https://www.qikqiak.com/k8strain2/security/rbac/
https://www.bookstack.cn/read/feiskyer-kubernetes-handbook/plugins-auth.md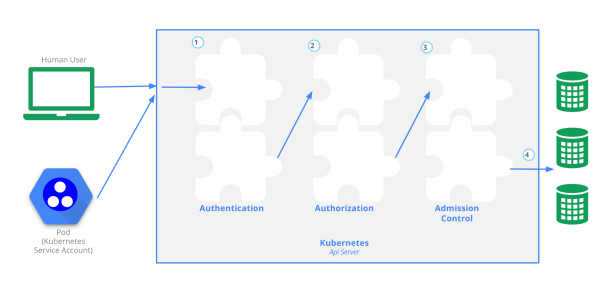
https://kubernetes.io/zh/docs/reference/access-authn-authz/rbac/
基于角色(Role)的访问控制(RBAC)是一种基于组织中用户的角色来调节控制对 计算机或网络资源的访问的方法
API 对象
Role 和 ClusterRole
kubectl create ns app-team1kubectl create serviceaccount cicd-token -n app-team1kubectl create clusterrole deployment-clusterrole --verb=create --resource=deployment,statefulset,daemonsetkubectl create rolebinding cicd-clusterrole --clusterrole=deployment-clusterrole --serviceaccount=app-team1:cicd-token
1[rancher@rmaster01 ~]$ kubectl create clusterrole deploymen-clusterrole --verb=create --resource=deployments,daemonsets,statefulsetsclusterrole.rbac.authorization.k8s.io/deploymen-clusterrole created2[rancher@rmaster01 ~]$ kubectl create namespace app-team1namespace/app-team1 created3[rancher@rmaster01 ~]$ kubectl -n app-team1 create serviceaccount cicd-tokenserviceaccount/cicd-token created4[rancher@rmaster01 ~]$ kubectl -n app-team1 create rolebinding cicd-token-binding --clusterrole=deployment-clusterrole --serviceaccount=app-team1:cicd-tokenrolebinding.rbac.authorization.k8s.io/cicd-token-binding created5[rancher@rmaster01 ~]$ kubectl -n app-team1 get clusterrole |grep deploymen-clusterroledeploymen-clusterrole 2021-03-23T13:40:18Z[rancher@rmaster01 ~]$[rancher@rmaster01 ~]$ kubectl -n app-team1 describe clusterrole deploymen-clusterroleName: deploymen-clusterroleLabels: <none>Annotations: <none>PolicyRule:Resources Non-Resource URLs Resource Names Verbs--------- ----------------- -------------- -----daemonsets.apps [] [] [create]deployments.apps [] [] [create]statefulsets.apps [] [] [create]6[rancher@rmaster01 ~]$ kubectl -n app-team1 get rolebindingNAME ROLE AGEcicd-token-binding ClusterRole/deployment-clusterrole 39s7[rancher@rmaster01 ~]$ kubectl -n app-team1 describe rolebinding cicd-token-bindingName: cicd-token-bindingLabels: <none>Annotations: <none>Role:Kind: ClusterRoleName: deployment-clusterroleSubjects:Kind Name Namespace---- ---- ---------ServiceAccount cicd-token app-team18[rancher@rmaster01 ~]$ kubectl -n app-team1 get serviceaccountsNAME SECRETS AGEcicd-token 1 20sdefault 1 3d20h[rancher@rmaster01 ~]$[rancher@rmaster01 ~]$ kubectl -n app-team1 describe serviceaccounts cicd-tokenName: cicd-tokenNamespace: app-team1Labels: <none>Annotations: <none>Image pull secrets: <none>Mountable secrets: cicd-token-token-8wvckTokens: cicd-token-token-8wvckEvents: <none>9[rancher@rmaster01 ~]$ kubectl -n app-team1 get secretsNAME TYPE DATA AGEcicd-token-token-8wvck kubernetes.io/service-account-token 3 27sdefault-token-d28tf kubernetes.io/service-account-token 3 3d20h[rancher@rmaster01 ~]$[rancher@rmaster01 ~]$ kubectl -n app-team1 describe secrets cicd-token-token-8wvckName: cicd-token-token-8wvckNamespace: app-team1Labels: <none>Annotations: kubernetes.io/service-account.name: cicd-tokenkubernetes.io/service-account.uid: 936fdb19-8083-400c-b45e-3c5eefb4936aType: kubernetes.io/service-account-tokenData====ca.crt: 1017 bytesnamespace: 9 bytestoken: eyJhbGciOiJSUzI1NiIsImtpZCI6IldsX0UyaDZXTm51N2RzUTRWa21td204R3dhVmxLNmNtOWZ1dkRKSG5WWUEifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJhcHAtdGVhbTEiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlY3JldC5uYW1lIjoiY2ljZC10b2tlbi10b2tlbi04d3ZjayIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJjaWNkLXRva2VuIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQudWlkIjoiOTM2ZmRiMTktODA4My00MDBjLWI0NWUtM2M1ZWVmYjQ5MzZhIiwic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50OmFwcC10ZWFtMTpjaWNkLXRva2VuIn0.biiSjHF1ihcig-1drK4YseWVsEQFTE1ihncRTpFJ5D-qf315F-v3USy9gBO2erC6KWi-_sLuUfgOQvZttzqLpzJZuky4X9jnaUPEdjgwHXOTNPBhN8Q93CPt_uCwyHSQVDaRZ_SBOwcBQzunrsakbVD1HpSlgNwiLyP8NJaFTnp_VbRlBWr9un3D4iYvSbgeVqfSru_4IVSPw7WLYPXdnzlsMLvZYXoh1vqXGzk5OS35Dmg69tw-EK-vO1j_N_AcIVzW3iVBRQC2MgifHpa8jf020naVKGUPtY-y0HENoCqzsRVXnDbI47vm8Lg1b9AQ7dQEvDgcEP5-fKME2wnfHA10[rancher@rmaster01 ~]$ kubectl -n app-team1 describe namespaces app-team1Name: app-team1Labels: <none>Annotations: cattle.io/status:{"Conditions":[{"Type":"ResourceQuotaInit","Status":"True","Message":"","LastUpdateTime":"2021-03-23T13:40:41Z"},{"Type":"InitialRolesPopu...lifecycle.cattle.io/create.namespace-auth: trueStatus: ActiveNo resource quota.No LimitRange resource.

