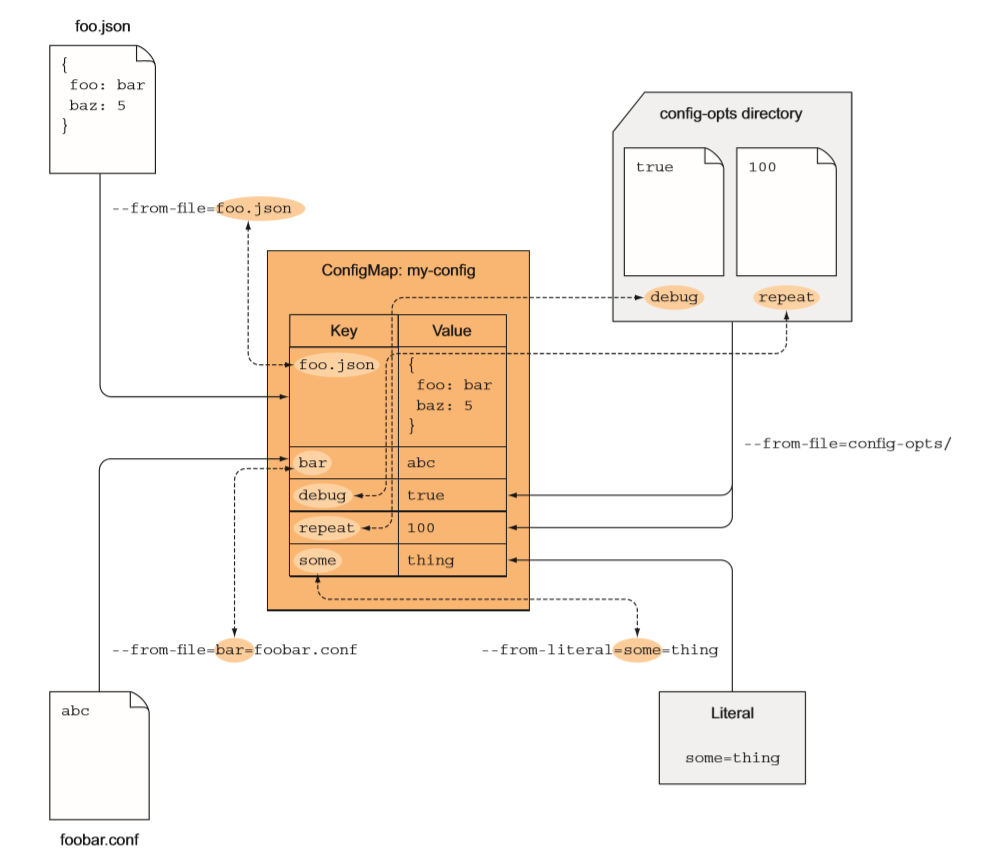
ConfigMap
许多应用经常会有从配置文件、命令行参数或者环境变量中读取一些配置信息,ConfigMap非常重要的资源对象。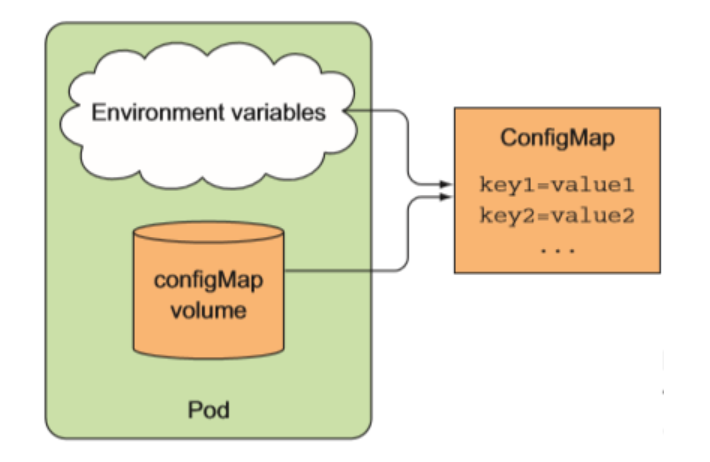
用命令创建
Examples:# Create a new configmap named my-config based on folder barkubectl create configmap my-config --from-file=path/to/bar# Create a new configmap named my-config with specified keys instead of file basenames on diskkubectl create configmap my-config --from-file=key1=/path/to/bar/file1.txt --from-file=key2=/path/to/bar/file2.txt# Create a new configmap named my-config with key1=config1 and key2=config2kubectl create configmap my-config --from-literal=key1=config1 --from-literal=key2=config2
键值格式
[root@master ~]# kubectl create configmap nginx-config --from-literal=nginx_port=80 --from-literal=server_name=myapp.magedu.com
configmap/nginx-config created
[root@master ~]# kubectl get cm
NAME DATA AGE
demo-config 3 13d
nginx-config 2 7s
[root@master ~]# kubectl describe cm nginx-config
Name: nginx-config
Namespace: default
Labels: <none>
Annotations: <none>
Data
====
nginx_port:
----
80
server_name:
----
myapp.magedu.com
Events: <none>
文件格式
[root@master ~]# vim www.conf
server {
server_name myapp.magedu.com;
listen 80;
root /usr/share/nginx/html;
}
[root@master ~]# kubectl create configmap nginx-www --from-file=www.conf
configmap/nginx-www created
[root@master ~]# kubectl get cm
NAME DATA AGE
demo-config 3 13d
nginx-config 2 3m38s
nginx-www 1 5s
[root@master ~]# kubectl describe cm nginx-www
Name: nginx-www
Namespace: default
Labels: <none>
Annotations: <none>
Data
====
www.conf:
----
server {
server_name myapp.magedu.com;
listen 80;
root /usr/share/nginx/html;
}
Events: <none>
yaml文件创建
kind: ConfigMap
apiVersion: v1
metadata:
name: cm-demo
namespace: default
data:
data.1: hello
data.2: world
config: |
property.1=value-1
property.2=value-2
property.3=value-3
env挂载configmap
vim myapp-pod-cm.yaml
apiVersion: v1
kind: Pod
metadata:
name: myapp-pod-cm
namespace: default
labels:
app: myapp
type: pod
spec:
containers:
- name: myapp
image: ikubernetes/myapp:v1
ports:
- name: http
containerPort: 80
env:
- name: NGINX_SERVER_PORT
valueFrom:
configMapKeyRef:
name: nginx-config
key: nginx_port
- name: NGINX_SERVER_NAME
valueFrom:
configMapKeyRef:
name: nginx-config
key: server_name
测试
[root@master pod_yaml]# kubectl apply -f myapp-pod-cm.yaml
pod/myapp-pod-cm created
[root@master pod_yaml]# kubectl get pod -o wide
NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES
demo-deploy-8675c97685-vhncn 1/1 Running 0 13d 10.244.2.5 node02 <none> <none>
demo-deploy-8675c97685-w7md2 1/1 Running 0 13d 10.244.1.5 node01 <none> <none>
demo-pod 1/2 Running 9 13d 10.244.2.4 node02 <none> <none>
myapp-nfs-pvc 1/1 Running 0 7h7m 10.244.1.11 node01 <none> <none>
myapp-pod-cm 1/1 Running 0 15s 10.244.1.14 node01 <none> <none>
nfs-client-provisioner-7fbb54945f-8rbcb 1/1 Running 0 5h17m 10.244.2.7 node02 <none> <none>
nfs-web-0 1/1 Running 0 4h58m 10.244.1.13 node01 <none> <none>
nfs-web-1 1/1 Running 0 4h58m 10.244.2.8 node02 <none> <none>
nfs-web-2 1/1 Running 0 4h57m 10.244.2.9 node02 <none> <none>
test-pod 1/1 Running 0 5h10m 10.244.1.12 node01 <none> <none>
[root@master pod_yaml]# kubectl exec myapp-pod-cm -it -- /bin/sh
/ # printenv
MYAPP_SVC_NODEPORT_SERVICE_HOST=10.106.106.242
MYAPP_SVC_PORT_80_TCP_ADDR=10.98.57.156
KUBERNETES_PORT=tcp://10.96.0.1:443
KUBERNETES_SERVICE_PORT=443
MYAPP_SVC_CLUSTERIP_SERVICE_HOST=10.98.148.121
MYAPP_SVC_PORT_80_TCP_PORT=80
HOSTNAME=myapp-pod-cm
SHLVL=1
MYAPP_SVC_PORT_80_TCP_PROTO=tcp
HOME=/root
MYAPP_SVC_NODEPORT_PORT=tcp://10.106.106.242:80
MYAPP_SVC_NODEPORT_SERVICE_PORT=80
MYAPP_SVC_CLUSTERIP_SERVICE_PORT=80
MYAPP_SVC_CLUSTERIP_PORT=tcp://10.98.148.121:80
NGINX_SERVER_PORT=80
NGINX_SERVER_NAME=myapp.magedu.com
MYAPP_SVC_PORT_80_TCP=tcp://10.98.57.156:80
MYAPP_SVC_NODEPORT_PORT_80_TCP_ADDR=10.106.106.242
MYAPP_SVC_CLUSTERIP_PORT_80_TCP_ADDR=10.98.148.121
MYAPP_SVC_NODEPORT_PORT_80_TCP_PORT=80
MYAPP_SVC_NODEPORT_PORT_80_TCP_PROTO=tcp
MYAPP_SVC_CLUSTERIP_PORT_80_TCP_PORT=80
TERM=xterm
NGINX_VERSION=1.12.2
MYAPP_SVC_CLUSTERIP_PORT_80_TCP_PROTO=tcp
KUBERNETES_PORT_443_TCP_ADDR=10.96.0.1
PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
KUBERNETES_PORT_443_TCP_PORT=443
KUBERNETES_PORT_443_TCP_PROTO=tcp
MYAPP_SVC_NODEPORT_PORT_80_TCP=tcp://10.106.106.242:80
MYAPP_SVC_SERVICE_HOST=10.98.57.156
MYAPP_SVC_CLUSTERIP_PORT_80_TCP=tcp://10.98.148.121:80
KUBERNETES_PORT_443_TCP=tcp://10.96.0.1:443
KUBERNETES_SERVICE_PORT_HTTPS=443
PWD=/
KUBERNETES_SERVICE_HOST=10.96.0.1
MYAPP_SVC_SERVICE_PORT=80
MYAPP_SVC_PORT=tcp://10.98.57.156:80
以存储卷形式挂载configmap
vim myapp-pod-cm-volume.yaml
apiVersion: v1
kind: Pod
metadata:
name: myapp-pod-cm-volume
namespace: default
labels:
app: myapp
type: pod
spec:
containers:
- name: myapp
image: ikubernetes/myapp:v1
ports:
- name: http
containerPort: 80
volumeMounts:
- name: nginxconf
mountPath: /etc/nginx/config.d
readOnly: true
volumes:
- name: nginxconf
configMap:
name: nginx-config
[root@master pod_yaml]# kubectl apply -f myapp-pod-cm-volume.yaml
pod/myapp-pod-cm-volume created
[root@master pod_yaml]# kubectl get pod -o wide
NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES
demo-deploy-8675c97685-vhncn 1/1 Running 0 13d 10.244.2.5 node02 <none> <none>
demo-deploy-8675c97685-w7md2 1/1 Running 0 13d 10.244.1.5 node01 <none> <none>
demo-pod 1/2 Running 9 13d 10.244.2.4 node02 <none> <none>
myapp-nfs-pvc 1/1 Running 0 7h16m 10.244.1.11 node01 <none> <none>
myapp-pod-cm 1/1 Running 0 8m41s 10.244.1.14 node01 <none> <none>
myapp-pod-cm-volume 1/1 Running 0 7s 10.244.1.15 node01 <none> <none>
nfs-client-provisioner-7fbb54945f-8rbcb 1/1 Running 0 5h26m 10.244.2.7 node02 <none> <none>
nfs-web-0 1/1 Running 0 5h6m 10.244.1.13 node01 <none> <none>
nfs-web-1 1/1 Running 0 5h6m 10.244.2.8 node02 <none> <none>
nfs-web-2 1/1 Running 0 5h6m 10.244.2.9 node02 <none> <none>
test-pod 1/1 Running 0 5h18m 10.244.1.12 node01 <none> <none>
[root@master pod_yaml]# kubectl exec myapp-pod-cm-volume -it -- /bin/sh
/ # cd /etc/nginx/config.d/
/etc/nginx/config.d # ls
nginx_port server_name
/etc/nginx/config.d # cat nginx_port
80
/etc/nginx/config.d # cat server_name
myapp.magedu.com
Secret
一般情况下ConfigMap是用来存储一些非安全的配置信息,如果涉及到一些安全相关的数据的话用ConfigMap就非常不妥了,因为ConfigMap是名为存储的,我们说这个时候我们就需要用到另外一个资源对象了:Secret,Secret用来保存敏感信息,例如密码、OAuth 令牌和 ssh key等等,将这些信息放在Secret中比放在Pod的定义中或者docker镜像中来说更加安全和灵活。
Secret有三种类型:
- Opaque:base64 编码格式的 Secret,用来存储密码、密钥等;但数据也可以通过base64 –decode解码得到原始数据,所有加密性很弱。
- kubernetes.io/dockerconfigjson:用来存储私有docker registry的认证信息。
- kubernetes.io/service-account-token:用于被
serviceaccount引用,serviceaccout 创建时Kubernetes会默认创建对应的secret。Pod如果使用了serviceaccount,对应的secret会自动挂载到Pod目录/run/secrets/kubernetes.io/serviceaccount中。
