- Kubernetes Network Course FAQ
- TOPO:
- install:
- 使用docker创建四个不带网卡的容器
docker run -t -i -d —name vm01 —net=none —privileged burlyluo/nettoolbox:v1 /bin/bash
docker run -t -i -d —name vm02 —net=none —privileged burlyluo/nettoolbox:v1 /bin/bash
docker run -t -i -d —name vm03 —net=none —privileged burlyluo/nettoolbox:v1 /bin/bash
docker run -t -i -d —name vm04 —net=none —privileged burlyluo/nettoolbox:v1 /bin/bash
docker run -t -i -d —name vm05 —net=none —privileged burlyluo/nettoolbox:v1 /bin/bash
docker run -t -i -d —name vm06 —net=none —privileged burlyluo/nettoolbox:v1 /bin/bash
#创建OVS网桥
ovs-vsctl add-br vswitch0
ovs-vsctl add-br vswitch1
#使用ovs-docker工具给容器添加网卡到ovs网桥
ovs-docker add-port vswitch0 eth0 vm01 —ipaddress=192.168.1.11/24
ovs-docker add-port vswitch0 eth0 vm02 —ipaddress=192.168.1.12/24
ovs-docker add-port vswitch1 eth0 vm03 —ipaddress=192.168.1.13/24
ovs-docker add-port vswitch1 eth0 vm04 —ipaddress=192.168.1.14/24
ovs-docker add-port vswitch0 eth0 vm05 —ipaddress=192.168.1.15/24
ovs-docker add-port vswitch0 eth0 vm06 —ipaddress=192.168.1.16/24
#连接vswitch0和vswitch1
ovs-vsctl add-port vswitch0 patch_to_vswitch1
ovs-vsctl add-port vswitch1 patch_to_vswitch0 - set vlan tag:
- 为vm01、vm02对应的ovs端口设置tag为100,为vm03、vm04对应的ovs端口设置tag为200
- ovs-vsctl list interface 6eef85c4718a4_l | grep container_id
- ovs-vsctl set port 6eef85c4718a4_l tag=200
- ovs-vsctl list interface 39c0765e1c964_l | grep container_id
- ovs-vsctl set port 39c0765e1c964_l tag=100
