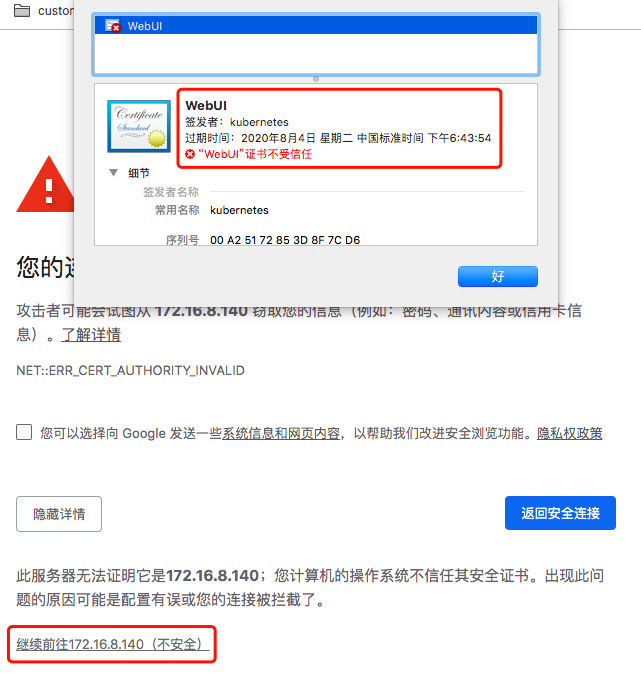
web UI
dashboard
用户授权
https://www.kubernetes.org.cn/4062.html
https://kubernetes.io/docs/reference/access-authn-authz/authorization/
部署dashboard
# kubectl apply -f https://raw.githubusercontent.com/kubernetes/dashboard/v2.0.0-beta1/aio/deploy/recommended.yamlnamespace/kubernetes-dashboard createdserviceaccount/kubernetes-dashboard createdservice/kubernetes-dashboard createdsecret/kubernetes-dashboard-certs createdsecret/kubernetes-dashboard-csrf createdsecret/kubernetes-dashboard-key-holder createdconfigmap/kubernetes-dashboard-settings createdrole.rbac.authorization.k8s.io/kubernetes-dashboard createdclusterrole.rbac.authorization.k8s.io/kubernetes-dashboard createdrolebinding.rbac.authorization.k8s.io/kubernetes-dashboard createdclusterrolebinding.rbac.authorization.k8s.io/kubernetes-dashboard createddeployment.apps/kubernetes-dashboard createdservice/dashboard-metrics-scraper createddeployment.apps/kubernetes-metrics-scraper created# kubectl get pods --namespace kubernetes-dashboardNAME READY STATUS RESTARTS AGEkubernetes-dashboard-5c8f9556c4-mcl44 1/1 Running 0 3m47skubernetes-metrics-scraper-86456cdd8f-6jhh8 1/1 Running 0 3m46s# kubectl proxyStarting to serve on 127.0.0.1:8001
由于 Dashboard 是一个 Web Server,为了避免公网暴露端口带来安全隐患,k8s1.7 版本之后的 Dashboard 项目部署完成后,只能通过 Proxy 的方式在执行了kubectl proxy的主机上访问到UI接口,要想在集群外部访问到dashboard需要通过loadbalance或者ingress
# kubectl get svc --namespace kubernetes-dashboardNAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGEdashboard-metrics-scraper ClusterIP 10.98.63.13 <none> 8000/TCP 26mkubernetes-dashboard ClusterIP 10.105.6.68 <none> 443/TCP 26m
将kubernetes-dashboard的Service类型改成NodePort
# kubectl patch svc kubernetes-dashboard -p '{"spec":{"type":"NodePort"}}' -n kubernetes-dashboardservice/kubernetes-dashboard patched# kubectl get svc --namespace kubernetes-dashboardNAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGEdashboard-metrics-scraper ClusterIP 10.98.63.13 <none> 8000/TCP 36mkubernetes-dashboard NodePort 10.105.6.68 <none> 443:30794/TCP 36m
创建用于认证的用户
创建ServiceAccount类型的认证账号,被dashboard pod拿来由kubernetes进行认证
# kubectl apply -f dashboard-adminuser.yaml# cat dashboard-adminuser.yamlapiVersion: v1kind: ServiceAccountmetadata:name: admin-usernamespace: kube-system
绑定授权,使用clusterrolebinding绑定至合理role或clusterrole
# kubectl apply -f role-binding.yaml# cat role-binding.yamlapiVersion: rbac.authorization.k8s.io/v1kind: ClusterRoleBindingmetadata:name: admin-userroleRef:apiGroup: rbac.authorization.k8s.iokind: ClusterRolename: cluster-adminsubjects:- kind: ServiceAccountname: admin-usernamespace: kube-system
查看ServiceAccount的secret的详细信息,获取token
# kubectl -n kube-system get secret | grep admin-useradmin-user-token-7hnfg kubernetes.io/service-account-token 3 160m# kubectl -n kube-system describe secret $(kubectl -n kube-system get secret | grep admin-user | awk '{print $1}')
此时可以访问随机的端口
查看namespace
node资源情况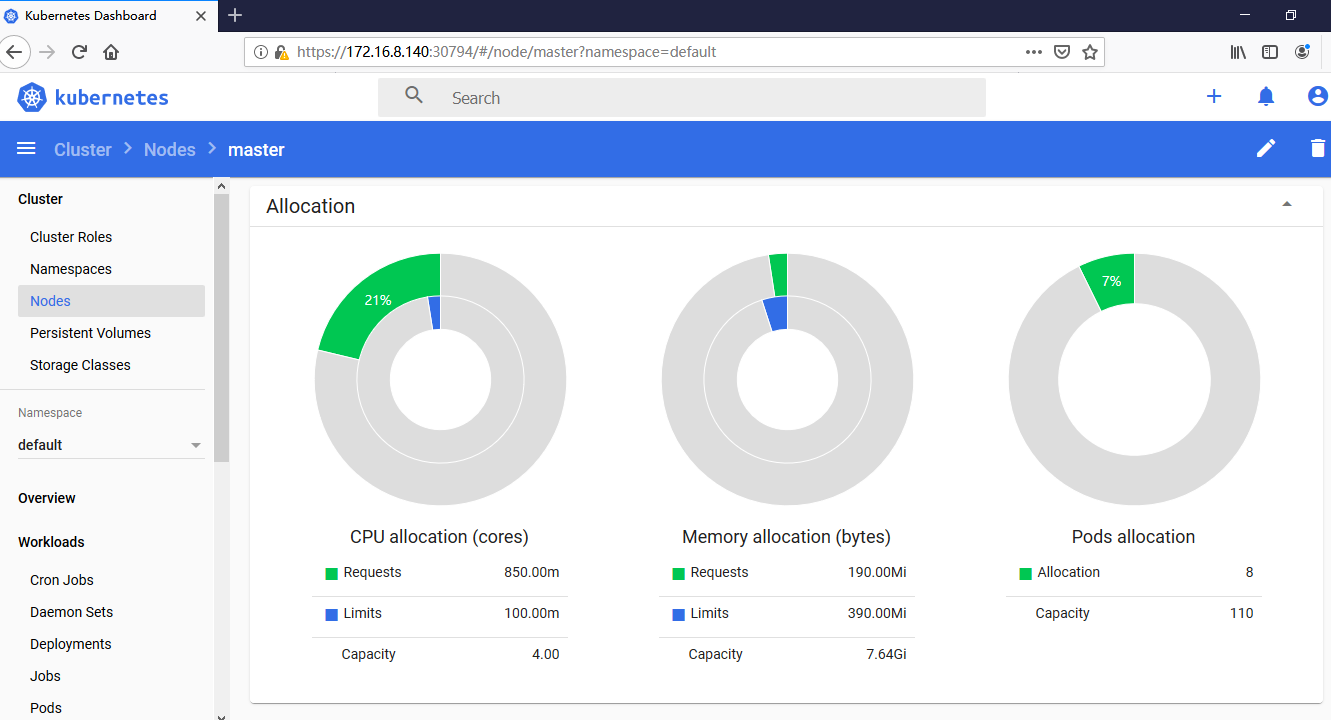
由于证书问题,Google浏览器无法访问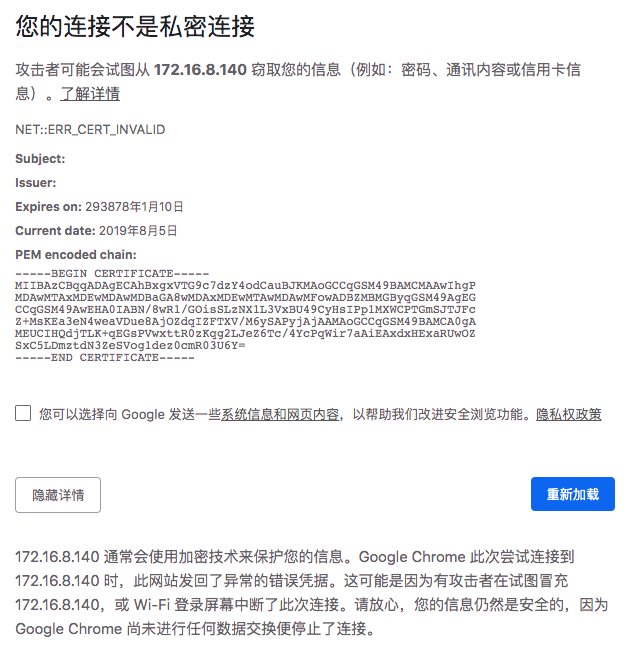
通过openssl生成自签名证书配置本地认证
# cd /etc/kubernetes/pki# (umask 077; openssl genrsa -out dashboard.key 2048)Generating RSA private key, 2048 bit long modulus................+++..................................+++e is 65537 (0x10001)# openssl req -new -key dashboard.key -out dashboard.csr -subj "/CN=WebUI"# openssl x509 -req -in dashboard.csr -CA ca.crt -CAkey ca.key -CAcreateserial -out dashboard.crt -days 365Signature oksubject=/CN=WebUIGetting CA Private Key# openssl x509 -in dashboard.crt -textCertificate:Data:Version: 1 (0x0)Serial Number:a2:51:72:85:3d:8f:7c:d6Signature Algorithm: sha256WithRSAEncryptionIssuer: CN=kubernetesValidityNot Before: Aug 5 10:43:54 2019 GMTNot After : Aug 4 10:43:54 2020 GMTSubject: CN=WebUISubject Public Key Info:Public Key Algorithm: rsaEncryptionPublic-Key: (2048 bit)......................................................
重新生成secret
# kubectl create secret generic kubernetes-dashboard-certs -n kubernetes-dashboard --from-file=dashboard.key --from-file=dashboard.crt
secret/kubernetes-dashboard-certs created
# kubectl get secret -n kubernetes-dashboard
NAME TYPE DATA AGE
default-token-ncd29 kubernetes.io/service-account-token 3 19m
kubernetes-dashboard-certs Opaque 2 19m
kubernetes-dashboard-csrf Opaque 1 6m31s
kubernetes-dashboard-key-holder Opaque 2 6m30s
kubernetes-dashboard-token-7gjt9 kubernetes.io/service-account-token 3 13m
# kubectl describe secret kubernetes-dashboard-certs -n kubernetes-dashboard
Name: kubernetes-dashboard-certs
Namespace: kubernetes-dashboard
Labels: <none>
Annotations: <none>
Type: Opaque
Data
====
dashboard.key: 1679 bytes
dashboard.crt: 973 bytes
将配置文件中创建secret的相关信息去掉,重新apply
---
apiVersion: v1
kind: Secret
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard-certs
namespace: kube-system
type: Opaque
---
也可以修改svc类型为NodePort并指定映射端口,范围为30000-32767
---
kind: Service
apiVersion: v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kubernetes-dashboard
spec:
type: NodePort
ports:
- port: 443
nodePort: 31777
targetPort: 8443
selector:
k8s-app: kubernetes-dashboard
---
# kubectl apply -f create-dashboard.yml
再次使用Google浏览器访问即可正常查看证书信息