1、开启ad的ssl
请参考官方文档或windows server安装AD DC
或者使用自签名证书开启ssl参考文档
https://bl.ocks.org/magnetikonline/0ccdabfec58eb1929c997d22e7341e45
2、在每个节点上安装krb5
yum install krb5-workstation
编辑krb5配置文件
Configuration snippets may be placed in this directory as well
includedir /etc/krb5.conf.d/
[logging]
default = FILE:/var/log/krb5libs.log
kdc = FILE:/var/log/krb5kdc.log
admin_server = FILE:/var/log/kadmind.log
kinit = {
renewable = ture
forwardable = ture
}
[libdefaults]
default_realm = FAYSON.COM
ticket_lifetime = 24h
renew_lifetime = 7d
forwardable = true
renewable = true
rdns = false
udp_prefrence_limit=0
[realms]
FAYSON.COM = {
kdc = xxx.xxx.xxx.xxx:88
admin_server = xxx.xxx.xxx.xxx:749
kdc = xxx.xxx.xxx.xxx
}
[domain_realm]
.fayson.com = FAYSON.COM
fayson.com = FAYSON.COM
验证
如图所示,使用kinit 命令认证AD中的用户就代表krb5.conf配置成功
kinit sentry_admin
注意:一定要在CDH集群安装完成后开启sssd
yum install -y mlocate sssd authconfig
authconfig --enablesssd --enablesssdauth --enablelocauthorize --enablemkhomedir --update
配置sssd.conf
[sssd]
config_file_version = 2
reconnection_retries = 3
sbus_timeout = 30
services = nss, pam, autofs
domains = FAYSON.COM
[nss]
filter_groups = root
filter_users = root
reconnection_retries = 3
[pam]
reconnection_retries = 3
[domain/FAYSON.COM] #ad的域
debug_level = 7
cache_credentials = False
id_provider = ldap
auth_provider = ldap
chpass_provider = ldap
ldap_uri = ldap://192.168.160.178:389 #AD的ip地址
ldap_schema = rfc2307bis
ldap_referrals = False
ldap_id_mapping = True
fallback_homedir = /home/%u
default_shell = /bin/bash
ldap_default_bind_dn = administrator@fayson.com #ad的用户
ldap_default_authtok_type = password
ldap_default_authtok = xxxxx #ad的密码
ldap_search_base = dc=fayson,dc=com
ldap_user_search_base = dc=fayson,dc=com #AD的域
ldap_user_object_class = user
ldap_user_name = sAMAccountName
ldap_user_member_of = member
ldap_user_objectsid = objectSid
ldap_group_objectsid = objectSid
ldap_group_search_base = dc=fayson,dc=com #搜索基础
ldap_group_object_class = group
ldap_group_name = sAMAccountName
ldap_referrals = false
ldap_use_tokengroups = false
ldap_user_primary_group = primaryGroupID
case_sensitive = false
[autofs]
启动sssd
systemctl start sssd && systemctl enable sssd
验证
注意观察返回回来的gid和uid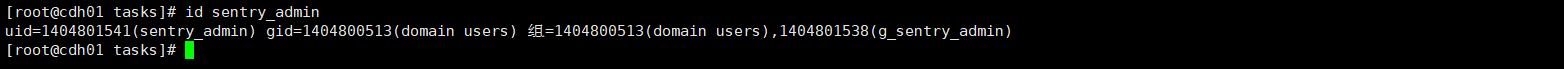
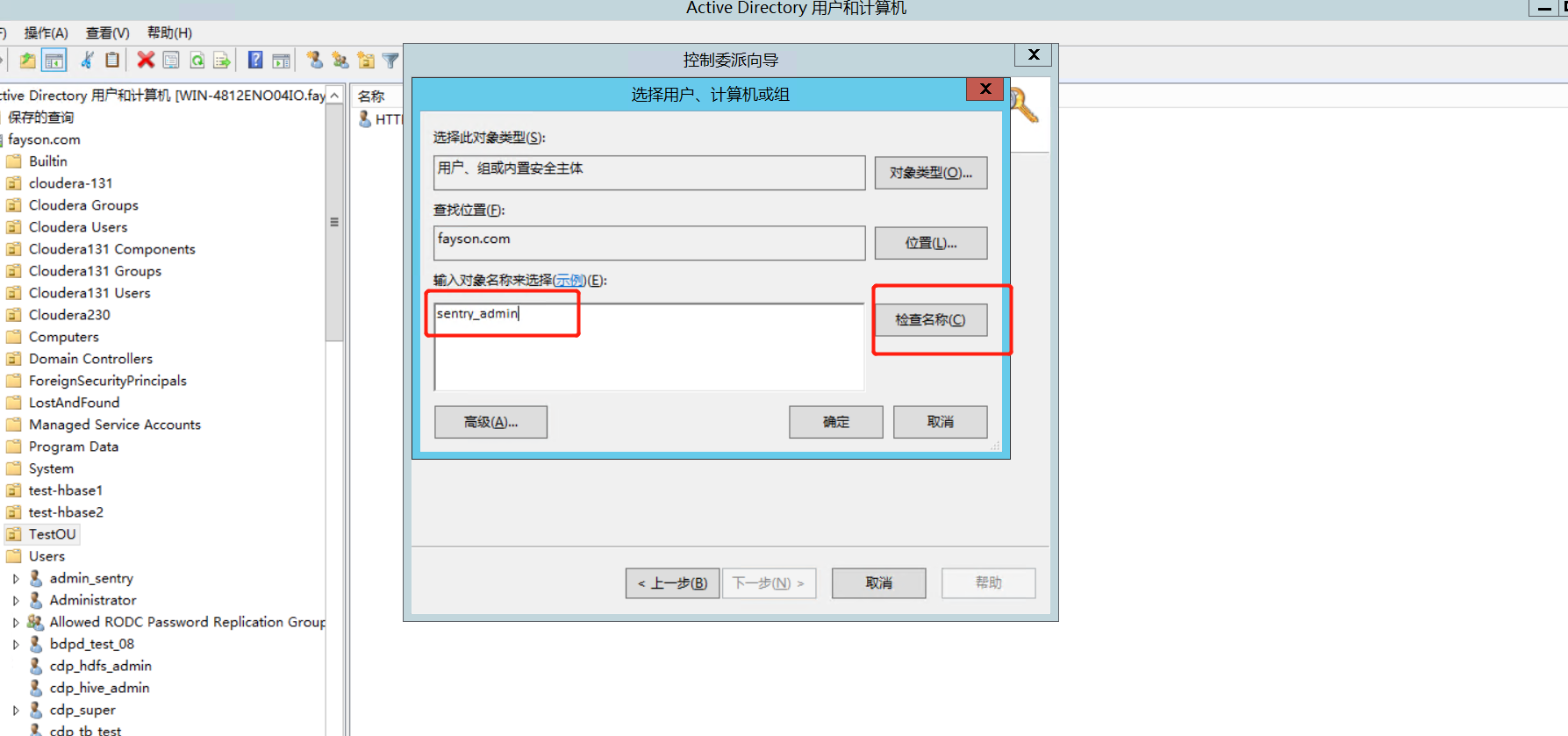
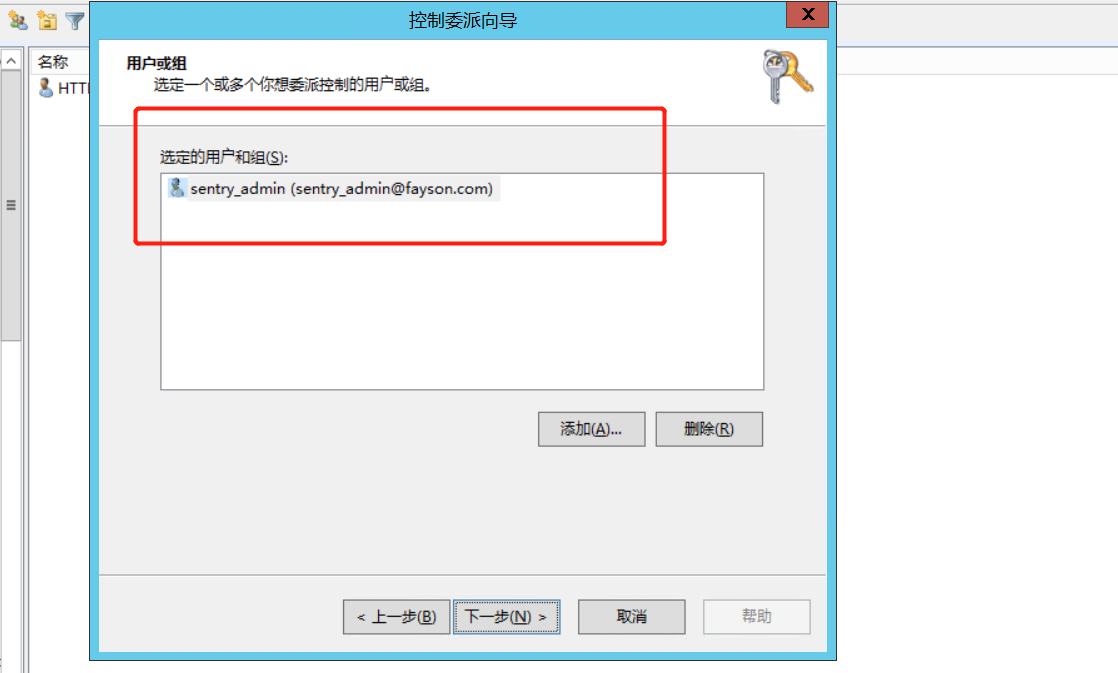
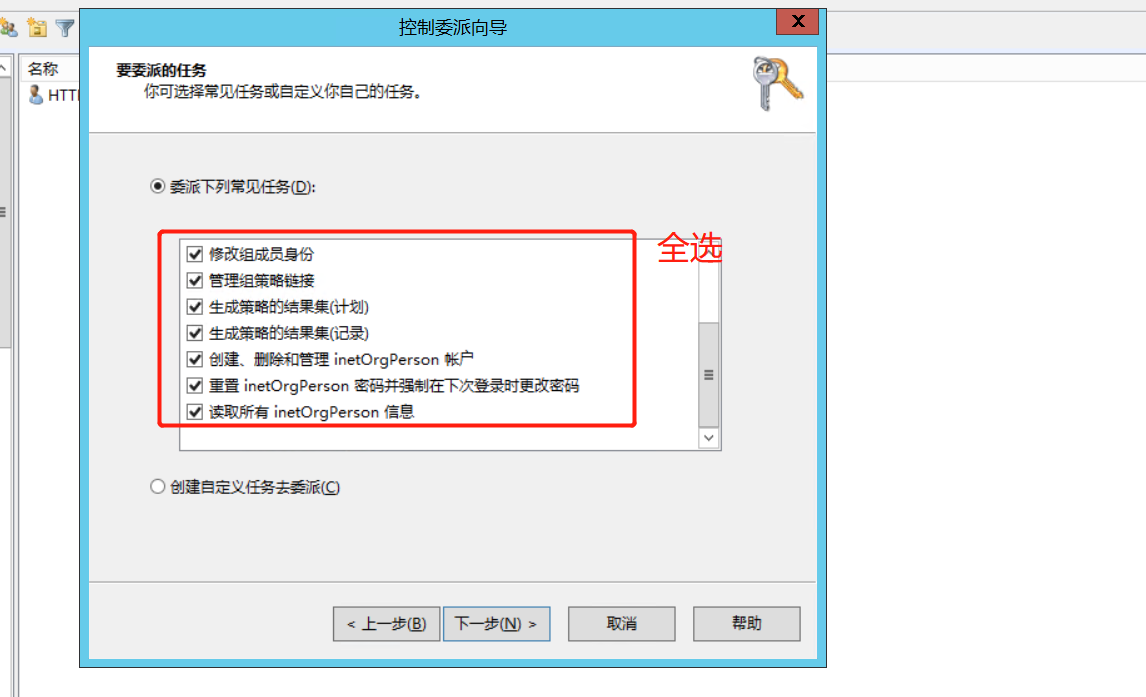
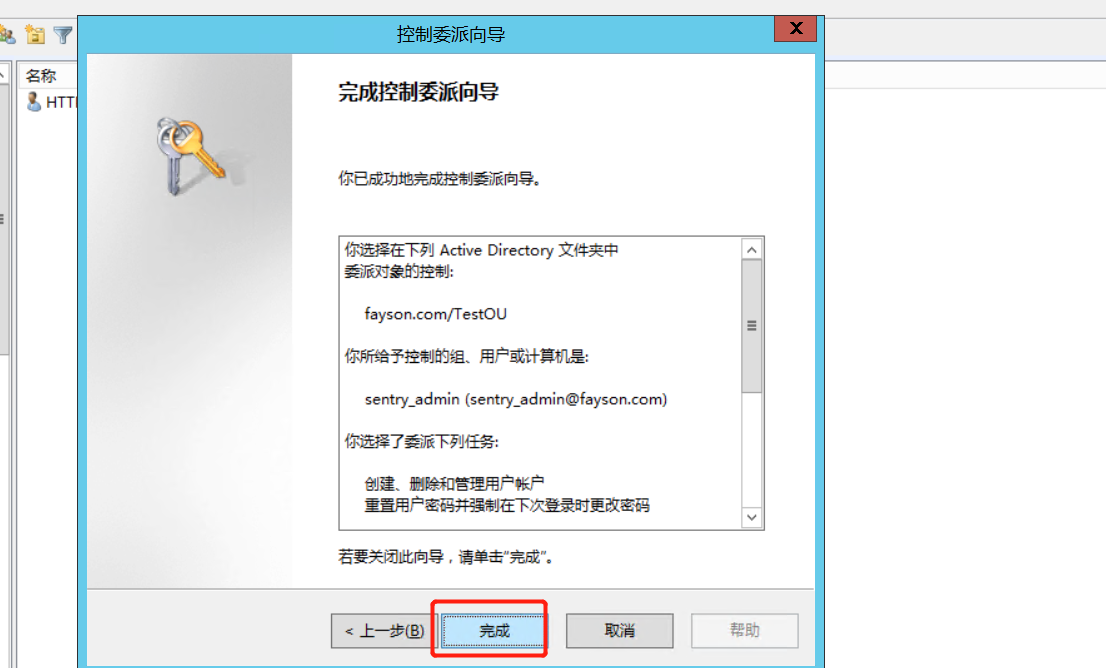
4、在AD中设置委派控制
5、在cm页面开启kerberos
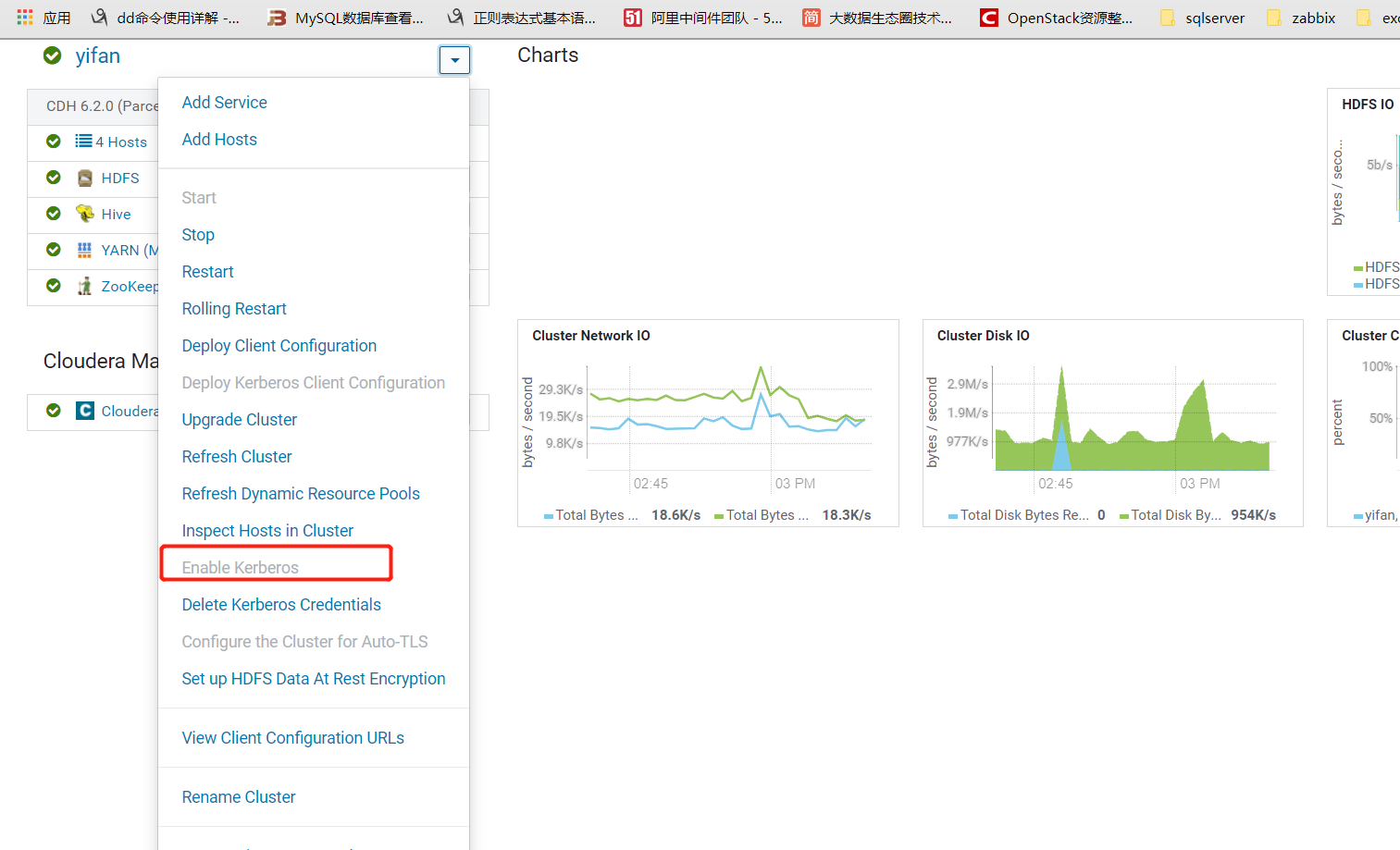
按照步骤一直下一步 。注意配置。
导入用户时使用上面委派控制的用户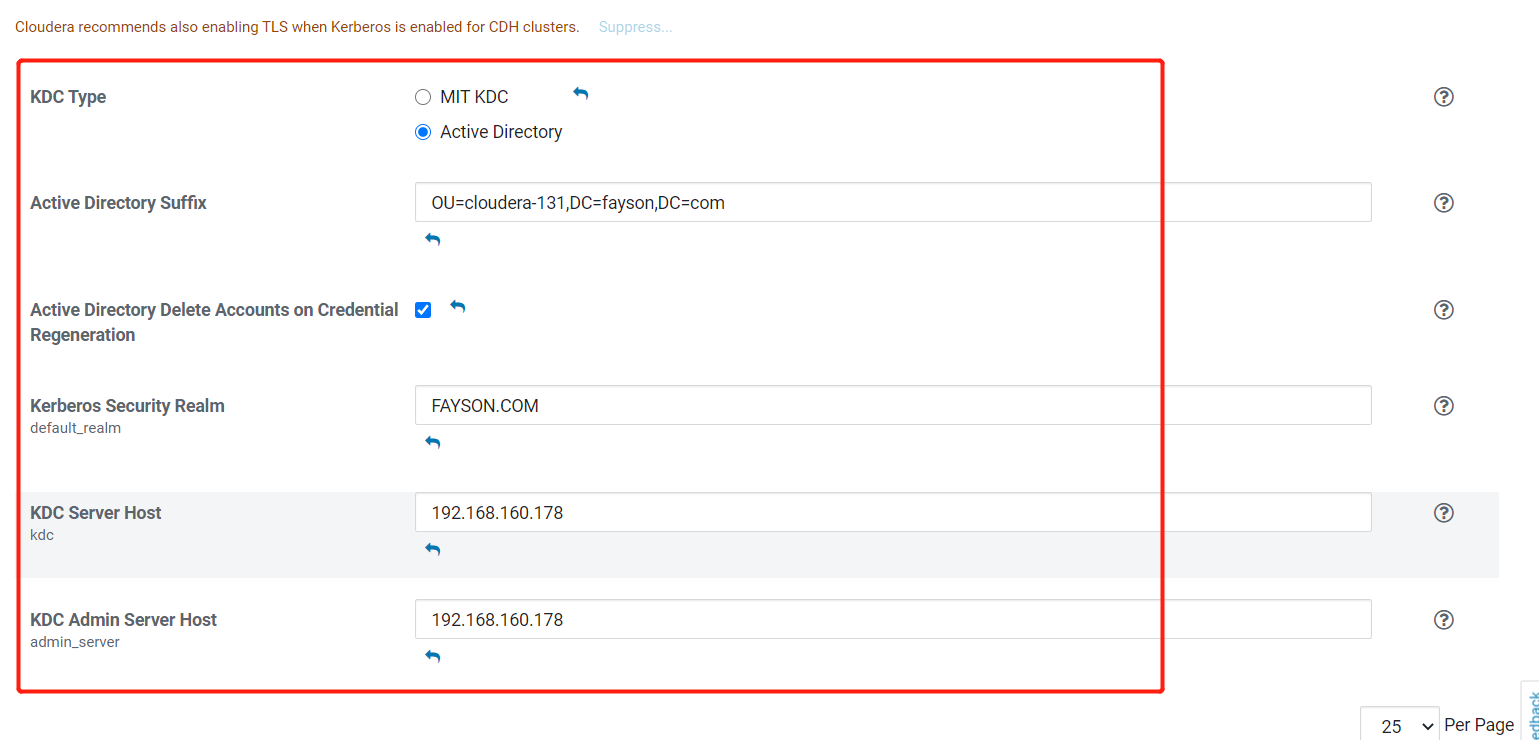
开启后会自动重启集群,重启成功后。开启成功