在计算机网络上,OpenSSL是一个开放源代码的软件库包,应用程序可以使用这个包来进行安全通信,避免窃听,同时确认另一端连接者的身份。这个包广泛被应用在互联网的网页服务器上。
OpenSSL生成CSR
openssl req -new -nodes -newkey rsa:2048 -keyout server.key -out server.csr
C:\Windows\system32>openssl req -new -nodes -newkey rsa:2048 -keyout server.key -out server.csr
Generating a RSA private key
………..+++++
………………………………………………………………………………………………………………………………………………………………………………+++++
writing new private key to ‘server.key’
——-
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter ‘.’, the field will be left blank.
——-
Country Name (2 letter code) [AU]:CN
State or Province Name (full name) [Some-State]:Shanghai
Locality Name (eg, city) []:Shanghai
Organization Name (eg, company) [Internet Widgits Pty Ltd]:Shanghai Electronic Certificate Authority Center Co., Ltd.
Organizational Unit Name (eg, section) []:Prod Dept
Common Name (e.g. server FQDN or YOUR name) []:www.sheca.com
Email Address []:
Please enter the following ‘extra’ attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
完成之后当前目录下将产生两个文件:server.key 和 server.csr。请妥善保存这两个文件,请不要泄露server.key私钥文件。
OpenSSL生成中文CSR
首先需要修改openssl.cnf,添加修改以下参数
string_mask = utf8only
commonName_default = www.sheca.com
organizationName_default = 上海市数字证书认证中心有限公司
organizationalUnitName_default = 战略发展部
stateOrProvinceName_default = 上海
localityName_default = 上海
countryName_default = CN
修改完成之后将文件按照UTF8编码格式保存(可使用notepad++这类工具保存)
在准备好openssl.cnf文件之后输入指令
openssl req -utf8 -config openssl.cnf -newkey rsa:2048 -keyout server.key -out server.csr -nodes -batch
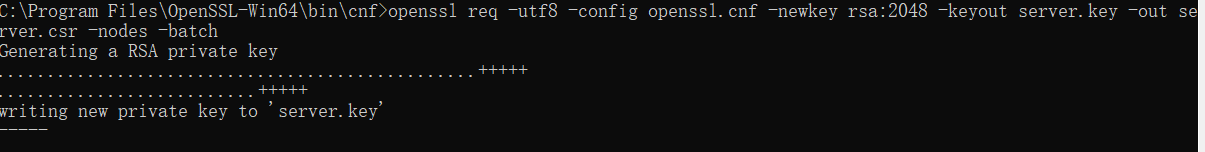
完成之后当前目录下将产生两个文件:server.key 和 server.csr。请妥善保存这两个文件,请不要泄露server.key私钥文件。
PKCS8格式私钥转为PKCS1格式
PKCS8格式私钥形如:
——-BEGIN PRIVATE KEY——-
MIIEvwIBADANBgkqhkiG9w0BAQEFAASCBKkwggSlAgEAAoIBAQDXmD8FWLvvWHBv
p6tG2TtBUd6v/Hp2MYSDgwRih7aUa8kSicogZBmHSVv+Xo1DIFe6zJjmIBm3jF/D
slNCDiAr9f8RXUDo62lnt0eo3K+1cIk16Kj/qrMVFtQaNAdUL1ugeglmQjx9TMMr
pSdiymnwmMsCgYEA7WuUpmfN7gtoXfOZUr23Aka8WHH5SiNxm1u2uKG6L6wwlPiW
39u6Urq6lj1tnhxxua3oJuoeypWDdbSCiMkTVpolMsdOKaBKhBVLvZRXIFzgDMHh
b6xHZOaMxWpXeMGxuxrME3CUKmfradWCwELZKz8qXEA6+K5FL/SJpkqDFIkCgYEA
uoo6zRfuVLep4Bq/vNOxSxgb2EPtd3Wp4G2h/7wuEPbzuocz9TwGV1vKOPupqP/v
9vYNB3/mviX0LCleGoJbv2F6580RWSp0Eojhfg4uvbECm75bUdwFPEEeluiuj86V
+qB1aTHSiKf52bTW+xnaIz5YC4tUAPSZZvMi8jHHhHcCgYAVqiLNdQAIFS95KA6T
zQtmA6dnCAwgBwHU3iD/NfkRZCELwOH6+7IKhJSPEyCQRp9gViZNAoroJk7/e+FT
AF0/GlIGCPMjCiL7Nc1A/cAVSEF3OoNRYXzQ8apYxGU4GBHR5ESW8nn6YdarVoN+
dkvWoHuVTbzYqZPiplBFRA/GBQ==
——-END PRIVATE KEY——-
PKCS1格式私钥形如:
——-BEGIN RSA PRIVATE KEY——-
MIIEpQIBAAKCAQEA15g/BVi771hwb6erRtk7QVHer/x6djGEg4MEYoe2lGvJEonK
IGQZh0lb/l6NQyBXusyY5iAZt4xfw7JTQg4gK/X/EV1A6OtpZ7dHqNyvtXCJNeio
/6qzFRbUGjQHVC9boHoJZkI8fUzDK1jV7vkkR7BKafKfnvGufxj3zk3FEQaOrG3M
VEVMOxSf87PmjcncDzweRuucJ1iHRWLdLJlmalsWIwOHQ7tM2nP1PCrxua23MZvz
jZvqxOcLI2jv3Kw6DjtGRrvAyvn9B+M6r6VJ8xtX053kauUiS+5e9BXdsGAbpB/C
WxSjH8WVQqkd5igtWn8IILcYzc1iZ5JwOwAF0wIDAQABAoIBAQCEWmGt/Zh6ShfU
gbFCqd8C8OkcuclT6Jrs4i015jCgi6UnYspp8JjLAoGBAO1rlKZnze4LaF3zmVK9
twJGvFhx+UojcZtbtrihui+sMJT4lt/bulK6upY9bZ4ccbmt6CbqHsqVg3W0gojJ
E1aaJTLHTimgSoQVS72UVyBc4AzB4W+sR2TmjMVqV3jBsbsazBNwlCpn62nVgsBC
2Ss/KlxAOviuRS/0iaZKgxSJAoGBALqKOs0X7lS3qeAav7zTsUsYG9hD7Xd1qeBt
of+8LhD287qHM/U8Bldbyjj7qaj/7/b2DQd/5r4l9CwpXhqCW79heufNEVkqdBKI
4X4OLr2xApu+W1HcBTxBHpboro/OlfqgdWkx0oin+dm01vsZ2iM+WAuLVAD0mWbz
IvIxx4R3AoGAFaoizXUACBUveSgOk80LZgOnZwgMIAcB1N4g/zX5EWQhC8Dh+vuy
CoSUjxMgkEafYFYmTQKK6CZO/3vhUwBdPxpSBgjzIwoi+zXNQP3AFUhBdzqDUWF8
0PGqWMRlOBgR0eRElvJ5+mHWq1aDfnZL1qB7lU282KmT4qZQRUQPxgU=
——-END RSA PRIVATE KEY——-
通过以下指令可做格式转换:
openssl rsa -in PKCS8.key -out PKCS1.key
**
查看服务器证书安装状态
openssl s_client -connect www.sheca.com:443
通过返回信息certificate chain字段能够查看到两个或两个以上不同证书信息即为正确安装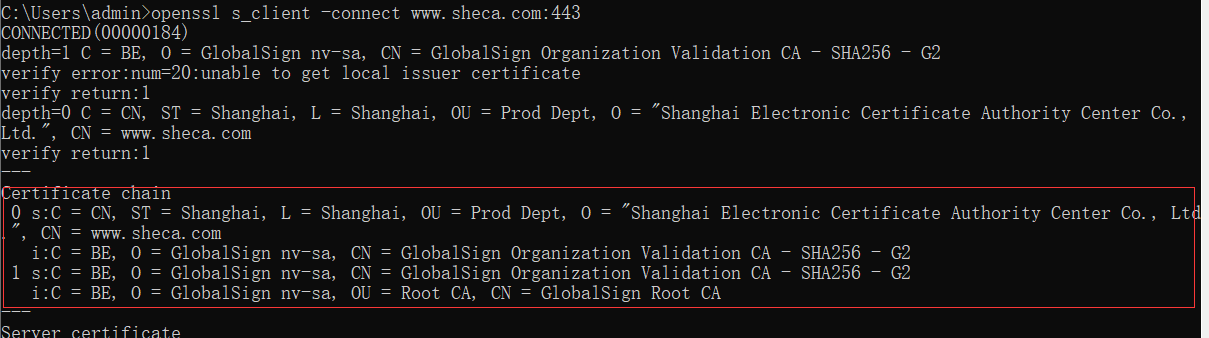
从PFX(PKCS12)文件中,提取出私钥和服务器证书
将PFX文件转为一个PEM文件
openssl pkcs12 -info -in rsaovg3.good.sheca.com.pfx -nodes -out server.pem
导出私钥文件
openssl rsa -in server.pem -out private.key
导出服务器证书文件
openssl x509 -in server.pem -out public.crt
查看服务器证书信息
openssl x509 -in public.crt -noout -text
查看PKCS12文件内容
openssl pkcs12 -info -in rsaovg3.good.sheca.com.pfx
将PEM文件合成为PFX(PKCS12)文件
需要合成PFX文件,必须有私钥文件server.key和服务器证书文件server.crt。此外,还需要中间证书(如有交叉证书要将交叉证书一起放入此文件)chain.crt,以保证PFX文件中直接包含了中间证书。
openssl pkcs12 -export -out server.pfx -inkey server.key -in server.crt -certfile chain.crt

