Reference
- ARM Datasheet
Background (Why)
What is Security
Security Attacks
ARM Security Features
This diagram shows different security features in the Arm architecture. These features can be used to defend different assets in the system.
- SecurCore
Arm SecurCore processors are designed specifically for high-performance and high-volume smartcard and embedded security applications. 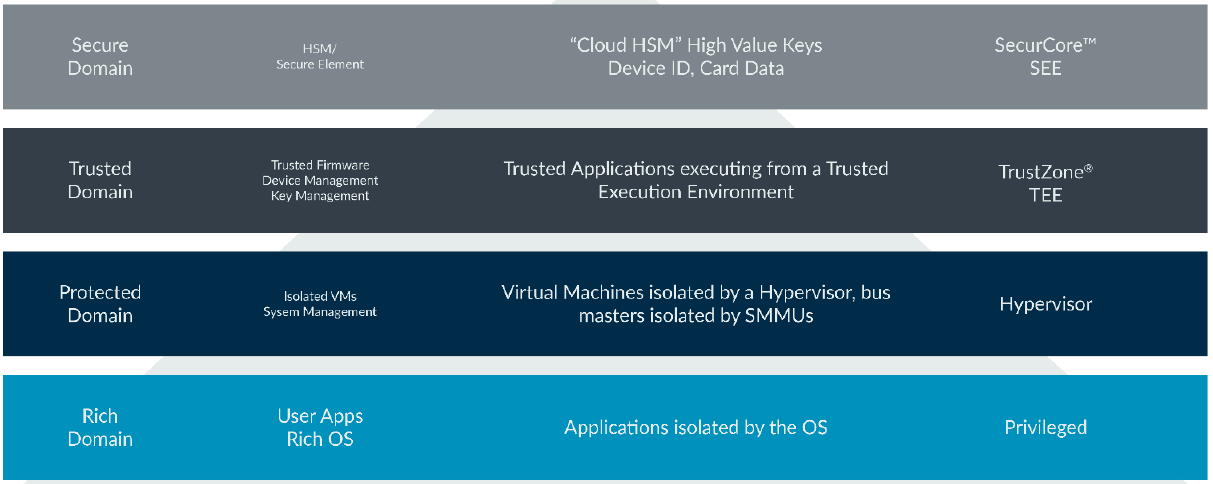
(The picture is from Introduction_to_security.pdf)
TrustZone Overview (What)
- TrustZone is the name of the Security architecture in the Arm A-profile architecture. The TrustZone architecture provides a means for system designers to help secure systems, using the TrustZone Security Extensions, and Secure peripherals.
- TrustZone technology is designed to protect against software attacks. Good design practice with the TrustZone Extension can also give a good defense against simple hardware attacks.
- TrustZone provides two execution environments with system-wide hardware enforced isolation between them.
Normal world: Rich Execution Environment (REE).
Trusted world: Trusted Execution Environment (TEE).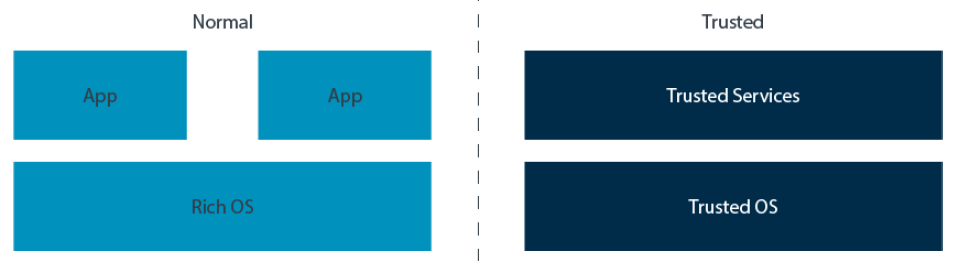
TrustZone System
TrustZone is much more than just a set of processor features. To take advantage of the TrustZone features, we need support in the rest of the system as well.
• Secure
Only Secure accesses are passed to device. Interconnect generates a fault for all Non-secure accesses, without the access being presented to the device.
• Non-secure
Only Non-secure accesses are passed to device. Interconnect generates a fault for all Secure accesses, without the access being presented to the device.
• Boot time configurable
At boot time, system initialization software can program the device as Secure or Non-secure. The default is Secure.
• TrustZone aware
The interconnect allows all accesses through. The connected device must implement isolation.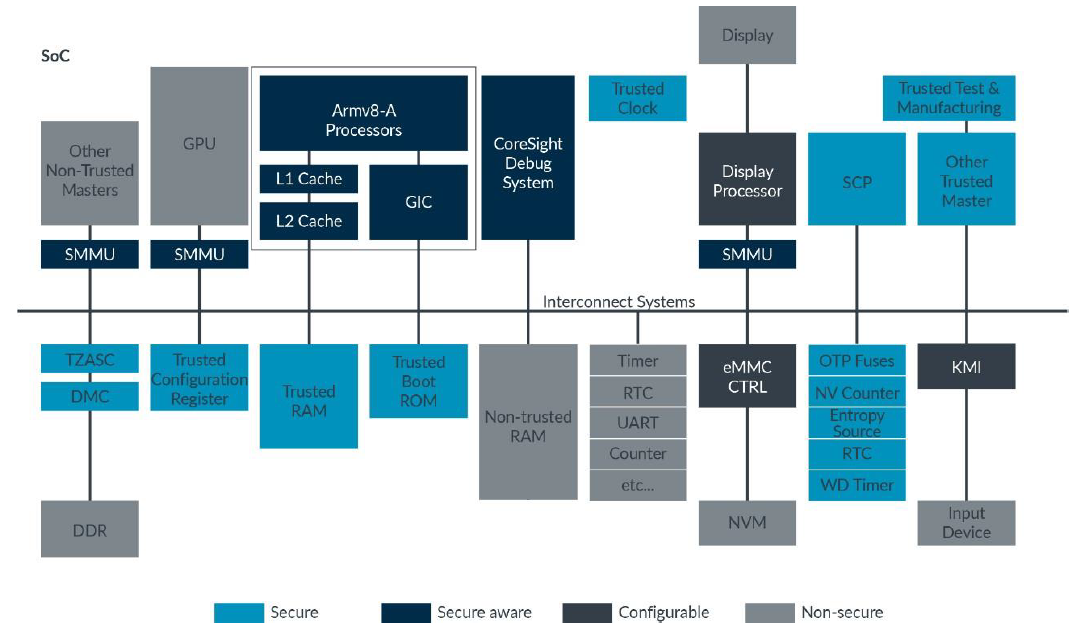
TrustZone Aware Components
- Interconnect
The memory system-based checking is done by the interconnect.
- TZASC
For larger memories, like off-chip DDR, we might want to partition the memory into Secure and Non-secure regions. A TrustZone Address Space Controller (TZASC) allows us to do this.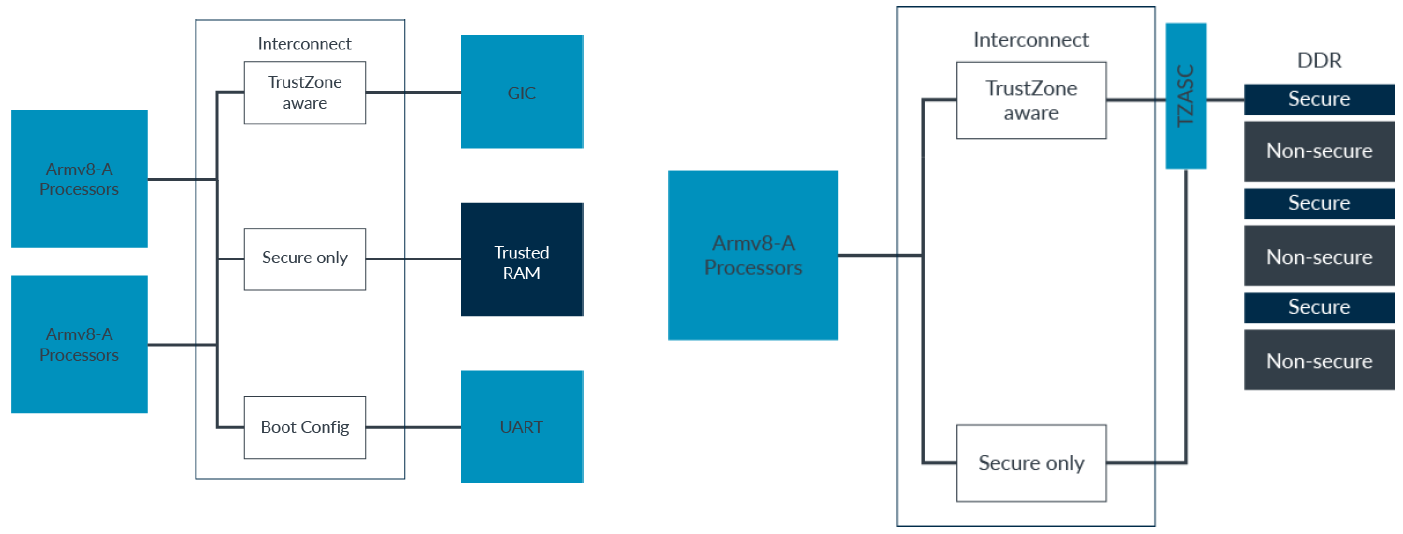
- SMMU
A more flexible option is an SMMU. For a trusted requester, the SMMU behaves like the MMU in Secure state. This includes the NS bit in the translation table entries, controlling which physical address space is accessed.
- GIC
The Generic Interrupt Controller (GIC), supports TrustZone. Each interrupt source, called an INTID in the GIC specification, is assigned to one of three Groups:
• Group 0: Secure interrupt, signaled as FIQ
• Secure Group 1: Secure interrupt, signaled as IRQ or FIQ
• Non-secure Group 1: Non-secure interrupt, signaled as IRQ or FIQ
- Processor
The A-profile processors in the system are TrustZone aware and send the correct security status with each bus access. This is supported by Processor Trustzone Security Extentions.
Trustzone Security Extentions (How)
Trustzone Security Extentions is for processor.
Secure States
In the Arm architecture, there are two Security states: Secure and Non-secure. These Security states map onto the Trusted and Normal worlds.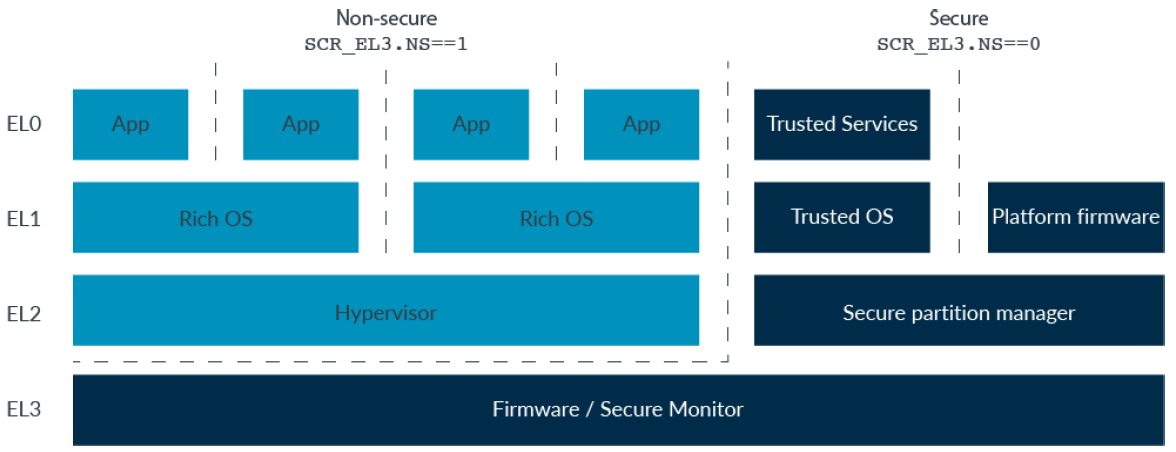
