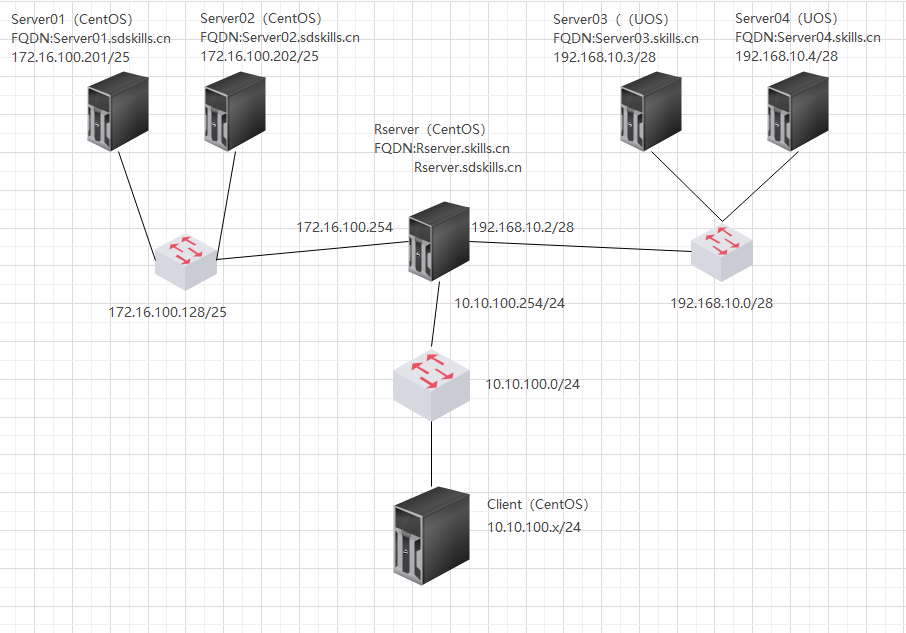
1 配置任务
在Server02上配置邮件服务器 · Postfix • sdskills.cn 的邮件发送服务器 • 支持smtps(465)协议连接,使用Rserver颁发的证书,证书路径/CA/cacert.pem • 创建邮箱账户“user1~user99”(共99个用户),密码为Chinaskill20!; · Dovecot • sdskills.cn 的邮件接收服务器; • 支持imaps(993)协议连接,使用Rserver颁发的证书,证书路径/CA/cacert.pem; • 请保留至少两个用户已成功登录并能正常收发邮件,以方便测试.
2 配置过程
2.1 配置前的准备工作
2.1.1. 配置好DNS服务器
参照DNS服务器配置场景一
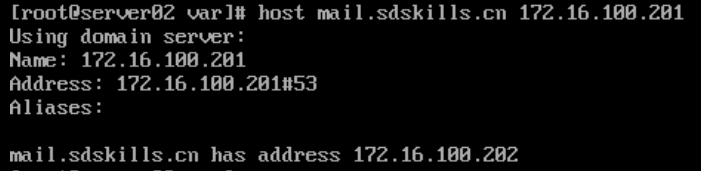
在Server01上需要配置好DNS服务器,能够实现对sdskills.cn的域名解析,并且已经创建了MX记录和邮件服务器的A记录。如下所示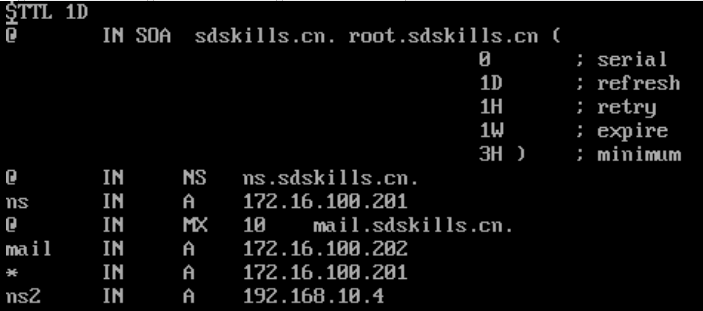
在Server02以及其他测试邮件系统的计算机上将Server01作为DNS服务器,能够解析邮件服务器的域名。
在Server02或者其他测试邮件系统的计算机上安装bind-utils 工具(DNS客户端测试工具) yum -y install bind-utils 可以使用如下命令测试DNS服务器对域名的解析
2.1.2 配置好CA服务器
在RServer上配置CA • CA根证书路径/CA/cacert.pem; • 签发数字证书,颁发者信息: 国家 = CN 单位 = Inc 组织机构 = www.skills.com 公用名 = Skill Global Root CA • 创建用户组ldsgp ,将zsuser、lsusr、wuusr添加到组内。
可以参考这个文档 4-搭建私有CA.pdf
:::info
在RSERVER上搭建CA认证中心
(1)创建所需目录级文件
[root@rserver ~]# touch /etc/pki/CA/index.txt
#创建生成证书索引数据库文件
[root@rserver ~]# echo 01 > /etc/pki/CA/serial
#创建serial文件并指定第一个颁发证书的序列号
(2)生成私钥
[root@rserver ~]# cd /etc/pki/CA
[root@rserver CA]# umask 066
[root@rserver CA]# openssl genrsa -out private/cakey.pem -des3 2048
#在private目录下生成以des3算法加密的私钥文件,私钥长度为2048位,并设定私钥文件的权限为属主读写。
Generating RSA private key, 2048 bit long modulus …………………….+++
……………+++ e is 65537 (0x10001)
Enter pass phrase for private/cakey.pem: #输入私钥加密口令,输入不会回显。
Verifying - Enter pass phrase for private/cakey.pem: #确认加密口令
(3)生成自签名证书
[root@rserver CA]# openssl req -x509 -key private/cakey.pem -out cacert.pem -days 7300
Enter pass phrase for private/cakey.pem:
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter ‘.’, the field will be left blank.
——-
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:SiChuan
Locality Name (eg, city) [Default City]:Luzhou
Organization Name (eg, company) [Default Company Ltd]:Inc
Organizational Unit Name (eg, section) []:www.skills.com
Common Name (eg, your name or your server’s hostname) []:Skill Global Root CA
Email Address []:
[root@rserver CA]# ls
cacert.pem certs crl index.txt newcerts private serial
[root@rserver CA]# ls -l cacert.pem
-rw———-. 1 root root 1359 6月 29 23:29 cacert.pem
2.2 在Server02安装邮件服务器端软件
在Server02上安装电子邮件服务器软件之前,确认Server02能够访问DNS服务器(Server01,172.16.100.201),能够解析域名mail.sdskills.cn。
关闭Server02上面的SELinux和防火墙。
2.2.1 在Server02安装配置邮件发送服务器软件包
1.在Server02上安装postfix、dovecot、cyrus-sasl软件
:::info
[root@server02 ~]# yum -y install profix dovecot cyrus-sasl
说明:
(1)postfix是邮件发送服务器端软件
(2)dovecot是邮件接收服务器端软件
(3)cyus-sasl 访问控制软件
:::
2.启动saslauthd服务
:::info
[root@server02 ~]# systemctl restart saslauthd
[root@server02 ~]# systemctl enable saslauthd
:::
3. 修改/etc/postfix/main.cf配置文件
:::info
[root@server02 ~]# cd /etc/postfix
[root@server02 postfix]# cp main.cf main.cf.origin
#将main.cf文件进行备份
[root@server02 postfix]# vi main.cf
:::
修改main.cf配置文件内容如下:
myhostname = mail.sdskills.cn mydomain = sdskills.cn myorigin = $mydomain inet_interfaces = all mydestination = $myhostname, localhost.$mydomain , localhost , $domain
home_mailbox = Maildir/
smtpd_sasl_auth_enable = yes
说明:
(1)上述配置内容在配置文件为注释,去掉注释修改一下就可以了。
(2)上述配置与域名设置、邮箱设置有关
smtpd_sasl_auth_enable = yes smtpd_sasl_security_options = noanonymous smtpd_recipient_restrictions = permit_mynetworks,permit_sasl_authenticated,reject_unauth_destination
说明:
(1)上述配置系统没有预定义,需要手工添加到配置文件末尾
(2)上述配置与认证方式有关
重启postfix服务
:::info
[root@server02 conf.d]# systemctl restart postfix
[root@server02 conf.d]# systemctl enable postfix
可以使用如下命令查看postfix的端口是否正常运行
[root@server02 postfix]# netstat -anpt | grep ‘master’
tcp 0 0 127.0.0.1:25 0.0.0.0: LISTEN 1036/master
tcp6 0 0 ::1:25 ::: LISTEN 1036/master
#说明:
#如果没有netstat软件,可以使用如下命令安装
#[root@server02 postfix]# yum -y install net-tools
:::
4.创建电子邮件登录账户user1和user2
:::info
[root@server02 postfix]# useradd user1
[root@server02 postfix]# echo ‘Chinaskill20!’ | passwd —stdin user1
更改用户 user1 的密码 。
passwd:所有的身份验证令牌已经成功更新。
[root@server02 postfix]# useradd user2
[root@server02 postfix]# echo ‘Chinaskill20!’ | passwd —stdin user2
更改用户 user2 的密码 。
passwd:所有的身份验证令牌已经成功更新。
:::
批量创建100个用户可以使用如下脚本程序
#!/bin/bash#addusers.shfor i in $(seq 3 100)douseradd user${i}echo 'Chinaskills20!' | passwd --stdin user${i}done
2.2.2 配置邮件接收服务器软件包
1.修改/etc/dovecot/dovecot.conf配置文件
:::danger
protocols = imap pop3 lmtp
disable_plaintext_auth = no
#说明:
# 允许用户使用明文进行密码验证。之所以这样操作,是因为Dovecot服务程序为了保证电子邮件系统的安全而默认强制用户使用加密方式进行登录,而由于当前还没有加密系统,因此需要添加该参数来允许用户的明文登录。
:::
2.修改/etc/dovecot/conf.d/10-mail.conf
在Dovecot服务程序单独的子配置文件中,定义一个路径,用于指定要将收到的邮件存放到服务器本地的哪个位置。这个路径默认已经定义好了,只需要将该配置文件中对应行的井号(#)删除即可。
:::danger
mail_location = mbox:/var/mail/%d/%1n/%n:INDEX=/var/indexes/%d/%1n/%n
:::
3.修改/etc/dovecot/conf.d/10-ssl.conf配置文件
:::danger
ssl = no
注释掉下面两项
#ssl_cert = #ssl_key =
4.重启dovecot服务
:::info
[root@server02 dovecot]# systemctl restart dovecot
[root@server02 dovecot]# systemctl enable dovecot
:::
2.3 在Server02上进行邮件访问测试
1.在Server02上安装mailx软件
:::info [root@server02 conf.d]# yum -y install mailx :::
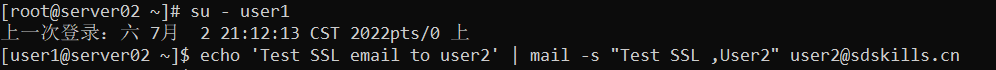
2.切换到user1的身份,使用mail给user2发送电子邮件
:::info
[root@server02 user2]# su - user1
上一次登录:六 7月 2 21:10:33 CST 2022pts/0 上
[user1@server02 ~]$ echo ‘Test email to user2’ | mail -s “Test,User2” user2@sdskills.cn
#这个命令用来向user2@sdskills.cn发送电子邮件
[user1@server02 ~]$ exit
:::
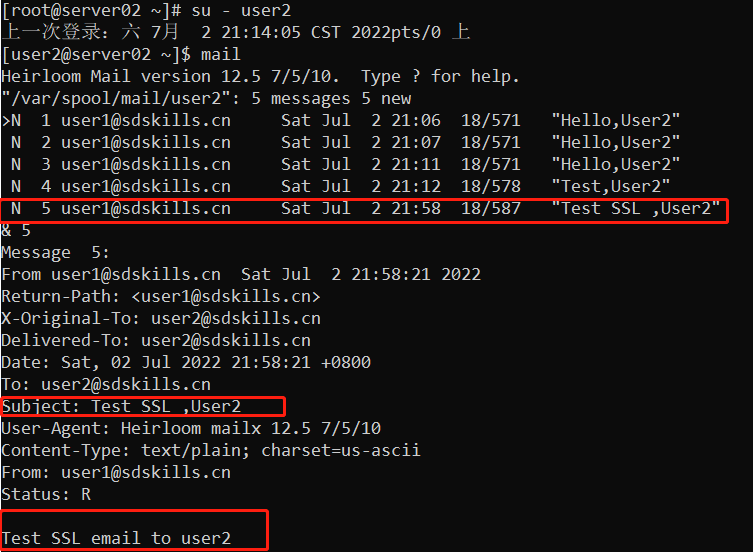
切换到user2身份,使用mail接收邮件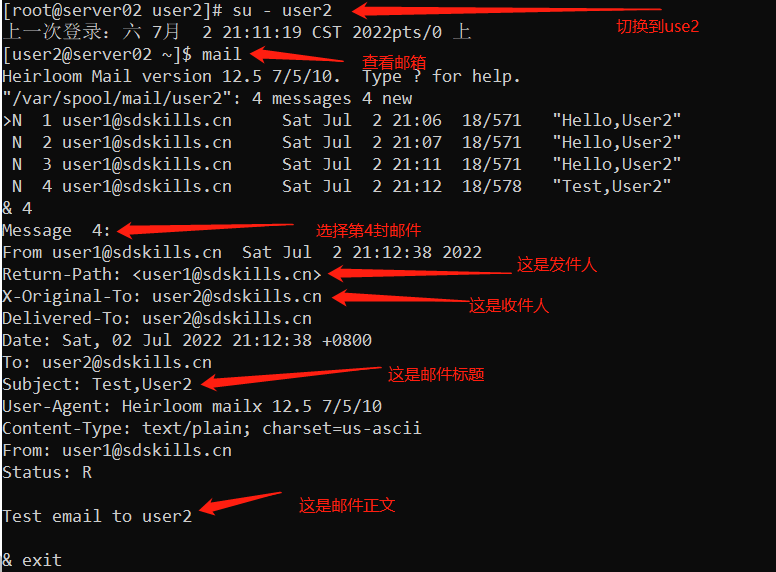
2.4 配置邮件服务器SSL
1.在Server02上生成服务器的私钥文件mail.pem
:::info
[root@server02 ~]# cd /etc/pki/tls/private
[root@server02 private]# openssl genrsa 2048 > mail.pem
Generating RSA private key, 2048 bit long modulus
………………………………………………………+++
……………………………………………………………………+++
e is 65537 (0x10001)
[root@server02 private]# ls -l
总用量 4
-rw-r—r—. 1 root root 1679 7月 2 21:19 mail.pem
[root@server02 private]# chmod 600 mail.pem
:::
2.在Server02上生成SSL证书申请文件mail.csr
:::info
[root@server02 private]# openssl req -new -key mail.pem > ~/mail.csr
#注意:mail.csr证书申请文件是存放在/root目录下
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter ‘.’, the field will be left blank.
——-
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:SiChuan
Locality Name (eg, city) [Default City]:Luzhou
Organization Name (eg, company) [Default Company Ltd]:Inc
Organizational Unit Name (eg, section) []:sdskills.cn
Common Name (eg, your name or your server’s hostname) []:mail.sdskills.cn
Email Address []:
Please enter the following ‘extra’ attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
[root@server02 private]# cd ~
[root@server02 ~]# ls -l
总用量 8
-rw———-. 1 root root 1383 4月 8 17:35 anaconda-ks.cfg
-rw-r—r—. 1 root root 1013 7月 2 21:23 mail.csr
:::
3.将证书申请上传给Rserver(CA Server)
:::info
[root@server02 ~]# scp /root/mail.csr root@172.16.100.254:/etc/pki/CA
#将mail.csr文件上传给Rserver,这里使用的是scp 命令传送的。
The authenticity of host ‘172.16.100.254 (172.16.100.254)’ can’t be established.
ECDSA key fingerprint is SHA256:Ja9VJfWivnH/nqY40iHswSLzkH3vP7DW/tWCnbaMsJY.
ECDSA key fingerprint is MD5:a1:82:73:c2:79:96:8f:18:60:d6:c9:24:fe:56:33:1c.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added ‘172.16.100.254’ (ECDSA) to the list of known hosts.
root@172.16.100.254’s password:
mail.csr 100% 1013 759.3KB/s 00:00
:::
4.在RServer上为邮件服务器生成SSL证书
:::info
[root@rserver ~]# cd /etc/pki/CA
[root@rserver CA]# openssl ca -in mail.csr -out ./newcerts/cacert.pem -days 365
Using configuration from /etc/pki/tls/openssl.cnf
Enter pass phrase for /etc/pki/CA/private/cakey.pem: #这里输入CA 私钥的使用密码
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 2 (0x2)
Validity
Not Before: Jul 2 21:32:46 2022 GMT
Not After : Jul 2 21:32:46 2023 GMT
Subject:
countryName = CN
stateOrProvinceName = SiChuan
organizationName = Inc
organizationalUnitName = sdskills.cn
commonName = mail.sdskills.cn
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
5E:38:F7:89:8B:77:D9:E0:2C:DE:22:A1:35:47:01:57:18:58:C5:61
X509v3 Authority Key Identifier:
keyid:29:53:CA:3E:CF:B1:35:0A:6D:43:23:A4:9C:C5:DD:C4:40:44:6D:B4
Certificate is to be certified until Jul 2 21:32:46 2023 GMT (365 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
:::
查看cacert.pem文件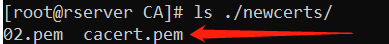
5.从Rserver上将邮件服务器的证书下发给邮件服务器Server02
:::info
[root@rserver CA]# scp ./newcerts/cacert.pem root@172.16.100.202:/etc/pki/tls/certs
root@172.16.100.202’s password:
cacert.pem 100% 4508 2.2MB/s 00:00
:::
在Server02上查看cacert.pem文件
6.修改postfix的配置文件/etc/postfix/main.cf,支持SSL加密
在/etc/postfix/main.cf配置文件末尾添加如下内容:
:::danger
smtpd_use_tls = yes
smtpd_tls_key_file = /etc/pki/tls/private/mail.pem
smtpd_tls_cert_file = /etc/pki/tls/certs/cacert.pem
:::
修改完成后,重启postfix服务
:::info
[root@server02 ~]# systemctl restart postfix
:::
7.修改dovecot配置文件,支持SSL加密通信
修改 /etc/dovecot/conf.d/10-ssl.conf
:::danger
ssl = yes
ssl_cert = ssl_key =
2.5 在Server02上进行邮件访问测试
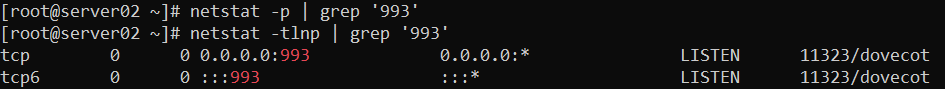
1.查看993端口
2.切换到user1的身份,使用mail给user2发送电子邮件
3.切换到user2身份,使用mail接收邮件
参考文献
[1] CentOS 7 安装 Postfix Dovecot https://blog.csdn.net/mshxuyi/article/details/105194383
[2] CentOS7下搭建邮件服务器(dovecot + postfix + SSL) http://t.zoukankan.com/cp-miao-p-5783552.html
[3] Centos 下搭建postfix和Dovecot的邮箱服务系统 https://blog.csdn.net/qq_35158197/article/details/123308532
.[4] Linux搭建邮件服务器postfix 6https://blog.csdn.net/qq_34267076/article/details/120024075
[5] Linux之POSTFIX邮件服务 https://blog.csdn.net/qq_46839776/article/details/120027066
[6] Linux-企业邮件部署-Postfix https://www.cnblogs.com/weicunqi/p/15272298.html
[7] 第15章 使用 Postfix 与 Dovecot 部署邮件系统 https://www.wenjiangs.com/doc/rvfwaeh3
[8] mail postfix dovecot SSL https://blog.csdn.net/weixin_46248008/article/details/120024550
[9] Postfix+SSL配置
postfix配置ssl - CSDN
[10] centos7邮件服务器SSL配置 https://www.cnblogs.com/operationhome/p/9084446.html
[11] 2022年中职国赛网搭样题postfix+dovecot+ssl https://www.bilibili.com/video/BV1Vr4y1J7K4?spm_id_from=333.337.search-card.all.click
[12] postfix官网文档 https://de.postfix.org/httpmirror/documentation.html
[13] openssl pem 生成公钥和私钥及文件 https://blog.csdn.net/yiyihuazi/article/details/123257184https://blog.csdn.net/sirobot/article/details/115765132?spm=1001.2101.3001.6661.1&utm_medium=distribute.pc_relevant_t0.none-task-blog-2%7Edefault%7ECTRLIST%7Edefault-1-115765132-blog-123257184.pc_relevant_aa&depth_1-utm_source=distribute.pc_relevant_t0.none-task-blog-2%7Edefault%7ECTRLIST%7Edefault-1-115765132-blog-123257184.pc_relevant_aa&utm_relevant_index=1
[14] CentOS7下搭建postfix邮箱服务器并实现extmail的web访问 https://blog.51cto.com/zero01/2064693
[15] postfix 实现 tls smtps pop3s https://blog.51cto.com/fghjk/836444
[16] 邮件TLS/SSL加密通信 https://blog.51cto.com/u_13735155/2134584