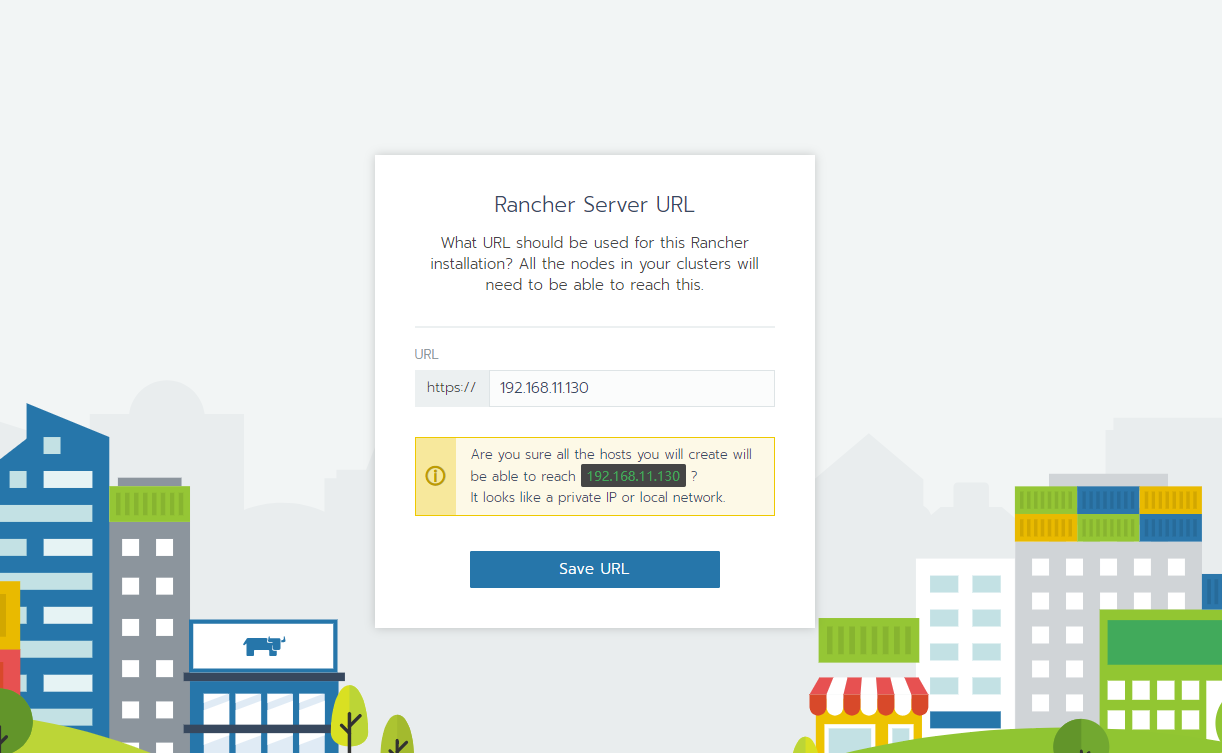
1.2 版本升级 数据备份
docker ps |grep rancherdocker stop rancherdocker create --volumes-from rancher --name rancher-data rancher/rancherdocker run --volumes-from rancher-data -v $PWD:/backup busybox tar zcvf /backup/rancher-data-backup-v2.4.13.tar.gz /var/lib/rancher
[root@rancher-server ~]# docker run --name rancher -d --privileged --restart=unless-stopped --volumes-from rancher-data -p 80:80 -p 443:443 rancher/rancher9f366e8c6c90f4482d3bb2252ab637df1398136a37e9f1f8afd460e5479bb12a[root@rancher-server ~]#[root@rancher-server ~]# docker ps |grep rancher9f366e8c6c90 rancher/rancher:v2.5.7-ent-rc3-linux-amd64 "entrypoint.sh" 13 seconds ago Up 11 seconds 0.0.0.0:80->80/tcp, 0.0.0.0:443->443/tcp rancher[root@rancher-server ~]#
新版UI
问题1:
[root@node01 ~]# docker run -d --restart=unless-stopped -p 80:80 -p 443:443 rancher/rancherc0b84379c876a78d00c177202f3ca0f61251bf70aa1e1a6b4cf5183f0986f3b6[root@node01 ~]#[root@node01 ~]# docker psCONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMESc0b84379c876 rancher/rancher "entrypoint.sh" 3 seconds ago Restarting (1) Less than a second ago crazy_mccarthy
查看日志:
[root@node01 ~]# docker logs c0bERROR: Rancher must be ran with the --privileged flag when running outside of KubernetesERROR: Rancher must be ran with the --privileged flag when running outside of KubernetesERROR: Rancher must be ran with the --privileged flag when running outside of KubernetesERROR: Rancher must be ran with the --privileged flag when running outside of KubernetesERROR: Rancher must be ran with the --privileged flag when running outside of KubernetesERROR: Rancher must be ran with the --privileged flag when running outside of KubernetesERROR: Rancher must be ran with the --privileged flag when running outside of KubernetesERROR: Rancher must be ran with the --privileged flag when running outside of Kubernetes[root@node01 ~]#
2 使用 helm部署rancher
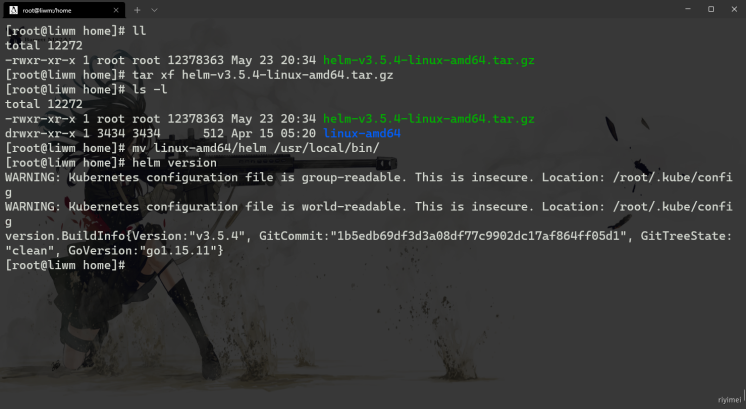
2.1 helm 安装
文件下载
rancher中国官方提供 http://mirror.cnrancher.com/
https://helm.sh/zh/docs/intro/install/
https://github.com/helm/helm/releases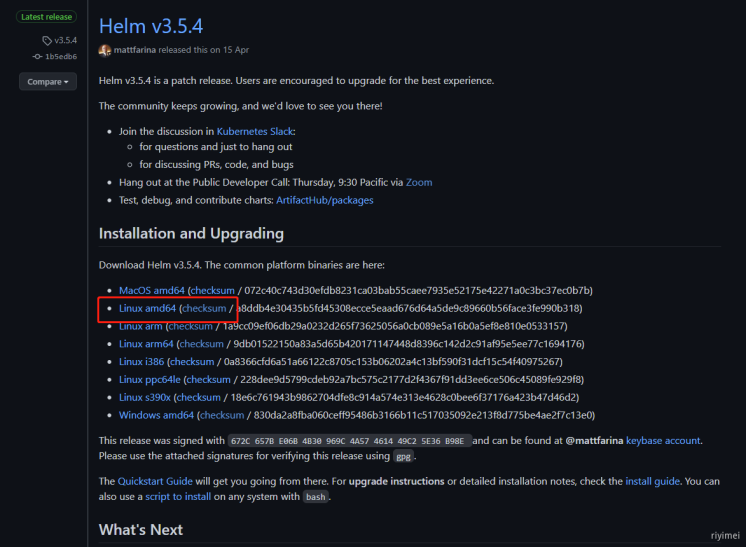
4.1 添加 helm rancher仓库
https://github.com/rancher/rancher/blob/master/chart/values.yaml
helm rancher仓库
https://artifacthub.io/packages/helm/rancher-stable/rancher
[root@liwm home]# helm repo add rancher-latest https://releases.rancher.com/server-charts/latest
4.2 部署rancher 证书
cattle-system
cert-manager
[root@liwm home]# kubectl create namespace cattle-systemnamespace/cattle-system created[root@liwm home]# kubectl apply --validate=false -f https://github.com/jetstack/cert-manager/releases/download/v1.0.4/cert-manager.crds.yamlcustomresourcedefinition.apiextensions.k8s.io/certificaterequests.cert-manager.io createdcustomresourcedefinition.apiextensions.k8s.io/certificates.cert-manager.io createdcustomresourcedefinition.apiextensions.k8s.io/challenges.acme.cert-manager.io createdcustomresourcedefinition.apiextensions.k8s.io/clusterissuers.cert-manager.io createdcustomresourcedefinition.apiextensions.k8s.io/issuers.cert-manager.io createdcustomresourcedefinition.apiextensions.k8s.io/orders.acme.cert-manager.io created[root@liwm home]# kubectl get pods --namespace cert-managerNo resources found in cert-manager namespace.[root@liwm home]# kubectl create namespace cert-managernamespace/cert-manager created[root@liwm home]# helm repo add jetstack https://charts.jetstack.ioWARNING: Kubernetes configuration file is group-readable. This is insecure. Location: /root/.kube/configWARNING: Kubernetes configuration file is world-readable. This is insecure. Location: /root/.kube/config"jetstack" has been added to your repositories[root@liwm home]# helm install \> cert-manager jetstack/cert-manager \> --namespace cert-manager \> --version v1.0.4WARNING: Kubernetes configuration file is group-readable. This is insecure. Location: /root/.kube/configWARNING: Kubernetes configuration file is world-readable. This is insecure. Location: /root/.kube/configNAME: cert-managerLAST DEPLOYED: Sun May 23 20:42:39 2021NAMESPACE: cert-managerSTATUS: deployedREVISION: 1TEST SUITE: NoneNOTES:cert-manager has been deployed successfully!In order to begin issuing certificates, you will need to set up a ClusterIssueror Issuer resource (for example, by creating a 'letsencrypt-staging' issuer).More information on the different types of issuers and how to configure themcan be found in our documentation:https://cert-manager.io/docs/configuration/For information on how to configure cert-manager to automatically provisionCertificates for Ingress resources, take a look at the `ingress-shim`documentation:https://cert-manager.io/docs/usage/ingress/[root@liwm home]# kubectl get pods --namespace cert-managerNAME READY STATUS RESTARTS AGEcert-manager-6d87886d5c-s6zq4 0/1 ContainerCreating 0 9scert-manager-cainjector-55db655cd8-h6qmt 0/1 ContainerCreating 0 9scert-manager-webhook-6846f844ff-lwwnr 0/1 ContainerCreating 0 9s[root@liwm home]#
[root@liwm home]# helm install rancher rancher-latest/rancher \> --namespace cattle-system \> --set hostname=rancher.my.orgWARNING: Kubernetes configuration file is group-readable. This is insecure. Location: /root/.kube/configWARNING: Kubernetes configuration file is world-readable. This is insecure. Location: /root/.kube/configNAME: rancherLAST DEPLOYED: Sun May 23 20:45:33 2021NAMESPACE: cattle-systemSTATUS: deployedREVISION: 1TEST SUITE: NoneNOTES:Rancher Server has been installed.NOTE: Rancher may take several minutes to fully initialize. Please standby while Certificates are being issued and Ingress comes up.Check out our docs at https://rancher.com/docs/rancher/v2.x/en/Browse to https://rancher.my.orgHappy Containering![root@liwm home]#
[root@liwm Eren]# helm ls --all-namespacesWARNING: Kubernetes configuration file is group-readable. This is insecure. Location: /root/.kube/configWARNING: Kubernetes configuration file is world-readable. This is insecure. Location: /root/.kube/configNAME NAMESPACE REVISION UPDATED STATUS CHARTAPP VERSIONcert-manager cert-manager 1 2021-05-23 20:42:39.3257997 +0800 CST deployed cert-manager-v1.0.4 v1.0.4fleet fleet-system 2 2021-05-23 12:48:46.4524648 +0000 UTC deployed fleet-0.3.5000.3.5rancher cattle-system 1 2021-05-23 20:45:33.0318282 +0800 CST deployed rancher-2.5.8v2.5.8rancher-operator rancher-operator-system 1 2021-05-23 12:47:30.1734295 +0000 UTC deployed rancher-operator-0.1.400 0.1.4rancher-webhook cattle-system 1 2021-05-23 12:47:46.7790814 +0000 UTC deployed rancher-webhook-0.1.000 0.1.0[root@liwm Eren]# kubectl -n cattle-system rollout status deploy/rancherdeployment "rancher" successfully rolled out[root@liwm Eren]# kubectl -n cattle-system get deploy rancherNAME READY UP-TO-DATE AVAILABLE AGErancher 3/3 3 3 139m[root@liwm Eren]#
修改 server的ClusterIP类型为:NodePort
[root@liwm Eren]# kubectl -n cattle-system get serviceNAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGErancher NodePort 10.101.123.206 <none> 80:30053/TCP,443:30155/TCP 150mrancher-webhook ClusterIP 10.102.182.200 <none> 443/TCP 148m[root@liwm Eren]#

