CVE-2019-12415
In Apache POI up to 4.1.0, when using the tool XSSFExportToXml to convert user-provided Microsoft Excel documents, a specially crafted document can allow an attacker to read files from the local filesystem or from internal network resources via XML External Entity (XXE) Processing.
https://b1ue.cn/archives/241.html
CVE-2016-5000
The XLSX2CSV example in Apache POI before 3.14 allows remote attackers to read arbitrary files via a crafted OpenXML document containing an external entity declaration in conjunction with an entity reference, related to an XML External Entity (XXE) issue.
CVE-2014-3529
The OPC SAX setup in Apache POI before 3.10.1 allows remote attackers to read arbitrary files via an OpenXML file containing an XML external entity declaration in conjunction with an entity reference, related to an XML External Entity (XXE) issue.
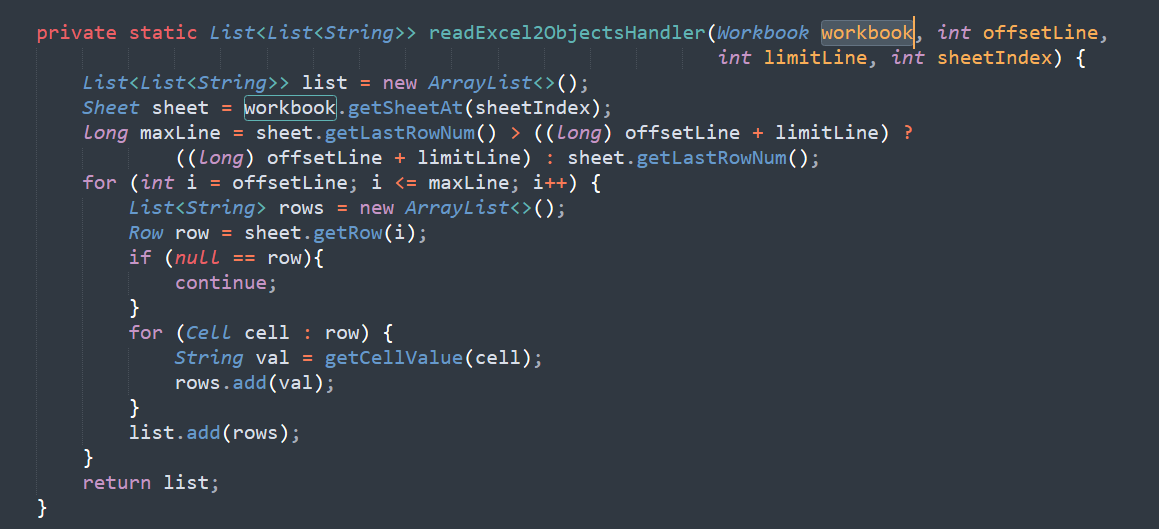
项目1
参数类型
org.springframework.web.multipart.MultipartFile
com.example.crm.common.utils.ImportExcelUtil.read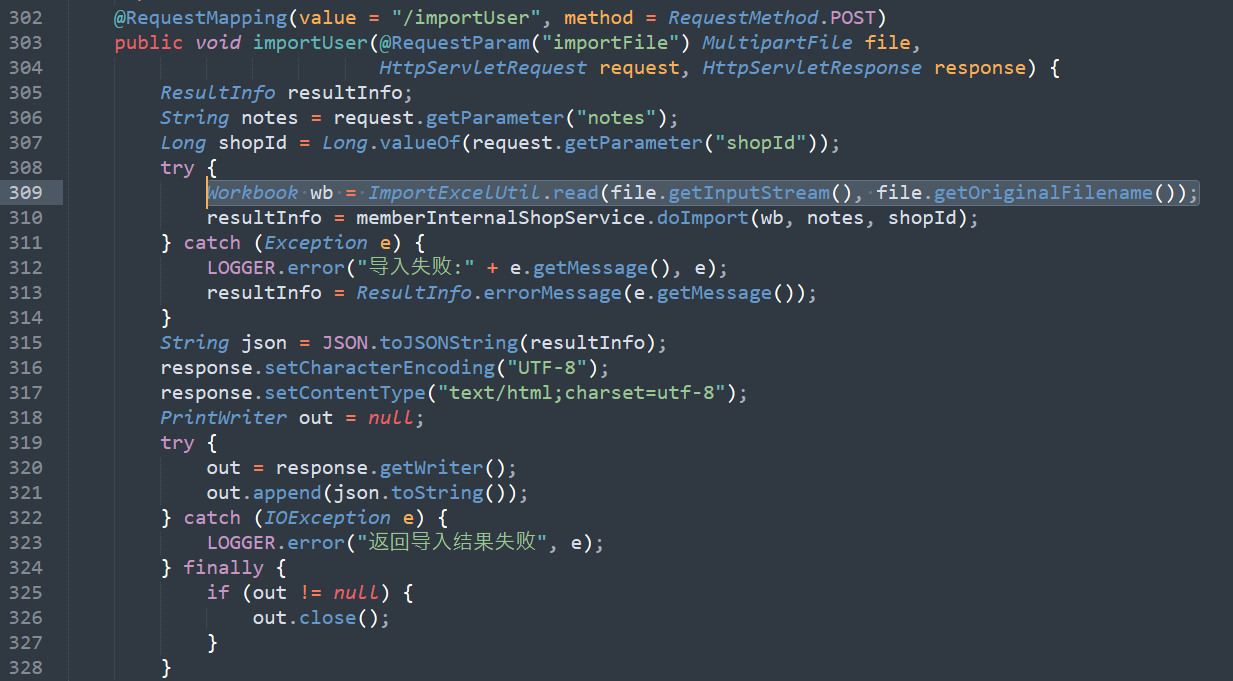
org.apache.poi.poifs.filesystem.POIFSFileSystem
org.apache.poi.hssf.usermodel.HSSFWorkbook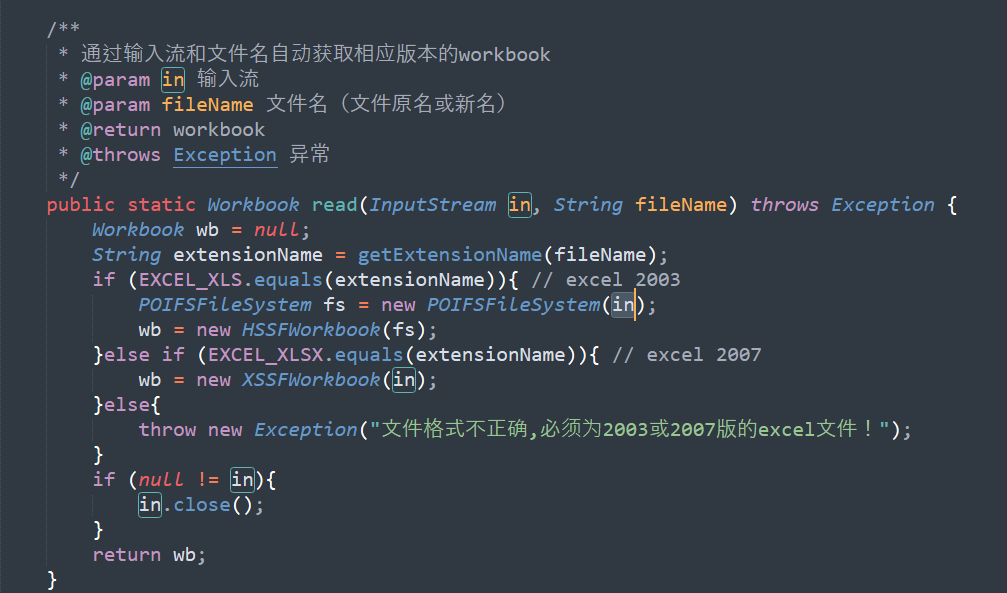
org.apache.poi.ss.usermodel.Workbook.getSheetAt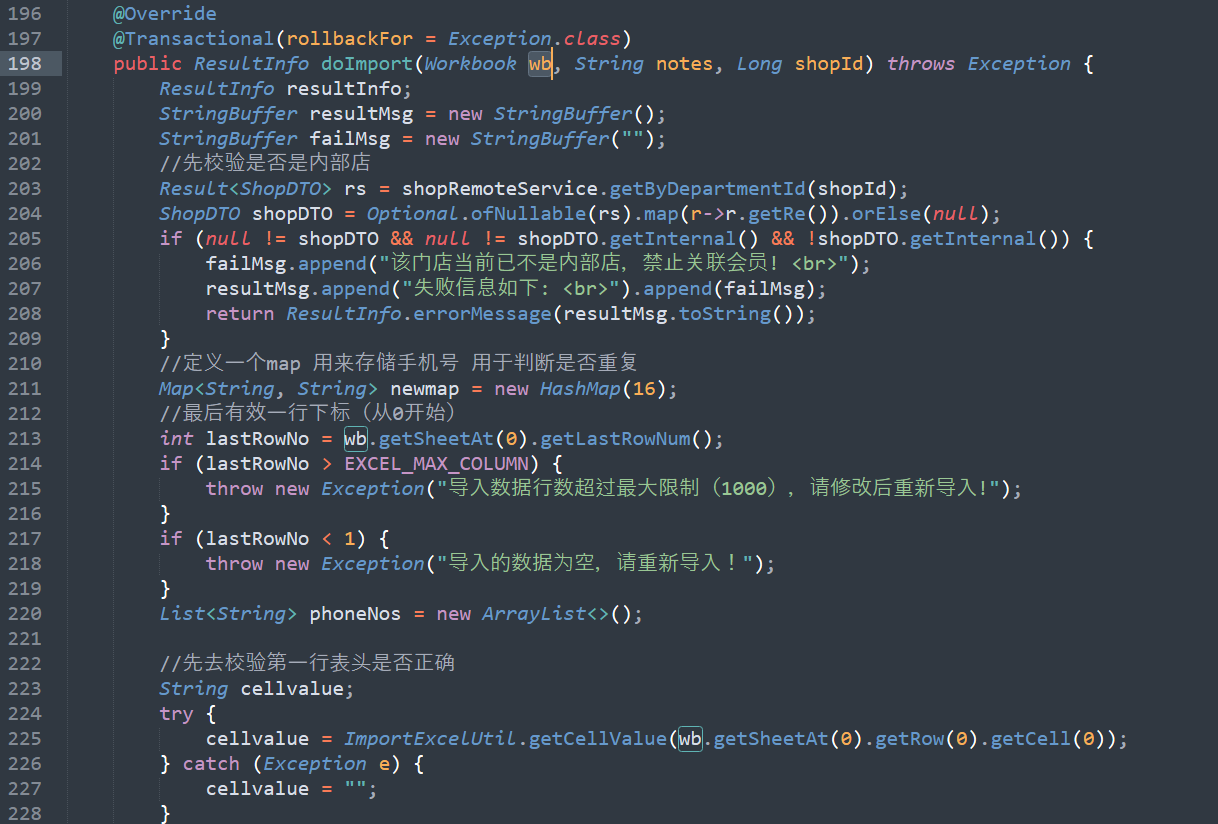
项目2
org.springframework.web.multipart.MultipartFile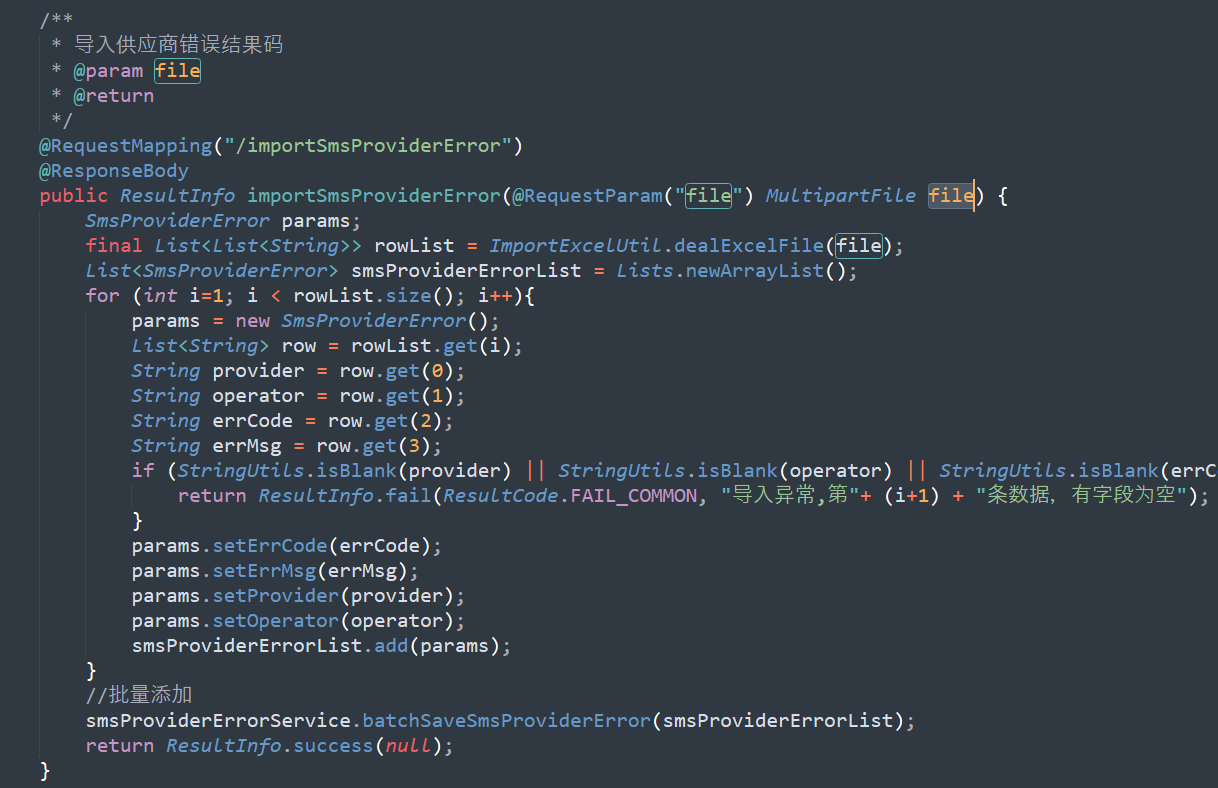
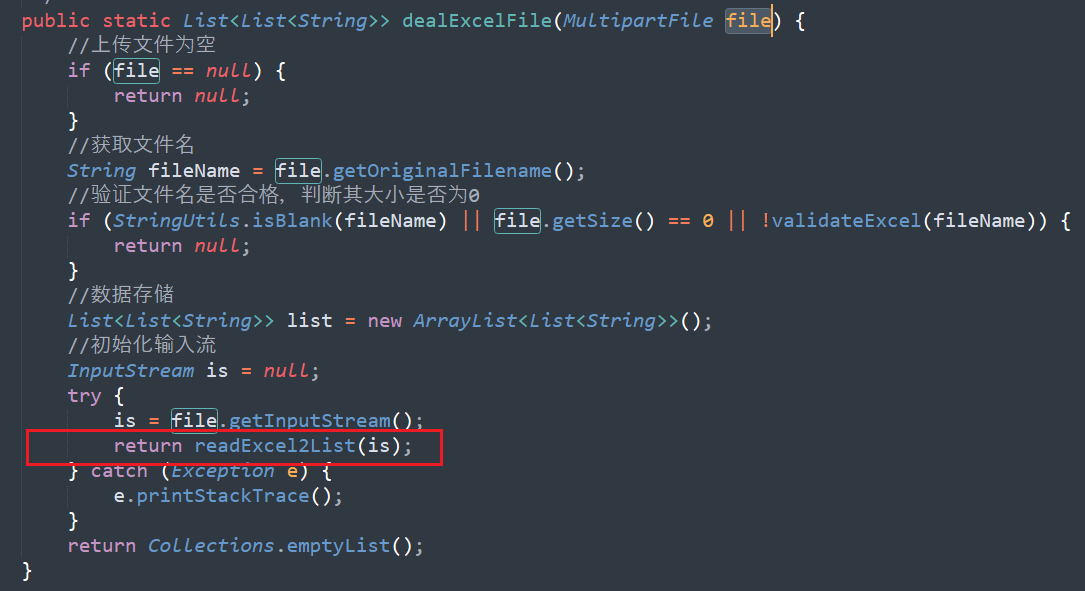
org.apache.poi.ss.usermodel.WorkbookFactory.create
org.apache.poi.ss.usermodel.Workbook
org.apache.poi.ss.usermodel.Workbook.getSheetAt