- ovs-vsctl list interface 2720669d9c064_l | grep container_id
- ovs-vsctl set port 2720669d9c064_l tag=200
- ovs-vsctl list interface f4e1ae64ef704_l | grep container_id
- ovs-vsctl set port f4e1ae64ef704_l tag=100
- 或者采用下变的CLI:[这里 不要对vm06做任何标签处理!!!,不然抓不到802.1Q的包]
—————————————————————————————————————————————————————————————————————
ovs-docker set-vlan vswitch0 eth0 vm01 100
ovs-docker set-vlan vswitch0 eth0 vm02 200
ovs-docker set-vlan vswitch1 eth0 vm03 100
ovs-docker set-vlan vswitch1 eth0 vm04 200
ovs-docker set-vlan vswitch0 eth0 vm05 100
—————————————————————————————————————————————————————————————————————
#设置网桥之间的patch端口trunk100,200
ovs-vsctl set port patch_to_vswitch1 VLAN_mode=trunk
ovs-vsctl set port patch_to_vswitch0 VLAN_mode=trunk - 测试Trunk:
ovs-vsctl set port patch_to_vswitch0 trunk=200
ovs-vsctl set port patch_to_vswitch1 trunk=200
#查看flow table
$ ovs-ofctl dump-flows vswitch0
NXST_FLOW reply (xid=0x4):
cookie=0x0, duration=2504.456s, table=0, n_packets=292, n_bytes=36188, idle_age=410, priority=0 actions=NORMAL - 附一些OVS配置命令
#设置VLAN mode
ovs-vsctl set port VLAN_mode=trunk|access|native-tagged|native-untagged
#设置VLAN tag
ovs-vsctl set port tag=
#设置VLAN trunk
ovs-vsctl set port trunk=100,200
#删除port的配置
ovs-vsctl remove port
Kubernetes Network Course FAQ
20201118:
课程主题:开课介绍+IP And MAC介绍。
课程准备:eNSP环境,Wireshark,VirtualBox,eNSP.chm。
课程作业:使用eNSP探索MAC学习过程。
课程课件:链接:https://pan.baidu.com/s/1P6AEIGfaLWIPknjsjq1nQQ 提取码:k8sn
20201120:
课程主题:Kubernetes Network IPVLAN And MACVLAN
课程准备:1.Linux环境,kernel>=4.4。2.OpenStack知识预备。
