规划图
etcd
etcd ca
{"CN": "etcd-ca","key": {"algo": "rsa","size": 2048},"ca": {"expiry": "87600h"}}
cfssl gencert -initca etcd-ca-csr.json | cfssljson -bare etcd-ca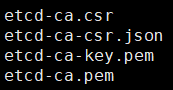
证书生成策略文件
{
"signing": {
"default": {
"expiry": "87600h"
},
"profiles": {
"etcd": {
"expiry": "87600h",
"usages": [
"signing",
"key encipherment",
"server auth",
"client auth"
]
}
}
}
}
etcd 证书申请
{
"CN": "etcd",
"hosts": [
"192.168.80.201",
"192.168.80.202",
"192.168.80.203",
"etcd01",
"etcd02",
"etcd03",
"127.0.0.1"
],
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"L": "BJ"
}
]
}
cfssl gencert -ca=etcd-ca.pem -ca-key=etcd-ca-key.pem -config=ca-config.json -profile=etcd etcd-csr.json | cfssljson -bare etcd
解压 tar 包
tar xf etcd-v3.4.16-linux-amd64.tar.gz
mv etcd-v3.4.16-linux-amd64 /data/etcd
启动脚本参照
#!/bin/bash
/data/etcd/etcd \
--name=etcd-201 \
--data-dir=/data/etcd/data \
--wal-dir=/data/etcd/wal \
--listen-client-urls=https://192.168.80.201:2379,http://127.0.0.1:2379 \
--listen-peer-urls=https://192.168.80.201:2380 \
--initial-advertise-peer-urls=https://192.168.80.201:2380 \
--advertise-client-urls=https://192.168.80.201:2379,http://127.0.0.1:2379 \
--initial-cluster=etcd-201=https://192.168.80.201:2380,etcd-202=https://192.168.80.202:2380,etcd-203=https://192.168.80.203:2380 \
--initial-cluster-token=etcd-cluster-token-1 \
--initial-cluster-state=new \
--cert-file=/data/etcd/etcd.pem \
--key-file=/data/etcd/etcd-key.pem \
--client-cert-auth \
--trusted-ca-file=/data/etcd/etcd-ca.pem \
--peer-cert-file=/data/etcd/etcd.pem \
--peer-key-file=/data/etcd/etcd-key.pem \
--peer-client-cert-auth \
--peer-trusted-ca-file=/data/etcd/etcd-ca.pem
etcd集群验证
/data/etcd/etcdctl \
—cacert=/data/etcd/etcd-ca.pem \
—cert=/data/etcd/etcd.pem \
—key=/data/etcd/etcd-key.pem \
—endpoints=”https://192.168.80.201:2379,https://192.168.80.202:2379,https://192.168.80.203:2379“ member list
/data/etcd/etcdctl \
—cacert=/data/etcd/etcd-ca.pem \
—cert=/data/etcd/etcd.pem \
—key=/data/etcd/etcd-key.pem \
—endpoints=”https://192.168.80.201:2379,https://192.168.80.202:2379,https://192.168.80.203:2379“ endpoint status
/data/etcd/etcdctl \
—cacert=/data/etcd/etcd-ca.pem \
—cert=/data/etcd/etcd.pem \
—key=/data/etcd/etcd-key.pem \
—endpoints=”https://192.168.80.201:2379,https://192.168.80.202:2379,https://192.168.80.203:2379“ endpoint health
k8s
k8s ca
{
"CN": "k8s-ca",
"key": {
"algo": "rsa",
"size": 2048
}
}
cfssl gencert -initca k8s-ca-csr.json | cfssljson -bare k8s-ca
证书生成策略文件
{
"signing": {
"default": {
"expiry": "87600h"
},
"profiles": {
"k8s": {
"expiry": "87600h",
"usages": [
"signing",
"key encipherment",
"server auth",
"client auth"
]
}
}
}
}
front-proxy
ca
{
"CN": "front-proxy-ca",
"key": {
"algo": "rsa",
"size": 2048
}
}
cfssl gencert -initca front-proxy-ca-csr.json | cfssljson -bare front-proxy-ca
