1. HTTPS原理
1.1. 加密类型
1.1.1. 对称加密
Symmetric[sɪ’mɛtrɪk] Encrypiton[ɛn’krɪpʃən],对称加密在加密与解密时使用相同密钥或者可以进行简单转换的不同密钥,这种加密方式一旦被第三方窃取密钥就容易造成数据泄漏,常见的算法有DES,3DES,IDEA,RC5,RC6等。
1.1.2. 非对称加密
非对称加密在加密和解时使用不同的密钥,分为公钥和私钥。一般用公钥对数据进行加密,而用私钥对数据进行解密。常见的算法有RSA,ECC等。其中RSA利用的是现有计算机无法完成超大数字的质因数分解来保证安全的。
相对于非对称加密而言,对称加密算法非常消耗性能,因此在实际使用中非对称加密一般仅用于建立SSL会话,会话建立后的一段时间内不再使用非加密对称进行验证。
1.2. HTTPS原理
1.2.1. 原理图
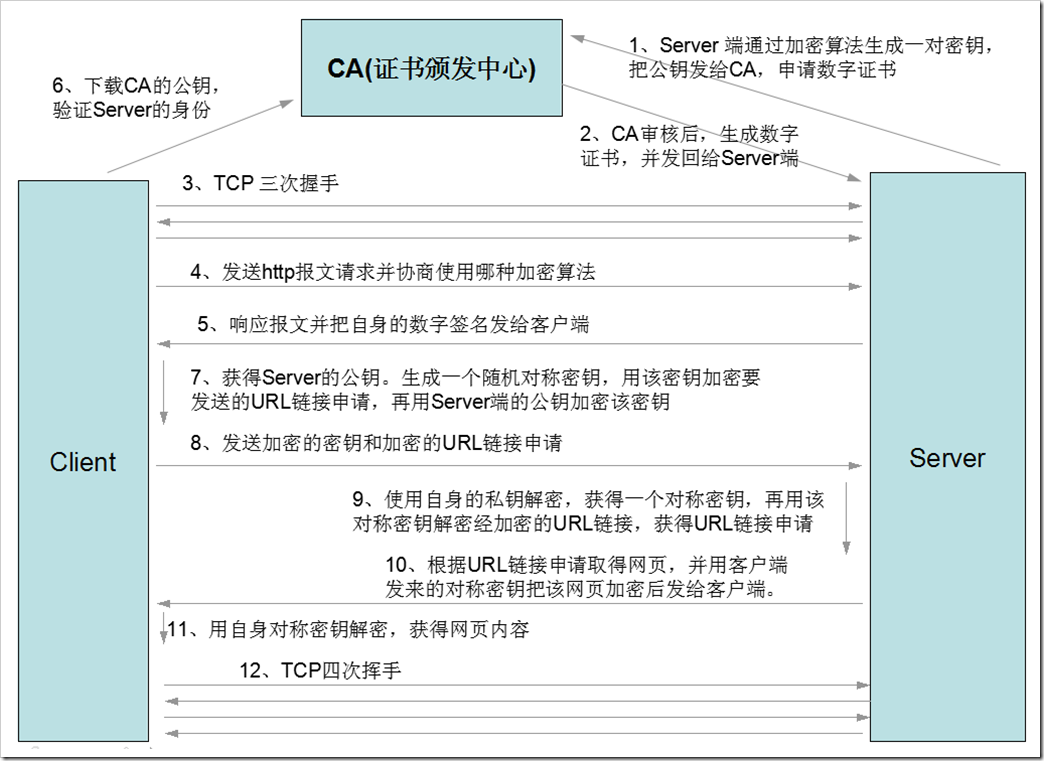

1.2.2. 文字表述
- 数字证书申请
- Server 通过加密工具生成一对公钥和私钥,并将公钥和相关信息发给CA申请数字证书
- CA 对Server 发来的信息进行验证。通过后发放数字证书给Server
- Client 与 Server 通信过程
- Client 与 Server 通过三次握手建立TCP连接
- Client 与 Server 协商加密算法
- Server 将数字证书发送给Client
- Client 通过CA验证数字证书的有效性,如果数字证书有效,则使用CA的公钥解密数字证书,得到Server的公钥
- Client 生成对称加密的密钥,使用对称密钥对报文进行加密,并使用Server公钥对加对称密钥进行加密
- Server 收到报文后,使用私钥对加密后的对称密钥进行解密,得到对称密钥,使用对称密钥解密Client的请求报文
- Server 对响应报文使用对称加密密钥进行加密,并发给Client
- Client 通过对称密钥对响应报文进行解密,得到响应信息
- Server 与 Client 四次挥手
注意点:
- HTTPS 涉及到对称和非对称加密,仅在建立SSL会话时使用非对称加密,后期同一个SSL会话使用的都是对称加密算法
- 如果涉及到多个七层负载均衡,一般会在第一个负载均衡器中卸载SSL,第一个负载均衡器到后端的业务服务器之间使用HTTP协议,这样可以提高性能,同时还可以避免在每一个后端服务器上部署证书
- HTTPS 中的非对称加密会消耗较多的CPU资源,因此为了降低SSL会话建立的开销,建议将SSL会话有效期设置长一些
- 各类客户端,包括但不限于浏览器、操作系统、服务器应用程序,都会内置常用的CA机构的数字证书,因此无需额外添加根证书。其它机构出具的CA证书是不受信任的,需要添加相关的根证书,如12306网站
2. http_ssl_module
2.1. ssl
Directives
Syntax: ssl on | off ;Default: ssl off ;Contest: http,server
Instroduction
This directive was made obsolete in version 1.15.0. The ssl parameter of the listen directive should be used instead.
2.2. ssl_buffer_size
Directives
Syntax: ssl_buffer_size size ;Default: ssl_buffer_size 16k ;Contest: http,server
Instroduction
Sets the size of the buffer used for sending data.By default, the buffer size is 16k, which corresponds to minimal overhead when sending big responses. To minimize Time To First Byte it may be beneficial to use smaller values, for example: ssl_buffer_size 4k ; .
2.3. ssl_certificate
Directives
Syntax: ssl_certificate file ;Default: CloseContest: http,server
Instroduction
Sepcifies certificate file,it looks like .crt or .pem.
2.4. ssl_certificate_key
Directives
Syntax: ssl_certificate_key file ;Default: CloseContest: http,server
Instroduction
Sepcifies certificate key file,it looks like *.key.
2.5. ssl_ciphers
Directives
Syntax: ssl_ciphers ciphers ;Default: ssl_ciphers HIGH:!aNULL:!MD5;Contest: http,server
Instroduction
The ciphers are specified in the format understood by the OpenSSL library.Different version maybe has differeent ciphers,so the better choice is specified.
2.6. ssl_protocols
Directives
Syntax: ssl_protocols [SSLv2] [SSLv3] [TLSv1] [TLSv1.1] [TLSv1.2] [TLSv1.3];Default: ssl_protocols TLSv1 TLSv1.1 TLSv1.2;Contest: http,server
Instroduction
Enables the specified protocols.
The TLSv1.1 and TLSv1.2 parameters (1.1.13, 1.0.12) work only when OpenSSL 1.0.1 or higher is used.
The TLSv1.3 parameter (1.13.0) works only when OpenSSL 1.1.1 built with TLSv1.3 support is used.
2.7. ssl_session_cache
Directives
Syntax: ssl_session_cache off|none|[builtin[:size]] [shared:name:size];Default: ssl_session_cache none ;Contest: http,server
Instroduction
off: Nginx tells client the session isn’t be reused.
none: Nginx tells client the session may be reused,but nginx doesn’t store session to cache.
builtin: the cache used by one worker process only,default size 20480 sessions.The parameter will cause memory fragmentation.
shared: the cache will share by all worker processes,1m size can store about 4000 sessions.
2.8. ssl_session_timeout
Directives
Syntax: ssl_session_timeout time ;Default: ssl_session_timeout 5m ;Contest: http,server
Instroduction
Specifies a time during which a client may reuse the session.
3. Example
3.1. Basic Example
3.1.1. Create certificate
[root@centos-81 ~]# openssl version ## 查看openssl版本
OpenSSL 1.0.2k-fips 26 Jan 2017
[root@centos-81 ~]# mkdir /opt/apps/nginx/conf/ssl_key ; cd /opt/apps/nginx/conf/ssl_key ## 创建SSL目录
[root@centos-81 ssl_key]# openssl genrsa -idea -out server.key 1024 ## 生成密钥
Generating RSA private key, 1024 bit long modulus....++++++.....++++++e is 65537 (0x10001)Enter pass phrase for server.key:Verifying - Enter pass phrase for server.key:
[root@centos-81 ssl_key]# openssl req -days 3650 -x509 -sha256 -nodes -newkey rsa:2048 -keyout server.key -out server.crt ## 生成签名证书
Generating a 2048 bit RSA private key..........................................................................................+++.......................................................................................+++writing new private key to 'server.key'-----You are about to be asked to enter information that will be incorporatedinto your certificate request.What you are about to enter is what is called a Distinguished Name or a DN.There are quite a few fields but you can leave some blankFor some fields there will be a default value,If you enter '.', the field will be left blank.-----Country Name (2 letter code) [XX]:CNState or Province Name (full name) []:AHLocality Name (eg, city) [Default City]:CZOrganization Name (eg, company) [Default Company Ltd]:BLOGOrganizational Unit Name (eg, section) []:Common Name (eg, your name or your server's hostname) []:www.heyang.comEmail Address []:1659775014@qq.com
3.1.2. Nginx配置
server{listen 80 ;server_name *.heyang.com;# rewrite (.*) https://$host$1 permanent ; ## 将http请求重定向成httpsrewrite (.*) https://$host$1 redirect ;}server {listen 443 ssl backlog=2048 ;server_name *.heyang.com;root /opt/website ;keepalive_timeout 100s ; ## 增加长连接的时间keepalive_requests 200 ;ssl_certificate ssl_key/server.crt ;ssl_certificate_key ssl_key/server.key ;ssl_ciphers HIGH:!aNULL:!MD5 ;ssl_session_cache shared:SSL:30m ; ## 设置SSL session缓存ssl_session_timeout 10m ;......

