1 概述
报文重组是为了处理两种情况. 第一种情况是因为 MTU 等限制, 导致协议数据需要通过多个报文来承载:
另一种情况, 则是有的协议本身定义了分块规则, 导致可能一个报文中也可能有多个数据段:
实际情况中这两种情况是可能混合出现的. 不论是哪种情况, 还是混合, 协议解析程序都必须先正确取得原始的协议数据, 然后才能对它进行正确分析.
2 用户手册中的报文重组
Network protocols often need to transport large chunks of data which are complete in themselves, e.g. when transferring a file. The underlying protocol might not be able to handle that chunk size (e.g. limitation of the network packet size), or is stream-based like TCP, which doesn’t know data chunks at all.
In that case the network protocol has to handle the chunk boundaries itself and (if required) spread the data over multiple packets. It obviously also needs a mechanism to determine the chunk boundaries on the receiving side.
Wireshark calls this mechanism reassembly, although a specific protocol specification might use a different term for this (e.g. desegmentation, defragmentation, etc).
Wireshark是如何处理的
For some of the network protocols Wireshark knows of, a mechanism is implemented to find, decode and display these chunks of data. Wireshark will try to find the corresponding packets of this chunk, and will show the combined data as additional pages in the “Packet Bytes” pane (for information about this pane. See Section 3.20, “The “Packet Bytes” Pane”).
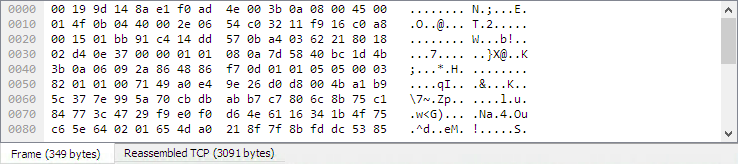
Reassembly might take place at several protocol layers, so it’s possible that multiple tabs in the “Packet Bytes” pane appear.
For example, in a HTTP GET response, the requested data (e.g. an HTML page) is returned. Wireshark will show the hex dump of the data in a new tab “Uncompressed entity body” in the “Packet Bytes” pane.
http_gnu.zip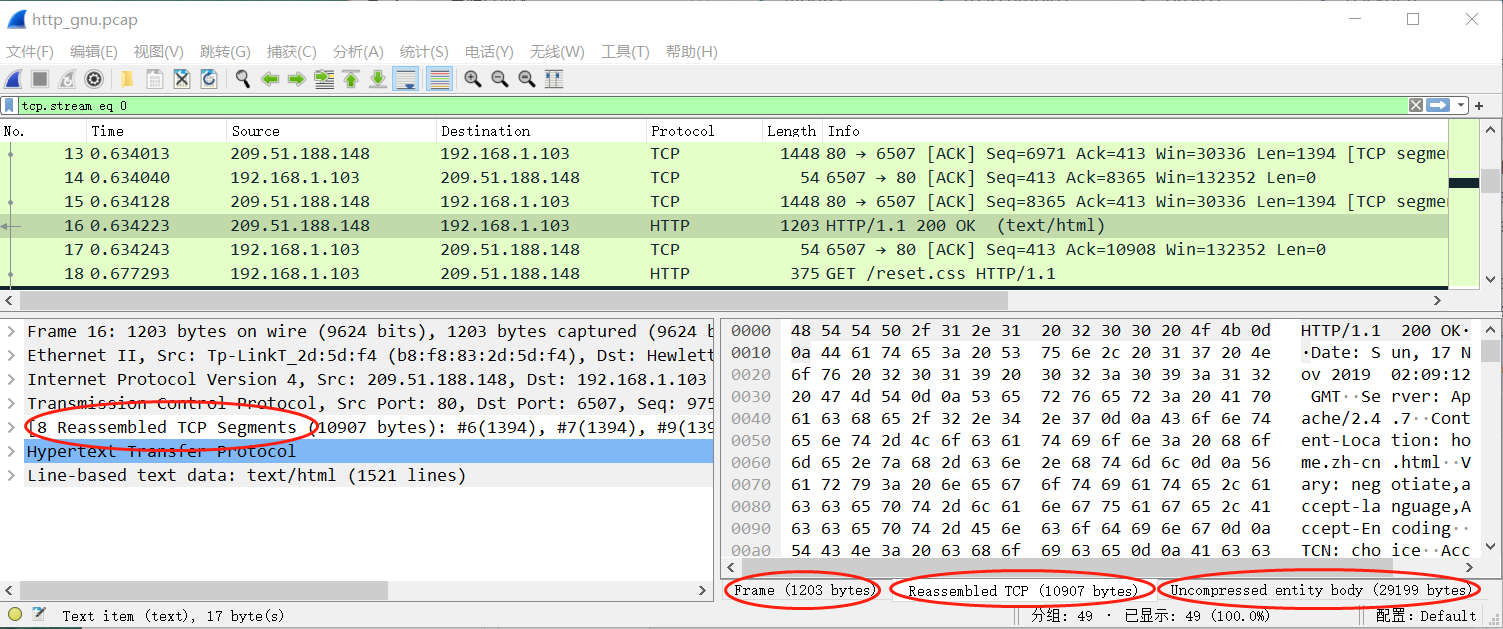
HTTP/1.1 200 OKDate: Sun, 17 Nov 2019 02:09:12 GMTServer: Apache/2.4.7Content-Location: home.zh-cn.htmlVary: negotiate,accept-language,Accept-EncodingTCN: choiceAccess-Control-Allow-Origin: (null)Accept-Ranges: bytesContent-Encoding: gzipCache-Control: max-age=0Expires: Sun, 17 Nov 2019 02:09:12 GMTContent-Length: 10454Keep-Alive: timeout=3, max=100Connection: Keep-AliveContent-Type: text/htmlContent-Language: zh-cn
Reassembly is enabled in the preferences by default but can be disabled in the preferences for the protocol in question. Enabling or disabling reassembly settings for a protocol typically requires two things:
- The lower level protocol (e.g., TCP) must support reassembly. Often this reassembly can be enabled or disabled via the protocol preferences.
- The higher level protocol (e.g., HTTP) must use the reassembly mechanism to reassemble fragmented protocol data. This too can often be enabled or disabled via the protocol preferences.
The tooltip of the higher level protocol setting will notify you if and which lower level protocol setting also has to be considered.
TCP重组
像 HTTP 或 TLS 这样的协议, (协议数据)可能会跨多个 TCP segments. 通过打开 TCP 首选项 “Allow subdissector to reassemble TCP streams”(默认打开) 可以让 Wireshark 收集连续的 TCP segment 然后再把它们交给上层协议(比如, 重组完整的 HTTP 消息). 最终的 segment 在报文列表中会标记为 “[TCP segment of a reassembled PDU]”.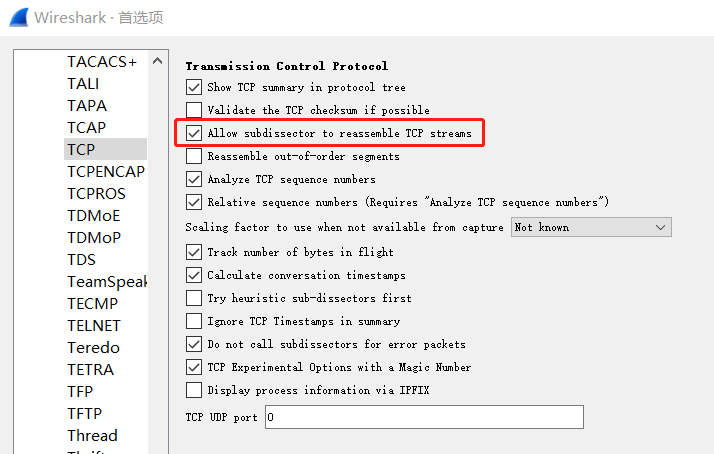
不打开这个选项会减少内存占用和处理开销, 如果你只关心 TCP 序列号分析的话(Section 7.5, “TCP Analysis”). 但记住, 这样的话会导致上层协议解析错误. 例如, HTTP 消息可能显示为”Continuation”, TLS 记录可能会显示为”Ingnored Unknown Record”. 如果在 TCP 连接建立后才开始抓包, 或者某些 TCP segments 丢失或乱序, 这些后果也会产生.