课程作业:
课程课件:链接:https://pan.baidu.com/s/1bqCeiWl8sxAj0xp5velYYg 提取码:k8sn
20201122:
课程主题:Kubernetes Linux Network
课程准备:2 vm。
课程作业:
课程课件:链接:https://pan.baidu.com/s/1qcKCsK5D9ArdMPGYr8h0fA 提取码:k8sn
20201125:
课程主题:Kubernetes Network ARP
课程准备:2 vm + eNSP。
课程作业:
课程课件:链接:https://pan.baidu.com/s/1cAUF-iCkvY2Q7tzWTzRKHg 提取码:k8sn
20201127:
课程主题:Kubernetes Network SNAT And DNAT
课程准备:2vm + eNSP
课程作业:
课程课件:链接:https://pan.baidu.com/s/1DqawLA37JtUGRjFZCFhigQ 提取码:k8sn
20201129:
课程主题:Kubernetes Network Route And Switch
课程准备:2vm+eNSP
课程作业:
课程课件:链接:https://pan.baidu.com/s/1PeHbfkTmZkZ8mURTMBsTFg 提取码:k8sn
20201202:
课程主题:BGP RR
课程准备:2vm+eNSP
课程作业:
课程课件:链接:https://pan.baidu.com/s/1PeHbfkTmZkZ8mURTMBsTFg 提取码:k8sn
20201204:
课程主题:Kubernetes Network - DNS
课程准备:1vm+eNSP
课程作业:
课程课件:链接:https://pan.baidu.com/s/1bqYxI4_h6s337IIrMAXACg 提取码:k8sn
20201206:
课程主题:VLAN介绍
课程准备:1vm+eNSP
课程作业:
课程课件:链接:https://pan.baidu.com/s/1TDAOPB9ZZZhutZx07DTHGg 提取码:k8sn
20201209:
课程主题:DHCP
课程准备:1VM + eNSP
课程作业:
课程课件:链接:https://pan.baidu.com/s/1GzZsx4-nZQrPcp-JAAt1Lw 提取码:k8sn
20201211:
课程主题:OVS精讲
课程准备:1VM+1桌面版CentOS7
课程作业:
课程课件:链接:https://pan.baidu.com/s/18KZdSfr7jZZPIpB8lgDtOg 提取码:k8sn
20201213:
课程主题:VxLAN And Flannel
课程准备:1Master+1Node+eNSP[CE12800]
课程作业:
课程课件:链接:https://pan.baidu.com/s/1IaygipkJpJrbfrg172k2gw 提取码:k8sn
20201216:
课程主题:iptables + TCP 与UDP
课程准备:1VM
课程作业:
课程课件:链接:https://pan.baidu.com/s/16Fesie6B5Atinp-BqUf27Q 提取码:k8sn
20201218:
课程主题:DANM-Muti Interface CNI
课程准备:1Master+1Node
课程作业:
课程课件:链接:https://pan.baidu.com/s/1JNT6kFBiqoJ0hkvvfuU_jA 提取码:k8sn
20201220:
课程主题:Calico And BGP
课程主备:1Master+1Node
课程作业:
课程连接:链接:https://pan.baidu.com/s/1ShsdzA1GV4600Fy2zqIOQg 提取码:k8sn
20201225:
课程主题:Kubernetes Service
课程准备:1Master+1Node
课程作业:
课程链接:链接:https://pan.baidu.com/s/137i-3pjzKMwgRg93aSroVQ 提取码:k8sn
FAQ1:20201111-eNSP
eNSP(Enterprise Network Simulation Platform)是一款由华为提供的免费的、可扩展的、图形化的网络设备仿真平台,主要对企业网路由器、交换机、WLAN等设备进行软件仿真,完美呈现真实设备部署实景,支持大型网络模拟,让你有机会在没有真实设备的情况下也能够开展实验测试,学习网络技术。
在这里顺便说一下eNSP的原理。大家可以提前ready自己的环境。目前eNSP只支持Win下边安装,推荐使用Win7-SP1的OS[其他winOS也支持,但稳定性未知]。
eNSP是来自于华为企业网设备的一款模拟器,主要是实现华为AR系列路由器和S系列的交换机(当然也包含CE12800这种高级交换机[不太稳定])模拟。AR系列的路由器的运行需要依靠VirtualBox来运行对应的镜像,所以我们需要安装对应版本的VirtualBox。同时该模拟器也提供接口抓包,使用开源软件Wireshark,所以我们也建议安装Wireshark,这里的软件版本建议使用eNSP自带的版本为主,当然也欢迎大家自己去摸索(主要是工具路径的指引)。
关于相关软件版本说明见:具体下载地址为:
链接:https://pan.baidu.com/s/1mgeBP1YWK1vGPSYrnzGY5Q
提取码:k8sn
https://cloud.189.cn/t/Q7f2Ubfy2qyq (访问码:yz3n) —- 推荐使用这个。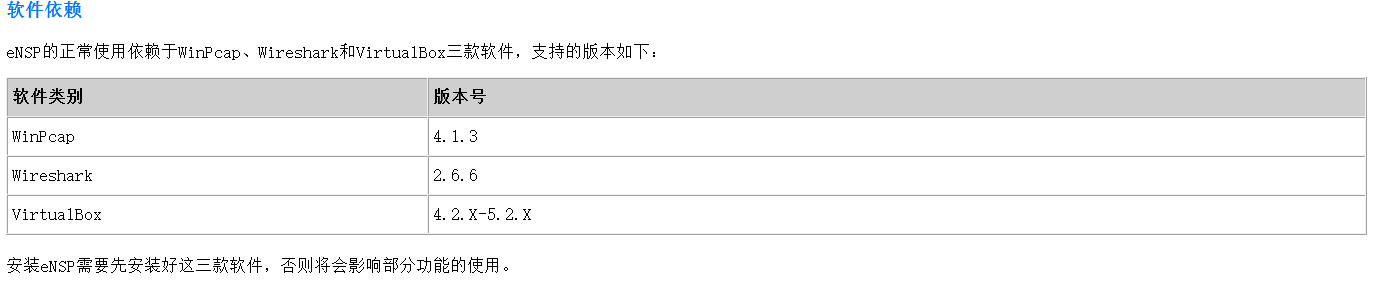
具体的说明参考网盘文档:eNSP.chm
链接:https://pan.baidu.com/s/1bREsaF4Zu_-MZAe3OnpLPg
提取码:k8sn
安装完成以后,通过运行AR路由器来观察是否正常工作:
具体表现为,在启动[点击左边栏中图标直接拖拽到右边空白的区域,然后右键启动]AR路由器后: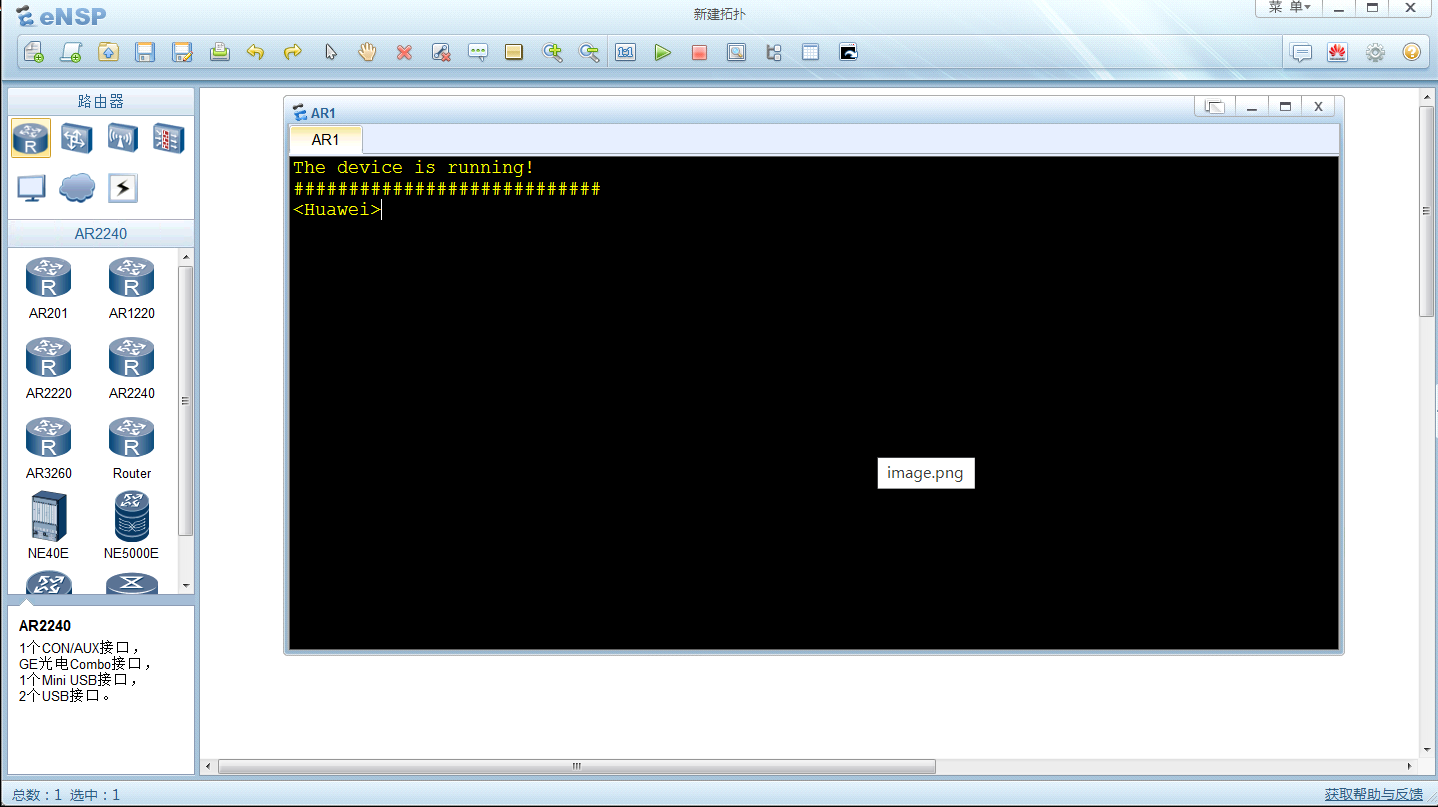
可能涉及的问题:
1.我电脑上已经安装了VMWare,我再安装VirtualBox是否会有影响?
Answer:不影响。
2.我是MAC系统,eNSP不支持为该怎么办?
Answer:eNSP的确没有MAC系统对应的发行版,所以需要自己去找相应的WIN资源,不过是否支持在MAC上安装虚机来实现,需要自己尝试。需要考虑的是:我们eNSP运行AR系列路由器的时候,需要借助virtualbox来运行对应的AR路由器,这样就是需要支持虚机中嵌套虚机的问题了。还有需要考虑性能问题,因为涉及到双重嵌套的问题。
3.安装eNSP的时候,提示关联的软件版本不支持,怎么办?
Answer:按照提示更换相关联的软件的版本。请认真阅读安装过程中出现的提示。
4.我能不能使用vmware来代替virtualbox?
Answer:不推荐,没有对接的案例供参考。有余力的情况下,可以自己去折腾。
FAQ2:本次课程涉及的软件及环境:
Local PC:8G+
CentOS 7 :http://www.centos.org/ version>=7.4 Kernel>=4.4
Wireshark:https://www.wireshark.org/
Xshell:https://www.netsarang.com/en/xshell/
Notepad++:https://notepad-plus-plus.org/
VMWare:https://my.vmware.com/en/web/vmware/downloads
VirtualBox:https://www.virtualbox.org/
Docker-CE:https://docs.docker.com/install/linux/docker-ce/centos/
Docker-CE:https://yq.aliyun.com/articles/110806
Kubernetes:V1.16.0
Mirrors:https://opsx.alibaba.com/mirror
Note:https://www.yinxiang.com/download/
eNSP:https://pan.baidu.com/s/1n2nZbeMDP49CE6ZDRxZHcA Extraction code:k8sn
RFC Docs:https://ietf.org/standards/rfcs/
HTTP2:https://http2.github.io/
Kubernetes Docs:https://github.com/kubernetes/Kubernetes
https://kubernetes.io/docs/concepts/
https://kubernetes.io/docs/tasks/
https://kubernetes.io/docs/reference/
https://kubernetes.io/docs/tutorials/
Flannel Docs:https://github.com/coreos/flannel
https://coreos.com/flannel/docs/latest/
Calico Docs:https://www.projectcalico.org/
https://github.com/projectcalico/calico
Cilium Docs:https://cilium.io/
https://github.com/cilium/cilium
DANM Docs:https://www.gitmemory.com/nokia/danm
https://github.com/nokia/danm
Nuage Docs:https://www.nuagenetworks.net/
https://github.com/nuagenetworks
Multus Docs: https://01.org/kubernetes/building-blocks/multus-cni
https://github.com/intel/multus-cni
Genie Docs: https://asciinema.org/a/118191
https://github.com/cni-genie/CNI-Genie
IP:https://tools.ietf.org/html/rfc791
RIP:https://tools.ietf.org/html/rfc2453
OSPF:https://tools.ietf.org/html/rfc2328
BGP:https://tools.ietf.org/html/rfc1105
3GPP:https://www.3gpp.org/
FAQ3:CentOS7 kernel 升级
[升级前请务必确认自己环境,商业环境慎用!]
Linux的kernel需要在4.4+以上,才能提供稳定的ipvlan方案。
升级kernel:升级为最新版本的kernel。
uname -r
rpm —import https://www.elrepo.org/RPM-GPG-KEY-elrepo.org
rpm -Uvh http://www.elrepo.org/elrepo-release-7.0-3.el7.elrepo.noarch.rpm
yum —enablerepo=elrepo-kernel install kernel-ml-devel kernel-ml -y
grub2-set-default 0
reboot
uname -r
FAQ5:文档密码
课程中所有PDF课件的密码均为:network
FAQ6:OpenVSwitch 安装[2.5.2版本]
setenforce 0
yum -y install make gcc openssl-devel autoconf automake rpm-build redhat-rpm-config
yum -y install python-devel openssl-devel kernel-devel kernel-debug-devel libtool wget
wget http://openvswitch.org/releases/openvswitch-2.5.2.tar.gz
mkdir -p ~/rpmbuild/SOURCES
cp openvswitch-2.5.2.tar.gz ~/rpmbuild/SOURCES/
cd ~/rpmbuild/SOURCES
tar xvfz openvswitch-2.5.2.tar.gz
sed ‘s/openvswitch-kmod, //g’ openvswitch-2.5.2/rhel/openvswitch.spec > openvswitch-2.5.2/rhel/openvswitch_no_kmod.spec
#编译之前请修改为如图所示:
vi /usr/include/linux/netfilter/nf_conntrack_sctp.h
rpmbuild -bb —nocheck openvswitch-2.5.2/rhel/openvswitch_no_kmod.spec
yum localinstall ~/rpmbuild/RPMS/x86_64/openvswitch-2.5.2-1.x86_64.rpm
systemctl restart openvswitch
另外我们可以使用RDO的REPO来安装:
yum install -y https://www.rdoproject.org/repos/rdo-release.rpm
sudo yum install openvswitch libibverbs
sudo systemctl enable —now openvswitch
wget https://raw.githubusercontent.com/openvswitch/ovs/master/utilities/ovs-docker
chmod +x ovs-docker
mv ovs-docker /usr/bin/ovs-docker
FAQ7:OVS抓包问题:
在说明OVS抓包的过程中,我们经过在ROOT NS中使用tcpdump -n -e -i any icmp or arp看不到802.1q的包。所以暂时无法用来验证我们OVS实现的VLAN相关的属性,经过查询,我们需要采用OVS的端口镜像的来抓取相对应的数据包。
创建过程:
yum -y install ntp
yum -y install make gcc openssl-devel autoconf automake rpm-build redhat-rpm-config
yum -y install python-devel openssl-devel kernel-devel kernel-debug-devel libtool wget
mkdir -p ~/rpmbuild/SOURCES
wget http://openvswitch.org/releases/openvswitch-2.5.0.tar.gz
cp openvswitch-2.5.0.tar.gz ~/rpmbuild/SOURCES/
tar xfz openvswitch-2.5.0.tar.gz
sed ‘s/openvswitch-kmod, //g’ openvswitch-2.5.0/rhel/openvswitch.spec > openvswitch-2.5.0/rhel/openvswitch_no_kmod.spec
rpmbuild -bb —nocheck openvswitch-2.5.0/rhel/openvswitch_no_kmod.spec
yum -y localinstall ~/rpmbuild/RPMS/x86_64/openvswitch-2.5.0-1.x86_64.rpm
systemctl enable openvswitch.service
systemctl start openvswitch.service
systemctl status openvswitch.service
systemctl restart ntpd
systemctl status ntpd
TOPO:
vm06100 /vm05 /100 | / 200vm01------vswtich0-----vm02100|200100|200vm03------vswtich1-----vm04100 200
install:
使用docker创建四个不带网卡的容器
docker run -t -i -d —name vm01 —net=none —privileged burlyluo/nettoolbox:v1 /bin/bash
docker run -t -i -d —name vm02 —net=none —privileged burlyluo/nettoolbox:v1 /bin/bash
docker run -t -i -d —name vm03 —net=none —privileged burlyluo/nettoolbox:v1 /bin/bash
docker run -t -i -d —name vm04 —net=none —privileged burlyluo/nettoolbox:v1 /bin/bash
docker run -t -i -d —name vm05 —net=none —privileged burlyluo/nettoolbox:v1 /bin/bash
docker run -t -i -d —name vm06 —net=none —privileged burlyluo/nettoolbox:v1 /bin/bash
#创建OVS网桥
ovs-vsctl add-br vswitch0
ovs-vsctl add-br vswitch1
#使用ovs-docker工具给容器添加网卡到ovs网桥
ovs-docker add-port vswitch0 eth0 vm01 —ipaddress=192.168.1.11/24
ovs-docker add-port vswitch0 eth0 vm02 —ipaddress=192.168.1.12/24
ovs-docker add-port vswitch1 eth0 vm03 —ipaddress=192.168.1.13/24
ovs-docker add-port vswitch1 eth0 vm04 —ipaddress=192.168.1.14/24
ovs-docker add-port vswitch0 eth0 vm05 —ipaddress=192.168.1.15/24
ovs-docker add-port vswitch0 eth0 vm06 —ipaddress=192.168.1.16/24
#连接vswitch0和vswitch1
ovs-vsctl add-port vswitch0 patch_to_vswitch1
ovs-vsctl add-port vswitch1 patch_to_vswitch0
ovs-vsctl set interface patch_to_vswitch1 type=patch
ovs-vsctl set interface patch_to_vswitch0 type=patch
ovs-vsctl set interface patch_to_vswitch0 options:peer=patch_to_vswitch1
ovs-vsctl set interface patch_to_vswitch1 options:peer=patch_to_vswitch0
ovs-vsctl show
[root@k8s-2 ~]# ovs-vsctl show
d5db5884-f041-4659-93ab-e212321eaf2e
Bridge “vswitch1”
Port “vswitch1”
Interface “vswitch1”
type: internal
Port “8e0c56dadea74_l”
Interface “8e0c56dadea74_l”
Port “9a8d14b0ba214_l”
Interface “9a8d14b0ba214_l”
Port “patch_to_vswitch0”
Interface “patch_to_vswitch0”
type: patch
options: {peer=”patch_to_vswitch1”}