Opaque Secret
Opaque 类型的数据是一个 map 类型,要求value是base64编码格式,比如我们来创建一个用户名为 admin,密码为 admin321 的 Secret 对象,首先我们先把这用户名和密码做 base64 编码
命令创建
[root@master ~]# kubectl create secret generic mysql-root --from-literal=username=admin --from-literal=password=admin321
secret/mysql-root created
[root@master ~]# kubectl get secret
NAME TYPE DATA AGE
default-token-f9699 kubernetes.io/service-account-token 3 13d
demo-secret Opaque 1 13d
mysql-root Opaque 2 14s
nfs-client-provisioner-token-q5h6t kubernetes.io/service-account-token 3 5h51m
[root@master ~]# kubectl describe secrets mysql-root
Name: mysql-root
Namespace: default
Labels: <none>
Annotations: <none>
Type: Opaque
Data
====
password: 8 bytes
username: 5 bytes
yaml文件创建
[root@master ~]# echo -n "admin321" | base64
YWRtaW4zMjE=
[root@master ~]# echo -n "admin" | base64
YWRtaW4=
[root@master ~]# vim mysql-root-secret.yaml
apiVersion: v1
kind: Secret
metadata:
name: mysecret
type: Opaque
data:
username: YWRtaW4=
password: YWRtaW4zMjE=
[root@master ~]# kubectl get secrets
NAME TYPE DATA AGE
default-token-f9699 kubernetes.io/service-account-token 3 13d
demo-secret Opaque 1 13d
mysecret Opaque 2 4m46s
mysql-root Opaque 2 9m51s
nfs-client-provisioner-token-q5h6t kubernetes.io/service-account-token 3 6h
[root@master ~]# kubectl describe secrets mysecret
Name: mysecret
Namespace: default
Labels: <none>
Annotations:
Type: Opaque
Data
====
password: 8 bytes
username: 5 bytes
[root@master ~]# kubectl get secrets mysecret -o yaml
apiVersion: v1
data:
password: YWRtaW4zMjE=
username: YWRtaW4=
kind: Secret
metadata:
annotations:
kubectl.kubernetes.io/last-applied-configuration: |
{"apiVersion":"v1","data":{"password":"YWRtaW4zMjE=","username":"YWRtaW4="},"kind":"Secret","metadata":{"annotations":{},"name":"mysecret","namespace":"default"},"type":"Opaque"}
creationTimestamp: "2019-04-13T14:36:50Z"
name: mysecret
namespace: default
resourceVersion: "93037"
selfLink: /api/v1/namespaces/default/secrets/mysecret
uid: 92c96158-5df9-11e9-8bc6-000c296cdc6e
type: Opaque
[root@master ~]# echo "YWRtaW4zMjE=" | base64 -d
admin321
[root@master ~]# echo "YWRtaW4=" | base64 -d
admin
env挂载
vim secret1-pod.yaml
apiVersion: v1
kind: Pod
metadata:
name: secret1-pod
spec:
containers:
- name: secret1
image: busybox:latest
imagePullPolicy: IfNotPresent
command: [ "/bin/sh", "-c", "env" ]
env:
- name: USERNAME
valueFrom:
secretKeyRef:
name: mysecret
key: username
- name: PASSWORD
valueFrom:
secretKeyRef:
name: mysecret
key: password
[root@master ~]# kubectl apply -f secret1-pod.yaml
[root@master ~]# kubectl get pod -o wide
NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES
demo-deploy-8675c97685-vhncn 1/1 Running 0 13d 10.244.2.5 node02 <none> <none>
demo-deploy-8675c97685-w7md2 1/1 Running 0 13d 10.244.1.5 node01 <none> <none>
demo-pod 1/2 Running 9 13d 10.244.2.4 node02 <none> <none>
myapp-nfs-pvc 1/1 Running 0 7h58m 10.244.1.11 node01 <none> <none>
myapp-pod-cm 1/1 Running 0 51m 10.244.1.14 node01 <none> <none>
myapp-pod-cm-volume 1/1 Running 0 42m 10.244.1.15 node01 <none> <none>
nfs-client-provisioner-7fbb54945f-8rbcb 1/1 Running 0 6h8m 10.244.2.7 node02 <none> <none>
nfs-web-0 1/1 Running 0 5h49m 10.244.1.13 node01 <none> <none>
nfs-web-1 1/1 Running 0 5h49m 10.244.2.8 node02 <none> <none>
nfs-web-2 1/1 Running 0 5h48m 10.244.2.9 node02 <none> <none>
secret1-pod 0/1 Completed 2 26s 10.244.2.10 node02 <none> <none>
test-pod 1/1 Running 0 6h1m 10.244.1.12 node01 <none> <none>
[root@master ~]# kubectl logs secret1-pod
MYAPP_SVC_NODEPORT_SERVICE_HOST=10.106.106.242
KUBERNETES_SERVICE_PORT=443
KUBERNETES_PORT=tcp://10.96.0.1:443
MYAPP_SVC_CLUSTERIP_SERVICE_HOST=10.98.148.121
HOSTNAME=secret1-pod
SHLVL=1
HOME=/root
MYAPP_SVC_NODEPORT_PORT=tcp://10.106.106.242:80
MYAPP_SVC_NODEPORT_SERVICE_PORT=80
MYAPP_SVC_CLUSTERIP_PORT=tcp://10.98.148.121:80
MYAPP_SVC_CLUSTERIP_SERVICE_PORT=80
MYAPP_SVC_NODEPORT_PORT_80_TCP_ADDR=10.106.106.242
MYAPP_SVC_CLUSTERIP_PORT_80_TCP_ADDR=10.98.148.121
MYAPP_SVC_NODEPORT_PORT_80_TCP_PORT=80
MYAPP_SVC_NODEPORT_PORT_80_TCP_PROTO=tcp
USERNAME=admin
MYAPP_SVC_CLUSTERIP_PORT_80_TCP_PORT=80
KUBERNETES_PORT_443_TCP_ADDR=10.96.0.1
MYAPP_SVC_CLUSTERIP_PORT_80_TCP_PROTO=tcp
PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
KUBERNETES_PORT_443_TCP_PORT=443
KUBERNETES_PORT_443_TCP_PROTO=tcp
MYAPP_SVC_NODEPORT_PORT_80_TCP=tcp://10.106.106.242:80
MYAPP_SVC_CLUSTERIP_PORT_80_TCP=tcp://10.98.148.121:80
KUBERNETES_PORT_443_TCP=tcp://10.96.0.1:443
KUBERNETES_SERVICE_PORT_HTTPS=443
KUBERNETES_SERVICE_HOST=10.96.0.1
PWD=/
PASSWORD=admin321
Volume 挂载
vim secret2-pod.yaml
apiVersion: v1
kind: Pod
metadata:
name: secret2-pod
spec:
containers:
- name: secret2
image: busybox:latest
imagePullPolicy: IfNotPresent
command: ["/bin/sh", "-c", "ls /etc/secrets"]
volumeMounts:
- name: secrets
mountPath: /etc/secrets
volumes:
- name: secrets
secret:
secretName: mysecret
[root@master01 ~]# kubectl get pod
NAME READY STATUS RESTARTS AGE
demo-deploy-8675c97685-vhncn 1/1 Running 0 13d
demo-deploy-8675c97685-w7md2 1/1 Running 0 13d
demo-pod 1/2 Running 9 13d
myapp-nfs-pvc 1/1 Running 0 8h
myapp-pod-cm 1/1 Running 0 56m
myapp-pod-cm-volume 1/1 Running 0 47m
nfs-client-provisioner-7fbb54945f-8rbcb 1/1 Running 0 6h13m
nfs-web-0 1/1 Running 0 5h54m
nfs-web-1 1/1 Running 0 5h54m
nfs-web-2 1/1 Running 0 5h53m
secret1-pod 0/1 CrashLoopBackOff 5 5m22s
secret2-pod 0/1 Completed 2 18s
test-pod 1/1 Running 0 6h6m
[root@master01 ~]# kubectl logs secret2-pod
password
username
kubernetes.io/service-account-token
另外一种Secret类型就是kubernetes.io/service-account-token,用于被serviceaccount引用。serviceaccout 创建时 Kubernetes 会默认创建对应的 secret。Pod 如果使用了 serviceaccount,对应的secret会自动挂载到Pod的/var/run/secrets/kubernetes.io/serviceaccount目录中。
[root@master01 ~]# kubectl get pod
NAME READY STATUS RESTARTS AGE
demo-deploy-8675c97685-vhncn 1/1 Running 0 13d
demo-deploy-8675c97685-w7md2 1/1 Running 0 13d
demo-pod 1/2 Running 9 13d
myapp-nfs-pvc 1/1 Running 0 8h
myapp-pod-cm 1/1 Running 0 60m
myapp-pod-cm-volume 1/1 Running 0 52m
nfs-client-provisioner-7fbb54945f-8rbcb 1/1 Running 0 6h18m
nfs-web-0 1/1 Running 0 5h58m
nfs-web-1 1/1 Running 0 5h58m
nfs-web-2 1/1 Running 0 5h58m
secret1-pod 0/1 CrashLoopBackOff 6 9m47s
secret2-pod 0/1 CrashLoopBackOff 5 4m43s
test-pod 1/1 Running 0 6h10m
[root@master01 ~]# kubectl describe pod demo-pod
Name: demo-pod
Namespace: default
Priority: 0
PriorityClassName: <none>
Node: node02/192.168.48.202
Start Time: Sun, 31 Mar 2019 12:53:32 +0800
Labels: app=myapp
type=pod
Annotations: kubectl.kubernetes.io/last-applied-configuration:
{"apiVersion":"v1","kind":"Pod","metadata":{"annotations":{},"labels":{"app":"myapp","type":"pod"},"name":"demo-pod","namespace":"default"...
Status: Running
IP: 10.244.2.4
Containers:
myapp:
Container ID: docker://83ae7929a8c83e907a8d445a44d4bc254942b83332cdc63044b2793f85a6658d
Image: ikubernetes/myapp:v1
Image ID: docker-pullable://ikubernetes/myapp@sha256:9c3dc30b5219788b2b8a4b065f548b922a34479577befb54b03330999d30d513
Port: 80/TCP
Host Port: 0/TCP
State: Running
Started: Sun, 31 Mar 2019 12:53:33 +0800
Ready: True
Restart Count: 0
Environment: <none>
Mounts:
/var/run/secrets/kubernetes.io/serviceaccount from default-token-f9699 (ro)
busybox:
Container ID: docker://75a994741b6583346519394a01701f9a444cfe5283ff78da2b818cf22c54cab3
Image: busybox:latest
Image ID: docker-pullable://busybox@sha256:954e1f01e80ce09d0887ff6ea10b13a812cb01932a0781d6b0cc23f743a874fd
Port: <none>
Host Port: <none>
Command:
/bin/sh
-c
mkdir -p /usr/share/nginx/html; echo $(date) >> /usr/share/nginx/html/test.html;sleep 3600
State: Terminated
Reason: Completed
Exit Code: 0
Started: Sat, 13 Apr 2019 18:54:24 +0800
Finished: Sat, 13 Apr 2019 19:54:24 +0800
Last State: Terminated
Reason: Completed
Exit Code: 0
Started: Sat, 13 Apr 2019 17:54:02 +0800
Finished: Sat, 13 Apr 2019 18:54:02 +0800
Ready: False
Restart Count: 9
Environment: <none>
Mounts:
/var/run/secrets/kubernetes.io/serviceaccount from default-token-f9699 (ro)
Conditions:
Type Status
Initialized True
Ready False
ContainersReady False
PodScheduled True
Volumes:
default-token-f9699:
Type: Secret (a volume populated by a Secret)
SecretName: default-token-f9699
Optional: false
QoS Class: BestEffort
Node-Selectors: <none>
Tolerations: node.kubernetes.io/not-ready:NoExecute for 300s
node.kubernetes.io/unreachable:NoExecute for 300s
Events: <none>
[root@master01 ~]# kubectl exec demo-pod ls /var/run/secrets/kubernetes.io/serviceaccount
ca.crt
namespace
token
[root@master01 ~]# kubectl exec demo-pod cat /var/run/secrets/kubernetes.io/serviceaccount/token
eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJkZWZhdWx0Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZWNyZXQubmFtZSI6ImRlZmF1bHQtdG9rZW4tZjk2OTkiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoiZGVmYXVsdCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6IjhkN2RhOWMwLTUzMWQtMTFlOS04NmVhLTAwMGMyOTZjZGM2ZSIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDpkZWZhdWx0OmRlZmF1bHQifQ.VwxzFq7N1UHBDaPxkrELrnnUYsMvFbQIaz18XdYlryYWGIMAvQ3NzSKqrNka2Ydk1joh9RLA-XIyCa1I2jREpkcKZqeVjE5KQ9wURbjRQEhVTfUG3tw8NQomO_f41M5c1TGq5OrD7AvBfeS96OQnArEdzJwNQCK1guhp2jhoyiHQBdRCoYvjlOnHkUznZ2VT8_IQ7D7cVbkSNvneHqXcCYhpdtGa
kubernetes.io/dockerconfigjson
除了上面的Opaque这种类型外,我们还可以来创建用户docker registry认证的Secret,直接使用kubectl create命令创建即可,如下:
$ kubectl create secret docker-registry myregistry --docker-server=DOCKER_SERVER --docker-username=DOCKER_USER --docker-password=DOCKER_PASSWORD --docker-email=DOCKER_EMAIL
secret "myregistry" created
然后查看Secret列表:
$ kubectl get secret
NAME TYPE DATA AGE
default-token-n9w2d kubernetes.io/service-account-token 3 33d
myregistry kubernetes.io/dockerconfigjson 1 15s
mysecret Opaque 2 34m
注意看上面的TYPE类型,myregistry是不是对应的kubernetes.io/dockerconfigjson,同样的可以使用describe命令来查看详细信息:
$ kubectl describe secret myregistry
Name: myregistry
Namespace: default
Labels: <none>
Annotations: <none>
Type: kubernetes.io/dockerconfigjson
Data
====
.dockerconfigjson: 152 bytes
同样的可以看到Data区域没有直接展示出来,如果想查看的话可以使用-o yaml来输出展示出来:
$ kubectl get secret myregistry -o yaml
apiVersion: v1
data:
.dockerconfigjson: eyJhdXRocyI6eyJET0NLRVJfU0VSVkVSIjp7InVzZXJuYW1lIjoiRE9DS0VSX1VTRVIiLCJwYXNzd29yZCI6IkRPQ0tFUl9QQVNTV09SRCIsImVtYWlsIjoiRE9DS0VSX0VNQUlMIiwiYXV0aCI6IlJFOURTMFZTWDFWVFJWSTZSRTlEUzBWU1gxQkJVMU5YVDFKRSJ9fX0=
kind: Secret
metadata:
creationTimestamp: 2018-06-19T16:01:05Z
name: myregistry
namespace: default
resourceVersion: "3696966"
selfLink: /api/v1/namespaces/default/secrets/myregistry
uid: f91db707-73d9-11e8-a101-525400db4df7
type: kubernetes.io/dockerconfigjson
可以把上面的data.dockerconfigjson下面的数据做一个base64解码,看看里面的数据是怎样的呢?
$ echo eyJhdXRocyI6eyJET0NLRVJfU0VSVkVSIjp7InVzZXJuYW1lIjoiRE9DS0VSX1VTRVIiLCJwYXNzd29yZCI6IkRPQ0tFUl9QQVNTV09SRCIsImVtYWlsIjoiRE9DS0VSX0VNQUlMIiwiYXV0aCI6IlJFOURTMFZTWDFWVFJWSTZSRTlEUzBWU1gxQkJVMU5YVDFKRSJ9fX0= | base64 -d
{"auths":{"DOCKER_SERVER":{"username":"DOCKER_USER","password":"DOCKER_PASSWORD","email":"DOCKER_EMAIL","auth":"RE9DS0VSX1VTRVI6RE9DS0VSX1BBU1NXT1JE"}}}
如果我们需要拉取私有仓库中的docker镜像的话就需要使用到上面的myregistry这个Secret:
apiVersion: v1
kind: Pod
metadata:
name: foo
spec:
containers:
- name: foo
image: 192.168.1.100:5000/test:v1
imagePullSecrets:
- name: myregistrykey
我们需要拉取私有仓库镜像192.168.1.100:5000/test:v1,我们就需要针对该私有仓库来创建一个如上的Secret,然后在Pod的 YAML 文件中指定imagePullSecrets
Secret 与 ConfigMap 对比
最后我们来对比下Secret和ConfigMap这两种资源对象的异同点:
相同点:
- key/value的形式
- 属于某个特定的namespace
- 可以导出到环境变量
- 可以通过目录/文件形式挂载
- 通过 volume 挂载的配置信息均可热更新
不同点:
- Secret 可以被 ServerAccount 关联
- Secret 可以存储 docker register 的鉴权信息,用在 ImagePullSecret 参数中,用于拉取私有仓库的镜像
- Secret 支持 Base64 加密
- Secret 分为 kubernetes.io/service-account-token、kubernetes.io/dockerconfigjson、Opaque 三种类型,而 Configmap 不区分类型