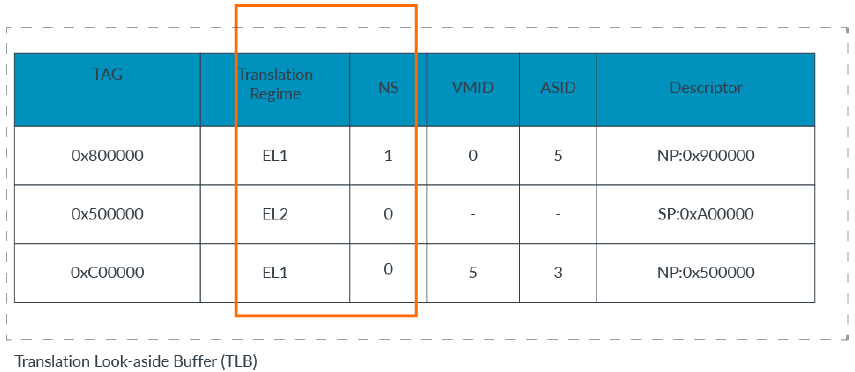
Virtual Address Spaces (Translation Regimes)
There are also separate translation regimes for the Secure and Non-secure states.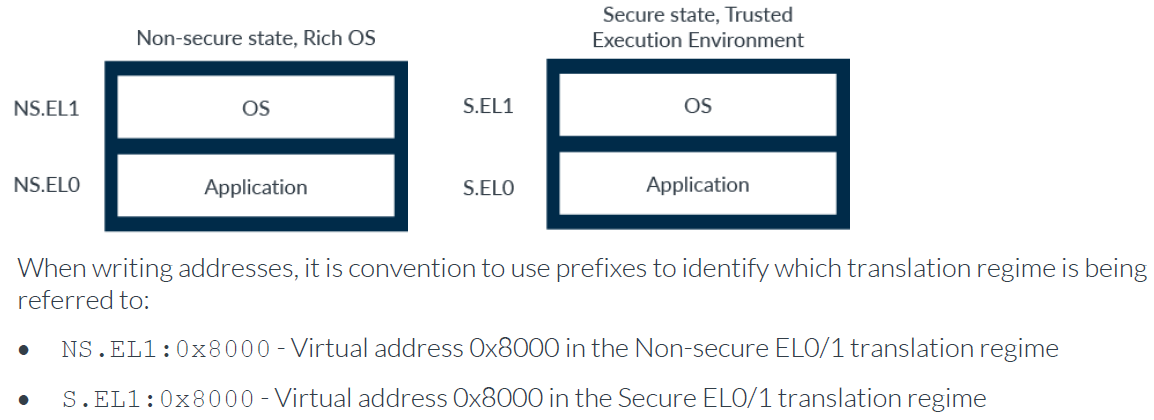
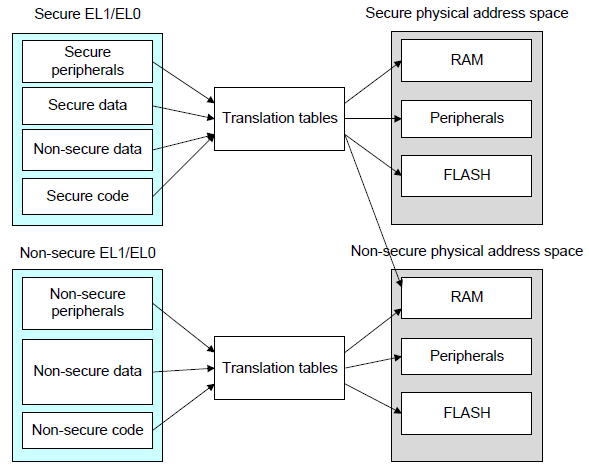
Physical Address Spaces
In addition to two Security states, the architecture provides two physical address spaces: Secure and Non-secure. While in Non-secure state, virtual addresses always translate to Non-secure physical addresses. While in Secure state, software can access both the Secure and Non-secure physical address spaces.
Cache & TLB
In the Arm architecture, data caches are physically tagged.
The TLB records which translation regime, including the Security state, an entry represents.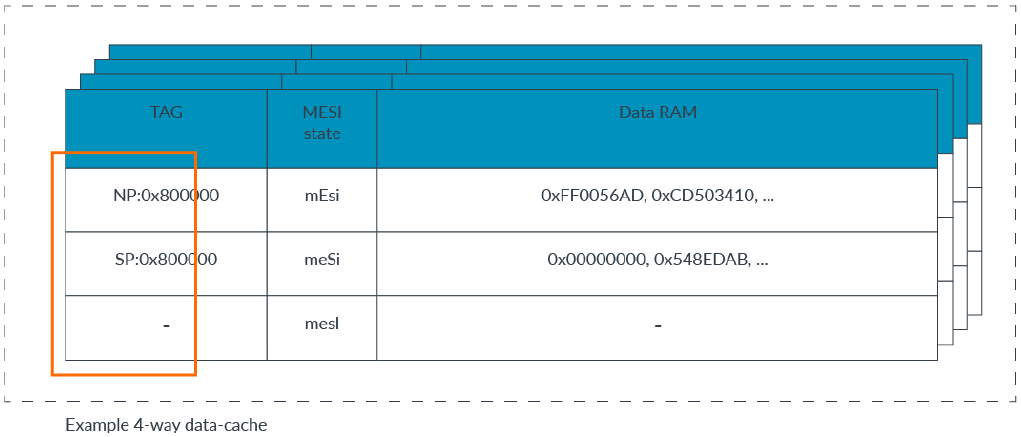
Trustzone Software Architecture (How)
Trusted Firmware
Trusted Firmware is an open-source reference implementation of Secure world software for Armv8-A devices. Trusted Firmware provides SoC developers and OEMs with a reference Trusted code base that complies with the relevant Arm specifications, including TBBR and SMCC.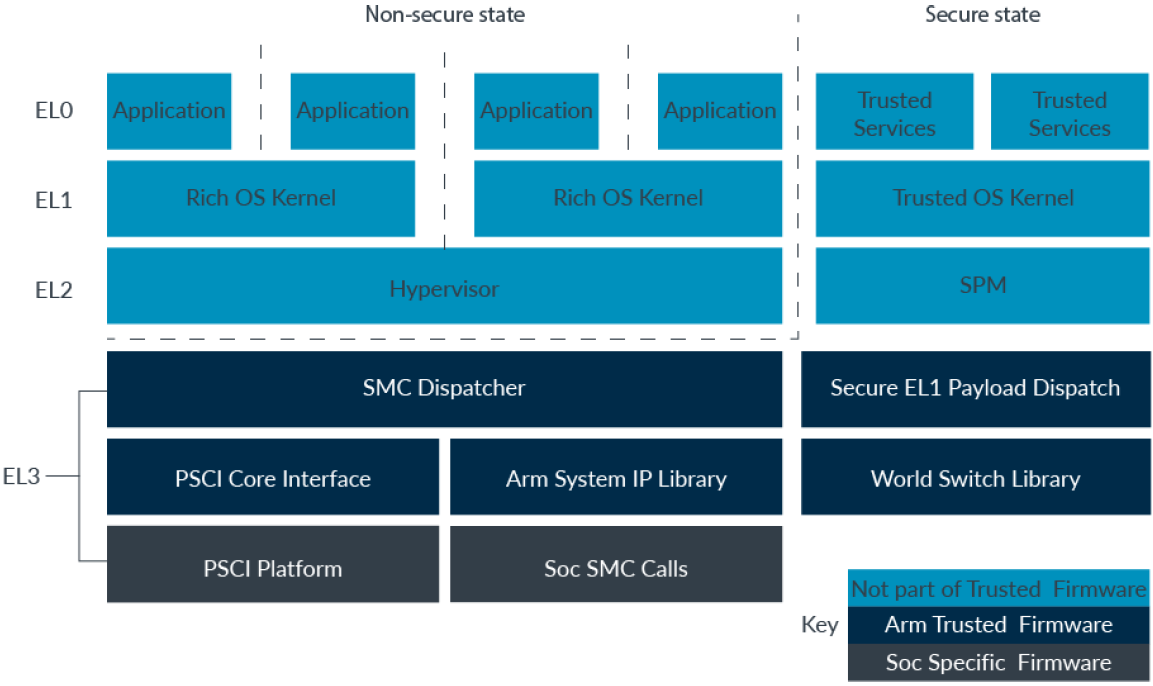
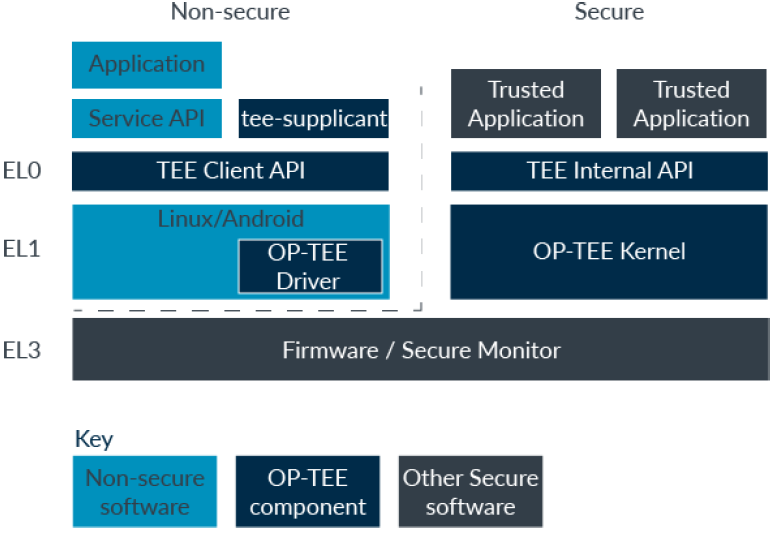
OPTEE
There are many Trusted kernels, both commercial and open source. One example is OP-TEE, originally developed by ST-Ericsson, but now an open- source project hosted by Linaro. OP-TEE provides a fully featured Trusted Execution Environment, and you can find a detailed description on the OP-TEE project website.