第一种方法:直接迁移
1、开启ESXI上的ssh服务和ESXI Shell服务。
ESXI5.5如下: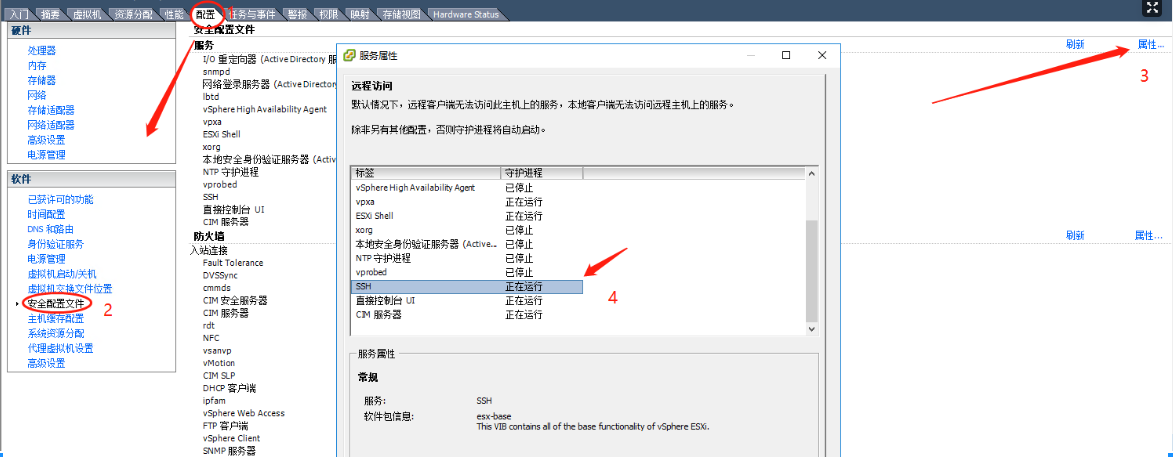
ESXI6.7如下: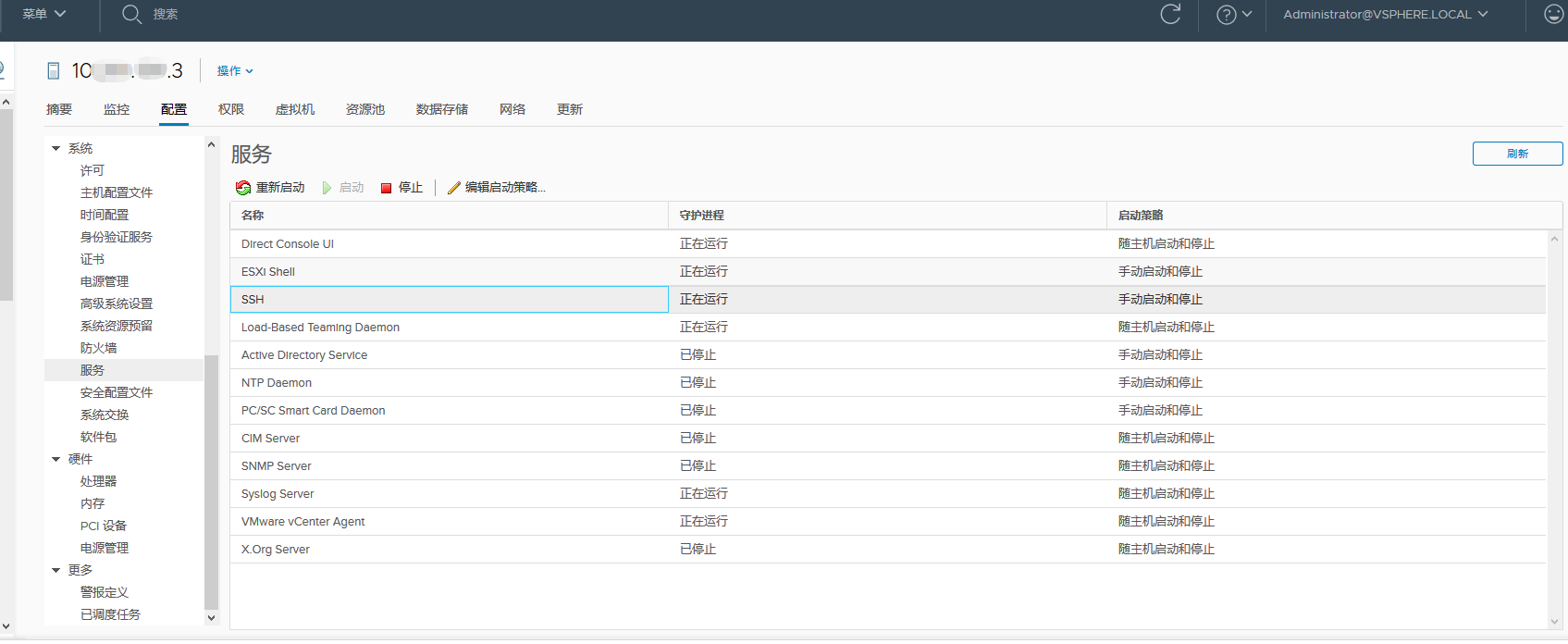
2、配置KVM到ESXI免密认证
[root@SIT-KVM01 ~]# ssh-keygenGenerating public/private rsa key pair.Enter file in which to save the key (/root/.ssh/id_rsa):Created directory '/root/.ssh'.Enter passphrase (empty for no passphrase):Enter same passphrase again:Your identification has been saved in /root/.ssh/id_rsa.Your public key has been saved in /root/.ssh/id_rsa.pub.The key fingerprint is:SHA256:Cd2XpDjQiR0Nz1eGRDcJhQFm6hyapIXLQ3BeAzRectk root@SIT-KVM01The key's randomart image is:+---[RSA 2048]----+| ...o=++. || = Bo+EO.oo=.. || = + * = + || o = * + o || = o S || . || || || |+----[SHA256]-----+[root@SIT-KVM01 ~]# ssh-copy-id -i .ssh/id_rsa.pub 10.xxx.128.145/usr/bin/ssh-copy-id: INFO: Source of key(s) to be installed: ".ssh/id_rsa.pub"The authenticity of host '10.xxx.128.145 (10.xxx.128.145)' can't be established.RSA key fingerprint is SHA256:DUhcdrc8dWdwMVv6RwOQs9AVjonPqIFwD7kumhURcjQ.RSA key fingerprint is MD5:86:2f:b2:02:e4:75:6b:13:3e:ec:32:48:c9:01:85:d3.Are you sure you want to continue connecting (yes/no)? yes/usr/bin/ssh-copy-id: INFO: attempting to log in with the new key(s), to filter out any that are already installed/usr/bin/ssh-copy-id: INFO: 1 key(s) remain to be installed -- if you are prompted now it is to install the new keysPassword:Number of key(s) added: 1Now try logging into the machine, with: "ssh '10.xxx.128.145'"and check to make sure that only the key(s) you wanted were added.[root@SIT-KVM01 ~]#
3、调整ESXI中上一步添加的KEY认证文件
[root@SIT-KVM01 ~]# ssh 10.xxx.128.145Password:The time and date of this login have been sent to the system logs.VMware offers supported, powerful system administration tools. Pleasesee www.vmware.com/go/sysadmintools for details.The ESXi Shell can be disabled by an administrative user. See thevSphere Security documentation for more information.~ # cd /etc/ssh//etc/ssh # lskeys-root moduli ssh_host_dsa_key ssh_host_dsa_key.pub ssh_host_rsa_key ssh_host_rsa_key.pub sshd_config/etc/ssh # cd keys-root//etc/ssh/keys-root # lsauthorized_keys/etc/ssh/keys-root # cd~ # cat .ssh/authorized_keys >> /etc/ssh/keys-root/authorized_keys~ # exitConnection to 10.xxx.128.145 closed.[root@SIT-KVM01 ~]# ssh 10.xxx.128.145The time and date of this login have been sent to the system logs.VMware offers supported, powerful system administration tools. Pleasesee www.vmware.com/go/sysadmintools for details.The ESXi Shell can be disabled by an administrative user. See thevSphere Security documentation for more information.~ #
4、开始迁移,(注:迁移前需要将虚拟机关机,虚拟机路径里面不要包含空格,中文字符,否则汇报URI错误)。
[root@SIT-KVM01 ~]# eval `ssh-agent`Agent pid 30714[root@SIT-KVM01 ~]# ssh-add .ssh/id_rsaIdentity added: .ssh/id_rsa (.ssh/id_rsa)[root@SIT-KVM01 ~]# export LIBGUESTFS_BACKEND=direct[root@SIT-KVM01 vmfs]# virt-v2v -i vmx -it ssh "ssh://root@10.xxx.128.145/vmfs/volumes/553503c1-37053e17-f472-a0369f6/d1search02--10.xxx.128.55/d1search02--10.xxx.128.55.vmx" -os vmfs -of qcow2 --bridge br128[ 0.0] Opening the source -i vmx ssh://root@10.xxx.128.145/vmfs/volumes/553503c1-37053e17-f472-a0369f677064/d1searc[ 0.6] Creating an overlay to protect the source from being modified[ 1.0] Opening the overlay[ 5.6] Inspecting the overlay[ 19.4] Checking for sufficient free disk space in the guest[ 19.4] Estimating space required on target for each disk[ 19.4] Converting Red Hat Enterprise Linux Server release 6.5 (Santiago) to run on KVMvirt-v2v: This guest has virtio drivers installed.[ 110.6] Mapping filesystem data to avoid copying unused and blank areas[ 112.1] Closing the overlay[ 112.2] Assigning disks to buses[ 112.2] Checking if the guest needs BIOS or UEFI to boot[ 112.2] Initializing the target -o libvirt -os vmfs[ 112.2] Copying disk 1/1 to /vmfs/d1search02--10.xxx.128.55-sda (qcow2)(100.00/100%)[2321.3] Creating output metadataPool vmfs refreshedDomain d1search02--10.xxx.128.55 defined from /tmp/v2vlibvirt56ad9d.xml[2321.4] Finishing off[root@SIT-KVM01 ~]# virt-v2v -i vmx -it ssh "ssh://root@10.xxx.128.145/vmfs/volumes/553503c1-37053e17-f472-a0369f677064/sitdns2 --10.xxx.128.203/sitdns2 --10.xxx.128.203.vmx" -os vmfs -of qcow2 --bridge br128[ 0.0] Opening the source -i vmx ssh://root@10.xxx.128.145/vmfs/volumes/553503c1-37053e17-f472-a0369f677064/sitdns2 --10.xxx.128.203/sitdns2 --10.xxx.128.203.vmxvirt-v2v: error: remote vmx‘ssh://root@10.xxx.128.145/vmfs/volumes/553503c1-37053e17-f472-a0369f677064/sitdns2--10.xxx.128.203/sitdns2 --10.xxx.128.203.vmx’ could not be parsed as aURI
5、查看迁移完成的虚拟机。
[root@SIT-KVM01 ~]# virsh list --allId Name State----------------------------------------------------1 d1test-10.xxx.128.213 running2 d1rongyiwang-10.xxx.128.135 running3 d1search02--10.xxx.128.55 running4 D1openAPI--10.xxx.128.239--IBM running5 d1search04-10.xxx.128.136 running
第二种方法:将虚拟机导出为OVF模板,然后转换为KVM。
[root@SIT-KVM01 OVF]# virt-v2v -i ova 'sitdns2 --10.xxx.128.203' -os vmfs -of qcow2 -b br128[ 0.0] Opening the source -i ova sitdns2 --10.xxx.128.203[ 6.4] Creating an overlay to protect the source from being modified[ 6.5] Opening the overlay[ 10.1] Inspecting the overlay[ 21.5] Checking for sufficient free disk space in the guest[ 21.5] Estimating space required on target for each disk[ 21.5] Converting Red Hat Enterprise Linux Server release 6.5 (Santiago) to run on KVMvirt-v2v: This guest has virtio drivers installed.[ 83.2] Mapping filesystem data to avoid copying unused and blank areas[ 85.5] Closing the overlay[ 85.5] Assigning disks to buses[ 85.5] Checking if the guest needs BIOS or UEFI to boot[ 85.5] Initializing the target -o libvirt -os vmfs[ 85.6] Copying disk 1/1 to /vmfs/sitdns2 --10.xxx.128.203-sda (qcow2)(100.00/100%)[ 247.0] Creating output metadataPool vmfs refreshedDomain sitdns2 --10.xxx.128.203 defined from /tmp/v2vlibvirt3a4adb.xml[ 247.0] Finishing off[root@SIT-KVM01 OVF]# virsh list --allId Name State----------------------------------------------------1 d1test-10.xxx.128.213 running2 d1rongyiwang-10.xxx.128.135 running3 d1search02--10.xxx.128.55 running4 D1openAPI--10.xxx.128.239--IBM running5 d1search04-10.xxx.128.136 running6 d1search03--10.xxx.128.56 running7 sitdns2 --10.xxx.128.203 running
第三种方法:将虚拟机导出为OVF模板,然后将磁盘文件转换为KVM磁盘文件格式,再导入KVM。
[root@SIT-KVM01 OVF]#qemu-img convert -f vmdk -O qcow2 redhat-6.5--10.xxx.128.136-disk1.vmdk redhat-6.5--10.xxx.128.136-disk1.qcow2[root@SIT-KVM01 OVF]#virt-manager
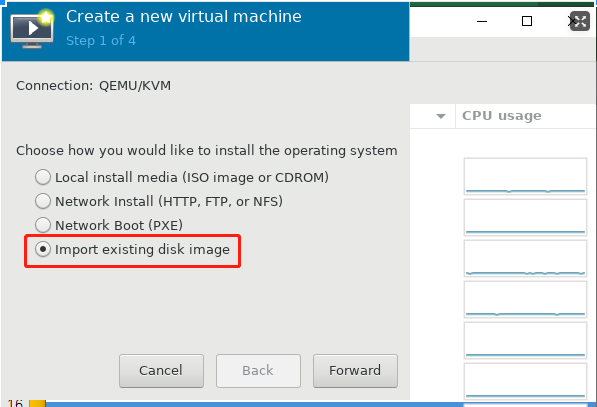
https://access.redhat.com/articles/1353463
查看KVM支持machine列表
root@sit-kvm04:/vmfs# /usr/libexec/qemu-kvm -M help
Supported machines are:
microvm microvm (i386)
pc-i440fx-zesty Ubuntu 17.04 PC (i440FX + PIIX, 1996)
pc-i440fx-yakkety Ubuntu 16.10 PC (i440FX + PIIX, 1996)
pc-i440fx-xenial Ubuntu 16.04 PC (i440FX + PIIX, 1996)
pc-i440fx-wily Ubuntu 15.04 PC (i440FX + PIIX, 1996)
pc-i440fx-trusty Ubuntu 14.04 PC (i440FX + PIIX, 1996)
ubuntu Ubuntu 20.04 PC (i440FX + PIIX, 1996) (alias of pc-i440fx-focal)
pc-i440fx-focal Ubuntu 20.04 PC (i440FX + PIIX, 1996) (default)
pc-i440fx-focal-hpb Ubuntu 20.04 PC (i440FX + PIIX +host-phys-bits=true, 1996)
pc-i440fx-eoan Ubuntu 19.10 PC (i440FX + PIIX, 1996)
pc-i440fx-eoan-hpb Ubuntu 19.10 PC (i440FX + PIIX +host-phys-bits=true, 1996)
排错一
root@sit-kvm04:/vmfs# virsh start D1ConfigManage—10.201.129.126
error: Failed to start domain D1ConfigManage—10.201.129.126
error: internal error: qemu unexpectedly closed the monitor: 2020-12-24T02:40:06.716466Z qemu-system-x86_64: -blockdev {“driver”:”file”,”filename”:”/vmfs/D1ConfigManage—10.201.129.126-sda”,”node-name”:”libvirt-2-storage”,”cache”:{“direct”:true,”no-flush”:false},”auto-read-only”:true,”discard”:”unmap”}: Could not open ‘/vmfs/D1ConfigManage—10.201.129.126-sda’: Permission denied
修改为

