1. 前言
Apache Shiro是一个功能强大且易于使用的Java安全框架,提供了认证,授权,加密,和会话管理。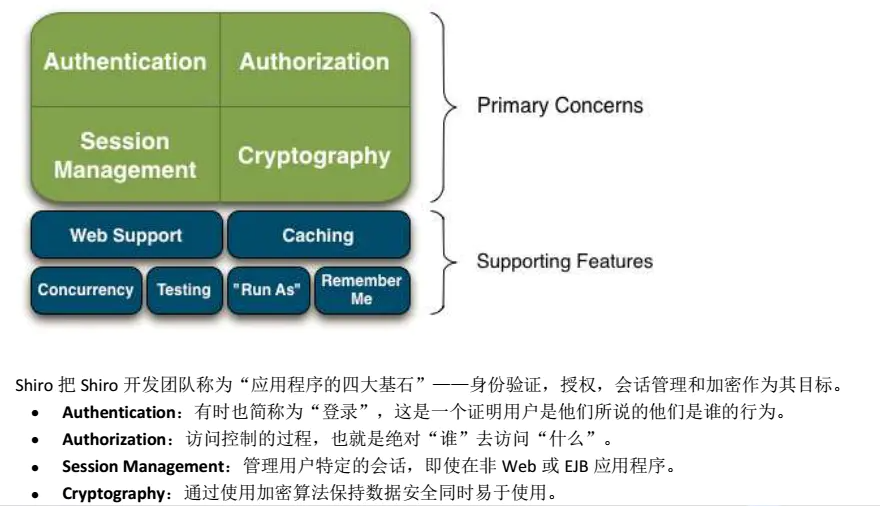
Shiro有三大核心组件:
Subject:即当前用户,在权限管理的应用程序里往往需要知道谁能够操作什么,谁拥有操作该程序的权利,shiro中则需要通过Subject来提供基础的当前用户信息,Subject 不仅仅代表某个用户,与当前应用交互的任何东西都是Subject,如网络爬虫等。所有的Subject都要绑定到SecurityManager上,与Subject的交互实际上是被转换为与SecurityManager的交互。
SecurityManager:即所有Subject的管理者,这是Shiro框架的核心组件,可以把他看做是一个Shiro框架的全局管理组件,用于调度各种Shiro框架的服务。作用类似于SpringMVC中的DispatcherServlet,用于拦截所有请求并进行处理。
Realm:Realm是用户的信息认证器和用户的权限人证器,我们需要自己来实现Realm来自定义的管理我们自己系统内部的权限规则。SecurityManager要验证用户,需要从Realm中获取用户。可以把Realm看做是数据源。
2. 数据库设计
2.1 User(用户)
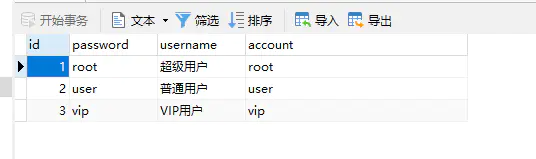
SET NAMES utf8mb4;SET FOREIGN_KEY_CHECKS = 0;-- ------------------------------ Table structure for user-- ----------------------------DROP TABLE IF EXISTS `user`;CREATE TABLE `user` (`id` bigint(20) NOT NULL AUTO_INCREMENT,`password` varchar(255) CHARACTER SET utf8 COLLATE utf8_general_ci NULL DEFAULT NULL,`username` varchar(255) CHARACTER SET utf8 COLLATE utf8_general_ci NULL DEFAULT NULL,`account` varchar(255) CHARACTER SET utf8 COLLATE utf8_general_ci NULL DEFAULT NULL,PRIMARY KEY (`id`) USING BTREE) ENGINE = MyISAM AUTO_INCREMENT = 4 CHARACTER SET = utf8 COLLATE = utf8_general_ci ROW_FORMAT = Dynamic;-- ------------------------------ Records of user-- ----------------------------INSERT INTO `user` VALUES (1, 'root', '超级用户', 'root');INSERT INTO `user` VALUES (2, 'user', '普通用户', 'user');INSERT INTO `user` VALUES (3, 'vip', 'VIP用户', 'vip');SET FOREIGN_KEY_CHECKS = 1;
2.2 Role(角色)
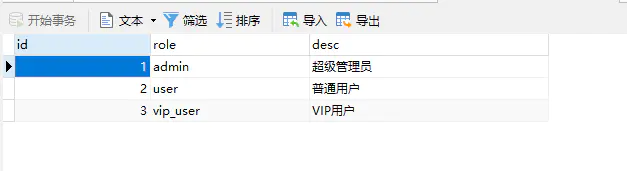
SET NAMES utf8mb4;
SET FOREIGN_KEY_CHECKS = 0;
-- ----------------------------
-- Table structure for role
-- ----------------------------
DROP TABLE IF EXISTS `role`;
CREATE TABLE `role` (
`id` int(11) NOT NULL AUTO_INCREMENT,
`role` varchar(255) CHARACTER SET utf8 COLLATE utf8_general_ci NULL DEFAULT NULL,
`desc` varchar(255) CHARACTER SET utf8 COLLATE utf8_general_ci NULL DEFAULT NULL,
PRIMARY KEY (`id`) USING BTREE
) ENGINE = MyISAM AUTO_INCREMENT = 4 CHARACTER SET = utf8 COLLATE = utf8_general_ci ROW_FORMAT = Dynamic;
-- ----------------------------
-- Records of role
-- ----------------------------
INSERT INTO `role` VALUES (1, 'admin', '超级管理员');
INSERT INTO `role` VALUES (2, 'user', '普通用户');
INSERT INTO `role` VALUES (3, 'vip_user', 'VIP用户');
SET FOREIGN_KEY_CHECKS = 1;
2.3 Permission(权限)
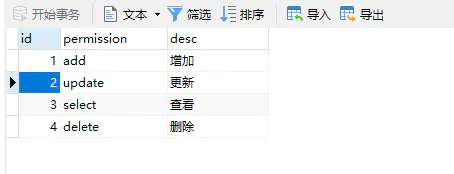
SET NAMES utf8mb4;
SET FOREIGN_KEY_CHECKS = 0;
-- ----------------------------
-- Table structure for permission
-- ----------------------------
DROP TABLE IF EXISTS `permission`;
CREATE TABLE `permission` (
`id` int(11) NOT NULL AUTO_INCREMENT,
`permission` varchar(255) CHARACTER SET utf8 COLLATE utf8_general_ci NULL DEFAULT NULL COMMENT '权限名称',
`desc` varchar(255) CHARACTER SET utf8 COLLATE utf8_general_ci NULL DEFAULT NULL COMMENT '权限描述',
PRIMARY KEY (`id`) USING BTREE
) ENGINE = MyISAM AUTO_INCREMENT = 5 CHARACTER SET = utf8 COLLATE = utf8_general_ci ROW_FORMAT = Dynamic;
-- ----------------------------
-- Records of permission
-- ----------------------------
INSERT INTO `permission` VALUES (1, 'add', '增加');
INSERT INTO `permission` VALUES (2, 'update', '更新');
INSERT INTO `permission` VALUES (3, 'select', '查看');
INSERT INTO `permission` VALUES (4, 'delete', '删除');
SET FOREIGN_KEY_CHECKS = 1;
2.4 User_Role(用户-角色)
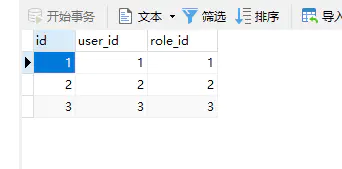
SET NAMES utf8mb4;
SET FOREIGN_KEY_CHECKS = 0;
-- ----------------------------
-- Table structure for user_role
-- ----------------------------
DROP TABLE IF EXISTS `user_role`;
CREATE TABLE `user_role` (
`id` int(11) NOT NULL AUTO_INCREMENT,
`user_id` int(11) NULL DEFAULT NULL,
`role_id` int(11) NULL DEFAULT NULL,
PRIMARY KEY (`id`) USING BTREE
) ENGINE = MyISAM AUTO_INCREMENT = 4 CHARACTER SET = utf8 COLLATE = utf8_general_ci ROW_FORMAT = Fixed;
-- ----------------------------
-- Records of user_role
-- ----------------------------
INSERT INTO `user_role` VALUES (1, 1, 1);
INSERT INTO `user_role` VALUES (2, 2, 2);
INSERT INTO `user_role` VALUES (3, 3, 3);
SET FOREIGN_KEY_CHECKS = 1;
2.5 Role_Permission(角色-权限)
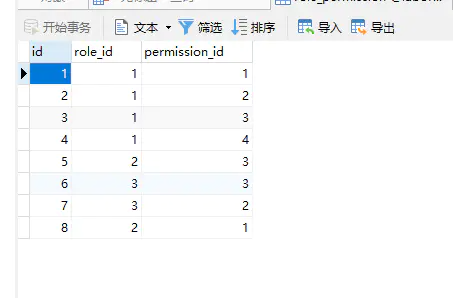
SET NAMES utf8mb4;
SET FOREIGN_KEY_CHECKS = 0;
-- ----------------------------
-- Table structure for role_permission
-- ----------------------------
DROP TABLE IF EXISTS `role_permission`;
CREATE TABLE `role_permission` (
`id` int(11) NOT NULL AUTO_INCREMENT,
`role_id` int(11) NULL DEFAULT NULL,
`permission_id` int(255) NULL DEFAULT NULL,
PRIMARY KEY (`id`) USING BTREE
) ENGINE = MyISAM AUTO_INCREMENT = 9 CHARACTER SET = utf8 COLLATE = utf8_general_ci ROW_FORMAT = Fixed;
-- ----------------------------
-- Records of role_permission
-- ----------------------------
INSERT INTO `role_permission` VALUES (1, 1, 1);
INSERT INTO `role_permission` VALUES (2, 1, 2);
INSERT INTO `role_permission` VALUES (3, 1, 3);
INSERT INTO `role_permission` VALUES (4, 1, 4);
INSERT INTO `role_permission` VALUES (5, 2, 3);
INSERT INTO `role_permission` VALUES (6, 3, 3);
INSERT INTO `role_permission` VALUES (7, 3, 2);
INSERT INTO `role_permission` VALUES (8, 2, 1);
