- https://github.com/volatilityfoundation/volatility/wiki/Command-Reference
- https://code.google.com/archive/p/volatility/wikis/CommandReference.wiki
工具
Volatility
amcache Print AmCache informationapihooks Detect API hooks in process and kernel memoryatoms Print session and window station atom tablesatomscan Pool scanner for atom tablesauditpol Prints out the Audit Policies from HKLM\SECURITY\Policy\PolAdtEvbigpools Dump the big page pools using BigPagePoolScannerbioskbd Reads the keyboard buffer from Real Mode memorycachedump Dumps cached domain hashes from memorycallbacks Print system-wide notification routinesclipboard Extract the contents of the windows clipboardcmdline Display process command-line argumentscmdscan Extract command history by scanning for _COMMAND_HISTORYconnections Print list of open connections [Windows XP and 2003 Only]connscan Pool scanner for tcp connectionsconsoles Extract command history by scanning for _CONSOLE_INFORMATIONcrashinfo Dump crash-dump informationdeskscan Poolscaner for tagDESKTOP (desktops)devicetree Show device treedlldump Dump DLLs from a process address spacedlllist Print list of loaded dlls for each processdriverirp Driver IRP hook detectiondrivermodule Associate driver objects to kernel modulesdriverscan Pool scanner for driver objectsdumpcerts Dump RSA private and public SSL keysdumpfiles Extract memory mapped and cached filesdumpregistry Dumps registry files out to diskeditbox Displays information about Edit controls. (Listbox experimental.)envars Display process environment variableseventhooks Print details on windows event hooksevtlogs Extract Windows Event Logs (XP/2003 only)filescan Pool scanner for file objectsgahti Dump the USER handle type informationgditimers Print installed GDI timers and callbacksgdt Display Global Descriptor Tablegetservicesids Get the names of services in the Registry and return Calculated SIDgetsids Print the SIDs owning each processhandles Print list of open handles for each processhashdump Dumps passwords hashes (LM/NTLM) from memoryhibinfo Dump hibernation file informationhivedump Prints out a hivehivelist Print list of registry hives.hivescan Pool scanner for registry hiveshpakextract Extract physical memory from an HPAK filehpakinfo Info on an HPAK fileidt Display Interrupt Descriptor Tableiehistory Reconstruct Internet Explorer cache / historyimagecopy Copies a physical address space out as a raw DD imageimageinfo Identify information for the imageimpscan Scan for calls to imported functionsjoblinks Print process job link informationkdbgscan Search for and dump potential KDBG valueskpcrscan Search for and dump potential KPCR valuesldrmodules Detect unlinked DLLslsadump Dump (decrypted) LSA secrets from the registrymachoinfo Dump Mach-O file format informationmalfind Find hidden and injected codembrparser Scans for and parses potential Master Boot Records (MBRs)memdump Dump the addressable memory for a processmemmap Print the memory mapmessagehooks List desktop and thread window message hooksmftparser Scans for and parses potential MFT entriesmoddump Dump a kernel driver to an executable file samplemodscan Pool scanner for kernel modulesmodules Print list of loaded modulesmultiscan Scan for various objects at oncemutantscan Pool scanner for mutex objectsnotepad List currently displayed notepad textobjtypescan Scan for Windows object type objectspatcher Patches memory based on page scanspoolpeek Configurable pool scanner pluginprintkey Print a registry key, and its subkeys and valuesprivs Display process privilegesprocdump Dump a process to an executable file samplepslist Print all running processes by following the EPROCESS listspsscan Pool scanner for process objectspstree Print process list as a treepsxview Find hidden processes with various process listingsqemuinfo Dump Qemu informationraw2dmp Converts a physical memory sample to a windbg crash dumpscreenshot Save a pseudo-screenshot based on GDI windowsservicediff List Windows services (ala Plugx)sessions List details on _MM_SESSION_SPACE (user logon sessions)shellbags Prints ShellBags infoshimcache Parses the Application Compatibility Shim Cache registry keyshutdowntime Print ShutdownTime of machine from registrysockets Print list of open socketssockscan Pool scanner for tcp socket objectsssdt Display SSDT entriesstrings Match physical offsets to virtual addresses (may take a while, VERY verbose)svcscan Scan for Windows servicessymlinkscan Pool scanner for symlink objectsthrdscan Pool scanner for thread objectsthreads Investigate _ETHREAD and _KTHREADstimeliner Creates a timeline from various artifacts in memorytimers Print kernel timers and associated module DPCstruecryptmaster Recover TrueCrypt 7.1a Master Keystruecryptpassphrase TrueCrypt Cached Passphrase Findertruecryptsummary TrueCrypt Summaryunloadedmodules Print list of unloaded modulesuserassist Print userassist registry keys and informationuserhandles Dump the USER handle tablesvaddump Dumps out the vad sections to a filevadinfo Dump the VAD infovadtree Walk the VAD tree and display in tree formatvadwalk Walk the VAD treevboxinfo Dump virtualbox informationverinfo Prints out the version information from PE imagesvmwareinfo Dump VMware VMSS/VMSN informationvolshell Shell in the memory imagewindows Print Desktop Windows (verbose details)wintree Print Z-Order Desktop Windows Treewndscan Pool scanner for window stationsyarascan Scan process or kernel memory with Yara signatures
常用插件
- clipboard
- hivelist
- imageinfo
- lsadump
- malfind
- memdump
pslist、psscan、pstree
案例
JarvisOJ 取证 2(磁盘解密)
https://www.jarvisoj.com/challenges > MISC > 取证 2 还记得取证那题吗?既然有了取证神器,这里有一个可疑文件以及该存储该文件电脑的一个内存快照,那么接下来我们实战一下吧。 由于文件比较大,请大家至百度云盘下载: 链接: http://pan.baidu.com/s/1c2BIGLE 密码: 9v2z
附件 suspicion.7z 解压出来有两个文件:
suspicion:这个不知道是啥文件mem.vmem:这个是内存映像
volatility.exe -f .\mem.vmem imageinfo 查看操作系统类型是 WinXP
Volatility Foundation Volatility Framework 2.6INFO : volatility.debug : Determining profile based on KDBG search...Suggested Profile(s) : WinXPSP2x86, WinXPSP3x86 (Instantiated with WinXPSP2x86)AS Layer1 : IA32PagedMemoryPae (Kernel AS)AS Layer2 : FileAddressSpace (D:\Users\DP\Downloads\mem.vmem)PAE type : PAEDTB : 0xb18000LKDBG : 0x80546ae0LNumber of Processors : 1Image Type (Service Pack) : 3KPCR for CPU 0 : 0xffdff000LKUSER_SHARED_DATA : 0xffdf0000LImage date and time : 2016-05-03 04:41:19 UTC+0000Image local date and time : 2016-05-03 12:41:19 +0800
volatility.exe -f .\mem.vmem pslist 查看进程
Offset(V) Name PID PPID Thds Hnds Sess Wow64 Start Exit---------- -------------------- ------ ------ ------ -------- ------ ------ ------------------------------ ------------------------------0x821b9830 System 4 0 62 253 ------ 00x81fb9210 smss.exe 552 4 3 19 ------ 0 2016-05-03 04:32:10 UTC+00000x81c14da0 csrss.exe 616 552 10 328 0 0 2016-05-03 04:32:12 UTC+00000x81f81880 winlogon.exe 640 552 18 449 0 0 2016-05-03 04:32:12 UTC+00000x8208fda0 services.exe 684 640 16 260 0 0 2016-05-03 04:32:12 UTC+00000x81c32b10 lsass.exe 696 640 18 333 0 0 2016-05-03 04:32:12 UTC+00000x820a19a0 vmacthlp.exe 852 684 1 25 0 0 2016-05-03 04:32:13 UTC+00000x81c30458 svchost.exe 864 684 18 201 0 0 2016-05-03 04:32:13 UTC+00000x81c67020 svchost.exe 948 684 11 238 0 0 2016-05-03 04:32:13 UTC+00000x81ce7da0 svchost.exe 1040 684 55 1103 0 0 2016-05-03 04:32:13 UTC+00000x81c25020 svchost.exe 1096 684 4 66 0 0 2016-05-03 04:32:13 UTC+00000x82002b28 svchost.exe 1256 684 13 194 0 0 2016-05-03 04:32:14 UTC+00000x81f6c988 explorer.exe 1464 1448 12 329 0 0 2016-05-03 04:32:14 UTC+00000x82085550 spoolsv.exe 1576 684 13 140 0 0 2016-05-03 04:32:14 UTC+00000x81f64560 vmtoolsd.exe 1712 1464 5 145 0 0 2016-05-03 04:32:15 UTC+00000x820a3528 ctfmon.exe 1736 1464 1 78 0 0 2016-05-03 04:32:15 UTC+00000x81f7d3c0 vmtoolsd.exe 2020 684 7 273 0 0 2016-05-03 04:32:23 UTC+00000x8207db28 TPAutoConnSvc.e 512 684 5 99 0 0 2016-05-03 04:32:25 UTC+00000x81c26da0 alg.exe 1212 684 6 105 0 0 2016-05-03 04:32:26 UTC+00000x81f715c0 wscntfy.exe 1392 1040 1 39 0 0 2016-05-03 04:32:26 UTC+00000x81e1f520 TPAutoConnect.e 1972 512 1 72 0 0 2016-05-03 04:32:26 UTC+00000x81f9d3e8 TrueCrypt.exe 2012 1464 2 139 0 0 2016-05-03 04:33:36 UTC+0000
发现可疑进程 TrueCrypt.exe,搜索得知是磁盘加密工具,那么 suspicion 应该是被加密的文件
搜索 TrueCrypt 破解软件,找到 EFDD(Elcomsoft Forensic Disk Decryptor),下面开始破解volatility.exe -f .\mem.vmem memdump -p 2012 -D . 将进程 dump 出来
************************************************************************Writing TrueCrypt.exe [ 2012] to 2012.dmp
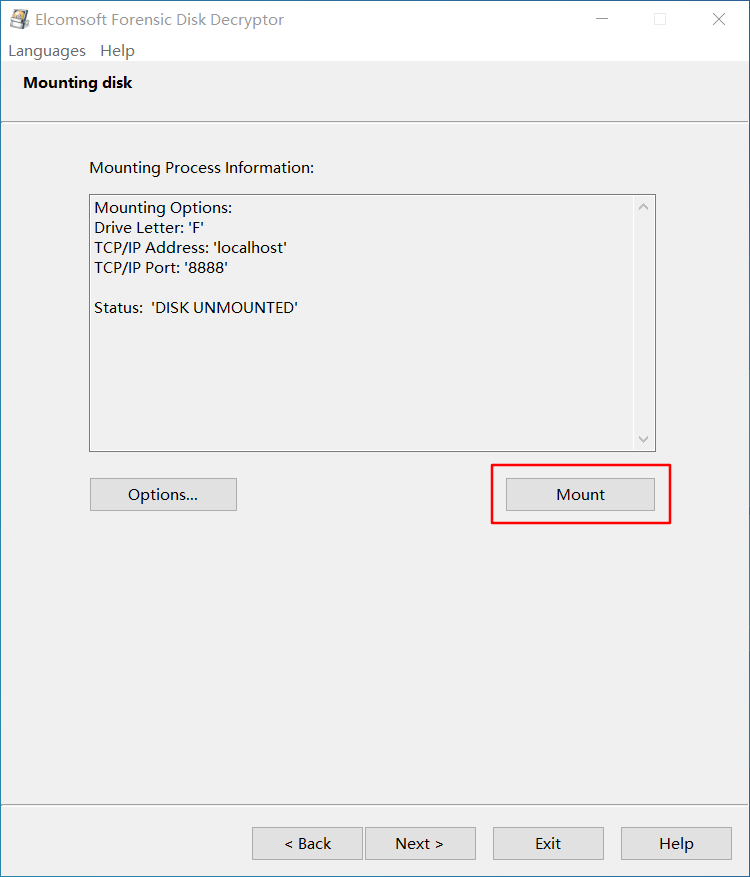
打开 EFDD,选择 suspicion 和 2012.dmp 文件,开始破解密钥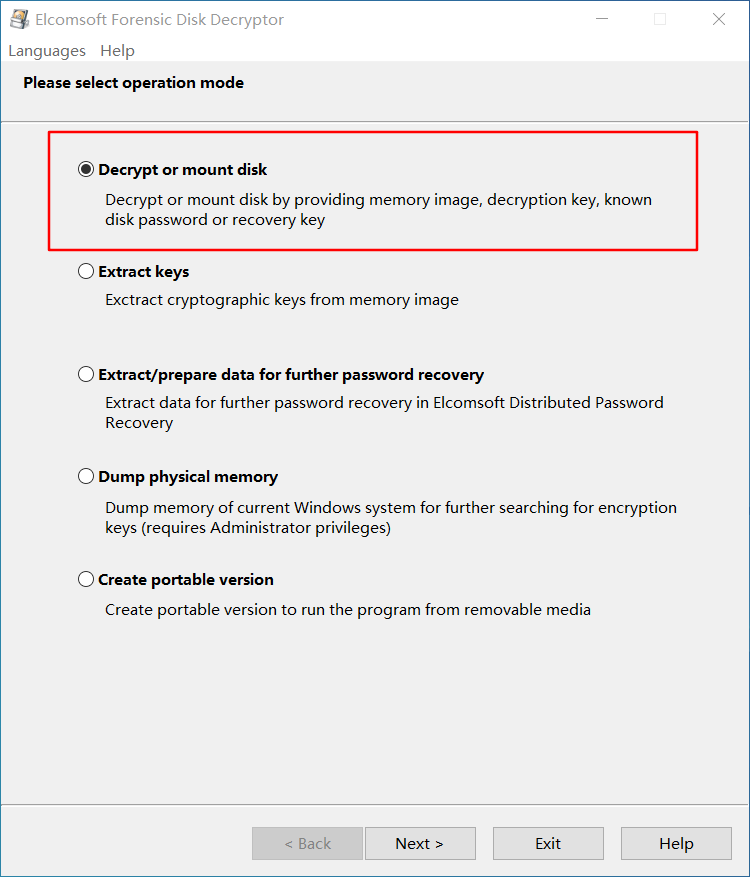
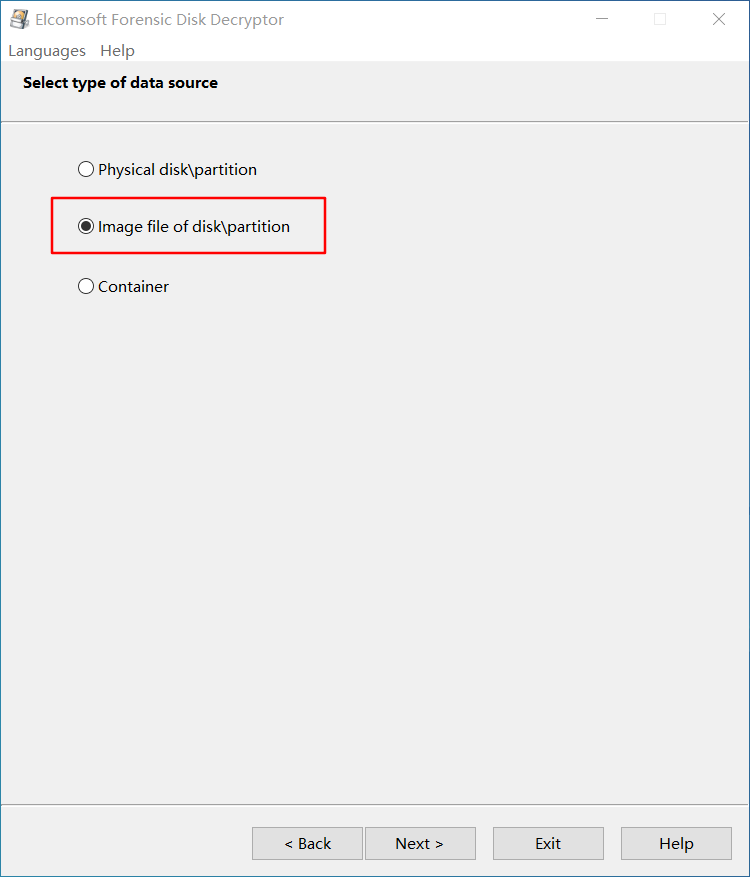
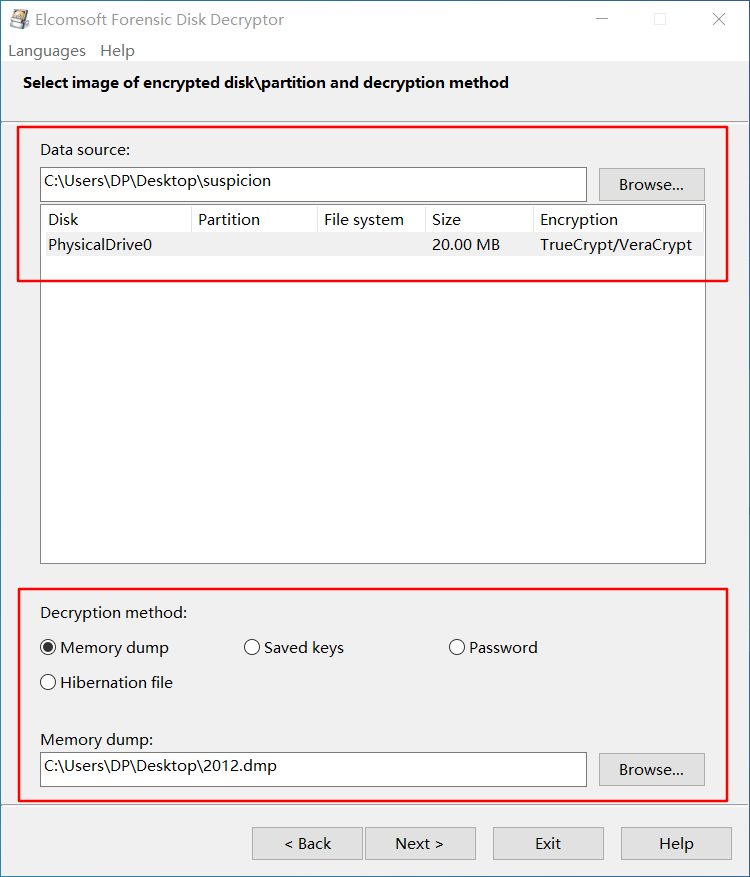
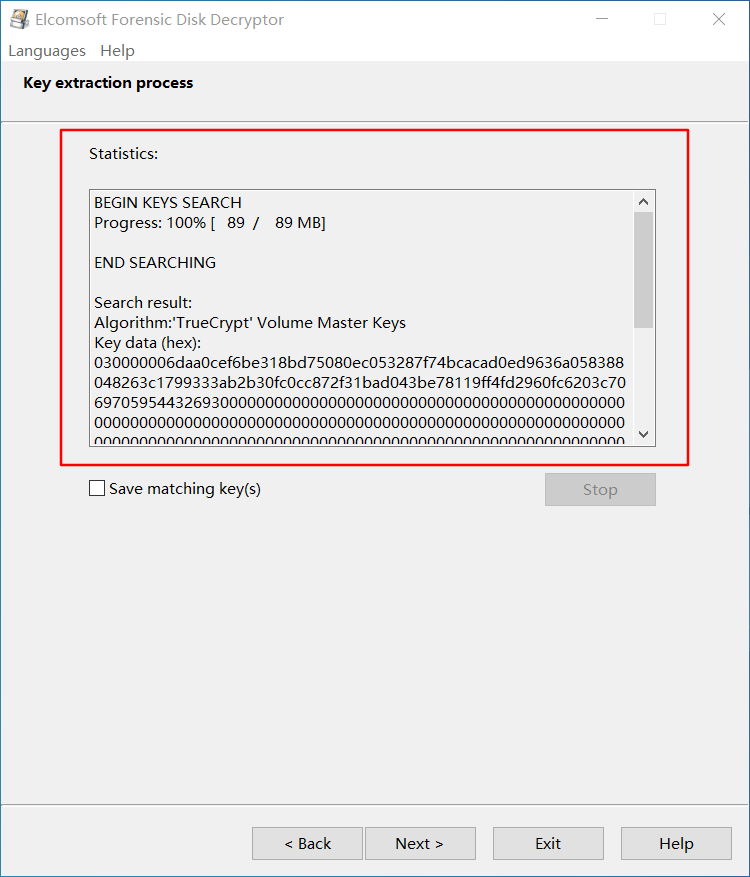
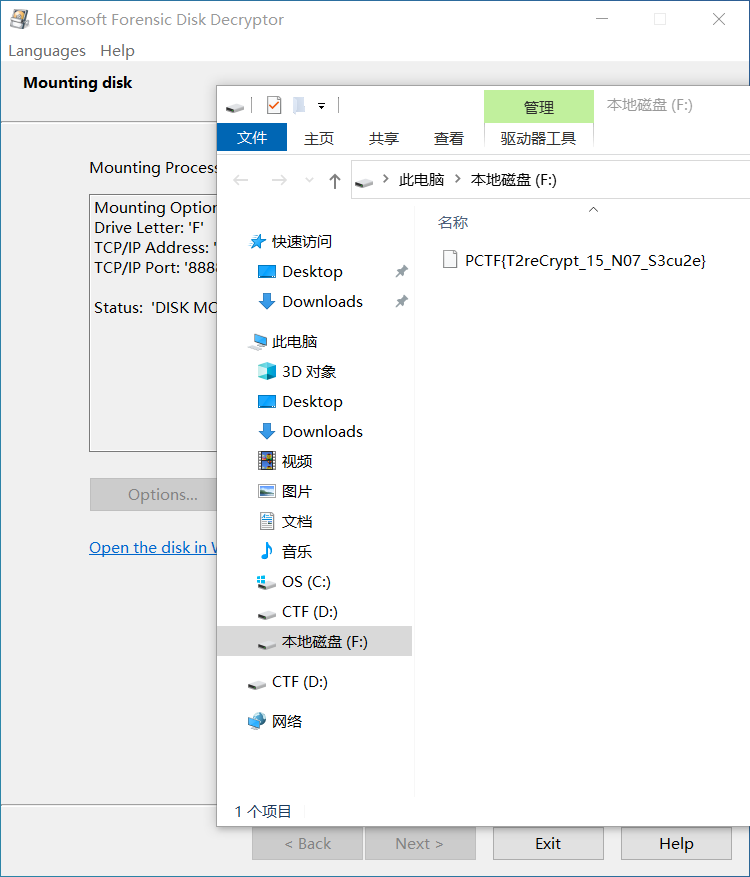
直接用密钥解密磁盘并挂载,发现 flag 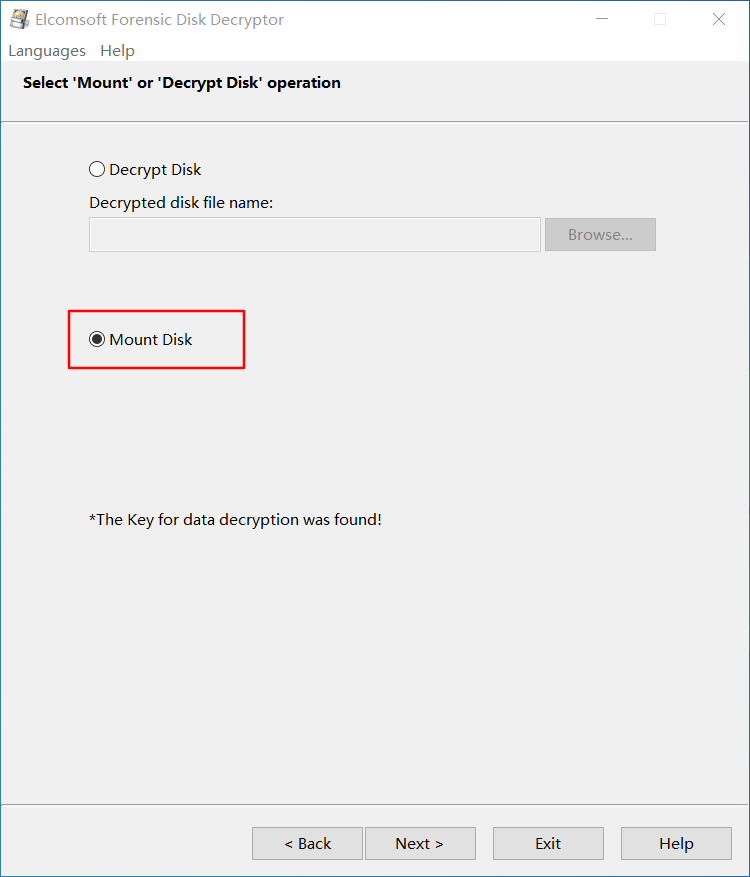
相关链接:

