1、获取ETCD证书
对于etcd集群,在搭建的时候我们就采用了https证书认证的方式,所以这里如果想用Prometheus访问到etcd集群的监控数据,就需要添加证书
2、systemctl status etcd查看证书路径
vim /usr/lib/systemd/system/etcd.service[Unit]Description=Etcd ServerAfter=network.targetAfter=network-online.targetWants=network-online.targetDocumentation=https://github.com/coreos[Service]Type=notifyWorkingDirectory=/var/lib/etcdExecStart=/usr/local/bin/etcd \--name=master1 \--data-dir=/data1/etcd/var/lib/etcd \--cert-file=/etc/etcd/pki/server.pem \--key-file=/etc/etcd/pki/server-key.pem \--trusted-ca-file=/etc/etcd/pki/ca.pem \--peer-cert-file=/etc/etcd/pki/peer.pem \--peer-key-file=/etc/etcd/pki/peer-key.pem \--peer-trusted-ca-file=/etc/etcd/pki/ca.pem \--listen-peer-urls=https://172.31.243.137:2380 \--initial-advertise-peer-urls=https://172.31.243.137:2380 \--listen-client-urls=https://172.31.243.137:2379,http://127.0.0.1:2379 \--advertise-client-urls=https://172.31.243.137:2379 \--initial-cluster-token=etcd-cluster-0 \--initial-cluster=master1=https://172.31.243.137:2380,master2=https://172.31.243.232:2380,master3=https://172.31.243.253:2380 \--initial-cluster-state=new \--heartbeat-interval=250 \--election-timeout=2000Restart=on-failureRestartSec=5LimitNOFILE=65536[Install]WantedBy=multi-user.target
3、创建secret
#第一种方法kubectl create secret generic etcd-certs --from-file=/etc/kubernetes/cert/ca.pem --from-file=/etc/etcd/cert/etcd.pem --from-file=/etc/etcd/cert/etcd-key.pem -n monitoring#第二种方法编辑 etcd-secret.yamlapiVersion: v1data:ca.pem: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSURFakNDQWZxZ0F3SUJBZ0lVYkV2bVJ2SndDUTZPREVXNGUvZ3ZISVN6Zms0d0RRWUpLb1pJaHZjTkFRRUwKQlFBd0R6RU5NQXNHQTFVRUF4TUVaWFJqWkRBZUZ3MHlNREEyTVRrd05qTXdNREJhRncweU5UQTJNVGd3TmpNdwpNREJhTUE4eERUQUxCZ05WQkFNVEJHVjBZMlF3Z2dFaU1BMEdDU3FHU0liM0RRRUJBUVVBQTRJQkR3QXdnZ0VLCkFvSUJBUUM4dmVwMWgwejdJaGpPZHZpWXRweXFJcDNEVDZGaklIYXArU2pzSDQzN1JyVHVmdXluNzZ2U2VjTVEKclQ3c0JOaC9qdCtCNlQzQU5OYWQwcTM5WjRXckxCajlTQUNIb3NaNmh4UDZNMzY1VHNiZkVJYittdXR4QXZLQwo4M2E2a0Y3dUkwUGJXV2N2b1JEbGxZV1VFOEVQbzNseXFJbU5NUFNEV3hwQStPUUY3NHJ0ZzRuSWZSYWlDWU9YClVIMlJoZTM3UGNLYWJacFpXeFNaQUhRWlQ5NTBpOG8yOWlUdHp2eXlQOXBVY0VlNmZCcEljNDYzMXNoQ2g2S0YKWnNEaDJTT3dvdWcxYTBZU2tZY0F6ZU1pTktZVFR1VXFnc0h1YlZBTS8va0tjVTJCa3pQVmN2ZFdlNWU0ZHc4NAoyS29RMngzdFpOeFZIbnE1TjdqemxMZnorQUxYQWdNQkFBR2paakJrTUE0R0ExVWREd0VCL3dRRUF3SUJCakFTCkJnTlZIUk1CQWY4RUNEQUdBUUgvQWdFQ01CMEdBMVVkRGdRV0JCU1drRnc4LzFhK2I1U29POXhod1BFT3owc3oKZHpBZkJnTlZIU01FR0RBV2dCU1drRnc4LzFhK2I1U29POXhod1BFT3owc3pkekFOQmdrcWhraUc5dzBCQVFzRgpBQU9DQVFFQWFieEdxRFU3VmIwcjA4eWZYNFlsK2p6SDUxZ1hKZ0NVSkVrOGVxOFg1RlJ3Ynd1dXN4Qm45dUVQCkZTcFQ4ZTF0YUNTRkdQSVFFRFloQ3lWVHNIcHBGdzN2WHZ2eldlU1FNM05UeVdiR0pxREZ3MVNCd3dGa3JHcncKK3l0RFVkVE9tK2VDWVhGc0ZJMWVUSFhWNjZJSW9WUFFJRU1Ma3lGVzRvMm5IaWFNb2NCTk5yTVJiRWF5SkFwRwppbFRZODc2dVd6Y0Z3cDhWQTdMZ2pCN1M3cXNUOG1YM3RxVDZJQ1NBcy9FSnF1c3BFeW9oV1NQbzhreWhUdjVlCnhMd0VrWHFsdUREQmQvWTA1ZVhZd1NxZTErTVVQR3IyNzV4aXJNNnVEWmU1WWNtS2pqVWlEZEhOQ3B4UDdxcmcKZktCa01pV2dJUThZNWJNQVhRVnlCUFg4UFFvVFhBPT0KLS0tLS1FTkQgQ0VSVElGSUNBVEUtLS0tLQo=server-key.pem: LS0tLS1CRUdJTiBFQyBQUklWQVRFIEtFWS0tLS0tCk1IY0NBUUVFSUtKRUE1dkVVL0JVVk1KaElOeXMyNG1TSFZ4eUszUnNCL0VQc0dzTVFMOTlvQW9HQ0NxR1NNNDkKQXdFSG9VUURRZ0FFN1lLV3RnVXRlZkRtdk1ESmtrZWUrYVkxZGJGcDMza3JYbVFlRGp1KzRsMXRpS2tTZmI0UAoyZC9md0NnTkdhU2NvV0NnSklickhRUXp2c2pKeDJ6UjNnPT0KLS0tLS1FTkQgRUMgUFJJVkFURSBLRVktLS0tLQo=server.pem: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUNyRENDQVpTZ0F3SUJBZ0lVRUNGS1psemtBWDR4dWtDTFNabHdyaldGcDlJd0RRWUpLb1pJaHZjTkFRRUwKQlFBd0R6RU5NQXNHQTFVRUF4TUVaWFJqWkRBZUZ3MHlNREEyTVRrd05qTTFNREJhRncweU5UQTJNVGd3TmpNMQpNREJhTURZeEN6QUpCZ05WQkFZVEFrTk9NUXN3Q1FZRFZRUUlFd0pUU0RFTE1Ba0dBMVVFQnhNQ1UwZ3hEVEFMCkJnTlZCQU1UQkdWMFkyUXdXVEFUQmdjcWhrak9QUUlCQmdncWhrak9QUU1CQndOQ0FBVHRncGEyQlMxNThPYTgKd01tU1I1NzVwalYxc1duZmVTdGVaQjRPTzc3aVhXMklxUko5dmcvWjM5L0FLQTBacEp5aFlLQWtodXNkQkRPKwp5TW5IYk5IZW80R2pNSUdnTUE0R0ExVWREd0VCL3dRRUF3SUZvREFkQmdOVkhTVUVGakFVQmdnckJnRUZCUWNECkFRWUlLd1lCQlFVSEF3SXdEQVlEVlIwVEFRSC9CQUl3QURBZEJnTlZIUTRFRmdRVSt0anFJWEJBQVNsZXVuemEKZVhjZHhaVllQVk13SHdZRFZSMGpCQmd3Rm9BVWxwQmNQUDlXdm0rVXFEdmNZY0R4RHM5TE0zY3dJUVlEVlIwUgpCQm93R0ljRWZ3QUFBWWNFckIvemlZY0VyQi96NkljRXJCL3ovVEFOQmdrcWhraUc5dzBCQVFzRkFBT0NBUUVBCkcvaDNkY3NzRklEYlpndlVoeHVZeG0zL08xN2F5ZUZaSTNJTW4zUThyYmhzejhrTlZXUjNTOXdqMEVza0ZTay8Kb0c3ekpOaW91QjgrUFo5SE84b2pTYmNkT3BRMi85UjVlMkUrQTg1YU5XTEl6VmZaWDQwNGJoZmJoU0g1QlpjZQpDNDZETmovRktRVWRGQkYvSHp3ODM4ZDM0ckNaREFzVUlKN3JXNjFoenFsU1ZsUUZPb3hDQWwwSW05eGIxL2FHCmFhQ2d0M1dQN1RqNTZPUi9YYnZYeEtxQUkwUURsdHU4R0FoRk9BTVZUU0pvVnlGT0dmcVptTzg3dmlVWmQ4WVYKTE1Rc3J0a0EyT1FvSWRIMW9sc1NTb0NCeGk3K2JIUVo1Y3Mwb21kcHhNV1FQSG5CWFIxZ2x1WW1PRnJSVGQxcQpsa3dYNVNGcnI5THNlQnpVYkZPbEVnPT0KLS0tLS1FTkQgQ0VSVElGSUNBVEUtLS0tLQo=kind: Secretmetadata:name: etcd-certsnamespace: monitoringtype: Opaque#查看[root@hf-aipaas-172-31-243-137 etcd]# kubectl describe secrets -n monitoring etcd-certsName: etcd-certsNamespace: monitoringLabels: <none>Annotations:Type: OpaqueData====server.pem: 989 bytesca.pem: 1127 bytesserver-key.pem: 227 bytes#查看prometheus相关配置[root@hf-aipaas-172-31-243-137 etcd]# kubectl exec -it -n monitoring prometheus-k8s-0 /bin/shDefaulting container name to prometheus.Use 'kubectl describe pod/prometheus-k8s-0 -n monitoring' to see all of the containers in this pod./prometheus $ ls /etc/prometheus/secrets/etcd-ssl/ls: /etc/prometheus/secrets/etcd-ssl/: No such file or directory/prometheus $ ls /etc/prometheus/secrets/etcd-certs/ca.pem server-key.pem server.pem
4、将etcd-ssl secret配置放到prometheus资源对象中
修改prometheus-prometheus.yaml 文件
secrets: #增加etcd配置- etcd-certsruleSelector:matchLabels:prometheus: k8srole: alert-rules
5、编辑etcd-service.yaml
apiVersion: v1kind: Servicemetadata:name: etcd-k8snamespace: kube-systemlabels:k8s-app: etcdspec:type: ClusterIPclusterIP: Noneports:- name: portport: 2379protocol: TCP---apiVersion: v1kind: Endpointsmetadata:name: etcd-k8snamespace: kube-systemlabels:k8s-app: etcdsubsets:- addresses:- ip: 172.31.243.137- ip: 172.31.243.232- ip: 172.31.243.254ports:- name: portport: 2379protocol: TCP
6、编辑etcd-servicemonitor.yaml
apiVersion: monitoring.coreos.com/v1kind: ServiceMonitormetadata:name: etcd-k8snamespace: monitoringlabels:k8s-app: etcd-k8smonitor: k8sspec:jobLabel: k8s-appendpoints:- port: portinterval: 30sscheme: httpstlsConfig:caFile: /etc/prometheus/secrets/etcd-certs/ca.pemcertFile: /etc/prometheus/secrets/etcd-certs/server.pemkeyFile: /etc/prometheus/secrets/etcd-certs/server-key.peminsecureSkipVerify: trueselector:matchLabels:k8s-app: etcdnamespaceSelector:matchNames:- kube-system
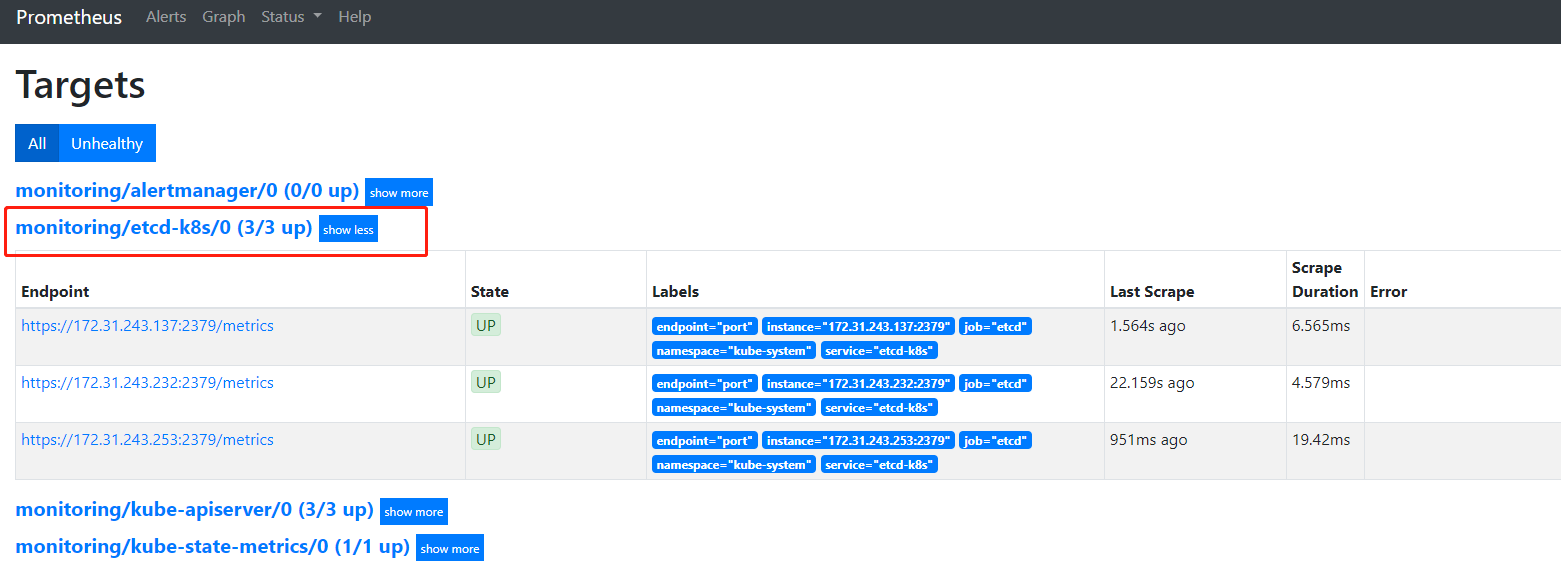
7、查看prometheus界面target