SET FOREIGN_KEY_CHECKS = 1;
4. 前期准备
4.1 依赖导入
<dependencies>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-web</artifactId>
</dependency>
<dependency>
<groupId>mysql</groupId>
<artifactId>mysql-connector-java</artifactId>
</dependency>
<dependency>
<groupId>org.mybatis.spring.boot</groupId>
<artifactId>mybatis-spring-boot-starter</artifactId>
<version>1.3.2</version>
</dependency>
<dependency>
<groupId>org.apache.shiro</groupId>
<artifactId>shiro-spring</artifactId>
<version>1.4.0</version>
</dependency>
</dependencies>
4.2 application.yml
server:
port: 29898
spring:
datasource:
driver-class-name: com.mysql.jdbc.Driver
url: jdbc:mysql://127.0.0.1:3306/shiro?charset=utf8
username: root
password: 123456
mybatis-plus:
config-location: classpath:mapper/*.xml
4.3 实体类
4.3.1 User.java
@Data
public class User implements Serializable {
private static final long serialVersionUID = -6056125703075132981L;
private Integer id;
private String account;
private String password;
private String username;
}
4.3.2 Role.java
@Data
public class Role implements Serializable {
private static final long serialVersionUID = -1767327914553823741L;
private Integer id;
private String role;
private String desc;
}
4.3.3 Permission.java
@Data
public class Permission implements Serializable {
private static final long serialVersionUID = 1L;
private Integer id;
private String permission;
private String desc;
}
4.3.4 RolePermission
@Data
public class RolePermission implements Serializable {
private Integer id;
private Integer roleId;
private Integer permissionId;
private static final long serialVersionUID = 1L;
}
4.3.5 UserRole
@Data
public class UserRole implements Serializable {
private Integer id;
private Integer userId;
private Integer roleId;
private static final long serialVersionUID = 1L;
}
4.4 Mapper层
4.4.1 PermissionMapper.java
@Mapper
public interface PermissionMapper extends BaseMapper<Permission> {
List<String> findByRoleIds(@Param("roleIds") List<Integer> roleIds);
}
4.4.2 PermissionMapper.xml
<mapper namespace="com.zukxu.shiro.mapper.PermissionMapper">
<resultMap id="BaseResultMap" type="com.zukxu.shiro.entity.Permission">
<!--@mbg.generated-->
<id column="id" jdbcType="INTEGER" property="id"/>
<result column="permission" jdbcType="VARCHAR" property="permission"/>
<result column="desc" jdbcType="VARCHAR" property="desc"/>
</resultMap>
<sql id="Base_Column_List">
id,
permission,
`desc`
</sql>
<select id="findByRoleIds" resultType="java.lang.String">
select r.permission
from shiro_permission r,
shiro_role_permission rp
where rp.permission_id = p.id
and rp.role_id in
<foreach close=")" collection="roleIds" item="id" open="(" separator=",">
#{id}
</foreach>
</select>
</mapper>
4.4.3 RoleMapper.java
@Mapper
public interface RoleMapper extends BaseMapper<Role> {
/**
* 通过用户id查询角色
*
* @param userId
* @return
*/
List<Role> findRoleByUserId(@Param("userId") Integer userId);
}
4.4.4 RoleMapper.xml
<mapper namespace="com.zukxu.shiro.mapper.RoleMapper">
<resultMap id="BaseResultMap" type="com.zukxu.shiro.entity.Role">
<!--@mbg.generated-->
<id column="id" jdbcType="INTEGER" property="id"/>
<result column="role" jdbcType="VARCHAR" property="role"/>
<result column="desc" jdbcType="VARCHAR" property="desc"/>
</resultMap>
<sql id="Base_Column_List">
id,
`role`,
`desc`
</sql>
<select id="findRoleByUserId" resultMap="BaseResultMap">
select r.id, role
from shiro_role r,
shiro_user u,
shiro_user_role ur
where r.id = ur.role_id
and ur.user_id = u.id
and u.id = #{userId}
</select>
</mapper>
4.4.5 UserMapper.java
@Mapper
public interface UserMapper extends BaseMapper<User> {
/**
* 通过用户名查询用户信息
*
* @param account
* @return
*/
User findByAccount(@Param("account") String account);
}
4.4.6 UserMapper.xml
<mapper namespace="com.zukxu.shiro.mapper.UserMapper">
<resultMap id="BaseResultMap" type="com.zukxu.shiro.entity.User">
<!--@mbg.generated-->
<id column="id" jdbcType="BIGINT" property="id"/>
<result column="password" jdbcType="VARCHAR" property="password"/>
<result column="username" jdbcType="VARCHAR" property="username"/>
<result column="account" jdbcType="VARCHAR" property="account"/>
</resultMap>
<sql id="Base_Column_List">
id,
`password`,
username,
account
</sql>
<select id="findByAccount" resultMap="BaseResultMap">
select
<include refid="Base_Column_List"/>
from shiro_user
where account = #{account}
</select>
</mapper>
4.4.7 RolePermissionMapper
@Mapper
public interface RolePermissionMapper extends BaseMapper<RolePermission> {
}
4.4.8 UserRoleMapper
@Mapper
public interface UserRoleMapper extends BaseMapper<UserRole> {
}
4.5 Service层
4.5.1 PermissionServiceImpl.java
@Service
public class PermissionServiceImpl implements PermissionService {
@Autowired
private PermissionMapper permissionMapper;
@Override
public List<String> findByRoleId(List<Integer> roleIds) {
return permissionMapper.findByRoleId(roleIds);
}
}
4.5.2 RoleServiceImpl.java
@Service
public class RoleServiceImpl implements RoleService {
@Autowired
private RoleMapper roleMapper;
@Override
public List<Role> findRoleByUserId(Integer id) {
return roleMapper.findRoleByUserId(id);
}
}
4.5.3 UserServiceImpl.java
@Service
public class UserServiceImpl implements UserService {
@Autowired
private UserMapper userMapper;
@Override
public User findByAccount(String account) {
return userMapper.findByAccount(account);
}
}
4.6. 结果集封装
4.6.1 RStatus.java
@Getter
public enum RStatus {
OK(200, "请求成功"),
FAIL(500, "请求失败"),
PARAM_ERROR(501, "参数错误"),
//账号相关
ACCOUNT_NOT_EXIST(11, "账号不存在"),
DUPLICATE_ACCOUNT(12, "账号重复"),
ACCOUNT_IS_DISABLED(13, "账号被禁用"),
INCORRECT_CREDENTIALS(14, "账号或密码错误"),
NOT_LOGIN_IN(15, "账号未登录"),
UNAUTHORIZED(16, "账号没有权限");
private int code;
private String message;
RStatus(int code, String message) {
this.code = code;
this.message = message;
}
}
4.6.2 R.java
@Data
@Accessors(chain = true)
public class R<T> implements Serializable {
private static final long serialVersionUID = -45239331572204682L;
private int code;
private String msg;
private T data;
private R() {}
/**
* 通用返回成功
*
* @return R<Void>
*/
public static <T> R<T> ok() {
return ok(null);
}
/**
* @param data data
* @param <T> T
* @return R<T>
*/
public static <T> R<T> ok(T data) {
return genResult(RStatus.OK, data);
}
/**
* @param msg 消息
* @param data 数据
* @param <T> T
* @return R<T>
*/
public static <T> R<T> ok(String msg, T data) {
return genResult(RStatus.OK.getCode(), msg, data);
}
/**
* 通用返回失败,未知错误
*
* @return R<T>
*/
public static <T> R<T> fail() {
return genResult(RStatus.FAIL, null);
}
/**
* @param msg msg
* @param <T> <T>
* @return R
*/
public static <T> R<T> fail(String msg) {
return fail(msg, null);
}
/**
* @param msg msg
* @param data data
* @return R<T>
*/
public static <T> R<T> fail(String msg, T data) {
return genResult(RStatus.FAIL.getCode(), msg, data);
}
/**
* @param code code int
* @param msg msg String
* @param <T> T
* @return R
*/
public static <T> R<T> fail(int code, String msg) {
return genResult(code, msg, null);
}
/**
* @param status RStatus
* @param data T data
* @param <T> T
* @return R
*/
public static <T> R<T> fail(RStatus status, T data) {
return genResult(status, data);
}
//chain calls methods
//R.ok().code(200).message("成功").data(null);
//R.fail().code(500).message("失败").data(null);
public R<T> data(T data) {
this.setData(data);
return this;
}
public R<T> message(String message) {
this.setMsg(message);
return this;
}
public R<T> code(Integer code) {
this.setCode(code);
return this;
}
/**
* @param status RStatus
* @param data data
* @param <T> T
* @return R
*/
private static <T> R<T> genResult(RStatus status, T data) {
R<T> r = new R<>();
r.setCode(status.getCode());
r.setMsg(status.getMessage());
r.setData(data);
return r;
}
/**
* generate a R instance
*
* @param code code
* @param msg msg
* @param data data
* @param <T> <T>
* @return R
*/
private static <T> R<T> genResult(int code, String msg, T data) {
R<T> r = new R<>();
r.setCode(code);
r.setData(data);
r.setMsg(msg);
return r;
}
}
4.7 统一异常处理
当用户身份认证失败时,会抛出UnauthorizedException,我们可以通过统一异常处理来处理该异常
@ControllerAdvice
public class MyExceptionHandler {
/**
* 没有授权异常处理
*
* @param e unauthorizedException
* @return R
*/
@ExceptionHandler(UnauthorizedException.class)
@ResponseStatus(HttpStatus.UNAUTHORIZED)
public R<?> UnauthorizedExceptionHandler(UnauthorizedException e) {
return R.fail(RStatus.UNAUTHORIZED, null);
}
}
5. 集成Shiro
5.1 UserRealm.java
这只是最基础的Realm定义,后续可以根据自己的需求增加更多的Realm,只需要在配置类中声明即可
public class UserRealm extends AuthorizingRealm {
@Autowired
UserService userService;
@Autowired
RoleService roleService;
@Autowired
PermissionService permissionService;
/**
* 执行授权
*
* @param principalCollection 凭证集合
* @return 授权
*/
@Override
protected AuthorizationInfo doGetAuthorizationInfo(PrincipalCollection principalCollection) {
//1、获取登录对象
User principal = (User) principalCollection.getPrimaryPrincipal();
//2、生成授权集合实体
SimpleAuthorizationInfo authorizationInfo = new SimpleAuthorizationInfo();
//3、业务逻辑,从数据库获取权限数据,并将role放入一个Set集合中,role_id 放入一个list中
Stream<Role> roleList = roleService.findRoleByUserId(principal.getId()).stream();
Set<String> roleSet = new HashSet<>();
List<Integer> roleIds = new ArrayList<>();
roleList.forEach(role -> {
roleSet.add(role.getRole());
roleIds.add(role.getId());
});
//4、根据角色id获取相对应的权限
Set<String> permIdSet = permissionService.findByRoleIds(roleIds);
//5、将权限放入授权实体中
authorizationInfo.setRoles(roleSet);
authorizationInfo.setStringPermissions((permIdSet));
return authorizationInfo;
}
/**
* 执行认证
*
* @param authenticationToken token
* @return 认证
* @throws AuthenticationException 认证异常
*/
@Override
protected AuthenticationInfo doGetAuthenticationInfo(AuthenticationToken authenticationToken) throws AuthenticationException {
//1、获取登录token
UsernamePasswordToken token = (UsernamePasswordToken) authenticationToken;
User user = userService.findByUsername(token.getUsername());
if (ObjectUtil.isNotNull(user))
return new SimpleAuthenticationInfo(user, user.getPassword(), this.getName());
return null;
}
}
5.2 ShiroConfig.java
@Configuration
public class ShiroConfig {
//1、配置realm Bean生成
@Bean("userRealm")
public UserRealm userRealm() {
return new UserRealm();
}
//2、配置mgt
@Bean("defaultSecurityManager")
public DefaultSecurityManager defaultSecurityManager() {
DefaultSecurityManager securityManager = new DefaultSecurityManager();
securityManager.setRealm(userRealm());
return securityManager;
}
//3、配置过滤链
@Bean
public ShiroFilterFactoryBean shiroFilterFactoryBean(DefaultSecurityManager defaultSecurityManager) {
ShiroFilterFactoryBean shiroFilterFactoryBean = new ShiroFilterFactoryBean();
shiroFilterFactoryBean.setSecurityManager(defaultSecurityManager);
//配置登录
shiroFilterFactoryBean.setLoginUrl("/login");
shiroFilterFactoryBean.setSuccessUrl("/");
//配置权限
Map<String, String> map = new HashMap<>();
// 有先后顺序
map.put("/login", "anon"); // 允许匿名访问
map.put("/**", "authc"); // 进行身份认证后才能访问
shiroFilterFactoryBean.setFilterChainDefinitionMap(map);
return shiroFilterFactoryBean;
}
//4、可选,配置开启shiro注解模式,可在controller中开启注解模式
@Bean
public AuthorizationAttributeSourceAdvisor authorizationAttributeSourceAdvisor(@Qualifier("defaultSecurityManager") DefaultSecurityManager defaultSecurityManager) {
AuthorizationAttributeSourceAdvisor advisor = new AuthorizationAttributeSourceAdvisor();
advisor.setSecurityManager(defaultSecurityManager);
return advisor;
}
}
5.3 LoginController.java
@RestController
@RequestMapping
public class LoginController {
@PostMapping("/login")
public R login(@RequestParam(value = "account") String account, @RequestParam(value = "password") String password) {
Subject userSubject = SecurityUtils.getSubject();
UsernamePasswordToken token = new UsernamePasswordToken(account, password);
try {
// 登录验证
userSubject.login(token);
return R.ok();
} catch (UnknownAccountException e) {
return R.fail(RStatus.ACCOUNT_NOT_EXIST, null);
} catch (DisabledAccountException e) {
return R.fail(RStatus.ACCOUNT_IS_DISABLED, null);
} catch (IncorrectCredentialsException e) {
return R.fail(RStatus.INCORRECT_CREDENTIALS, null);
} catch (Throwable e) {
e.printStackTrace();
return R.fail(RStatus.FAIL, null);
}
}
@GetMapping("/role")
@RequiresRoles("vip")
public String role() {
return "测试Vip角色";
}
@GetMapping("/permission")
@RequiresPermissions(value = {"add", "update"}, logical = Logical.AND)
public String permission() {
return "测试Add和Update权限";
}
@GetMapping("/logout")
public String logOut() {
Subject userSubject = SecurityUtils.getSubject();
userSubject.logout();
return "注销登陆";
}
}
6. 测试
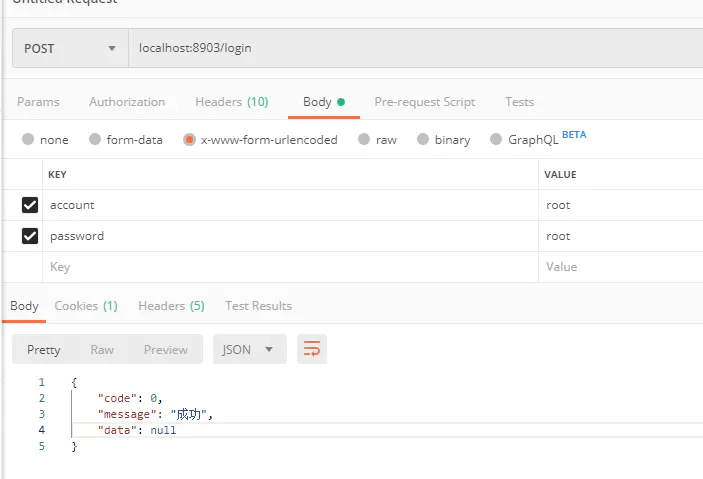
6.1 用root用户登录
6.1.1 登录
6.1.2 验证是否登录
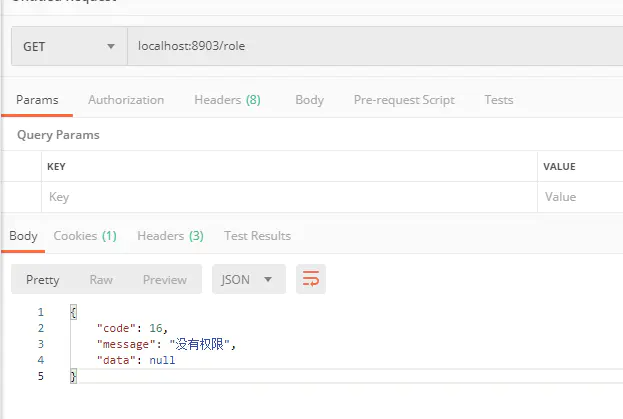
 6.1.3 测试角色权限
6.1.3 测试角色权限
6.1.4 测试用户操作权限
7. 总结
本文演示了 Spring Boot 极简集成 Shiro 框架,实现了基础的身份认证和授权功能,如有不足,请多指教。
后续可扩展的功能点有:
1. 集成 Redis 实现 Shiro 的分布式会话
2. 集成 JWT 实现单点登录功能