Bridge “vswitch0”
Port “f391e184ff8f4_l”
Interface “f391e184ff8f4_l”
Port “vswitch0”
Interface “vswitch0”
type: internal
Port “2d11f9e3a8ff4_l”
Interface “2d11f9e3a8ff4_l”
Port “patch_to_vswitch1”
Interface “patch_to_vswitch1”
type: patch
options: {peer=”patch_to_vswitch0”}
ovs_version: “2.5.0”
set vlan tag:
为vm01、vm02对应的ovs端口设置tag为100,为vm03、vm04对应的ovs端口设置tag为200
ovs-vsctl list interface 6eef85c4718a4_l | grep container_id
external_ids : {container_id=”vm04”, container_iface=”eth0”}
ovs-vsctl set port 6eef85c4718a4_l tag=200
ovs-vsctl list interface 39c0765e1c964_l | grep container_id
external_ids : {container_id=”vm02”, container_iface=”eth0”}
ovs-vsctl set port 39c0765e1c964_l tag=100
ovs-vsctl list interface 2720669d9c064_l | grep container_id
external_ids : {container_id=”vm03”, container_iface=”eth0”}
ovs-vsctl set port 2720669d9c064_l tag=200
ovs-vsctl list interface f4e1ae64ef704_l | grep container_id
external_ids : {container_id=”vm01”, container_iface=”eth0”}
ovs-vsctl set port f4e1ae64ef704_l tag=100
或者采用下变的CLI:[这里 不要对vm06做任何标签处理!!!,不然抓不到802.1Q的包]
—————————————————————————————————————————————————————————————————————
ovs-docker set-vlan vswitch0 eth0 vm01 100
ovs-docker set-vlan vswitch0 eth0 vm02 200
ovs-docker set-vlan vswitch1 eth0 vm03 100
ovs-docker set-vlan vswitch1 eth0 vm04 200
ovs-docker set-vlan vswitch0 eth0 vm05 100
—————————————————————————————————————————————————————————————————————
#设置网桥之间的patch端口trunk100,200
ovs-vsctl set port patch_to_vswitch1 VLAN_mode=trunk
ovs-vsctl set port patch_to_vswitch0 VLAN_mode=trunk
ovs-vsctl set port patch_to_vswitch0 trunk=100,200
ovs-vsctl set port patch_to_vswitch1 trunk=100,200
#测试抓包需要使用的OVS的端口镜像功能:
把vm01 ping vm03的流量镜像到vm06上:
ovs-vsctl — —id=@patch_to_vswitch1 get port patch_to_vswitch1 — —id=@d324d50982cc4_l get port d324d50982cc4_l — —id=@m create mirror name=m0 select-all=true output-port=@d324d50982cc4_l — set bridge vswitch0 mirrors=@m
#//说明:
创建mirror
指定mirror名称,name={name}
指定流量:
select-all: true,表示此bridge上的所有流量;
select-dst-port: 镜像从此port离开的流量;
select-src-port: 镜像从此port进入的流量;
select-vlan: 镜像此VLAN下的数据流量。
指定镜像目的端口:
output-port: 流量镜像至此端口;
output-vlan: 流量镜像至指定vlan,镜像至指定VLAN时,原始tag会被剥离。
#//
测试Trunk:
ovs-vsctl set port patch_to_vswitch0 trunk=200
ovs-vsctl set port patch_to_vswitch1 trunk=200
#查看flow table
$ ovs-ofctl dump-flows vswitch0
NXST_FLOW reply (xid=0x4):
cookie=0x0, duration=2504.456s, table=0, n_packets=292, n_bytes=36188, idle_age=410, priority=0 actions=NORMAL
$ ovs-ofctl dump-flows vswitch1
NXST_FLOW reply (xid=0x4):
cookie=0x0, duration=46151.880s, table=0, n_packets=155, n_bytes=10998, idle_age=63, priority=0 actions=NORMAL
附一些OVS配置命令
#设置VLAN mode
ovs-vsctl set port VLAN_mode=trunk|access|native-tagged|native-untagged
#设置VLAN tag
ovs-vsctl set port tag=
#设置VLAN trunk
ovs-vsctl set port trunk=100,200
#删除port的配置
ovs-vsctl remove port
#设置VLAN trunk
ovs-vsctl set port trunk=100,200
#删除port的配置
ovs-vsctl remove port
FAQ8:

