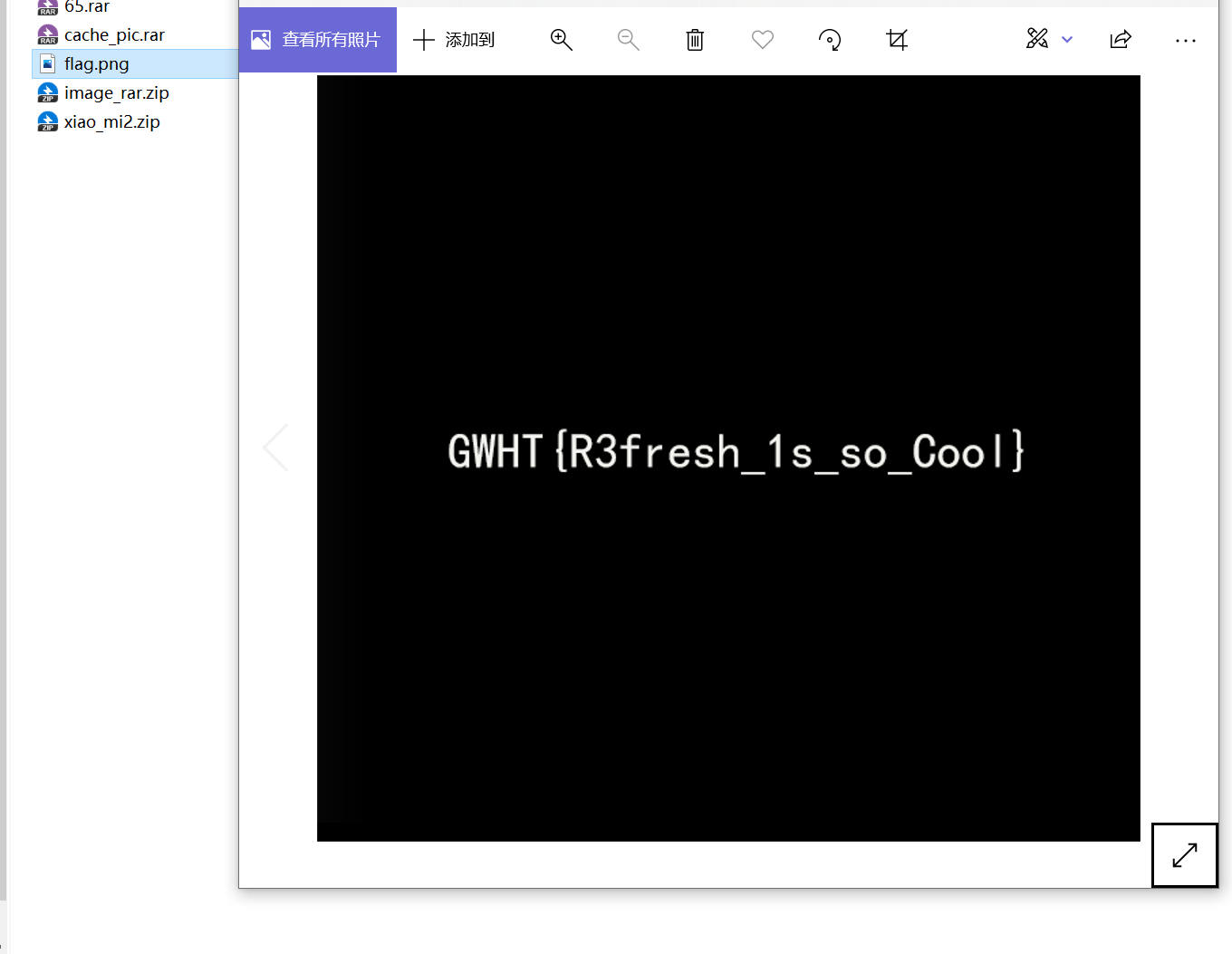
下载附件得到一个mp4,文件,打开发现:
看了一遍,发现没有什么异常。就拖进虚拟机先binwalk一下:
好像东西挺过,一直在跑,那就去010Editor中再看看: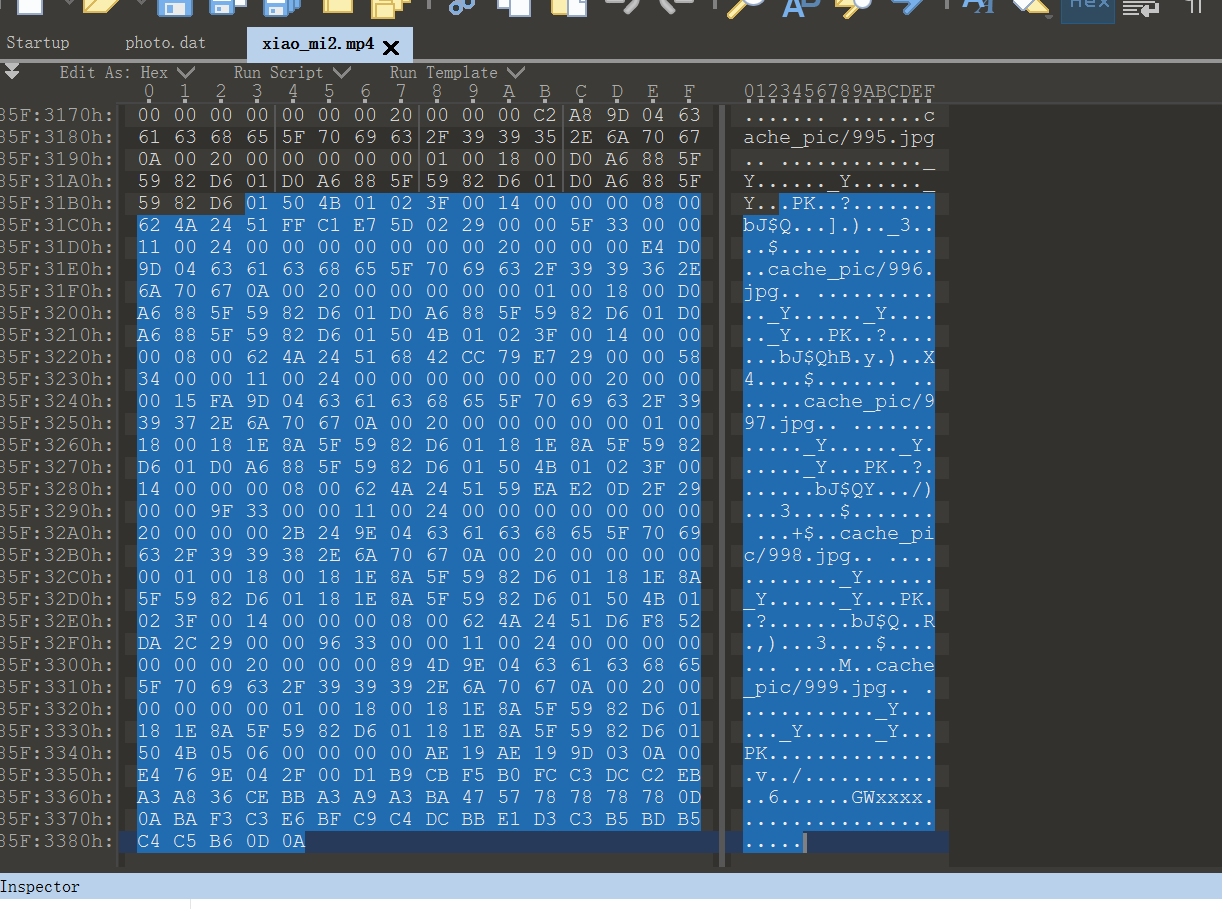
里面发现不少东西,尝试修改下文件后缀为zip.
解压出来6573个图片,虚拟机跑的看着和这差不多。
只不过还有原来的没解压缩的压缩包。
在这么多图片中发现一个异常的,在上图中也可以看到65.jpg,显然不是个图片。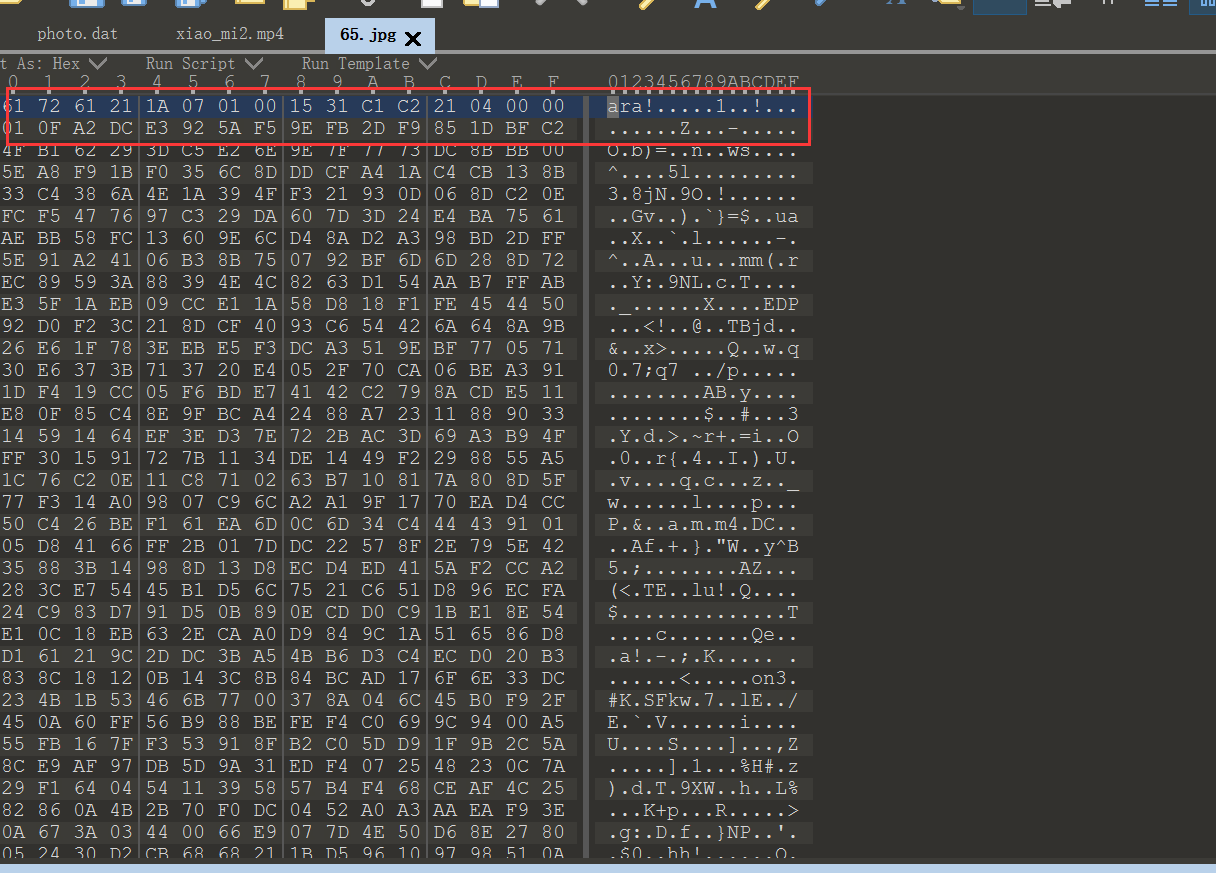
文件头被修改了,应该是rar。
正常的为: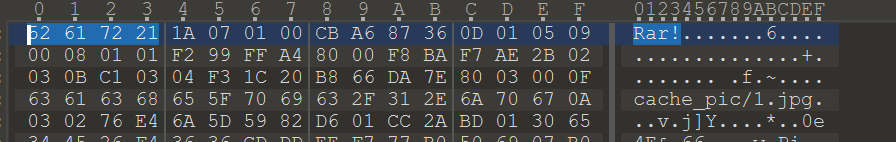
就0-3的部分修改下就行。
发现被加密了,试了试伪加密和简单的爆破发现没用。题目别的地方也没有发现压缩包密码的提示。
然后看师傅们的题解,说是有hint,应该是题目下放的hint.
##压缩包密码(6位):GWxxxx
##后面可能会用到的哦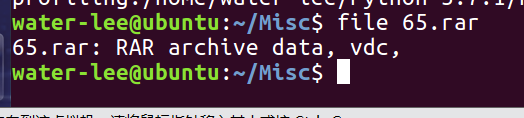 我file完文件没出现是RAR5.
我file完文件没出现是RAR5.
好像是ARCHPR无法爆破RAR5的密码。
这里用john下面的一个工具:rar2john
来提取hash。
rar2john 65.rar 65.rar:$rar5$16$a2dce3925af59efb2df9851dbfc24fb1$15$bb005ea8f91bf0356c8dddcfa41ac4cb$8$62293dc5e26e9e7f
开始安装好了,后来出了问题,这里后续补上图。
然后就是用hashcat爆破hash
D:\Tools\Misc\hashcat-6.2.2> .\hashcat.exe -m 13000 -a 3 '$rar5$16$a2dce3925af59efb2df9851dbfc24fb1$15$bb005ea8f91bf0356c8dddcfa41ac4cb$8$62293dc5e26e9e7f' GW?a?a?a?ahashcat (v6.2.2) starting...Successfully initialized NVIDIA CUDA library.Failed to initialize NVIDIA RTC library.* Device #1: CUDA SDK Toolkit not installed or incorrectly installed.CUDA SDK Toolkit required for proper device support and utilization.Falling back to OpenCL runtime.* Device #2: Unstable OpenCL driver detected!This OpenCL driver may fail kernel compilation or produce false negatives.You can use --force to override, but do not report related errors.nvmlDeviceGetFanSpeed(): Not SupportedOpenCL API (OpenCL 1.2 CUDA 11.1.114) - Platform #1 [NVIDIA Corporation]========================================================================* Device #1: GeForce GTX 1050, 3328/4096 MB (1024 MB allocatable), 5MCUOpenCL API (OpenCL 3.0 ) - Platform #2 [Intel(R) Corporation]=============================================================* Device #2: Intel(R) UHD Graphics 630, skippedMinimum password length supported by kernel: 0Maximum password length supported by kernel: 256Hashes: 1 digests; 1 unique digests, 1 unique saltsBitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotatesOptimizers applied:* Zero-Byte* Single-Hash* Single-Salt* Brute-Force* Slow-Hash-SIMD-LOOPWatchdog: Temperature abort trigger set to 90cHost memory required for this attack: 87 MB[s]tatus [p]ause [b]ypass [c]heckpoint [f]inish [q]uit =>Session..........: hashcatStatus...........: QuitHash.Name........: RAR5Hash.Target......: $rar5$16$a2dce3925af59efb2df9851dbfc24fb1$15$bb005e...6e9e7fTime.Started.....: Fri Jul 02 21:04:28 2021 (2 secs)Time.Estimated...: Fri Jul 02 23:44:57 2021 (2 hours, 40 mins)Kernel.Feature...: Pure KernelGuess.Mask.......: GW?a?a?a?a [6]Guess.Queue......: 1/1 (100.00%)Speed.#1.........: 8460 H/s (9.29ms) @ Accel:4 Loops:128 Thr:1024 Vec:1Recovered........: 0/1 (0.00%) DigestsProgress.........: 0/81450625 (0.00%)Rejected.........: 0/0 (0.00%)Restore.Point....: 0/81450625 (0.00%)Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:25472-25600Candidate.Engine.: Device GeneratorCandidates.#1....: GWEERA -> GW#ckeHardware.Mon.#1..: Temp: 60c Util: 99% Core:1683MHz Mem:3504MHz Bus:8
这里用到的参数:
-m指定爆破文档类型:
- [ Hash modes ] -# | Name | Category======+=====================================================+======================================13000 | RAR5 | Archives
-a指定爆破模式:
- [ Attack Modes ] -# | Mode===+======0 | Straight1 | Combination3 | Brute-force6 | Hybrid Wordlist + Mask7 | Hybrid Mask + Wordlist9 | Association
- GW?a?a?a?a,?a包含大小写字母、数字及特殊字符
最后爆破出来密码:GW5!3#
解压:
文件无后缀,加上得到: