通知文件:关于举办2020年度阜阳市网络与信息安全管理职业技能大赛的通知.pdf
理论题库:2020题库.xlsx
操作题
1.jpeg √
附件:1.jpeg.zip
010editor 打开,搜索 flag:flag{w9ii12y3jbdjh123}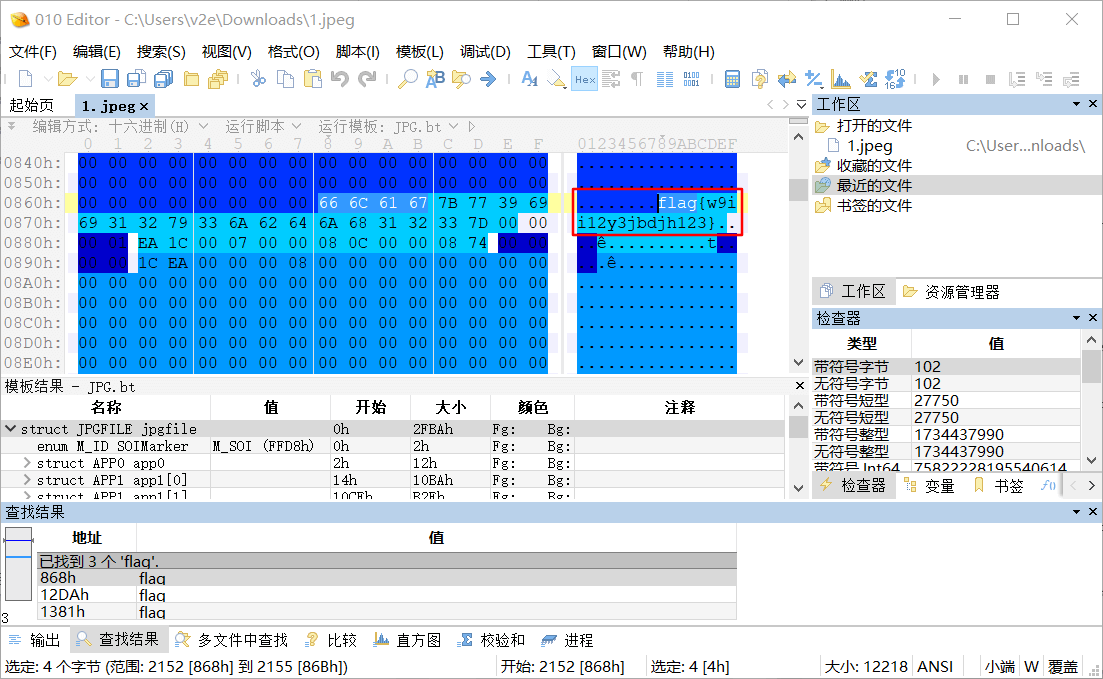
crypto(base64换编码表)√
请解密这段密文:FqsCFkufDSQgSf4NSgWFGPvMP6FCHwg= 附件:
这是泄漏的一段明文:!QAZ@WSX#EDC$RFV%TGB^YHN&UJM*IK<(OL>)P:?_{"+}|`1qaz2wsx3edc4rfv5tgb6yhn7ujm8ik,9ol.0p;/-['=]\The problem is that programs_width is a list. programs_width = list(). If none of these if statements if prog_width == '342' When you read an English book, you often come across new words. You might try to guess what the words mean from the words you know, but when you cannot guess the meanings of new words at all, what should you do?和对应的密文:8P51AN1SOhXByOy39596PVPOyg9LAOCE9MP+IUr9UfaeIgan+P0xRhbc8VibZ60sJA5xQwKfL3WMF6QgJqFjWSywDBFzG6lkKAriE6My/3MpH2laJ3up/PuwRPhJP6CM871dHj9uFAgXGSQXK6CCK21aJqbwJq5iJhbkGAygG21rJd1C86srJkTo871dHjKdDAhfSkKrF7ye83gXH6MfK2Xr/V19FV1oHjzM86bq87yeFSWM86Mq87WgDSyMHAPoK7QXGADXJ79pFhbkGAygG20bRU0wQfTd9d1SG6Po87MpKU1dFA5N865o84PoFjsrJjXXDqbpGdaXLAbh86bqK6Po86WpHAOXDAWdHkWf86zMKd1kHk9NJdlXAAbh86hrFjCg87ydLU1gHd1wKAPfJd1kG65g87yeFU1kHk9NJd1iFA5o86FdHjgXK6CM87KpJqyf87MpKU1yHqbk/21VKSTXKjCMHV1zHkOXDj5oHqbg86KhFSWf87yeFU1iFA5oGAzwJd1pFV1oFSJXKjbdF7QXDSTXDAsu/21kG65g87WeHkPuF21zHkOXF6vm
编写程序求解:
from mybase64 import *plain0 = """!QAZ@WSX#EDC$RFV%TGB^YHN&UJM*IK<(OL>)P:?_{"+}|`1qaz2wsx3edc4rfv5tgb6yhn7ujm8ik,9ol.0p;/-['=]\The problem is that programs_width is a list. programs_width = list(). If none of these if statements if prog_width == '342' When you read an English book, you often come across new words. You might try to guess what the words mean from the words you know, but when you cannot guess the meanings of new words at all, what should you do?"""cipher0 = """8P51AN1SOhXByOy39596PVPOyg9LAOCE9MP+IUr9UfaeIgan+P0xRhbc8VibZ60sJA5xQwKfL3WMF6QgJqFjWSywDBFzG6lkKAriE6My/3MpH2laJ3up/PuwRPhJP6CM871dHj9uFAgXGSQXK6CCK21aJqbwJq5iJhbkGAygG21rJd1C86srJkTo871dHjKdDAhfSkKrF7ye83gXH6MfK2Xr/V19FV1oHjzM86bq87yeFSWM86Mq87WgDSyMHAPoK7QXGADXJ79pFhbkGAygG20bRU0wQfTd9d1SG6Po87MpKU1dFA5N865o84PoFjsrJjXXDqbpGdaXLAbh86bqK6Po86WpHAOXDAWdHkWf86zMKd1kHk9NJdlXAAbh86hrFjCg87ydLU1gHd1wKAPfJd1kG65g87yeFU1kHk9NJd1iFA5o86FdHjgXK6CM87KpJqyf87MpKU1yHqbk/21VKSTXKjCMHV1zHkOXDj5oHqbg86KhFSWf87yeFU1iFA5oGAzwJd1pFV1oFSJXKjbdF7QXDSTXDAsu/21kG65g87WeHkPuF21zHkOXF6vm"""# 明文转为二进制串binstr = ""for i in plain0:binstr += "{:08b}".format(ord(i))# 求新的编码表# 二进制串每 6 位对应一个密文字符new_alphabet = ['?'] * 64for i in range(len(binstr) // 6):new_alphabet[int(binstr[i*6: i*6+6], 2)] = cipher0[i]# 用新的编码表解码bs64 = Base64(alphabet="".join(new_alphabet))print(bs64.base64decode("FqsCFkufDSQgSf4NSgWFGPvMP6FCHwg="))
flag{3as41$_CYi%Tfan}
key
黑客小A破解了一个邮箱,从邮箱里获取一个附件,名为e58cee651237c4b323b8ba88b96a1a1q flag格式:key{**} 附件:e58cee651237c4b323b8ba88b96a1a1q.zip
timu_841 √
NGY0ZTM0NTczNDM1NDI0NjQ3MzU0MjQ3NTk1NTQ0NDQ0YjM0MzQ1ODQxMzI0MzUwNDU1NTMzNTU0OTNkM2QzZA==
Base64解码:4f4e34573435424647354247595544444b3434584132435045553355493d3d3d
Hex -> ASCII:ON4W45BFG5BGYUDDK44XA2CPEU3UI===
Base32解码:synt%7BlPcW9phO%7D
URL解码:synt{lPcW9phO}
Rot13:flag{yCpJ9cuB}
timu_519 √
59574a4b443250324353584754485941564d4154584559564235465356335144575758545645563d
Hex -> ASCII:YWJKD2P2CSXGTHYAVMATXEYVB5FSV3QDWWXTVEV=
Rot13:LJWXQ2C2PFKTGULNIZNGKRLIO5SFI3DQJJKGIRI=
Base32 解码:ZmxhZyU3QmFZeEhwdTlpJTdE
Base64 解码:flag%7BaYxHpu9i%7D
URL 解码:flag{aYxHpu9i}
soeasy_re √
soeasy_re flag格式:flag{**} 附件:soeasy_re.zip
exeinfo 打开,64 bit elf,无壳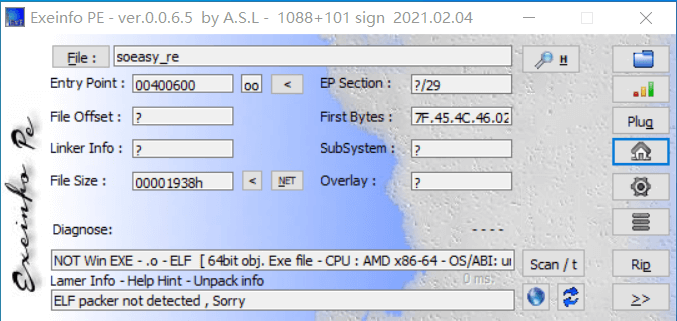
ida64 打开,发现关键代码
unsigned __int64 __fastcall main(int a1, char **a2, char **a3){char buf[40]; // [rsp+0h] [rbp-30h] BYREFunsigned __int64 v5; // [rsp+28h] [rbp-8h]v5 = __readfsqword(0x28u);read(0, buf, 0x26uLL);if ( strlen(buf) != 38 ) // flag 长度为38{puts("error");exit(0);}printf("input : %s\n", buf);sub_4006F6(buf, aKakalll); // 计算 flagif ( !strcmp(buf, s2) )printf("congratulation !");return __readfsqword(0x28u) ^ v5;}
size_t __fastcall sub_4006F6(const char *a1, const char *a2){char v2; // r13size_t result; // raxint i; // [rsp+1Ch] [rbp-24h]for ( i = 0; ; ++i ){result = strlen(a1);if ( i >= result )break;v2 = a1[i];a1[i] = v2 ^ a2[i % strlen(a2)]; // buf[i] = buf[i] ^ aKakalll[i % len(aKakalll[i])]}return result;}
