https://github.com/github/codeql/blob/main/docs/ql-style-guide.md
https://github.com/github/codeql/blob/main/java/ql/src/Security/CWE/CWE-338/JHipsterGeneratedPRNG.ql
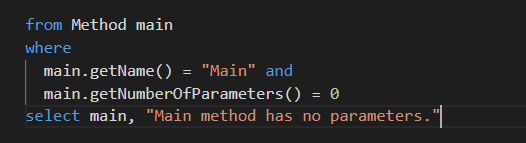
/*** @name Detect JHipster Generator Vulnerability CVE-2019-16303* @description Using a vulnerable version of JHipster to generate random numbers makes it easier for attackers to take over accounts.* @kind problem* @problem.severity error* @security-severity 7.8* @precision very-high* @id java/jhipster-prng* @tags security* external/cwe/cwe-338*/import javaimport semmle.code.java.frameworks.apache.Langprivate class PredictableApacheRandomStringUtilsMethod extends Method {PredictableApacheRandomStringUtilsMethod() {this.getDeclaringType() instanceof TypeApacheRandomStringUtils and// The one valid use of this type that uses SecureRandom as a source of data.not this.getName() = "random"}}private class PredictableApacheRandomStringUtilsMethodAccess extends MethodAccess {PredictableApacheRandomStringUtilsMethodAccess() {this.getMethod() instanceof PredictableApacheRandomStringUtilsMethod}}private class VulnerableJHipsterRandomUtilClass extends Class {VulnerableJHipsterRandomUtilClass() {// The package name that JHipster generated the 'RandomUtil' class in was dynamic. Thus 'hasQualifiedName' can not be used here.getName() = "RandomUtil"}}private class VulnerableJHipsterRandomUtilMethod extends Method {VulnerableJHipsterRandomUtilMethod() {this.getDeclaringType() instanceof VulnerableJHipsterRandomUtilClass andthis.getName().matches("generate%") andthis.getReturnType() instanceof TypeString andexists(ReturnStmt s |s = this.getBody().(SingletonBlock).getStmt() ands.getResult() instanceof PredictableApacheRandomStringUtilsMethodAccess)}}from VulnerableJHipsterRandomUtilMethod methodselect method,"Weak random number generator used in security sensitive method (JHipster CVE-2019-16303)."

