- 0X01. API攻击指南
- 1.API版本比对突破
- 2.API接口一般存在多个端点
- 3.暴力枚举API端点
- 4.API请求参数污染(HPP)
- 5.API中的SSRF漏洞利用方式
- 6.MA的方式去获取API端点
- 7.分清楚要测试的API是什么
- 8.检查API接口是否支持SOAP API
- 9. 请求体的参数(POST提交的请求体)比GET型的参数更容易受到攻击
- 10.可预测的API业务操作
- 11.多做尝试
- 12.使用API的MA绕过认证机制
- 13.从子域名或者兄弟域名下手,拓展攻击面(旁站)
- 14.关注静态资源的授权认证方式
- 15.使用Burpsuite的URL节点观察整个站点的目录结构
- 16.APP测试可以寻找无加固的版本测试
- 17.寻找更加脆弱并且少有人关注的API
- 18.找到你认为的重要的容易出现漏洞的点
- 19.有速率限制的生产环境
- 20.寻找历史网站镜像上存在的API端点
- 21.API设计不当会导致泄露PII(个人身份信息)
- 22.任意文件下载让黑盒测试变成灰盒测试
- 23.还是建议你去攻击非生产环境
- 24.导出注入
- 25.尝试去Bypass(绕过技巧)
- 26.关于API xss
- 27.理解API的业务逻辑
- 28.寻找旧版本的APK,IPA文件安装包
- 29.总之锤就对了
- 0X02.有的没的赏金技巧
0X01. API攻击指南
来自:https://github.com/inonshk/31-days-of-API-Security-Tips
https://www.ddosi.com/b422/
推特上搜索BugbountyTips
1.API版本比对突破
Older APIs versions tend to be more vulnerable and they lack security mechanisms. Leverage the predictable nature of REST APIs to find old versions. Saw a call to api/v3/login? Check if api/v1/login exists as well. It might be more vulnerable.
当拿到一个形如api/v3/login的时候,可以去猜测是否存在api/v1/login
低版本的API接口往往存在更多漏洞
2.API接口一般存在多个端点
Never assume there’s only one way to authenticate to an API! Modern apps have many API endpoints for AuthN: /api/mobile/login | /api/v3/login | /api/magic_link; etc.. Find and test all of them for AuthN problems.
_
3.暴力枚举API端点
形如api/v1/1,api/v1/2,api/v1/3…此时若未对端点进行鉴权,可能导致枚举出所有敏感信息
Remember how SQL Injections used to be extremely common 5-10 years ago, and you could break into almost every company? BOLA (IDOR) is the new epidemic of API security. As a pentester, if you understand how to exploit it, your glory is guaranteed.
Learn more about BOLA : https://medium.com/@inonst/a-deep-dive-on-the-most-critical-api-vulnerability-bola-1342224ec3f2
4.API请求参数污染(HPP)
Testing a Ruby on Rails App & noticed an HTTP parameter containing a URL? Developers sometimes use “Kernel#open” function to access URLs == Game Over. Just send a pipe as the first character and then a shell command (Command Injection by design)
Learn more about the open function: https://apidock.com/ruby/Kernel/open
5.API中的SSRF漏洞利用方式
扫描内网端口,扫描存活IP,使用webhook辅助验证,下载一个特别大的文件导致拒绝服务,反射性的ssrf会暴露内部控制台
Found SSRF? use it for:
- Internal port scanning
- Leverage cloud services(like 169.254.169.254)
- Use http://webhook.site to reveal IP Address & HTTP Library
- Download a very large file (Layer 7 DoS)
- Reflective SSRF? disclose local mgmt consoles
6.MA的方式去获取API端点
Mass Assignment is a real thing. Modern frameworks encourage developers to use MA without understanding the security implications. During exploitation, don’t guess object’s properties names, simply find a GET endpoint that returns all of them.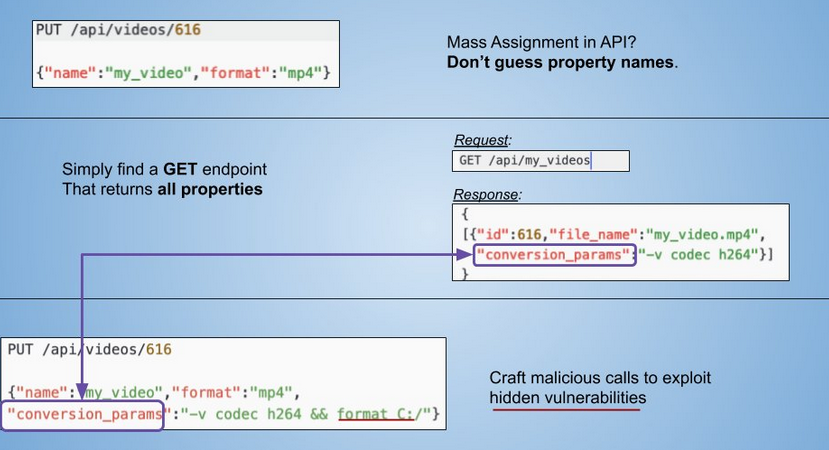
7.分清楚要测试的API是什么
A company exposes an API for developers? This is not the same API which is used by mobile / web application. Always test them separately. Don’t assume they implement the same security mechanisms.
8.检查API接口是否支持SOAP API
SOAP API往往会使用JWT的身份验证方式,弱JWT加密会导致jwt认证伪造
Pentest for REST API? Give it a chance and check if the API supports SOAP also. Change the content-type to “application/xml”, add a simple XML in the request body, and see how the API handles it.
Sometimes the authentication is done in a different component that is shared between REST & SOAP APIs == SOAP API may support JWT If the API returns stack trace with a DUMPling, it’s probably vulnerable**
9. 请求体的参数(POST提交的请求体)比GET型的参数更容易受到攻击
Pentest for APIs? Trying to find BOLA (IDOR) vulnerabilities? IDs in the HTTP bodies/headers tend to be more vulnerable than IDs in URLs. Try to focus on them first.
10.可预测的API业务操作
猜测API运作的方式,比如使用请求方法来添加用户或者删除用户
Exploiting BFLA (Broken Function Level Authorization)? Leverage the predictable nature of REST to find admin API endpoints! E.g: you saw the following API call GET /api/v1/users/<id>Give it a chance and change to DELETE / POST to create/delete users.
11.多做尝试
比如API使用的参数是字符型,那么可以尝试一下数字型或者其他类型测试
Testing for BOLA (IDOR)? Even if the ID is GUID or non-numeric, try to send a numeric value. For example: /?user_id=111 instead of user_id=inon@traceable.aiSometimes the AuthZ mechanism supports both and it’s easier the brute force numbers.
_
12.使用API的MA绕过认证机制
API中可能固定的端点用于更新密码而不做校验,则可能导致绕过身份认证
*Use Mass Assignment to bypass security mechanisms. E.g., “enter password” mechanism:
POST /api/reset_passrequires old password.PUT /api/update_useris vulnerable to MA == can be used to update pass without sending the old one (For CSRF)*
13.从子域名或者兄弟域名下手,拓展攻击面(旁站)
当没有突破时,可以尝试寻找同域名下的父/子级,兄弟域名进行测试,因为在这些域名上可能部署了同一套API机制,但是你可以从子域找到未曾发现的版本信息,API入口(正常情况下一般会存在三类环境,正式环境【生产环境】,预上线环境【介于生产和测试之间】,测试环境(安全性不那么可靠))
Got stuck during an API pentest? Expand your attack surface! Find sub/sibling domains using http://Virustotal.com & http://Censys.io. Some of these domains might expose the same APIs with different configurations/versions.
14.关注静态资源的授权认证方式
静态资源的授权不同于web应用,即使做了严格的鉴权也有可能越权访问其他用户的静态资源(一般出现在,保存的人脸认证视频,身份证信息,个人认证信息等高度敏感的静态资源)
Static resource==photo,video,.. Web Servers(IIS, Apache) treat static resources differently when it comes to authorization. Even if developers implemented decent authorization, there’s a good chance you can access static resources of other users.
_
15.使用Burpsuite的URL节点观察整个站点的目录结构
观察其结构,根据相似性,猜测没有探测到的敏感目录,备份文件
Even if you use another web proxy, always use Burp in the background. The guys at @PortSwigger are doing a really good job at helping you manage your pentest. Use the “tree view” (free version) feature to see all API endpoints you’ve accessed.
16.APP测试可以寻找无加固的版本测试
APP测试中,可能在前几个版本没有做证书认证,流量加密这些手段,但是它还是可以正常运行的,这种就可以方便测试,不必在逆向工程上耗费大量时间
Mobile Certificate Pinning? Before you start reverse engineering & patching the client app, check for both iOS & Android clients and older versions of them. There’s a decent chance that the pinning isn’t enabled in one of them. Save time.
17.寻找更加脆弱并且少有人关注的API
越是主站的API,防护力度一般越大,寻找分站或者子域名下的API口子测试,一般而言数据是互通的,就是数量的大小的问题。
Companies & developers tend to put more resources (including security) into the main APIs. Always look for the most niche features that nobody uses to find interesting vulnerabilities.POST /api/profile/upload_christmas_voice_greeting
18.找到你认为的重要的容易出现漏洞的点
Which features do you find tend to be more vulnerable?I’ll start:
- Organization’s user management
- Export to CSV/HTML/PDF
- Custom views of dashboards
- Sub user creation&management
- Object sharing (photos, posts,etc)
19.有速率限制的生产环境
这里还是找预上线环境或者测试环境测试,正式环境可能存在反爆破机制,甚至Waf等安全设备
Testing AuthN APIs? If you test in production, there’s a good chance that AuthN endpoints have anti brute-force protection. Anyhow, DevOps engineers tend to disable rate limiting in non-production environments. Don’t forget to test them :)
A good example of this issue: Facebook Breach (Found by @sehacure) http://www.anandpraka.sh/2016/03/how-i-could-have-hacked-your-facebook.html
20.寻找历史网站镜像上存在的API端点
如何扩大攻击面?寻找互联网备份网站http://archive.com上存在的网站镜像中包含的JS文件去探测可能在正式环境中剔除但是仍然在运作的API端点
Got stuck during an API pentest? Expand the attack surface! Use http://archive.com, find old versions of the web-app and explore new API endpoints. Can’t use the client? scan the .js files for URLs. Some of them are API endpoints.
_
21.API设计不当会导致泄露PII(个人身份信息)
寻找可以dump下所有身份凭据的API端点,比如/downloadreceipt,/export_receipt, etc..
_APIs tend to leak PII by design. BE engineers return raw JSON objects and rely on FE engineers to filter out sensitive data. Found a sensitive resource (e.g, receipt)? Find all the EPs that return it: /download_receipt,/export_receipt, etc..
Some of the endpoints might leak excessive data that should not be accessible by the user. This is an example for OWASP Top 10 For APIs - #3 - Excessive Data Exposure
22.任意文件下载让黑盒测试变成灰盒测试
通过任意文件读取下载网站整站备份文件,JAVA类型的站点可能存在war包,jar包,通过文件下载后,使用对应的反编译工具还原网站源码,进行代码审计,寻找其中的配置文件,如暴露在公网上的数据库端口,你可以读取到了数据库的用户和密码(一般配置文件中都有),提升危害度
Found a way to download arbitrary files from a web server? Shift the test from black-box to white-box. Download the source code of the app (DLL files: use IL-spy; Compiled Java - use Luyten) Read the code and find new issues!
_
23.还是建议你去攻击非生产环境
Got stuck during an API pentest? Expand your attack surface! Remember: developers often disable security mechanisms in non-production environments (qa/staging/etc); Leverage this fact to bypass AuthZ, AuthN, rate limiting & input validation.
_
24.导出注入
注意外部实体的引入会导致安全问题,这里说到的是Html转换导致的一些问题
关于导出攻击的演示参考:https://www.youtube.com/watch?v=2UIU9EvJunQ
Found an “export to PDF” feature? There’s a good chance the developers use an external library to convert HTML —> PDF behind the scenes. Try to inject HTML elements and cause “Export Injection”.
Learn more about Export Injection: https://medium.com/@inonst/export-injection-2eebc4f17117
关于HTML转换PDF如果引入外部库,如何判断外部库?
要了解使用了哪个外部库,只需使用Hex Editor打开已经转换好的PDF文件,然后搜索“ Creator”或“ Author”之类的字符串即可
25.尝试去Bypass(绕过技巧)
Looking for BOLA (IDOR) in APIs? got 401/403 errors? AuthZ bypass tricks:
- Wrap ID with an array
{“id”:111}—>{“id”:[111]} - JSON wrap
{“id”:111}—>{“id”:{“id”:111}} - Send ID twice
URL?id=<LEGIT>&id=<VICTIM> - Send wildcard
{"user_id":"*"}In some cases, the AuthZ mechanism expects a plain string (an ID in this case), and if it receives a JSON instead it won’t perform the AuthZ checks. Then, when the input goes to the data fetching component, it might be okay with a JSON instead of string(e.g: it flattens the JSON)
26.关于API xss
BE Servers no longer responsible for protecting against XSS. APIs don’t return HTML, but JSON instead. If API returns XSS payload? - E.g: {"name":"In<script>alert(21)</script>on}That’s fine! The protection always needs to be on the client side
_
27.理解API的业务逻辑
APIs expose the underlying implementation of the app. Pentesters should leverage this fact to better understand users, roles, resources & correlations between them and find cool vulnerabilities & exploits. Always be curious about the API responses.
_
28.寻找旧版本的APK,IPA文件安装包
开发人员不会第一天就把所有的安全设计好,至少目前做不到,所以和寻找历史网站镜像一样去寻找旧版本的app安装包,进行测试,这些老版本的app一般不会有安全防护,甚至可以找到一些历史的URL端点(新版本中已经删除,但是在旧版本依旧存在,功能依旧正常运作)。
Got stuck during an API pentest? Expand your attack surface! If the API has mobile clients, download old versions of the APK file to explore old/legacy functionality and discover new API endpoints.
Remember: companies don’t always implement security mechanisms from day one && DevOps engineers don’t often deprecate old APIs. Leverage these facts to find shadow API endpoints that don’t implement security mechanism (authorization, input filtering & rate limiting) Download old APK versions of android apps: https://apkpure.com
29.总之锤就对了
这里说的是Fuzzing测试,一般可能会导致拒绝服务,超出预先设置的数据长度,会使得程序内存溢出。
Found a limit / page param? (e.g: /api/news?limit=100) It might be vulnerable to Layer 7 DoS. Try to send a long value (e.g: limit=999999999) and see what happens :)
_
0X02.有的没的赏金技巧
很有用的一些技巧:https://www.infosecmatter.com/bug-bounty-tips-4-aug-03/
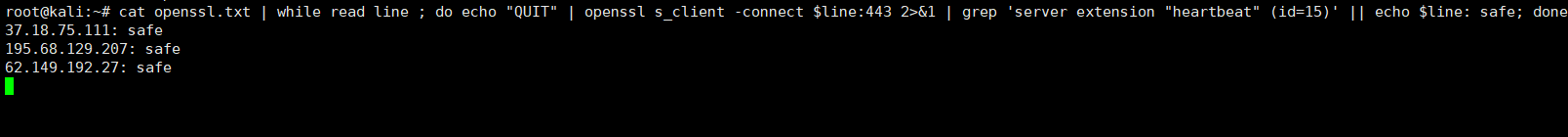
1) 一句话检测心脏滴血漏洞(CVE-2014-0160)
cat list.txt | while read line ; do echo "QUIT" | openssl s_client -connect $line:443 2>&1 | grep 'server extension "heartbeat" (id=15)' || echo $line: safe; done
2)使用grep从杂乱的文件中提取URL
cat file | grep -Eo "(http|https)://[a-zA-Z0-9./?=_-]*"*curl http://host.xx/file.js | grep -Eo "(http|https)://[a-zA-Z0-9./?=_-]*"*
3)提取APK中的敏感信息
解压APP
apktool d app_name.apk
提取信息
grep -EHirn "accesskey|admin|aes|api_key|apikey|checkClientTrusted|crypt|http:|https:|password|pinning|secret|SHA256|SharedPreferences|superuser|token|X509TrustManager|insert into" app_name/ --color=auto
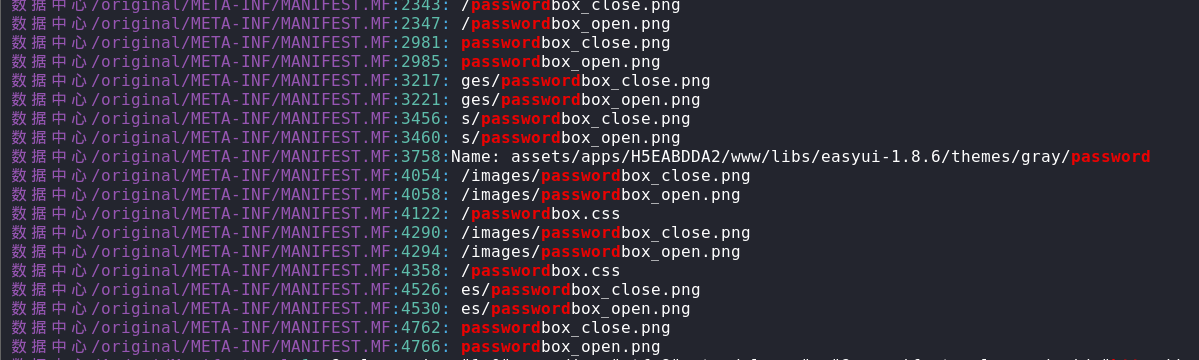
4) 远程提取ZIP文件的内容(针对巨大的网站备份文件)
pip install remotezip# 列出远程zip文件的内容remotezip -l "http://site/bigfile.zip"# 从远程zip文件中提取file.txtremotezip "http://site/bigfile.zip" "file.txt"
remotezip -l “http://47.111.15.14/vulhub-master.zip“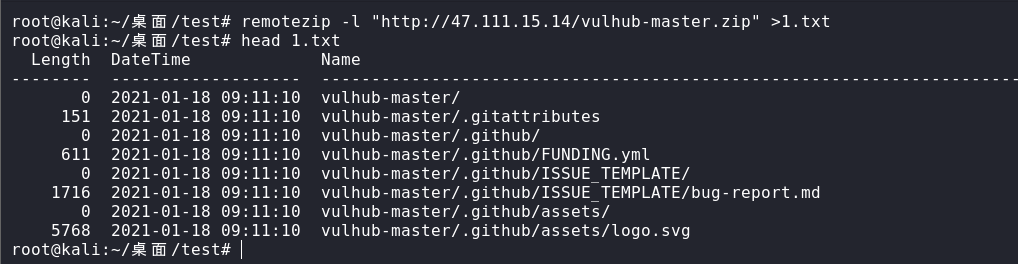
提取指定文件
remotezip “http://47.111.15.14/vulhub-master.zip“ “vulhub-master/zabbix/CVE-2017-2824/exploit.py”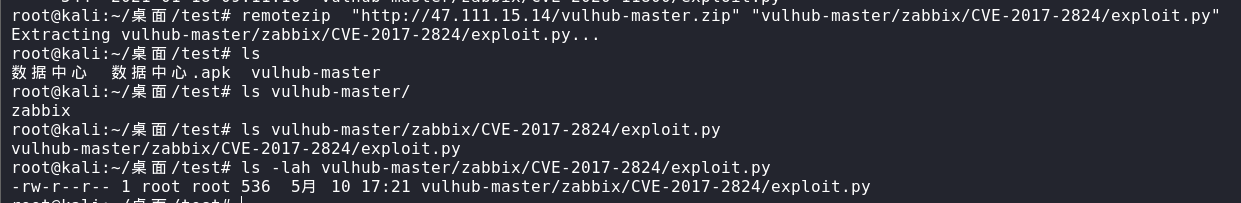
5)开放重定向的常见参数
可以写个脚本批量扫扫
/{payload}?next={payload}?url={payload}?target={payload}?rurl={payload}?dest={payload}?destination={payload}?redir={payload}?redirect_uri={payload}?redirect_url={payload}?redirect={payload}/redirect/{payload}/cgi-bin/redirect.cgi?{payload}/out/{payload}/out?{payload}?view={payload}/login?to={payload}?image_url={payload}?go={payload}?return={payload}?returnTo={payload}?return_to={payload}?checkout_url={payload}?continue={payload}?return_path={payload}
6)快速根据子域名列表判断验证主机名和子域列表
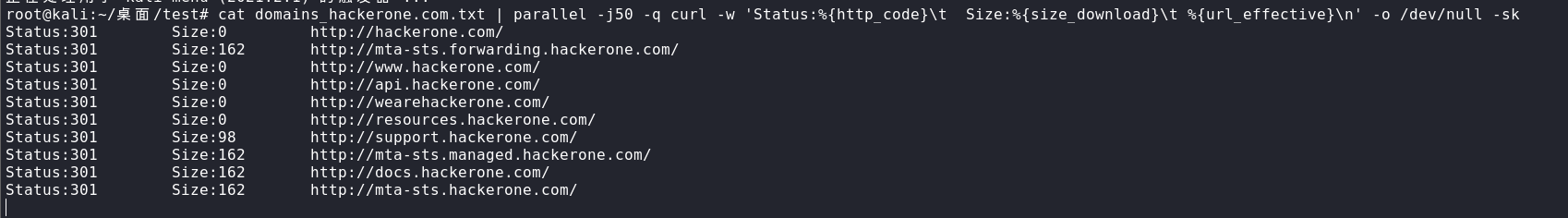
cat domains_hackerone.com.txt | parallel -j50 -q curl -w 'Status:%{http_code}\t Size:%{size_download}\t %{url_effective}\n' -o /dev/null -sk
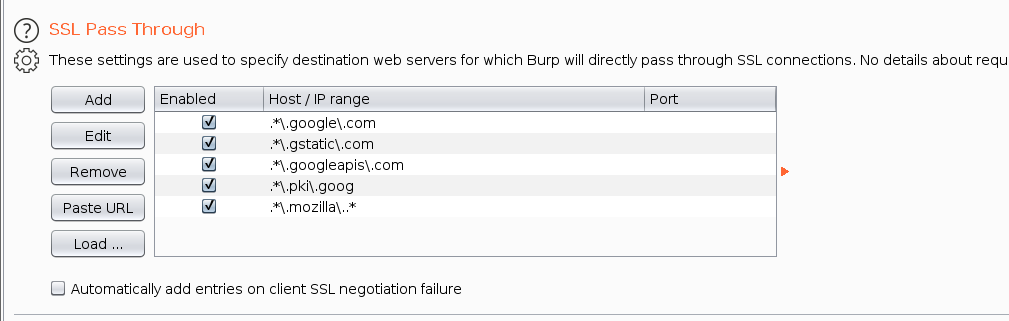
7)快速过滤Burp Suite中的无用信息
这里设置一下过滤,然后就干净了,不会有多余的请求
.*\.google\.com.*\.gstatic\.com.*\.googleapis\.com.*\.pki\.goog.*\.mozilla\..*
特别干净的数据流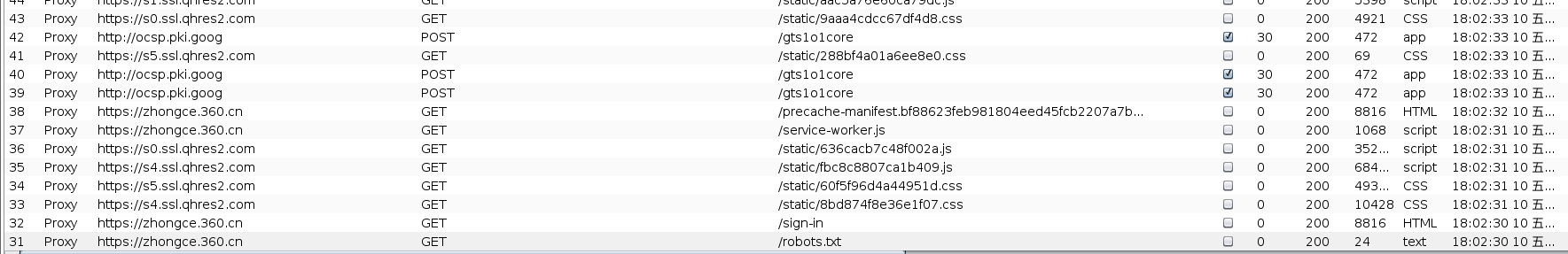
遇到广告之类的可以继续在这里过滤
8)一些邮件处的各种类型的payload
XSS(跨站脚本):
test+(<script>alert(0)</script>)@example.comtest@example(<script>alert(0)</script>).com"<script>alert(0)</script>"@example.com
模板注入:
"<%= 7 * 7 %>"@example.comtest+(${{7*7}})@example.com
SQL注入
"' OR 1=1 -- '"@example.com"mail'); DROP TABLE users;--"@example.com
SSRF(服务器端请求伪造):
john.doe@abc123.burpcollaborator.netjohn.doe@[127.0.0.1]
参数污染:
victim&email=attacker@example.com
(电子邮件)标头注入:
"%0d%0aContent-Length:%200%0d%0a%0d%0a"@example.com"recipient@test.com>\r\nRCPT TO:<victim+"@test.com
9.从员工报价到身份证
通过@silentbronco
来源:链接
注册为员工会导致要求获得“仅限员工私下发售”,并最终获得“身份证”。
这就是@silentbronco所做的完全是:
- 在Google上搜索Target的员工优惠:inurl:“目标名称”员工提供
- 找到了向目标公司提供报价的网站。
- 发现报价仅限于员工。
- 尝试在“ 员工ID ”字段中使用随机数进行注册
- 由于未验证 “ 员工ID ” ,因此成功注册为员工。
- 注册为员工会导致要求私人报价。
- 该网站还提供了“ 身份证 ”,可用于证明我们是目标公司的合法雇员。
下次当您要进入一个组织时,请尝试寻找@silentbronco之类的员工报价。
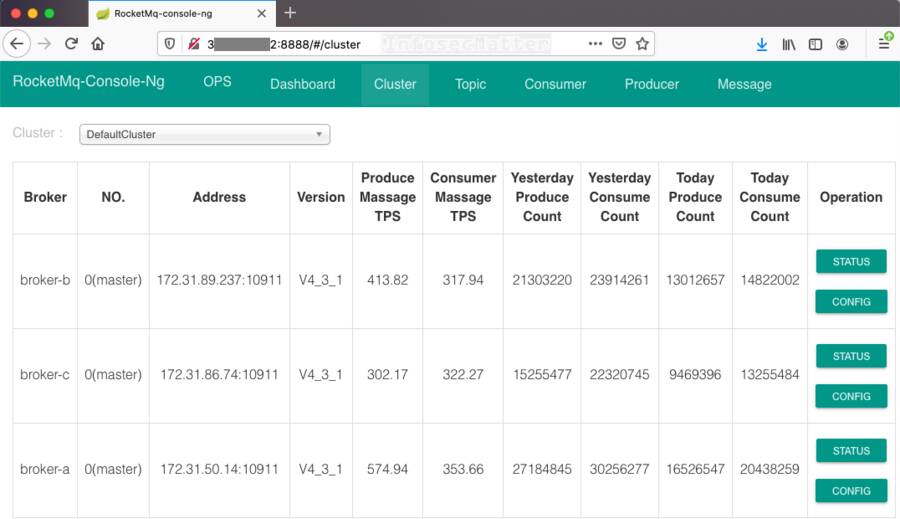
10.使用Shodan查找RocketMQ控制台
RocketMQ控制台,该控制台通常会公开相当机密的生产信息:
org:target.com http.title:rocketmq-console
例如,从公开的RocketMQ控制台中,我们可以找到:
- 其他主机名和子域
- 内部IP地址
- 日志文件位置
- 版本详细信息
11. SSRF绕过技巧
1)使用CIDR绕过SSRF:
http://127.127.127.127http://127.0.0.0
2)使用稀有地址绕行:
http://127.1http://0
3)使用技巧组合绕过:
http://1.1.1.1 &@2.2.2.2# @3.3.3.3/urllib : 3.3.3.3
4)绕过弱解析器:
http://127.1.1.1:80\@127.2.2.2:80/
5)用[::]绕过localhost:
http://[::]:80/http://0000::1:80/
12.关于文件上传的攻击方式
Pixel flood attack 像素泛洪攻击(服务端未验证图片的大小宽高限制,导致可以输入无限大的宽高实现拒绝服务)
https://hackerone.com/reports/390
- ASP / ASPX / PHP5 / PHP / PHP3:Webshell / RCE
- SVG:存储性XSS / SSRF / XXE
- GIF:存储性XSS / SSRF
- CSV:CSV注入
- XML:XXE
- AVI:LFI / SSRF
- HTML / JS:HTML注入/ XSS /重定向
- PNG / JPEG:像素泛洪攻击(DoS)
- ZIP:通过LFI / DoS进行RCE
- PDF / PPTX:SSRF /盲XXE
13.可能存在文件包含的参数
?cat={payload}?dir={payload}?action={payload}?board={payload}?date={payload}?detail={payload}?file={payload}?download={payload}?path={payload}?folder={payload}?prefix={payload}?include={payload}?page={payload}?inc={payload}?locate={payload}?show={payload}?doc={payload}?site={payload}?type={payload}?view={payload}?content={payload}?document={payload}?layout={payload}?mod={payload}?conf={payload}
14.使用AlienVault OTX查找敏感信息(网址关联分析)
curl -s "https://otx.alienvault.com/api/v1/indicators/domain/baidu.com/url_list?limit=100&page=1" | jq
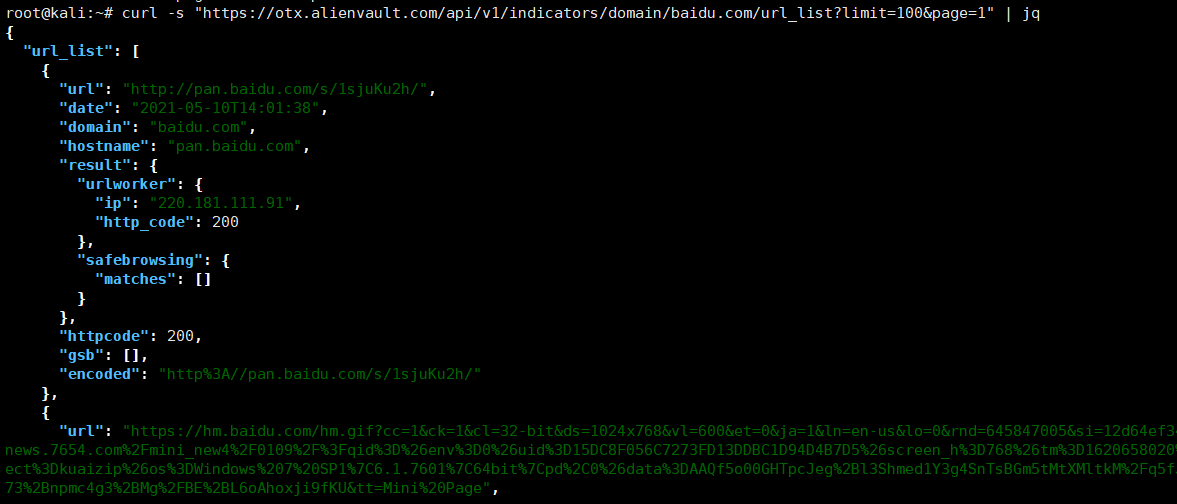
只抓取URL
curl -s "https://otx.alienvault.com/api/v1/indicators/domain/baidu.com/url_list?limit=100&page=1" | jq -r '.url_list[].url'
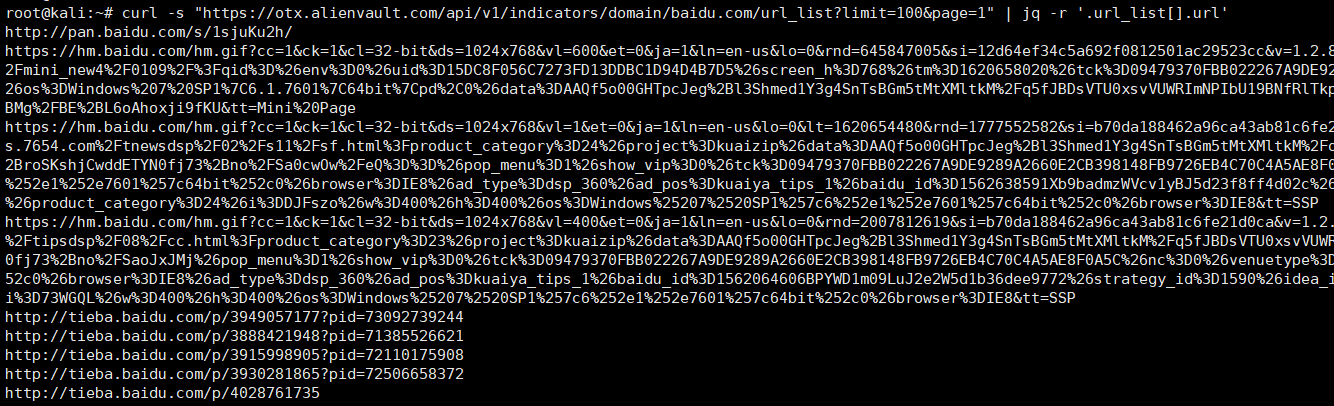
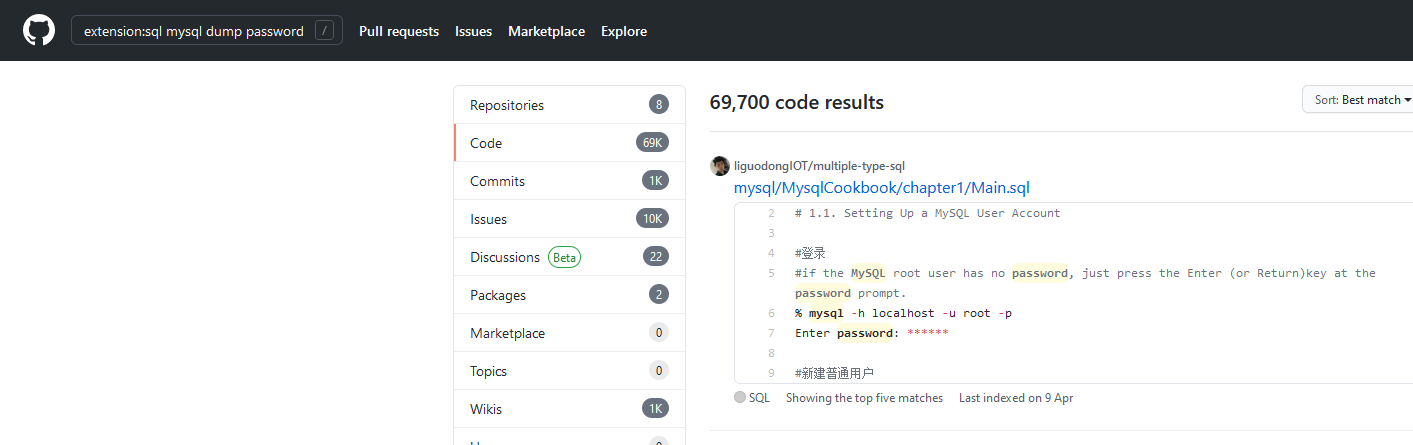
15.Github搜索敏感信息
https://github.com/techgaun/github-dorks
extension:pem privateextension:ppk privateextension:sql mysql dump passwordextension:json api.forecast.ioextension:json mongolab.comextension:yaml mongolab.comextension:ica [WFClient] Password=extension:avastlic "support.avast.com"extension:js jsforce conn.loginextension:json googleusercontent client_secret