为了重组乱序的 TCP segments, 需要打开 TCP 首选项”Reassemble out-of-order segments”(默认关闭). 若所有的报文都有序接收, 此选项没有影响; 否则, 它假定新的或丢失的 segments 属于同一 PDU. 注意:
- 假定丢失的报文会在之后收到(乱序或重传). 应用程序通常会重传 segment 直到它们被确认, 但如果抓包时丢失了报文, Wireshark 就不能重建 TCP 流了. 在此情况下, 你可以关闭这个选项, 希望使用部分解析而不是对每个 TCP segment 都标上 “[TCP segment of a reassembled PDU]” .
- 当在监听模式下抓包时(IEEE 802.11), 更可能因为信号接收问题而丢包. 这时推荐关闭这个选项.
- 如果新的和丢失的 segments 实际上是不同 PDU 的一部分, 则当前处理会被推迟, 直到拿到所有 segments. 例如, 假定 6 个 segments 组成 2 个 PDUs:
ABC,DEF. 当接收顺序为ABECDF, 程序会在接收到ABEC后开始处理第一个 PDU. 然而 Wireshark 要求丢失的 segmentD也要被接收才行. 此 issue 将在未来解决. - In the GUI and during a two-pass dissection (tshark -2), the previous scenario will display both PDUs in the packet with last segment (F) rather than displaying it in the first packet that has the final missing segment of a PDU. This issue will be addressed in the future.
- When enabled, fields such as the SMB “Time from request” (smb.time) might be smaller if the request follows other out-of-order segments (this reflects application behavior). If the previous scenario however occurs, then the time of the request is based on the frame where all missing segments are received.
不论这两个与重组相关的选项设置如何, 你都可以使用”Follow Protocol Stream“功能, 它会用正确的顺序显示 segments.
3 开发手册中的报文重组
Wireshark 开发手册中的 “9.5 How to reassemble split packets“ 一节讲述了报文重组相关问题, 本文此章领会这部分内容. 另外 Wireshark 源码目录中的 doc/README.dissector 文件的 “2.7 Reassembly/desegmentation for protocols running atop TCP”, “2.8 Using udp_dissect_pdus()” 也讲述了报文重组问题, 请参考原文, 或者我的 Wireshark 文章.
Some protocols have times when they have to split a large packet across multiple other packets. In this case the dissection can’t be carried out correctly until you have all the data. The first packet doesn’t have enough data, and the subsequent packets don’t have the expect format. To dissect these packets you need to wait until all the parts have arrived and then start the dissection.
The following sections will guide you through two common cases. For a description of all possible functions, structures and parameters, see epan/reassemble.h.
如何重组UDP报文
As an example, let’s examine a protocol that is layered on top of UDP that splits up its own data stream. If a packet is bigger than some given size, it will be split into chunks, and somehow signaled within its protocol.
To deal with such streams, we need several things to trigger from. We need to know that this packet is part of a multi-packet sequence. We need to know how many packets are in the sequence. We also need to know when we have all the packets.
For this example we’ll assume there is a simple in-protocol signaling mechanism to give details. A flag byte that signals the presence of a multi-packet sequence and also the last packet, followed by an ID of the sequence and a packet sequence number.
msg_pkt ::= SEQUENCE {.....flags ::= SEQUENCE {fragment BOOLEAN, // 是否分段last_fragment BOOLEAN, // 是否最后一个分段.....}msg_id INTEGER(0..65535), // 完整消息idfrag_id INTEGER(0..65535), // 如果是分段, 表示分段id.....}
重组第一步
#include <epan/reassemble.h>...save_fragmented = pinfo->fragmented;flags = tvb_get_guint8(tvb, offset); offset++;if (flags & FL_FRAGMENT) { /* fragmented */tvbuff_t* new_tvb = NULL;fragment_data *frag_msg = NULL;guint16 msg_seqid = tvb_get_ntohs(tvb, offset); offset += 2;guint16 msg_num = tvb_get_ntohs(tvb, offset); offset += 2;pinfo->fragmented = TRUE;frag_msg = fragment_add_seq_check(msg_reassembly_table,tvb, offset, pinfo,msg_seqid, NULL, /* ID for fragments belonging together */msg_num, /* fragment sequence number */tvb_captured_length_remaining(tvb, offset), /* fragment length - to the end */flags & FL_FRAG_LAST); /* More fragments? */
We start by saving the fragmented state of this packet, so we can restore it later. Next comes some protocol specific stuff, to dig the fragment data out of the stream if it’s present. Having decided it is present, we let the function fragment_add_seq_check() do its work. We need to provide this with a certain amount of parameters:
- The msg_reassembly_table table is for bookkeeping and is described later.The tvb buffer we are dissecting.
- The offset where the partial packet starts.
- The provided packet info.
- The sequence number of the fragment stream. There may be several streams of fragments in flight, and this is used to key the relevant one to be used for reassembly.
- Optional additional data for identifying the fragment. Can be set to NULL (as is done in the example) for most dissectors.
- msg_num is the packet number within the sequence.
- The length here is specified as the rest of the tvb as we want the rest of the packet data.
- Finally a parameter that signals if this is the last fragment or not. This might be a flag as in this case, or there may be a counter in the protocol.
重组第二步
new_tvb = process_reassembled_data(tvb, offset, pinfo,"Reassembled Message", frag_msg, &msg_frag_items,NULL, msg_tree);if (frag_msg) { /* Reassembled */col_append_str(pinfo->cinfo, COL_INFO," (Message Reassembled)");} else { /* Not last packet of reassembled Short Message */col_append_fstr(pinfo->cinfo, COL_INFO," (Message fragment %u)", msg_num);}if (new_tvb) { /* take it all */next_tvb = new_tvb;} else { /* make a new subset */next_tvb = tvb_new_subset_remaining(tvb, offset);}}else { /* Not fragmented */next_tvb = tvb_new_subset_remaining(tvb, offset);}.....pinfo->fragmented = save_fragmented;
Having passed the fragment data to the reassembly handler, we can now check if we have the whole message. If there is enough information, this routine will return the newly reassembled data buffer.
After that, we add a couple of informative messages to the display to show that this is part of a sequence. Then a bit of manipulation of the buffers and the dissection can proceed. Normally you will probably not bother dissecting further unless the fragments have been reassembled as there won’t be much to find. Sometimes the first packet in the sequence can be partially decoded though if you wish.
Now the mysterious data we passed into the fragment_add_seq_check().
重组初始化
static reassembly_table reassembly_table;static voidproto_register_msg(void){reassembly_table_register(&msg_reassemble_table,&addresses_ports_reassembly_table_functions);}
First a reassembly_tablestructure is declared and initialised in the protocol initialisation routine. The second parameter specifies the functions that should be used for identifying fragments. We will use addresses_ports_reassembly_table_functions in order to identify fragments by the given sequence number (msg_seqid), the source and destination addresses and ports from the packet.
Following that, a fragment_items structure is allocated and filled in with a series of ett items, hf data items, and a string tag. The ett and hf values should be included in the relevant tables like all the other variables your protocol may use. The hf variables need to be placed in the structure something like the following. Of course the names may need to be adjusted.
重组数据
...static int hf_msg_fragments = -1;static int hf_msg_fragment = -1;static int hf_msg_fragment_overlap = -1;static int hf_msg_fragment_overlap_conflicts = -1;static int hf_msg_fragment_multiple_tails = -1;static int hf_msg_fragment_too_long_fragment = -1;static int hf_msg_fragment_error = -1;static int hf_msg_fragment_count = -1;static int hf_msg_reassembled_in = -1;static int hf_msg_reassembled_length = -1;...static gint ett_msg_fragment = -1;static gint ett_msg_fragments = -1;...static const fragment_items msg_frag_items = {/* Fragment subtrees */&ett_msg_fragment,&ett_msg_fragments,/* Fragment fields */&hf_msg_fragments,&hf_msg_fragment,&hf_msg_fragment_overlap,&hf_msg_fragment_overlap_conflicts,&hf_msg_fragment_multiple_tails,&hf_msg_fragment_too_long_fragment,&hf_msg_fragment_error,&hf_msg_fragment_count,/* Reassembled in field */&hf_msg_reassembled_in,/* Reassembled length field */&hf_msg_reassembled_length,/* Tag */"Message fragments"};...static hf_register_info hf[] ={...{&hf_msg_fragments,{"Message fragments", "msg.fragments",FT_NONE, BASE_NONE, NULL, 0x00, NULL, HFILL } },{&hf_msg_fragment,{"Message fragment", "msg.fragment",FT_FRAMENUM, BASE_NONE, NULL, 0x00, NULL, HFILL } },{&hf_msg_fragment_overlap,{"Message fragment overlap", "msg.fragment.overlap",FT_BOOLEAN, 0, NULL, 0x00, NULL, HFILL } },{&hf_msg_fragment_overlap_conflicts,{"Message fragment overlapping with conflicting data","msg.fragment.overlap.conflicts",FT_BOOLEAN, 0, NULL, 0x00, NULL, HFILL } },{&hf_msg_fragment_multiple_tails,{"Message has multiple tail fragments","msg.fragment.multiple_tails",FT_BOOLEAN, 0, NULL, 0x00, NULL, HFILL } },{&hf_msg_fragment_too_long_fragment,{"Message fragment too long", "msg.fragment.too_long_fragment",FT_BOOLEAN, 0, NULL, 0x00, NULL, HFILL } },{&hf_msg_fragment_error,{"Message defragmentation error", "msg.fragment.error",FT_FRAMENUM, BASE_NONE, NULL, 0x00, NULL, HFILL } },{&hf_msg_fragment_count,{"Message fragment count", "msg.fragment.count",FT_UINT32, BASE_DEC, NULL, 0x00, NULL, HFILL } },{&hf_msg_reassembled_in,{"Reassembled in", "msg.reassembled.in",FT_FRAMENUM, BASE_NONE, NULL, 0x00, NULL, HFILL } },{&hf_msg_reassembled_length,{"Reassembled length", "msg.reassembled.length",FT_UINT32, BASE_DEC, NULL, 0x00, NULL, HFILL } },...static gint *ett[] ={...&ett_msg_fragment,&ett_msg_fragments...
These hf variables are used internally within the reassembly routines to make useful links, and to add data to the dissection. It produces links from one packet to another, such as a partial packet having a link to the fully reassembled packet. Likewise there are back pointers to the individual packets from the reassembled one. The other variables are used for flagging up errors.
如何重组TCP报文
A dissector gets a tvbuff_t pointer which holds the payload of a TCP packet. This payload contains the header and data of your application layer protocol.
When dissecting an application layer protocol you cannot assume that each TCP packet contains exactly one application layer message. One application layer message can be split into several TCP packets.
You also cannot assume that a TCP packet contains only one application layer message and that the message header is at the start of your TCP payload. More than one messages can be transmitted in one TCP packet, so that a message can start at an arbitrary position.
This sounds complicated, but there is a simple solution. tcp_dissect_pdus() does all this tcp packet reassembling for you. This function is implemented in epan/dissectors/packet-tcp.h.
// epan/dissectors/packet-tcp.h/** Loop for dissecting PDUs within a TCP stream; assumes that a PDU* consists of a fixed-length chunk of data that contains enough information* to determine the length of the PDU, followed by rest of the PDU.** The first three arguments are the arguments passed to the dissector* that calls this routine.** "proto_desegment" is the dissector's flag controlling whether it should* desegment PDUs that cross TCP segment boundaries.** "fixed_len" is the length of the fixed-length part of the PDU.** "get_pdu_len()" is a routine called to get the length of the PDU from* the fixed-length part of the PDU; it's passed "pinfo", "tvb", "offset" and* "dissector_data".** "dissect_pdu()" is the routine to dissect a PDU.*/WS_DLL_PUBLIC voidtcp_dissect_pdus(tvbuff_t *tvb, packet_info *pinfo, proto_tree *tree,gboolean proto_desegment, guint fixed_len,guint (*get_pdu_len)(packet_info *, tvbuff_t *, int, void*),dissector_t dissect_pdu, void* dissector_data);
重组 TCP fragments
#include "config.h"#include <epan/packet.h>#include <epan/prefs.h>#include "packet-tcp.h"...#define FRAME_HEADER_LEN 8/* This method dissects fully reassembled messages */static intdissect_foo_message(tvbuff_t *tvb, packet_info *pinfo _U_, proto_tree *tree _U_, void *data _U_){/* TODO: implement your dissecting code */return tvb_captured_length(tvb);}/* determine PDU length of protocol foo */static guintget_foo_message_len(packet_info *pinfo _U_, tvbuff_t *tvb, int offset, void *data _U_){/* TODO: change this to your needs */return (guint)tvb_get_ntohl(tvb, offset+4); /* e.g. length is at offset 4 */}/* The main dissecting routine */static intdissect_foo(tvbuff_t *tvb, packet_info *pinfo, proto_tree *tree, void *data){tcp_dissect_pdus(tvb, pinfo, tree, TRUE, FRAME_HEADER_LEN,get_foo_message_len, dissect_foo_message, data);return tvb_captured_length(tvb);}
As you can see this is really simple. Just call tcp_dissect_pdus() in your main dissection routine and move you message parsing code into another function. This function gets called whenever a message has been reassembled.
The parameters tvb, pinfo, tree and data are just handed over to tcp_dissect_pdus(). The 4th parameter is a flag to indicate if the data should be reassembled or not. This could be set according to a dissector preference as well. Parameter 5 indicates how much data has at least to be available to be able to determine the length of the foo message. Parameter 6 is a function pointer to a method that returns this length. It gets called when at least the number of bytes given in the previous parameter is available. Parameter 7 is a function pointer to your real message dissector. Parameter 8 is the data passed in from parent dissector.
Protocols which need more data before the message length can be determined can return zero. Other values smaller than the fixed length will result in an exception.
4 通用重组框架
5 IP重组
6 TCP重组
7 源码分析
通用重组框架
分片
typedef struct _fragment_item {struct _fragment_item *next;guint32 frame; /* XXX - does this apply to reassembly heads? */guint32 offset; /* XXX - does this apply to reassembly heads? */guint32 len; /* XXX - does this apply to reassembly heads? */guint32 fragment_nr_offset; /**< offset for frame numbering, for sequences, where the* provided fragment number of the first fragment does* not start with 0* XXX - does this apply only to reassembly heads? */guint32 datalen; /**< When flags&FD_BLOCKSEQUENCE is set, the* index of the last block (segments in* datagram + 1); otherwise the number of* bytes of the full datagram. Only valid in* the first item of the fragments list when* flags&FD_DATALEN is set.*/guint32 reassembled_in; /**< frame where this PDU was reassembled,* only valid in the first item of the list* and when FD_DEFRAGMENTED is set*/guint8 reas_in_layer_num; /**< The current "depth" or layer number in the current frame where reassembly was completed.* Example: in SCTP there can be several data chunks and we want the reassemblied tvb for the final* segment only. */guint32 flags; /**< XXX - do some of these apply only to reassembly* heads and others only to fragments within* a reassembly? */tvbuff_t *tvb_data;/*** Null if the reassembly had no error; non-null if it had* an error, in which case it's the string for the error.** XXX - this is wasted in all but the reassembly head; we* should probably have separate data structures for a* reassembly and for the fragments in a reassembly.*/const char *error;} fragment_item, fragment_head;
重组表
/** Data structure to keep track of fragments and reassemblies.*/typedef struct {GHashTable *fragment_table;GHashTable *reassembled_table;fragment_temporary_key temporary_key_func;fragment_persistent_key persistent_key_func;GDestroyNotify free_temporary_key_func; /* temporary key destruction function */} reassembly_table;
重组表函数
/** Table of functions for a reassembly table.*/typedef struct {/* Functions for fragment table */GHashFunc hash_func; /* hash function */GEqualFunc equal_func; /* comparison function */fragment_temporary_key temporary_key_func; /* temporary key creation function */fragment_persistent_key persistent_key_func; /* persistent key creation function */GDestroyNotify free_temporary_key_func; /* temporary key destruction function */GDestroyNotify free_persistent_key_func; /* persistent key destruction function */} reassembly_table_functions;
用于重组表中的分片哈希表的相关函数. glib 的哈希表支持提供 2 个函数, 用于在删除结点时释放 key 和 value 的内存:
GHashTable *g_hash_table_new_full (GHashFunc hash_func,GEqualFunc key_equal_func,GDestroyNotify key_destroy_func,GDestroyNotify value_destroy_func);
所以 reassembly_table_functions中的 free_persistent_key_func 用于删除分片哈希表中的 key.
Wireshark 已提供 2 个函数, 分别用于 3 元组和 5 元组哈希 key:
/** Tables of functions exported for the benefit of dissectors that* don't need special items in their keys.*/WS_DLL_PUBLIC const reassembly_table_functionsaddresses_reassembly_table_functions; /* keys have endpoint addresses and an ID */WS_DLL_PUBLIC const reassembly_table_functionsaddresses_ports_reassembly_table_functions; /* keys have endpoint addresses and ports and an ID */
对应 3 元组和 5 元组:
/** Functions for reassembly tables where the endpoint addresses, and a* fragment ID, are used as the key.*/typedef struct _fragment_addresses_key {address src;address dst;guint32 id;} fragment_addresses_key;/** Functions for reassembly tables where the endpoint addresses and ports,* and a fragment ID, are used as the key.*/typedef struct _fragment_addresses_ports_key {address src_addr;address dst_addr;guint32 src_port;guint32 dst_port;guint32 id;} fragment_addresses_ports_key;
而用于已重组哈希表的 key 不同, 比较简单:
typedef struct _reassembled_key {guint32 id;guint32 frame;} reassembled_key;
重组表注册
/** Register a reassembly table. By registering the table with epan, the creation and* destruction of the table can be managed by epan and not the dissector.*/WS_DLL_PUBLIC voidreassembly_table_register(reassembly_table *table,const reassembly_table_functions *funcs){register_reassembly_table_t* reg_table;...reg_table = g_new(register_reassembly_table_t,1);reg_table->table = table;reg_table->funcs = funcs;reassembly_table_list = g_list_prepend(reassembly_table_list, reg_table);}
需要重组功能的协议调用此接口注册重组表. 注册时生成下面的重组表注册数据结构, 并将其添加到全局链表 reassembly_table_list 中:
typedef struct register_reassembly_table {reassembly_table *table;const reassembly_table_functions *funcs;} register_reassembly_table_t;GList* reassembly_table_list = NULL;
重组表初始化
Wireshark 初始化时 (通过 epan_init(), 整个协议解析模块的初始化函数), 会调用以下函数初始化已注册的重组表:
/* Initialize internal structures*/void reassembly_tables_init(void){register_init_routine(&reassembly_table_init_reg_tables);register_cleanup_routine(&reassembly_table_cleanup_reg_tables);}
会将重组哈希表的初始化与清理函数挂接到全局初始化与清理链表中.
其中初始化就是对全局重组链表中的每一项调用 reassembly_table_init函数:
/** Initialize/destroy a reassembly table.** init: If table doesn't exist: create table;* else: just remove any entries;* destroy: remove entries and destroy table;*/WS_DLL_PUBLIC voidreassembly_table_init(reassembly_table *table,const reassembly_table_functions *funcs);
主要动作是创建 2 个哈希表, 即分片表和重组表:
table->fragment_table = g_hash_table_new_full(funcs->hash_func,funcs->equal_func, funcs->free_persistent_key_func, NULL);...table->reassembled_table = g_hash_table_new_full(reassembled_hash,reassembled_equal, reassembled_key_free, NULL);
这里也可以看到已重组表的删除 key 函数与分片表不同(reassembled_key_free).
清理函数则最终会调用 reassembly_table_destroy 释放资源.
WS_DLL_PUBLIC voidreassembly_table_destroy(reassembly_table *table);
添加分片
/** This function adds a new fragment to the reassembly table* If this is the first fragment seen for this datagram, a new entry* is created in the table, otherwise this fragment is just added* to the linked list of fragments for this packet.* The list of fragments for a specific datagram is kept sorted for* easier handling.** Datagrams (messages) are identified by a key generated by* fragment_temporary_key or fragment_persistent_key, based on the "pinfo", "id"* and "data" pairs. (This is the sole purpose of "data".)** Fragments are identified by "frag_offset".** Returns a pointer to the head of the fragment data list if we have all the* fragments, NULL otherwise. Note that the reassembled fragments list may have* a non-zero fragment offset, the only guarantee is that no gaps exist within* the list.*/WS_DLL_PUBLIC fragment_head *fragment_add(reassembly_table *table, tvbuff_t *tvb, const int offset,const packet_info *pinfo, const guint32 id, const void *data,const guint32 frag_offset, const guint32 frag_data_len,const gboolean more_frags);
添加分片有多个函数变种, 其中一些会调用到 fragment_add_common 函数.
// epan/reassemble.cstatic fragment_head *fragment_add_common(reassembly_table *table, tvbuff_t *tvb, const int offset,const packet_info *pinfo, const guint32 id,const void *data, const guint32 frag_offset,const guint32 frag_data_len, const gboolean more_frags,const gboolean check_already_added){fragment_head *fd_head;fragment_item *fd_item;gboolean already_added;/** Dissector shouldn't give us garbage tvb info.** XXX - should this code take responsibility for preventing* reassembly if data is missing due to the packets being* sliced, rather than leaving it up to dissectors?*/DISSECTOR_ASSERT(tvb_bytes_exist(tvb, offset, frag_data_len));/* key的产生与查表fragment_temporary_key() lookup()(pinfo, id, data) -------------------------> key -----------> fragment_headfragment_table -->*/fd_head = lookup_fd_head(table, pinfo, id, data, NULL);...// 检查当前报文是否已经处理过了. 如果检查发现此分片已经在分片表中, 则无动作/** Is this the first pass through the capture?*/if (!pinfo->fd->visited) {/** Yes, so we could be doing reassembly. If* "check_already_added" is true, and fd_head is non-null,* meaning that this fragment would be added to an* in-progress reassembly, check if we have seen this* fragment before, i.e., if we have already added it to* that reassembly. That can be true even on the first pass* since we sometimes might call a subdissector multiple* times.** We check both the frame number and the fragment offset,* so that we support multiple fragments from the same* frame being added to the same reassembled PDU.*/if (check_already_added && fd_head != NULL) {/** fd_head->frame is the maximum of the frame* numbers of all the fragments added to this* reassembly; if this frame is later than that* frame, we know it hasn't been added yet.*/if (pinfo->num <= fd_head->frame) {already_added = FALSE;/** The first item in the reassembly list* is not a fragment, it's a data structure* for the reassembled packet, so we* start checking with the next item.*/for (fd_item = fd_head->next; fd_item;fd_item = fd_item->next) {if (pinfo->num == fd_item->frame &&frag_offset == fd_item->offset) {already_added = TRUE;break;}}if (already_added) {/** Have we already finished* reassembling?*/if (fd_head->flags & FD_DEFRAGMENTED) {/** Yes.* XXX - can this ever happen?*/THROW_MESSAGE(ReassemblyError,"Frame already added in first pass");} else {/** No.*/return NULL;}}}}} else {*//** No, so we've already done all the reassembly and added* all the fragments. Do we have a reassembly and, if so,* have we finished reassembling?*/if (fd_head != NULL && fd_head->flags & FD_DEFRAGMENTED) {// FD_DEFRAGMENTED 表示之前已经重组过, 这时需要检查一些特殊情况/** Yes. This is probably being done after the* first pass, and we've already done the work* on the first pass.** If the reassembly got a fatal error, throw that* error again.*/if (fd_head->error)THROW_MESSAGE(ReassemblyError, fd_head->error);/** Is it later in the capture than all of the* fragments in the reassembly?*/if (pinfo->num > fd_head->frame) {/** Yes, so report this as a problem,* possibly a retransmission.*/THROW_MESSAGE(ReassemblyError, "New fragment overlaps old data (retransmission?)");}/** Does this fragment go past the end of the* results of that reassembly?*/if (frag_offset + frag_data_len > fd_head->datalen) {/** Yes.*/if (frag_offset >= fd_head->datalen) {/** The fragment starts past the* end of the reassembled data.*/THROW_MESSAGE(ReassemblyError, "New fragment past old data limits");} else {/** The fragment starts before the end* of the reassembled data, but* runs past the end. That could* just be a retransmission.*/THROW_MESSAGE(ReassemblyError, "New fragment overlaps old data (retransmission?)");}}return fd_head;} else {/** No.*/return NULL;}}// 正常流程// 如果是第一个分片, 则创建新的分片链表头, 把它加到分片哈希表if (fd_head==NULL){/* not found, this must be the first snooped fragment for this* packet. Create list-head.*/fd_head = new_head(0);/** Insert it into the hash table.*/insert_fd_head(table, fd_head, pinfo, id, data);}// fragment_add_work()真正处理分片添加if (fragment_add_work(fd_head, tvb, offset, pinfo, frag_offset,frag_data_len, more_frags)) {/** Reassembly is complete.*/return fd_head;} else {/** Reassembly isn't complete.*/return NULL;}}
fragment_add_work():
// epan/reassemble.c/** This function adds a new fragment to the fragment hash table.* If this is the first fragment seen for this datagram, a new entry* is created in the hash table, otherwise this fragment is just added* to the linked list of fragments for this packet.* The list of fragments for a specific datagram is kept sorted for* easier handling.** Returns a pointer to the head of the fragment data list if we have all the* fragments, NULL otherwise.** This function assumes frag_offset being a byte offset into the defragment* packet.** 01-2002* Once the fh is defragmented (= FD_DEFRAGMENTED set), it can be* extended using the FD_PARTIAL_REASSEMBLY flag. This flag should be set* using fragment_set_partial_reassembly() before calling fragment_add* with the new fragment. FD_TOOLONGFRAGMENT and FD_MULTIPLETAILS flags* are lowered when a new extension process is started.*/static gbooleanfragment_add_work(fragment_head *fd_head, tvbuff_t *tvb, const int offset,const packet_info *pinfo, const guint32 frag_offset,const guint32 frag_data_len, const gboolean more_frags){fragment_item *fd;fragment_item *fd_i;guint32 max, dfpos, fraglen;tvbuff_t *old_tvb_data;guint8 *data;/* create new fd describing this fragment */fd = g_slice_new(fragment_item);fd->next = NULL;fd->flags = 0;fd->frame = pinfo->num;fd->offset = frag_offset;fd->fragment_nr_offset = 0; /* will only be used with sequence */fd->len = frag_data_len;fd->tvb_data = NULL;fd->error = NULL;// 检查是否已经重组过, 非正常流程/** Are we adding to an already-completed reassembly?*/if (fd_head->flags & FD_DEFRAGMENTED) {...}// 设置帧序号, 重组链表头节点中的序号是最大序号/* Do this after we may have bailed out (above) so that we don't leave* fd_head->frame in a bad state if we do */if (fd->frame > fd_head->frame)fd_head->frame = fd->frame;// 没有更多分片, 即当前分片是最后一个分片if (!more_frags) {/** This is the tail fragment in the sequence.*/if (fd_head->flags & FD_DATALEN_SET) {/* ok we have already seen other tails for this packet* it might be a duplicate.*/if (fd_head->datalen != (fd->offset + fd->len) ){/* Oops, this tail indicates a different packet* len than the previous ones. Something's wrong.*/fd->flags |= FD_MULTIPLETAILS;fd_head->flags |= FD_MULTIPLETAILS;}} else {// 如果是正常的最后一个分片, 需要设置分片数据总长度, 并设置FD_DATALEN_SET/* This was the first tail fragment; now we know* what the length of the packet should be.*/fd_head->datalen = fd->offset + fd->len;fd_head->flags |= FD_DATALEN_SET;}}/* If the packet is already defragmented, this MUST be an overlap.* The entire defragmented packet is in fd_head->data.* Even if we have previously defragmented this packet, we still* check it. Someone might play overlap and TTL games.*/if (fd_head->flags & FD_DEFRAGMENTED) {.../* it was just an overlap, link it and return */LINK_FRAG(fd_head,fd);return TRUE;}/* If we have reached this point, the packet is not defragmented yet.* Save all payload in a buffer until we can defragment.*/if (!tvb_bytes_exist(tvb, offset, fd->len)) {g_slice_free(fragment_item, fd);THROW(BoundsError);}// 正常流程, 创建一个clone tvb. 分片添加到链表fd->tvb_data = tvb_clone_offset_len(tvb, offset, fd->len);LINK_FRAG(fd_head,fd);if( !(fd_head->flags & FD_DATALEN_SET) ){/* if we don't know the datalen, there are still missing* packets. Cheaper than the check below.*/return FALSE;}/** Check if we have received the entire fragment.* This is easy since the list is sorted and the head is faked.** First, we compute the amount of contiguous data that's* available. (The check for fd_i->offset <= max rules out* fragments that don't start before or at the end of the* previous fragment, i.e. fragments that have a gap between* them and the previous fragment.)*/max = 0;for (fd_i=fd_head->next;fd_i;fd_i=fd_i->next) {if ( ((fd_i->offset)<=max) &&((fd_i->offset+fd_i->len)>max) ){max = fd_i->offset+fd_i->len;}}if (max < (fd_head->datalen)) {/** The amount of contiguous data we have is less than the* amount of data we're trying to reassemble, so we haven't* received all packets yet.*/return FALSE;}// 收到完整数据, 分配一块大的内存, 把每个分片的数据拷贝到其中/* we have received an entire packet, defragment it and* free all fragments*//* store old data just in case */old_tvb_data=fd_head->tvb_data;data = (guint8 *) g_malloc(fd_head->datalen);fd_head->tvb_data = tvb_new_real_data(data, fd_head->datalen, fd_head->datalen);tvb_set_free_cb(fd_head->tvb_data, g_free);/* add all data fragments */for (dfpos=0,fd_i=fd_head;fd_i;fd_i=fd_i->next) {if (fd_i->len) {/** The loop above that calculates max also* ensures that the only gaps that exist here* are ones where a fragment starts past the* end of the reassembled datagram, and there's* a gap between the previous fragment and* that fragment.** A "DESEGMENT_UNTIL_FIN" was involved wherein the* FIN packet had an offset less than the highest* fragment offset seen. [Seen from a fuzz-test:* bug #2470]).** Note that the "overlap" compare must only be* done for fragments with (offset+len) <= fd_head->datalen* and thus within the newly g_malloc'd buffer.*/if (fd_i->offset + fd_i->len > dfpos) {if (fd_i->offset >= fd_head->datalen) {/** Fragment starts after the end* of the reassembled packet.** This can happen if the length was* set after the offending fragment* was added to the reassembly.** Flag this fragment, but don't* try to extract any data from* it, as there's no place to put* it.** XXX - add different flag value* for this.*/fd_i->flags |= FD_TOOLONGFRAGMENT;fd_head->flags |= FD_TOOLONGFRAGMENT;} else if (dfpos < fd_i->offset) {/** XXX - can this happen? We've* already rejected fragments that* start past the end of the* reassembled datagram, and* the loop that calculated max* should have ruled out gaps,* but could fd_i->offset +* fd_i->len overflow?*/fd_head->error = "dfpos < offset";} else if (dfpos - fd_i->offset > fd_i->len)fd_head->error = "dfpos - offset > len";else if (!fd_i->tvb_data)fd_head->error = "no data";else {fraglen = fd_i->len;if (fd_i->offset + fraglen > fd_head->datalen) {/** Fragment goes past the end* of the packet, as indicated* by the last fragment.** This can happen if the* length was set after the* offending fragment was* added to the reassembly.** Mark it as such, and only* copy from it what fits in* the packet.*/fd_i->flags |= FD_TOOLONGFRAGMENT;fd_head->flags |= FD_TOOLONGFRAGMENT;fraglen = fd_head->datalen - fd_i->offset;}if (fd_i->offset < dfpos) {guint32 cmp_len = MIN(fd_i->len,(dfpos-fd_i->offset));fd_i->flags |= FD_OVERLAP;fd_head->flags |= FD_OVERLAP;if ( memcmp(data + fd_i->offset,tvb_get_ptr(fd_i->tvb_data, 0, cmp_len),cmp_len)) {fd_i->flags |= FD_OVERLAPCONFLICT;fd_head->flags |= FD_OVERLAPCONFLICT;}}if (fraglen < dfpos - fd_i->offset) {/** XXX - can this happen?*/fd_head->error = "fraglen < dfpos - offset";} else {memcpy(data+dfpos,tvb_get_ptr(fd_i->tvb_data, (dfpos-fd_i->offset), fraglen-(dfpos-fd_i->offset)),fraglen-(dfpos-fd_i->offset));dfpos=MAX(dfpos, (fd_i->offset + fraglen));}}} else {if (fd_i->offset + fd_i->len < fd_i->offset) {/* Integer overflow? */fd_head->error = "offset + len < offset";}}if (fd_i->flags & FD_SUBSET_TVB)fd_i->flags &= ~FD_SUBSET_TVB;else if (fd_i->tvb_data)tvb_free(fd_i->tvb_data);fd_i->tvb_data=NULL;}}if (old_tvb_data)tvb_add_to_chain(tvb, old_tvb_data);/* mark this packet as defragmented.allows us to skip any trailing fragments */fd_head->flags |= FD_DEFRAGMENTED;fd_head->reassembled_in=pinfo->num;fd_head->reas_in_layer_num = pinfo->curr_layer_num;/* we don't throw until here to avoid leaking old_data and others */if (fd_head->error) {THROW_MESSAGE(ReassemblyError, fd_head->error);}return TRUE;}
处理分片
/** Process reassembled data; if we're on the frame in which the data* was reassembled, put the fragment information into the protocol* tree, and construct a tvbuff with the reassembled data, otherwise* just put a "reassembled in" item into the protocol tree.*/tvbuff_t *process_reassembled_data(tvbuff_t *tvb, const int offset, packet_info *pinfo,const char *name, fragment_head *fd_head, const fragment_items *fit,gboolean *update_col_infop, proto_tree *tree){tvbuff_t *next_tvb;gboolean update_col_info;proto_item *frag_tree_item;if (fd_head != NULL && pinfo->num == fd_head->reassembled_in && pinfo->curr_layer_num == fd_head->reas_in_layer_num) {/** OK, we've reassembled this.* Is this something that's been reassembled from more* than one fragment?*/if (fd_head->next != NULL) {/** Yes.* Allocate a new tvbuff, referring to the* reassembled payload, and set* the tvbuff to the list of tvbuffs to which* the tvbuff we were handed refers, so it'll get* cleaned up when that tvbuff is cleaned up.*/next_tvb = tvb_new_chain(tvb, fd_head->tvb_data);/* Add the defragmented data to the data source list. */add_new_data_source(pinfo, next_tvb, name);/* show all fragments */if (fd_head->flags & FD_BLOCKSEQUENCE) {update_col_info = !show_fragment_seq_tree(fd_head, fit, tree, pinfo, next_tvb, &frag_tree_item);} else {update_col_info = !show_fragment_tree(fd_head,fit, tree, pinfo, next_tvb, &frag_tree_item);}} else {/** No.* Return a tvbuff with the payload.*/next_tvb = tvb_new_subset_remaining(tvb, offset);pinfo->fragmented = FALSE; /* one-fragment packet */update_col_info = TRUE;}if (update_col_infop != NULL)*update_col_infop = update_col_info;} else {/** We don't have the complete reassembled payload, or this* isn't the final frame of that payload.*/next_tvb = NULL;/** If we know what frame this was reassembled in,* and if there's a field to use for the number of* the frame in which the packet was reassembled,* add it to the protocol tree.*/if (fd_head != NULL && fit->hf_reassembled_in != NULL) {proto_item *fei = proto_tree_add_uint(tree,*(fit->hf_reassembled_in), tvb,0, 0, fd_head->reassembled_in);proto_item_set_generated(fei);}}return next_tvb;}
IP重组分析
TCP重组分析
通过 gdb 跟踪分析 tshark 打开一个 HTTPS 报文时的执行过程.
bing.zip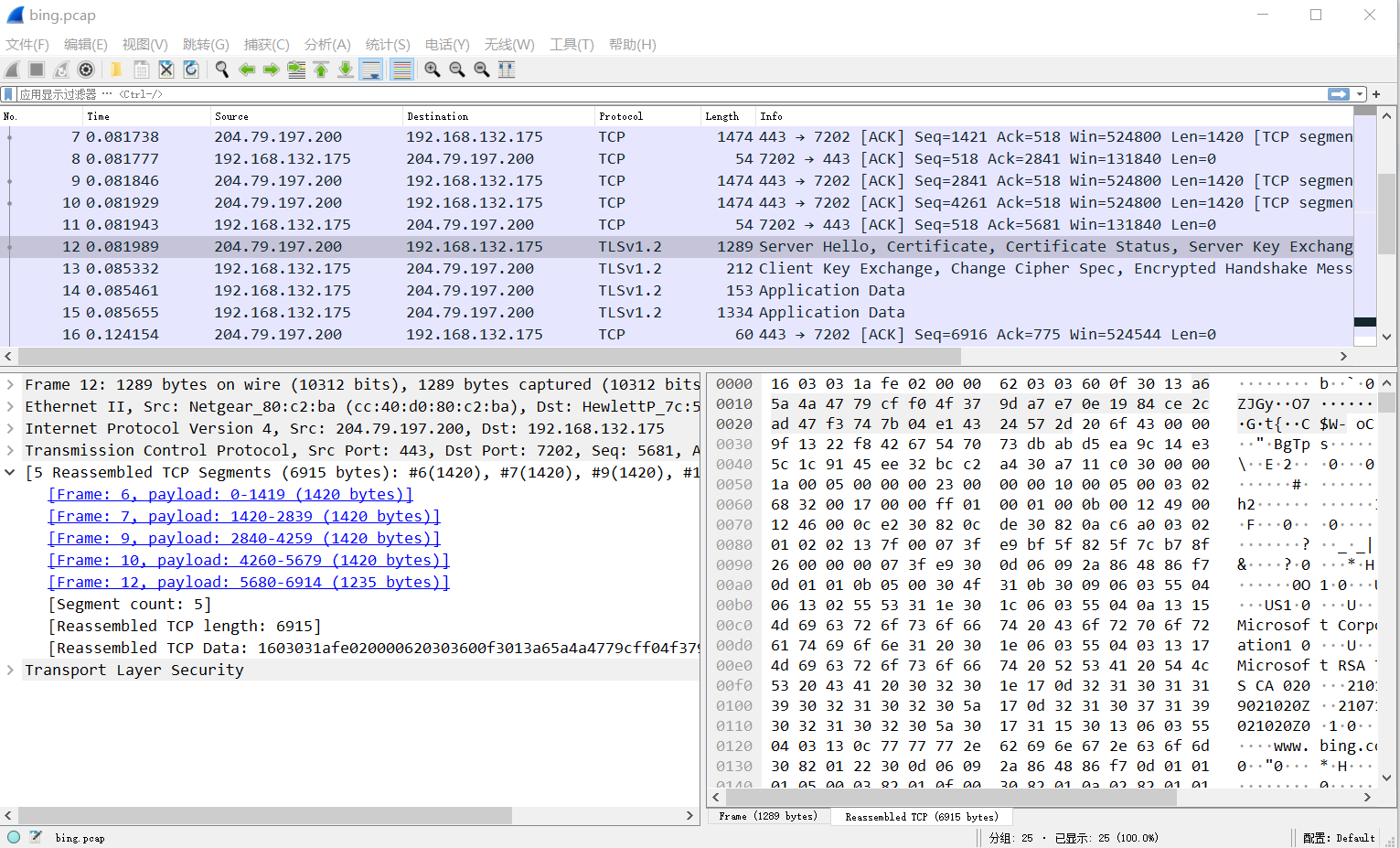
从上图可以看出, 第 12 个报文处进行了完整重组, 分片来自第 6, 7, 9, 10, 12 个报文.
命令行:
$ cd ~/dev/wireshark_build/run/$ gdb ./tshark(gdb) b desegment_tcp(gdb) b fragment_add_work(gdb) r -r ~/pcap/bing.pcap
调试时, tcp协议使用以下默认选项:
# Whether subdissector can request TCP streams to be reassembled# TRUE or FALSE (case-insensitive)#tcp.desegment_tcp_streams: TRUE# Whether out-of-order segments should be buffered and reordered before passing it to a subdissector. To use this option you must also enable "Allow subdissector to reassemble TCP streams".# TRUE or FALSE (case-insensitive)#tcp.reassemble_out_of_order: FALSE
调用栈
#0 fragment_add_work (fd_head=..., tvb=..., offset=..., pinfo=..., frag_offset=..., frag_data_len=..., more_frags=...)#1 0x00007ffff3d1121d in fragment_add_common (table=..., tvb=..., offset=..., pinfo=..., id=..., data=..., frag_offset=...,frag_data_len=..., more_frags=..., check_already_added=...)#2 0x00007ffff3d11282 in fragment_add (table=..., tvb=..., offset=..., pinfo=..., id=..., data=..., frag_offset=...,frag_data_len=..., more_frags=...)#3 0x00007ffff31f4198 in desegment_tcp (tvb=..., pinfo=..., offset=..., seq=..., nxtseq=..., sport=..., dport=..., tree=...,tcp_tree=..., tcpd=..., tcpinfo=...)#4 0x00007ffff31fa945 in dissect_tcp_payload (tvb=..., pinfo=..., offset=..., seq=..., nxtseq=..., sport=..., dport=..., tree=...,tcp_tree=..., tcpd=..., tcpinfo=...)#5 0x00007ffff31fdfc4 in dissect_tcp (tvb=..., pinfo=..., tree=..., data=...)...#29 0x00007ffff3ccf552 in call_dissector_with_data (handle=..., tvb=..., pinfo=..., tree=..., data=...)#30 0x00007ffff3cca9d8 in dissect_record (edt=..., file_type_subtype=..., rec=..., tvb=..., fd=..., cinfo=...)#31 0x00007ffff3cbf1d3 in epan_dissect_run_with_taps (edt=..., file_type_subtype=..., rec=..., tvb=..., fd=..., cinfo=...)#32 0x0000555555576b50 in process_packet_single_pass (cf=..., edt=..., offset=..., rec=..., buf=..., tap_flags=...)#33 0x0000555555576016 in process_cap_file_single_pass (cf=..., pdh=..., max_packet_count=..., max_byte_count=..., err=...,err_info=..., err_framenum=...)#34 0x0000555555576575 in process_cap_file (cf=..., save_file=..., out_file_type=..., out_file_name_res=..., max_packet_count=...,max_byte_count=...)#35 0x0000555555573d12 in main (argc=..., argv=...)
流程
1. 第一个分片- 创建分片链表头fd_head, 插入重组哈希表(insert_fd_head)- fragment_add_work, 重组完成返回分片表头, 否则返回NULL- 拷贝数据 (tvb_clone_offset_len)- 将分片插入有序链表 (LINK_FRAG)2. 中间的分片- tcpd(struct tcp_analysis) 已存在- fragment_add_work- 同1, 调用LINK_FRAG插入有序链表3. 最后一个分片- tcpd(struct tcp_analysis) 已存在- fragment_add_work- more_frags为FALSE, 没有更多分片, 设置fd_head的datalen- 调用LINK_FRAG插入有序链表- 遍历有序链表, 检查数据是否完整- 分配一个大缓冲区, 以容纳重组后的PDU- 遍历有序链表, 将分片数据拷贝到大缓冲区, 然后释放原分片数据内存- fd_head置为已重组- 返回fd_head. 注意之前的分片时都返回NULL- 对重组后的数据创建新tvb (next_tvb = tvb_new_chain)- 调用上层解析器 (process_tcp_payload)- 又创建tvb (next_tvb = tvb_new_subset_remaining)- dissect_ssl (TLS)
// TODO:
struct tcp_analysis, pdu, struct tcp_multisegment_pdu, desegment_tcp调用时机, 即TCP是怎样判断是分片的TCP序列号分析: tcp_analyze_sequence_number
tcp_analysis 是 tcp conversation 的数据: tcpd=get_tcp_conversation_data(conv,pinfo);
layer的概念:
if (add_proto_name) {pinfo->curr_layer_num++;wmem_list_append(pinfo->layers, GINT_TO_POINTER(proto_get_id(handle->protocol)));}
如何确定是分片, 或者说需要重组?
pkt #6
- 获取conversation- 从conversation获取tcp_analysis- 检查报文是IP分片情况(pinfo->fragmented)- 如果不是, 分析TCP序列号, 计算win等- 如果打开tcp重组, 设pinfo->can_desegment=2- 调用dissect_tcp_payload()- 调用desegment_tcp()- 检查当前报文是不是要重组报文的一部分(msp) epan/dissectors/packet-tcp.c #3142- 如果不是, 创建msp- 调用process_tcp_payload()- 调用decode_tcp_ports()- 创建新tvb- 通过dissector_try_uint_new()调用到dissect_ssl()- dissect_ssl3_record()检测到需要重组, 返回到decode_tcp_ports()此时tls还正确设置了pinfo->desegment_len, 表示还需要多少数据- 返回desegment_tcp(), must_desegment = TRUE- 添加msp (pdu_store_sequencenumber_of_next_pdu())- 添加分片 (fragement_add())
pkt #7, #9, #10
- 获取conversation- 从conversation获取tcp_analysis- 检查报文是IP分片情况(pinfo->fragmented)- 如果不是, 分析TCP序列号, 计算win等- 如果打开tcp重组, 设pinfo->can_desegment=2- 调用dissect_tcp_payload()- 调用desegment_tcp()- 检查当前报文是不是要重组报文的一部分(msp) epan/dissectors/packet-tcp.c #3142- 添加分片 (fragement_add()) epan/dissectors/packet-tcp.c #3323
pkt #12
- 获取conversation- 从conversation获取tcp_analysis- 检查报文是IP分片情况(pinfo->fragmented)- 如果不是, 分析TCP序列号, 计算win等- 如果打开tcp重组, 设pinfo->can_desegment=2- 调用dissect_tcp_payload()- 调用desegment_tcp()- 检查当前报文是不是要重组报文的一部分(msp) epan/dissectors/packet-tcp.c #3142- 添加分片 (fragement_add()) epan/dissectors/packet-tcp.c #3323- 添加分片返回非空值, 表示所有分片到齐- 创建新的tvb, 主要是把之前的tvb和重组后的tvb链接起来- 调用process_tcp_payload()- 调用decode_tcp_ports()- 创建新tvb- 通过dissector_try_uint_new()调用到dissect_ssl()- dissect_ssl3_record() TLS PDU完整, 解析完成
HTTP重组分析
DNS重组分析
RTMPT重组分析
通过 gdb 跟踪分析 tshark 打开一个 RTMP 报文时的执行过程.
![3JY_ES{CRGRT9@NFQ}0072.png
$ cd ~/dev/wireshark_build/run/$ gdb ./tshark(gdb) set print frame-info short-location(gdb) set print frame-arguments none(gdb) b dissect_rtmpt_tcp(gdb) b fragment_add_work(gdb) r -r ~/pcap/renren_rtmp.pcap
#0 dissect_rtmpt_tcp (tvb=..., pinfo=..., tree=..., data=...)#1 0x00007ffff3ccb0c2 in call_dissector_through_handle (handle=..., tvb=..., pinfo=..., tree=..., data=...)#2 0x00007ffff3ccb313 in call_dissector_work (handle=..., tvb=..., pinfo_arg=..., tree=..., add_proto_name=..., data=...)#3 0x00007ffff3ccc4ed in dissector_try_uint_new (sub_dissectors=..., uint_val=..., tvb=..., pinfo=..., tree=..., add_proto_name=...,data=...)#4 0x00007ffff31fa149 in decode_tcp_ports (tvb=..., offset=..., pinfo=..., tree=..., src_port=..., dst_port=..., tcpd=..., tcpinfo=...)#5 0x00007ffff31fa68a in process_tcp_payload (tvb=..., offset=..., pinfo=..., tree=..., tcp_tree=..., src_port=..., dst_port=..., seq=...,nxtseq=..., is_tcp_segment=..., tcpd=..., tcpinfo=...)#6 0x00007ffff31f3bee in desegment_tcp (tvb=..., pinfo=..., offset=..., seq=..., nxtseq=..., sport=..., dport=..., tree=..., tcp_tree=...,tcpd=..., tcpinfo=...)#7 0x00007ffff31fa945 in dissect_tcp_payload (tvb=..., pinfo=..., offset=..., seq=..., nxtseq=..., sport=..., dport=..., tree=...,tcp_tree=..., tcpd=..., tcpinfo=...)#8 0x00007ffff31fdfc4 in dissect_tcp (tvb=..., pinfo=..., tree=..., data=...)...#32 0x00007ffff3ccf552 in call_dissector_with_data (handle=..., tvb=..., pinfo=..., tree=..., data=...)#33 0x00007ffff3cca9d8 in dissect_record (edt=..., file_type_subtype=..., rec=..., tvb=..., fd=..., cinfo=...)#34 0x00007ffff3cbf1d3 in epan_dissect_run_with_taps (edt=..., file_type_subtype=..., rec=..., tvb=..., fd=..., cinfo=...)#35 0x0000555555576b50 in process_packet_single_pass (cf=..., edt=..., offset=..., rec=..., buf=..., tap_flags=...)#36 0x0000555555576016 in process_cap_file_single_pass (cf=..., pdh=..., max_packet_count=..., max_byte_count=..., err=..., err_info=...,err_framenum=...)#37 0x0000555555576575 in process_cap_file (cf=..., save_file=..., out_file_type=..., out_file_name_res=..., max_packet_count=...,max_byte_count=...)#38 0x0000555555573d12 in main (argc=..., argv=...)
/* Represents a header or a chunk that is split over two TCP* segments*/typedef struct rtmpt_frag {int ishdr;guint32 seq;guint32 lastseq;int have;int len;union {guint8 d[18]; /* enough for a complete header (3 + 11 + 4) */guint32 id;} saved;} rtmpt_frag_t;/* The full message header information for the last packet on a particular* ID - used for defaulting short headers*/typedef struct rtmpt_id {guint32 ts; /* bytes 1-3 */guint32 tsd;guint32 len; /* bytes 4-6 */guint32 src; /* bytes 8-11 */guint8 cmd; /* byte 7 */wmem_tree_t *packets;} rtmpt_id_t;/* Historical view of a whole TCP connection*/typedef struct rtmpt_conv {wmem_tree_t *seqs[2];wmem_tree_t *frags[2];wmem_tree_t *ids[2];wmem_tree_t *packets[2];wmem_tree_t *chunksize[2];wmem_tree_t *txids[2];} rtmpt_conv_t;
dissect_rtmpt_tcp:
static intdissect_rtmpt_tcp(tvbuff_t *tvb, packet_info *pinfo, proto_tree *tree, void* data){conversation_t *conv;rtmpt_conv_t *rconv;int cdir;struct tcpinfo *tcpinfo;/* Reject the packet if data is NULL */if (data == NULL) {return 0;}tcpinfo = (struct tcpinfo*)data;conv = find_or_create_conversation(pinfo);rconv = (rtmpt_conv_t*)conversation_get_proto_data(conv, proto_rtmpt);if (!rconv) {rconv = rtmpt_init_rconv(conv);}cdir = (addresses_equal(conversation_key_addr1(conv->key_ptr), &pinfo->src) &&addresses_equal(conversation_key_addr2(conv->key_ptr), &pinfo->dst) &&conversation_key_port1(conv->key_ptr) == pinfo->srcport &&conversation_key_port2(conv->key_ptr) == pinfo->destport) ? 0 : 1;dissect_rtmpt_common(tvb, pinfo, tree, rconv, cdir, tcpinfo->seq, tcpinfo->lastackseq);return tvb_reported_length(tvb);}
第 5 个报文(Handshake C0+C1)的完整数据分散在 2 个 TCP 报文 #4 #5 中.
1. 第一个分片, #4- rtmp会话不存在, 初始化 (rtmpt_init_rconv)- rtmp会话创建后要插入到通用会话表项中的协议私有数据树中 (conversation_add_proto_data(conv, proto_rtmpt, rconv))voidconversation_add_proto_data(conversation_t *conv, const int proto, void *proto_data){/* Add it to the list of items for this conversation. */if (conv->data_list == NULL)conv->data_list = wmem_tree_new(wmem_file_scope());wmem_tree_insert32(conv->data_list, proto, proto_data);}- rtmp会话是分2个方向的, 因此之后要判断方向(cdir)- dissect_rtmpt_common- 在rtmp会话中查找当前方向之前的分片 (tf = (rtmpt_frag_t *)wmem_tree_lookup32_le(rconv->frags[cdir], seq+offset-1))- 没找到, 说明这是首部, 解析rtmp首部信息- 将当前分片id信息(rtmpt_id)插入查找树 (wmem_tree_insert32(rconv->ids[cdir], id, ti))- 创建rtmp packet(pdu), 填入分片相关信息, 如整个报文的总长度(tp->want = basic_hlen + message_hlen + body_len)这时候还缺一部分, 在后面的报文- 将rtmp packet插入ti->packets- 分配内存, 以容纳所有分片 (tp->data.p = (guint8 *)wmem_alloc(wmem_file_scope(), tp->bhlen+tp->mhlen+tp->len))将当前分片数据拷贝到此内存中- 新建rtmp frag, 填写分片信息, 插入查找树 (wmem_tree_insert32(rconv->frags[cdir], seq+offset-want-1, tf2))2. 最后一个分片- rtmp会话已存在- dissect_rtmpt_common- 找到已保存的上一个分片信息tf- 进而找到分片id ti和pdu tp, 跳到unchunk- 已有所有分片(tp->have == tp->want), 开始解析- dissect_rtmpt
参考
- Wireshark User’s Guide: 7.5. TCP Analysis
- Wireshark User’s Guide: 7.8. Packet Reassembly
- tshark使用手册
- Wireshark Developer’s Guide: 9.4. How to handle transformed data
- Wireshark Developer’s Guide: 9.5. How to reassemble split packets
- Wireshark wiki: IP Reassembly
- Wireshark wiki: TCP Reassembly
- Wireshark源码: epan/reassemble.h, epan/dissectors/packet-tcp.c, epan/dissectors/packet-tls.c
- Difference Between Segments, Packets and Frames