client
{
"CN": "front-proxy-client",
"key": {
"algo": "rsa",
"size": 2048
}
}
cfssl gencert -ca=front-proxy-ca.pem -ca-key=front-proxy-ca-key.pem -config=ca-config.json -profile=k8s front-proxy-client-csr.json | cfssljson -bare front-proxy-client
apiserver
申请证书
{
"CN": "apiserver",
"hosts": [
"10.11.0.1",
"127.0.0.1",
"kubernetes",
"kubernetes.default",
"kubernetes.default.svc",
"kubernetes.default.svc.cluster",
"kubernetes.default.svc.cluster.local",
"192.168.80.191",
"192.168.80.192",
"192.168.80.193",
"192.168.80.188"
],
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"L": "BeiJing",
"ST": "BeiJing",
"O": "k8s",
"OU": "System"
}
]
}
cfssl gencert -ca=k8s-ca.pem -ca-key=k8s-ca-key.pem -config=ca-config.json -profile=k8s apiserver-csr.json | cfssljson -bare apiserver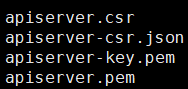
启动脚本
#!/bin/bash
/data/k8s/bin/kube-apiserver \
--logtostderr=false \
--v 2 \
--log-dir /data/k8s/logs/apiserver \
--apiserver-count 2 \
--bind-address 192.168.80.191 \
--secure-port 6443 \
--advertise-address 192.168.80.191 \
--allow-privileged=true \
--service-cluster-ip-range 10.11.0.0/24 \
--service-node-port-range 30000-50000 \
--enable-admission-plugins NamespaceLifecycle,LimitRanger,ServiceAccount,ResourceQuota,NodeRestriction \
--authorization-mode RBAC,Node \
--enable-bootstrap-token-auth=true \
--etcd-servers https://192.168.80.201:2379,https://192.168.80.202:2379,https://192.168.80.203:2379 \
--etcd-cafile /data/k8s/ssl/etcd/etcd-ca.pem \
--etcd-certfile /data/k8s/ssl/etcd/etcd.pem \
--etcd-keyfile /data/k8s/ssl/etcd/etcd-key.pem \
--client-ca-file /data/k8s/ssl/k8s-ca.pem \
--service-account-key-file /data/k8s/ssl/k8s-ca-key.pem \
--kubelet-client-certificate /data/k8s/ssl/apiserver.pem \
--kubelet-client-key /data/k8s/ssl/apiserver-key.pem \
--tls-cert-file /data/k8s/ssl/apiserver.pem \
--tls-private-key-file /data/k8s/ssl/apiserver-key.pem \
--service-account-signing-key-file=/data/k8s/ssl/k8s-ca-key.pem \
--service-account-issuer https://kubernetes.default.svc.cluster.local
controller-manager
#!/bin/bash
/data/k8s/bin/kube-controller-manager \
--logtostderr=false \
--v=2 \
--log-dir=/data/k8s/logs/controller-manager \
--leader-elect=true \
--master=127.0.0.1:8080 \
--address=127.0.0.1 \
--allocate-node-cidrs=true \
--cluster-cidr=172.11.0.0/16 \
--service-cluster-ip-range=10.11.0.0/24 \
--cluster-signing-cert-file=/data/k8s/ssl/k8s-ca.pem \
--cluster-signing-key-file=/data/k8s/ssl/k8s-ca-key.pem \
--root-ca-file=/data/k8s/ssl/k8s-ca.pem \
--service-account-private-key-file=/data/k8s/ssl/k8s-ca-key.pem \
--experimental-cluster-signing-duration=87600h0m0s
scheduler
#!/bin/bash
/data/k8s/bin/kube-scheduler \
--logtostderr=false \
--leader-elect \
--log-dir /data/k8s/logs/scheduler \
--master http://127.0.0.1:8080 \
--v 2