.data:00000000006010A0 s2 db 0Dh,0Dh,0Ah ; DATA XREF: main+83↑o.data:00000000006010A3 db 6.data:00000000006010A4 db 17h.data:00000000006010A5 db 0Dh.data:00000000006010A6 db 0Ah.data:00000000006010A7 db 5Bh ; [.data:00000000006010A8 db 59h ; Y.data:00000000006010A9 db 5Ch ; \.data:00000000006010AA db 4.data:00000000006010AB db 5Eh ; ^.data:00000000006010AC db 0Fh.data:00000000006010AD db 5Eh ; ^.data:00000000006010AE db 5Ch ; \.data:00000000006010AF db 7.data:00000000006010B0 db 5Eh ; ^.data:00000000006010B1 db 2.data:00000000006010B2 db 5Dh ; ].data:00000000006010B3 db 5Dh ; ].data:00000000006010B4 db 55h ; U.data:00000000006010B5 db 0Fh.data:00000000006010B6 db 53h ; S.data:00000000006010B7 db 0Fh.data:00000000006010B8 db 5.data:00000000006010B9 db 5Ah ; Z.data:00000000006010BA db 0Dh.data:00000000006010BB db 5Ah ; Z.data:00000000006010BC db 0Ah.data:00000000006010BD db 59h ; Y.data:00000000006010BE db 59h ; Y.data:00000000006010BF db 52h ; R.data:00000000006010C0 db 5Bh ; [.data:00000000006010C1 db 5Ch ; \.data:00000000006010C2 db 8.data:00000000006010C3 db 0Fh.data:00000000006010C4 db 56h ; V.data:00000000006010C5 db 16h.data:00000000006010C5 _data ends
编写程序求 flag:
buf = [0x0D, 0x0D, 0x0A, 6, 0x17, 0x0D, 0x0A, 0x5B, 0x59, 0x5C, 4, 0x5E, 0x0F, 0x5E, 0x5C, 7, 0x5E, 2, 0x5D, 0x5D, 0x55, 0x0F, 0x53, 0x0F, 5, 0x5A, 0x0D, 0x5A, 0x0A, 0x59, 0x59, 0x52, 0x5B, 0x5C, 8, 0x0F, 0x56, 0x16]aKakalll = 'kakalll' # len(aKakalll[i]): 7for i in range(38):print(chr(buf[i] ^ ord(aKakalll[i % 7])), end='')
flag{af087e2c27f5c119d2dd6a6a82370dd7}
re02
re02 flag格式:flag{**} 附件:re02.zip
exeinfo 打开,64bit elf
ida64 打开,发现关键代码:
__int64 sub_400BD0(){int v0; // edxint v1; // ecxint v2; // er8int v3; // er9unsigned __int64 v4; // rsiint v5; // edxint v6; // ecxint v7; // er8int v8; // er9int v9; // edxint v10; // er8int v11; // er9int v12; // ecxint v13; // eaxint v14; // eaxbool v15; // zfint v16; // eaxint v17; // eaxint i; // [rsp+9Ch] [rbp-B4h]char v20[32]; // [rsp+A0h] [rbp-B0h] BYREFchar v21[28]; // [rsp+C0h] [rbp-90h] BYREFint v22; // [rsp+DCh] [rbp-74h]char v23[48]; // [rsp+E0h] [rbp-70h] BYREFchar v24[16]; // [rsp+110h] [rbp-40h] BYREF__int64 v25; // [rsp+120h] [rbp-30h] BYREFunsigned int v26; // [rsp+13Ch] [rbp-14h]__int64 v27; // [rsp+140h] [rbp-10h]v26 = 0;sub_400320(v24, 0LL);sub_400320(v23, 0LL);v4 = (unsigned __int64)v24;sub_40F940((unsigned int)"input your flag\n", 0, v0, v1, v2, v3);sub_40FA70((unsigned int)"%s", (unsigned int)v24, v5, v6, v7, v8);v27 = sub_423F00(v24);for ( i = -1606510600; ; i = v14 ){while ( 1 ){while ( 1 ){while ( 1 ){while ( 1 ){while ( 1 ){while ( 1 ){while ( 1 ){while ( 1 ){v12 = i + 2131024272;if ( i != -2131024272 )break;v22 = 0;i = 1479129251;}if ( i != -1999545321 )break;v4 = (unsigned int)&unk_4A1800;v15 = (unsigned int)sub_400330(v20, v4) == 0;v17 = 787574043;if ( !v15 )v17 = 1098311993;i = v17;}if ( i != -1994519983 )break;v9 = byte_4A17B0[v22];LOBYTE(v4) = byte_4A17B0[v22] ^ v24[v22];v23[v22] = v4;i = -1452531375;}if ( i != -1606510600 )break;v13 = -2131024272;v9 = v27;if ( v27 != 32 )v13 = -1484903926;i = v13;}if ( i == -1484903926 ){sub_40F940((unsigned int)"size error", v4, v9, v12, v10, v11);sub_40F030(0LL);}if ( i != -1477025740 )break;sub_400320(v21, 0LL);sub_400320(v20, 0LL);sub_400980(&v25, v21);sub_400A90(v21, v20);v4 = (unsigned int)&unk_4A17E0;v15 = (unsigned int)sub_400330(v23, v4) == 0;v16 = -1999545321;if ( !v15 )v16 = 1098311993;i = v16;}if ( i != -1452531375 )break;++v22;i = 1479129251;}if ( i != 787574043 )break;i = 1981717114;sub_40F940((unsigned int)"success\n", v4, v9, v12, v10, v11);}if ( i != 1098311993 )break;i = 1981717114;sub_40F940((unsigned int)"wrong\n", v4, v9, v12, v10, v11);}if ( i != 1479129251 )break;v14 = -1477025740;if ( v22 < 16 )v14 = -1994519983;}return v26;}
1.exe √
flag格式:KEY{**} 附件:1.exe.zip
IDA 打开,得到伪代码
int __cdecl main_0(int argc, const char **argv, const char **envp){int v4; // [esp+0h] [ebp-1A0h]const char **v5; // [esp+4h] [ebp-19Ch]const char **v6; // [esp+8h] [ebp-198h]char v7; // [esp+Ch] [ebp-194h]int i; // [esp+D4h] [ebp-CCh]int v9; // [esp+E0h] [ebp-C0h]int v10[24]; // [esp+ECh] [ebp-B4h]char v11; // [esp+14Fh] [ebp-51h]char v12[36]; // [esp+178h] [ebp-28h]v11 = 0;v10[0] = 1;v10[1] = 4;v10[2] = 14;v10[3] = 10;v10[4] = 5;v10[5] = 36;v10[6] = 23;v10[7] = 42;v10[8] = 13;v10[9] = 19;v10[10] = 28;v10[11] = 13;v10[12] = 27;v10[13] = 39;v10[14] = 48;v10[15] = 41;v10[16] = 42;v10[17] = 26;v10[18] = 20;v10[19] = 59;v10[20] = 4;v10[21] = 0;printf("plz enter the flag:");while ( 1 ){v7 = getch();v12[v11] = v7;if ( !v7 || v12[v11] == 13 )break;if ( v12[v11] == 8 ){printf("\b\b");--v11;}else{printf("%c", v12[v11++]);}}v9 = 0;for ( i = 0; i < 17; ++i ){if ( v12[i] != byte_415768[v10[i]] )v9 = 1;}if ( v12[17] != 49 || v12[18] != 48 || v12[19] != 50 || v12[20] != 52 || v12[21] != 125 )v9 = 1;v12[v11] = 0;printf("\r\n");if ( v9 ){printf("u r wrong\r\n\r\n");main(v4, v5, v6);}else{printf("u r right!\r\n");}system("pause");return 0;}
编写程序求 flag:
KEY{e2s6ry3r5s8f61024}
rere √
flag格式:flag{**} 附件:rere.zip
拖到 exeinfo 发现是 .net 程序并且有 ConfuserEx 壳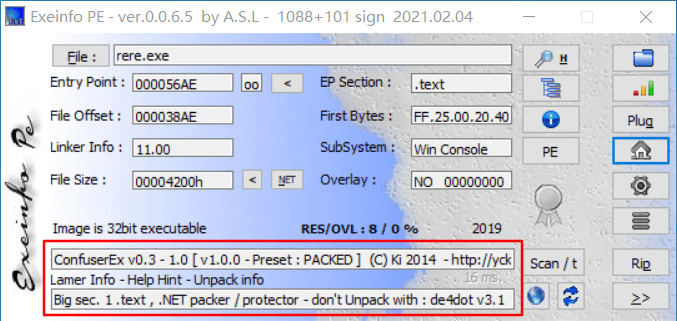
使用 UnConfuserEx 脱壳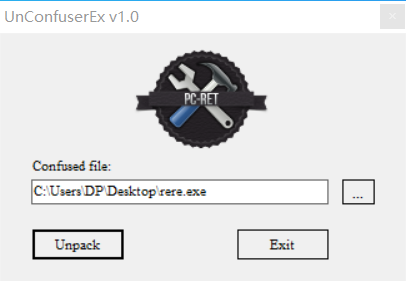
使用 .NET Reflector 反编译,得到 Program.cs
namespace NET2{using System;using System.Linq;using System.Text;internal class Program{private static byte[] res1 = new byte[] {0x80, 0x30, 0x98, 0x79, 0x7d, 0xaf, 180, 0xb3, 170, 0xb5, 0x79, 0x19, 0x43, 0xda, 0xcf, 0x61,0x26, 0x37, 0xcb, 13, 0x4c, 0x2e, 0xa9, 0x6f, 0x3a, 0x1d, 0xea, 0xed, 0xa8, 0x8f, 0x1b, 0x42,0x24, 0xa2, 0x5b, 0x39, 0xec, 0xa7};public static string ByteToHex(byte[] vByte){if ((vByte == null) || (vByte.Length < 1)){return null;}StringBuilder builder = new StringBuilder(vByte.Length * 2);for (int i = 0; i < vByte.Length; i++){uint num2 = (uint) (vByte[i] / 0x10);builder.Append((char) (num2 + ((num2 > 9) ? ((long) 0x37) : ((long) 0x30))));num2 = (uint) (vByte[i] % 0x10);builder.Append((char) (num2 + ((num2 > 9) ? ((long) 0x37) : ((long) 0x30))));}return builder.ToString();}private static byte[] Encrypt(byte[] data, byte[] key){if (data == null){return null;}byte[] buffer = new byte[data.Length];long num = 0L;long num2 = 0L;byte[] buffer2 = GetKey(key, 0x100);for (long i = 0L; i < data.Length; i += 1L){num = (num + 1L) % ((long) buffer2.Length);num2 = (num2 + buffer2[(int) ((IntPtr) num)]) % ((long) buffer2.Length);byte num4 = buffer2[(int) ((IntPtr) num)];buffer2[(int) ((IntPtr) num)] = buffer2[(int) ((IntPtr) num2)];buffer2[(int) ((IntPtr) num2)] = num4;byte num5 = data[(int) ((IntPtr) i)];byte num6 = buffer2[(buffer2[(int) ((IntPtr) num)] + buffer2[(int) ((IntPtr) num2)]) % buffer2.Length];buffer[(int) ((IntPtr) i)] = (byte) (num5 ^ num6);}return buffer;}private static byte[] GetKey(byte[] pass, int kLen){byte[] buffer = new byte[kLen];for (long i = 0L; i < kLen; i += 1L){buffer[(int) ((IntPtr) i)] = (byte) i;}long num = 0L;for (long j = 0L; j < kLen; j += 1L){num = ((num + buffer[(int) ((IntPtr) j)]) + pass[(int) ((IntPtr) (j % ((long) pass.Length)))]) % ((long) kLen);byte num4 = buffer[(int) ((IntPtr) j)];buffer[(int) ((IntPtr) j)] = buffer[(int) ((IntPtr) num)];buffer[(int) ((IntPtr) num)] = num4;}return buffer;}public static byte[] HexToByte(string szHex){int length = szHex.Length;if ((length <= 0) || ((length % 2) != 0)){return null;}int num2 = length / 2;byte[] buffer = new byte[num2];for (int i = 0; i < num2; i++){uint num3 = (uint) (szHex[i * 2] - ((szHex[i * 2] >= 'A') ? '7' : '0'));if (num3 >= 0x10){return null;}uint num4 = (uint) (szHex[(i * 2) + 1] - ((szHex[(i * 2) + 1] >= 'A') ? '7' : '0'));if (num4 >= 0x10){return null;}buffer[i] = (byte) ((num3 * 0x10) + num4);}return buffer;}private static void Main(string[] args){byte[] key = new byte[] { 0x41, 0x42, 0x43, 0x44, 0x45, 70 };Console.WriteLine("You know flag:");if (Encrypt(str2ASCII(Console.ReadLine()), key).SequenceEqual<byte>(res1)){Console.WriteLine("You are right");}else{Console.WriteLine("You are wrong");}}public static byte[] str2ASCII(string xmlStr) =>Encoding.Default.GetBytes(xmlStr);}}
修改程序求 flag:
namespace NET2{using System;using System.Linq;using System.Text;internal class Program{private static byte[] res1 = new byte[] {0x80, 0x30, 0x98, 0x79, 0x7d, 0xaf, 180, 0xb3, 170, 0xb5, 0x79, 0x19, 0x43, 0xda, 0xcf, 0x61,0x26, 0x37, 0xcb, 13, 0x4c, 0x2e, 0xa9, 0x6f, 0x3a, 0x1d, 0xea, 0xed, 0xa8, 0x8f, 0x1b, 0x42,0x24, 0xa2, 0x5b, 0x39, 0xec, 0xa7};private static void Decrypt(byte[] key){//byte[] buffer = new byte[data.Length];long num = 0L;long num2 = 0L;byte[] buffer2 = GetKey(key, 0x100);for (long i = 0L; i < res1.Length; i += 1L){num = (num + 1L) % ((long)buffer2.Length);num2 = (num2 + buffer2[(int)((IntPtr)num)]) % ((long)buffer2.Length);byte num4 = buffer2[(int)((IntPtr)num)];buffer2[(int)((IntPtr)num)] = buffer2[(int)((IntPtr)num2)];buffer2[(int)((IntPtr)num2)] = num4;//byte num5 = data[(int)((IntPtr)i)];byte num6 = buffer2[(buffer2[(int)((IntPtr)num)] + buffer2[(int)((IntPtr)num2)]) % buffer2.Length];//buffer[(int)((IntPtr)i)] = (byte)(num5 ^ num6);for(int j = 32; j < 127; j++){byte num5 = (byte)j;if((byte)(num5 ^ num6) == res1[(int)((IntPtr)i)]){Console.Write((char)j);break;}}}}private static byte[] GetKey(byte[] pass, int kLen){byte[] buffer = new byte[kLen];for (long i = 0L; i < kLen; i += 1L){buffer[(int)((IntPtr)i)] = (byte)i;}long num = 0L;for (long j = 0L; j < kLen; j += 1L){num = ((num + buffer[(int)((IntPtr)j)]) + pass[(int)((IntPtr)(j % ((long)pass.Length)))]) % ((long)kLen);byte num4 = buffer[(int)((IntPtr)j)];buffer[(int)((IntPtr)j)] = buffer[(int)((IntPtr)num)];buffer[(int)((IntPtr)num)] = num4;}return buffer;}private static void Main(string[] args){byte[] key = new byte[] { 0x41, 0x42, 0x43, 0x44, 0x45, 70 };Decrypt(key);}}}
flag{e484df0963c115a93042388333847726}
timu_837 √
NWE0ZDRhNTQ1MDRkMzMzMzU3NDEzNDUxNTY0NTQ1NGQ1NDU3NTU0OTUyMzc1NjI1MzM1MQ==
Base64解码:5a4d4a54504d3333574134515645454d54575549523756253351
Hex -> ASCII:ZMJTPM33WA4QVEEMTWUIR7V%3Q
Rot13:MZWGCZ33JN4DIRRZGJHVE7I%3D
URL解码:MZWGCZ33JN4DIRRZGJHVE7I=
Base32解码:flag{Kx4F92OR}
单选题
下面对于SSE-CMM保证过程的说法错误的是(D)A. 保证是指安全需求得到满足的可信任程度B. 信任程度来自于对安全工程过程结果质量的判断C. 自验证与证实安全的主要手段包括观察、论证、分析和测试D. PA“建立保证论据”为PA“验证与证实安全"提供了证据支持
在业务持续性计划中,RTO指的是什么?(C)A.灾难备份和恢复B.恢复技术项目C.业务恢复时间目标D.业务恢复点目标
信息网络安全(风险)评估的方法(B)A.定量评估B.定性评估与定量评估相结合C.定点评估D.定性评估
在原告起诉被告抢注域名案件中,以下不能判定被告对其域名的注册、使用具有恶意的是(D)A.为商业目的将他人驰名商标注册为域名的B.为商业目的注册与原告的域名近似的域名,故意造成与原告网站的混淆,误导网络用户访问其网站的C.曾要约高价出售其域名获取不正当利益的D.注册域名后自己准备使用的
以下哪一个是对人员安全管理中“授权蔓延”这概念的正确理解?(B)A.外来人员在进行系统维护时没有收到足够的监控B.一个人拥有了不是其完成工作所必要的权限C.敏感岗位和重要操作长期有一个人独自负责D.员工由一个岗位变动到另一人岗位,累积越来越多权限
关于加密算法的应用范围,说话正确的有(A)。A.DSS用于数字签名,RSA用于加密和签名B.DSS用于密钥交换,IDEA用于加密和签名C.DSS用于数字签名,MD5用于加密和签名D.DSS用于加密和签名,MD5用于完整性效验

