1、基本概述
官方文档:https://docs.gitlab.com/ 官方下载:https://about.gitlab.com/install/#centos-7
1.1 发布流程
1.1.1 原始版本
早在 Long long ago(故事开始),写完后的代码经过测试环境测试后,接下来进入发布流程,通过FTP工具(文本传输协议软件)如:FileZilla ,上传到服务器通过肉眼比对文件是否修复,然后进行上传代码覆盖。
这种方式的问题我总结有下几点问题:
- 不支持回滚操作
- 代码发布期间会造成服务中断
因为以上问题的存在,又是单机服务,所以每次发版基本都得是尽可能在下班以后或半夜操作,又是人工上传完成代码的覆盖,每次都得小心翼翼,如果一旦新版代码存在严重问题更是头大,最早期14年在北京一家做电商的时候每周必干的事情。
1.1.2 传统应用
我将上面的做法称为原始方法(纯手工,肉眼比对),后面接触到的更高级一点的做法,是使用的版本控制软件(GIT/SVN),配置 Webhook 的方式,代码自动推到指定分支后将触发部署脚本,那个时候的 webhook 写的还比较Low(就是直接 pull 某个分支代码),大多数用在测试环境集成,生产环境还是手动拉代码,可以是指定分支,也可以是指定 Tag Release(手动发版)。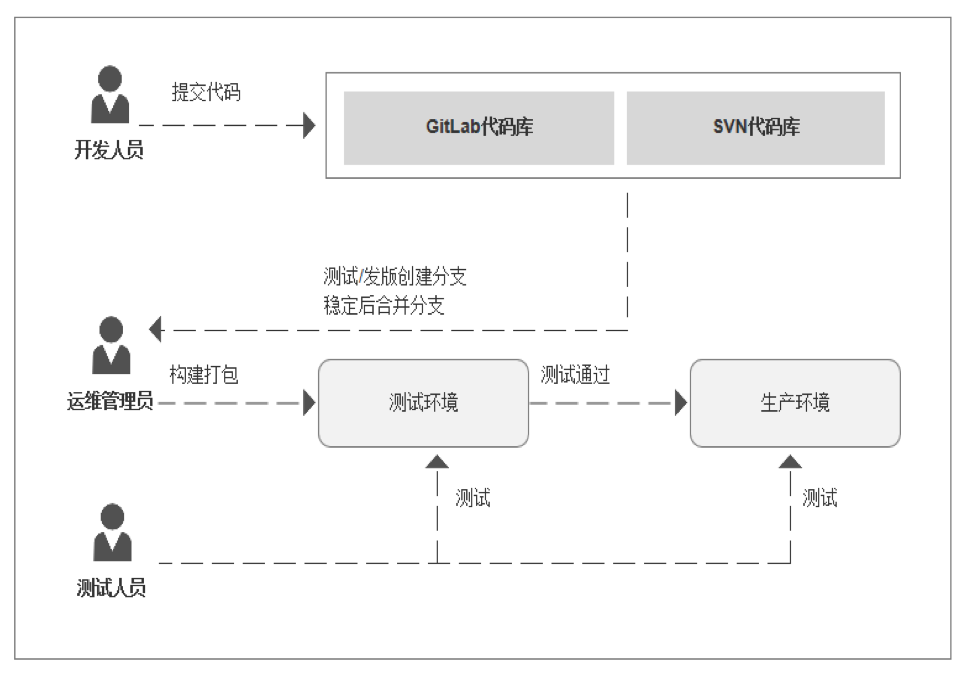
有些童鞋公司做法是直接拉最新 master 分支,不推荐这么做,原因是因为不方便后期出问题时回滚,为了解决这个问题打 release tag 是一种方案,也是我们之前的早期做法,以下是我司一个 laravel 项目,手工发版执行的部分示例命令如下:
# 本机打 Taggit tag -a v3.9.2 -m '版本描述'git push origin v3.9.2# 远端发版git fetch --tagsgit checkout -b v3.9.2 refs/tags/v3.9.2# 更新依赖(可选)composer update neox/lib neox/model --verbose -vvv --profile# 其他处理(可选)chmod -R storage/*key
注:还有使用 SVN 做代码管理,通过备注的特殊备注来自动触发,将代码发布测试或生产环境。
1.1.3 Gitlab CI/CD
1.2 DevOps 概念
DevOps :Development 和 Operations的组合词,是一种重视“软件开发人员(Dev)”和“IT运维技术人员(Ops)”之间沟通合作的文化、运动或惯例。通过自动化“软件交付”和“架构变更”的流程,来使得构建、测试、发布软件能够更加地快捷、频繁和可靠。
1.3 CI/CD
CI 持续集成(Continuous Integration):
解决:多位开发人员处理同一应用的不同功能时,可以帮助开发人员更加频繁的将代码合并到共享分支或“主干”中(自动构建应用时,通过会运行不同级别的自动化测试)
CD 持续交付(Continuous Delivery):
完成 CI 中构建以及单元测试和集成测试的自动化流程后,持续交付可自动将已验证的代码发布到存储库,在该流程结束时,运维团队可以快速、轻松的将应用部署到生产环境中
CD 持续部署(Continuous Integration ):
解决:可以自动将应用发布到生产环境
总而言之,CI/CD 是一种通过自动化来频繁向客户交付应用的方法, 其核心概念是持续集成、持续交付和持续部署,好处便是降低应用部署的风险。
1.4 Gitlab CI/CD 与 Jenkins 对比
Gitlab CI/CD
- 轻量级、配置简单,不需要复杂的安装
- 构建日志十分清晰,交互体验友好,gitlab 角色权限控制
- 配置依赖于项目代码仓库,根据 YAML 进行配置,没有统一的管理界面
Jenkins
- 构建服务与代码仓库分离,可以支持任意代码仓库
- 有统一管理界面,支持插件多、支持多语言(插件配置以及自身安装复杂)
- 体量大,不建议小团队使用
小结:
- Gitlab CI/CD 更适用于敏捷开发,开发与运维是同一(或一小组)人,最便捷的开发方式
- Jenkins 更适合在多角色团队,有单独运维团队,开发与运维两个部门,配置与代码分离,职责分明
1.5
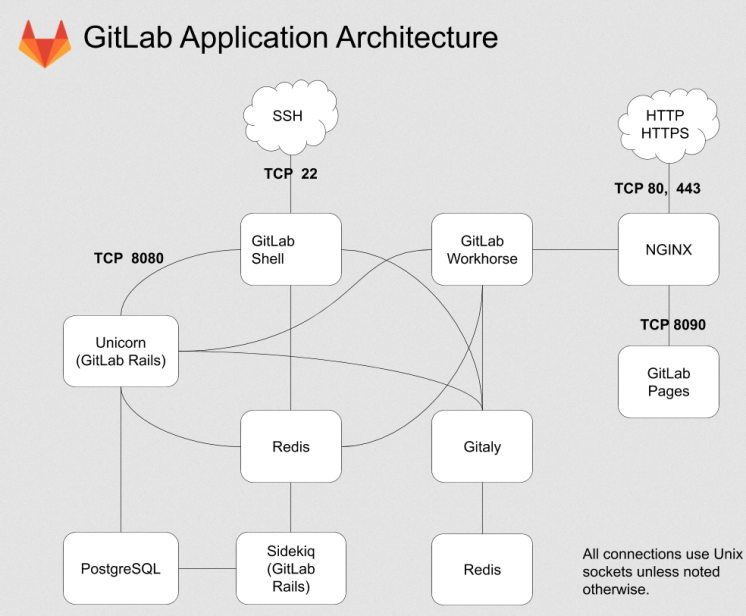
主要模块
- Unicorn: 是一个 Web Server,用于支持 GitLab 的主体 Web 应用;
- Sidekiq: 队列服务,需要 Redis 支持,用以支持 GitLab 的异步任务;
- GitLab Shell: Git SSH 的权限管理模块;
- Gitaly: Git RPC 服务,用于处理 GitLab 发出的 git 操作;
- GitLab Workhorse:基于 Go 语言,用于接替 Unicorn 处理比较大的 http 请求。
架构图:
对 GitLab 应用层的修改,主要关注的是 GitLab Rails 和 GitLab Shell 这两个子系统
流程图: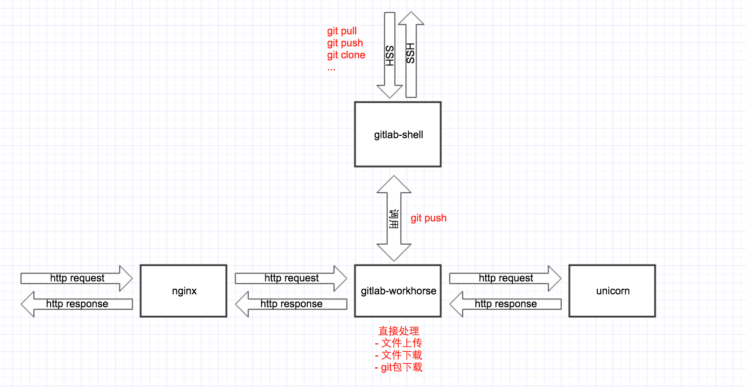
2、安装部署
2.1 云主机安装
以centos7为例:
# 安装依赖
yum install -y curl policycoreutils-python openssh-server perl postfix
# 启动ssh服务&设置为开机启动
systemctl start sshd && systemctl enable sshd
# ,postfix支持gitlab发信功能
systemctl enable postfix && systemctl start postfix
# 如果必须使用firewalld, 则开启http访问即可
firewall-cmd --permanent --add-service=http
firewall-cmd --permanent --add-service=https
systemctl reload firewalld
# 在线下载安装包:
wget https://mirrors.tuna.tsinghua.edu.cn/gitlab-ce/yum/el6/gitlab-ce-12.4.2-ce.0.el6.x 86_64.rpm
wget http://mirrors.jenkins-ci.org/redhat/jenkins-2.276-1.1.noarch.rpm
# 安装: rpm -i gitlab-ce-12.4.2-ce.0.el6.x86_64.rpm
#### 修改gitlab配置
vim /etc/gitlab/gitlab.rb
# 修改gitlab访问地址和端口,默认为80,我们改为880
external_url 'http://i8023.icu:880'
nginx['listen_port'] = 880
#### 重新启动, 默认是root用户
gitlab-ctl reconfigure
gitlab-ctl restart
2.2 docker安装
2.2.1 设置卷位置
配置一个新的环境变量$GITLAB_HOME,该变量指向配置,日志和数据文件将驻留的目录。确保该目录存在,并且已授予适当的权限。
export GITLAB_HOME=/srv/gitlab
| 本地目录 | 容器目录 | 用法 |
|---|---|---|
| $GITLAB_HOME/data | /var/opt/gitlab | 用于存储应用程序数据 |
| $GITLAB_HOME/logs | /var/log/gitlab | 用于存储日志 |
| $GITLAB_HOME/config | /etc/gitlab | 用于存储GitLab配置文件 |
2.2.2 docker 引擎安装
下载并启动一个GitLab容器,并发布访问SSH,HTTP和HTTPS所需的端口。所有的GitLab数据都将存储为的子目录$GITLAB_HOME。restart系统重启后,容器将自动运行
sudo docker run --detach \
--hostname gitlab.example.com \
--publish 443:443 --publish 80:80 --publish 22:22 \
--name gitlab \
--restart always \
--volume $GITLAB_HOME/config:/etc/gitlab \
--volume $GITLAB_HOME/logs:/var/log/gitlab \
--volume $GITLAB_HOME/data:/var/opt/gitlab \
gitlab/gitlab-ce:latest
使用的是SELinux,需要确保Docker进程具有足够的权限以在已安装的卷中创建配置文件。
sudo docker run --detach \
--hostname gitlab.example.com \
--publish 443:443 --publish 80:80 --publish 22:22 \
--name gitlab \
--restart always \
--volume $GITLAB_HOME/config:/etc/gitlab:Z \
--volume $GITLAB_HOME/logs:/var/log/gitlab:Z \
--volume $GITLAB_HOME/data:/var/opt/gitlab:Z \
gitlab/gitlab-ce:latest
初始化过程可能需要很长时间。您可以使用以下方法跟踪此过程:
sudo docker logs -f gitlab
启动容器时设置外部URL并启用LFS的示例:
sudo docker run --detach \
--hostname gitlab.example.com \
--env GITLAB_OMNIBUS_CONFIG="external_url 'http://my.domain.com/'; gitlab_rails['lfs_enabled'] = true;" \
--publish 443:443 --publish 80:80 --publish 22:22 \
--name gitlab \
--restart always \
--volume $GITLAB_HOME/config:/etc/gitlab \
--volume $GITLAB_HOME/logs:/var/log/gitlab \
--volume $GITLAB_HOME/data:/var/opt/gitlab \
gitlab/gitlab-ce:latest
在公共IP地址上运行GitLab
sudo docker run --detach \
--hostname gitlab.example.com \
--publish 198.51.100.1:443:443 \
--publish 198.51.100.1:80:80 \
--publish 198.51.100.1:22:22 \
--name gitlab \
--restart always \
--volume $GITLAB_HOME/config:/etc/gitlab \
--volume $GITLAB_HOME/logs:/var/log/gitlab \
--volume $GITLAB_HOME/data:/var/opt/gitlab \
gitlab/gitlab-ce:latest
2.2.3 Docker Compose安装GitLab
- 安装Docker Compose。
创建一个docker-compose.yml文件(或下载一个示例):
web: image: 'gitlab/gitlab-ce:latest' restart: always hostname: 'gitlab.example.com' environment: GITLAB_OMNIBUS_CONFIG: | external_url 'https://gitlab.example.com' # Add any other gitlab.rb configuration here, each on its own line ports: - '80:80' - '443:443' - '22:22' volumes: - '$GITLAB_HOME/config:/etc/gitlab' - '$GITLAB_HOME/logs:/var/log/gitlab' - '$GITLAB_HOME/data:/var/opt/gitlab'确保您与以下目录位于同一目录中,docker-compose.yml然后启动GitLab:
docker-compose up -d2.3 k8s 安装
2.3.1 helm 部署
2.3.2 yaml 部署
适合单机节点,如集群化可修改挂在卷为pvc方式
https://github.com/zeyangli/devops-on-k8s/blob/master/devops/gitlab.yaml
---
kind: Deployment
apiVersion: apps/v1
metadata:
labels:
k8s-app: gitlab
name: gitlab
namespace: devops
spec:
replicas: 1
revisionHistoryLimit: 10
selector:
matchLabels:
k8s-app: gitlab
template:
metadata:
labels:
k8s-app: gitlab
namespace: devops
name: gitlab
spec:
containers:
- name: gitlab
image: gitlab/gitlab-ce:12.9.0-ce.0
imagePullPolicy: IfNotPresent
ports:
- containerPort: 30088
name: web
protocol: TCP
- containerPort: 22
name: agent
protocol: TCP
resources:
limits:
cpu: 2000m
memory: 8Gi
requests:
cpu: 500m
memory: 512Mi
livenessProbe:
httpGet:
path: /users/sign_in
port: 30088
initialDelaySeconds: 60
timeoutSeconds: 5
failureThreshold: 12
readinessProbe:
httpGet:
path: /users/sign_in
port: 30088
initialDelaySeconds: 60
timeoutSeconds: 5
failureThreshold: 12
volumeMounts:
- name: gitlab-conf
mountPath: /etc/gitlab
- name: gitlab-log
mountPath: /var/log/gitlab
- name: gitlab-data
mountPath: /var/opt/gitlab
env:
- name: gitlab_HOME
value: /var/lib/gitlab
volumes:
- name: gitlab-conf
hostPath:
path: /data/devops/gitlab/config
type: Directory
- name: gitlab-log
hostPath:
path: /data/devops/gitlab/logs
type: Directory
- name: gitlab-data
hostPath:
path: /data/devops/gitlab/data
type: Directory
serviceAccountName: gitlab
---
apiVersion: v1
kind: ServiceAccount
metadata:
labels:
k8s-app: gitlab
name: gitlab
namespace: devops
---
kind: Service
apiVersion: v1
metadata:
labels:
k8s-app: gitlab
name: gitlab
namespace: devops
spec:
type: NodePort
ports:
- name: web
port: 30088
targetPort: 30088
nodePort: 30088
- name: slave
port: 22
targetPort: 22
nodePort: 30022
selector:
k8s-app: gitlab
---
kind: Role
apiVersion: rbac.authorization.k8s.io/v1beta1
metadata:
name: gitlab
namespace: devops
rules:
- apiGroups: [""]
resources: ["pods"]
verbs: ["create","delete","get","list","patch","update","watch"]
- apiGroups: [""]
resources: ["pods/exec"]
verbs: ["create","delete","get","list","patch","update","watch"]
- apiGroups: [""]
resources: ["pods/log"]
verbs: ["get","list","watch"]
- apiGroups: [""]
resources: ["secrets"]
verbs: ["get"]
---
apiVersion: rbac.authorization.k8s.io/v1beta1
kind: RoleBinding
metadata:
name: gitlab
namespace: devops
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: gitlab
subjects:
- kind: ServiceAccount
name: gitlab
namespace: devops
3、相关配置
3.1 汉化
yum install -y git
git clone https://gitlab.com/xhang/gitlab.git
/usr/bin/cp -r ./gitlab/* /opt/gitlab/embedded/service/gitlab-rails/
gitlab-ctl reconfigure
gitlab-ctl status
gitlab-ctl stop
gitlab-ctl start
3.2 邮件
grep '^[a-Z]' /etc/gitlab/gitlab.rb
#gitlab访问url
external_url 'http://git.bgx.com'
## Email Settings
gitlab_rails['gitlab_email_enabled'] = true
# 启动smtp
gitlab_rails['smtp_enable'] = true
gitlab_rails['smtp_address'] = "smtp.163.com"
gitlab_rails['smtp_port'] = 465
# 发件人邮箱
gitlab_rails['gitlab_email_from'] = "zzrfhc@163.com"
# 发件人显示名称
gitlab_rails['gitlab_email_display_name'] = 'zzrfhc'
# 163邮箱账户
gitlab_rails['smtp_user_name'] = "zzrfhc@163.com"
# 163邮箱密码(安全密码)
gitlab_rails['smtp_password'] = "rqoewdfrxnexbcjg"
gitlab_rails['smtp_domain'] = "smtp.163.com"
gitlab_rails['smtp_authentication'] = :plain
gitlab_rails['smtp_enable_starttls_auto'] = true
3.3 备份
使用如下命令会在/var/opt/gitlab/backups目录下创建一个名称类似为1481598919_gitlab_backup.tar的压缩包
这个压缩包就是Gitlab整个的完整部分, 其中开头的1481598919是备份创建的日期
- /etc/gitlab/gitlab.rb 配置文件须备份
- /var/opt/gitlab/nginx/conf nginx配置文件
- /etc/postfix/main.cfpostfix 邮件配置备份
备份目录gitlab-rake gitlab:backup:create
修改默认存放备份站点目录,然后进行重新加载配置文件[root@gitlab-ce ~]# vim /etc/gitlab/gitlab.rb ... gitlab_rails['backup_path'] = "/data/gitlab/backups" ... [root@gitlab-ce ~]# gitlab-ctl reconfigure4、gitlab runner
4.1 概述
在 GitLab CI / CD 中,运行程序运行.gitlab-ci.yml定义的代码.
GitLab Runner 是一种轻量级,高度可扩展的代理,它通过 GitLab CI / CD 的协调器 API 提取 CI 作业,运行该作业,并将结果发送回 GitLab 实例.
GitLab-CI 就是一套配合GitLab使用的持续集成系统,GitLab-Runner是配合GitLab-CI进行使用的。
一般地,GitLab里面的每一个工程都会定义一个属于这个工程的软件集成脚本,用来自动化地完成一些软件集成工作。当这个工程的仓库代码发生变动时,比如有人push了代码,GitLab就会将这个变动通知GitLab-CI。这时GitLab-CI会找出与这个工程相关联的Runner,并通知这些Runner把代码更新到本地并执行预定义好的执行脚本。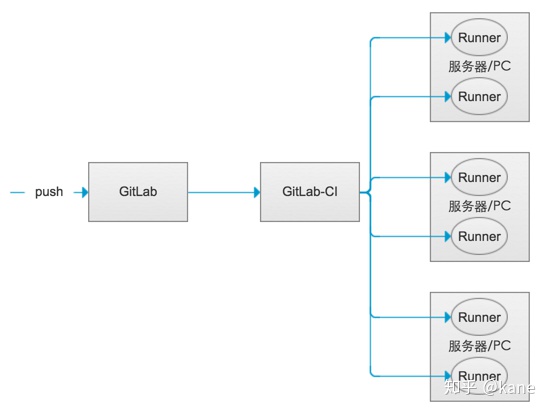
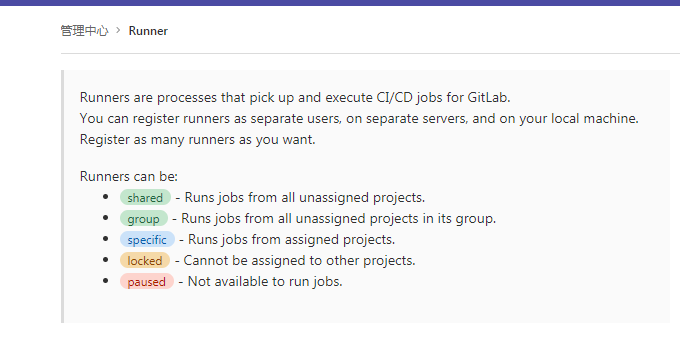
4.2 类型
- shared 共享 -Runner运行所有未分配项目中的作业
- group 组 -Runner运行其组中所有未分配项目的作业
- specific 具体 -Runner运行分配的项目中的作业
- locked 已锁定 -无法将跑步者分配给其他项目
- paused 已暂停 -跑步者将不会获得任何新工作
4.3 安装 runner
4.3.1 k8s 安装
Kubernetes集群中的官方方法是使用 gitlab-runner Helm图表。
# 添加GitLab Helm存储库
helm repo add gitlab https://charts.gitlab.io
helm install --namespace <NAMESPACE> gitlab-runner -f <CONFIG_VALUES_FILE> gitlab/gitlab-runner
helm search repo gitlab-runner
helm pull gitlab/gitlab-runner
tar -xf gitlab-runner-0.28.0.tgz
# 修改对应的yaml
vim gitlab-runner/values.yaml
# 渲染模板,查看修改是否存在问题
helm template --dry-run gitlab-runner gitlab-runner/ -n devops
# 安装
helm install gitlab-runner gitlab-runner/ -n devops
渲染后的配置信息如下:
---
# Source: gitlab-runner/templates/service-account.yaml
apiVersion: v1
kind: ServiceAccount
metadata:
annotations:
name: gitlab-runner-gitlab-runner
labels:
app: gitlab-runner-gitlab-runner
chart: gitlab-runner-0.28.0
release: "gitlab-runner"
heritage: "Helm"
---
# Source: gitlab-runner/templates/secrets.yaml
apiVersion: v1
kind: Secret
metadata:
name: "gitlab-runner-gitlab-runner"
labels:
app: gitlab-runner-gitlab-runner
chart: gitlab-runner-0.28.0
release: "gitlab-runner"
heritage: "Helm"
type: Opaque
data:
runner-registration-token: "cnptQ0VHS1pIYjJaRVVlMnl4TGY="
runner-token: ""
---
# Source: gitlab-runner/templates/configmap.yaml
apiVersion: v1
kind: ConfigMap
metadata:
name: gitlab-runner-gitlab-runner
labels:
app: gitlab-runner-gitlab-runner
chart: gitlab-runner-0.28.0
release: "gitlab-runner"
heritage: "Helm"
data:
entrypoint: |
#!/bin/bash
set -e
mkdir -p /home/gitlab-runner/.gitlab-runner/
cp /configmaps/config.toml /home/gitlab-runner/.gitlab-runner/
# Set up environment variables for cache
if [[ -f /secrets/accesskey && -f /secrets/secretkey ]]; then
export CACHE_S3_ACCESS_KEY=$(cat /secrets/accesskey)
export CACHE_S3_SECRET_KEY=$(cat /secrets/secretkey)
fi
if [[ -f /secrets/gcs-applicaton-credentials-file ]]; then
export GOOGLE_APPLICATION_CREDENTIALS="/secrets/gcs-applicaton-credentials-file"
elif [[ -f /secrets/gcs-application-credentials-file ]]; then
export GOOGLE_APPLICATION_CREDENTIALS="/secrets/gcs-application-credentials-file"
else
if [[ -f /secrets/gcs-access-id && -f /secrets/gcs-private-key ]]; then
export CACHE_GCS_ACCESS_ID=$(cat /secrets/gcs-access-id)
# echo -e used to make private key multiline (in google json auth key private key is oneline with \n)
export CACHE_GCS_PRIVATE_KEY=$(echo -e $(cat /secrets/gcs-private-key))
fi
fi
if [[ -f /secrets/azure-account-name && -f /secrets/azure-account-key ]]; then
export CACHE_AZURE_ACCOUNT_NAME=$(cat /secrets/azure-account-name)
export CACHE_AZURE_ACCOUNT_KEY=$(cat /secrets/azure-account-key)
fi
if [[ -f /secrets/runner-registration-token ]]; then
export REGISTRATION_TOKEN=$(cat /secrets/runner-registration-token)
fi
if [[ -f /secrets/runner-token ]]; then
export CI_SERVER_TOKEN=$(cat /secrets/runner-token)
fi
# Register the runner
if ! sh /configmaps/register-the-runner; then
exit 1
fi
# Run pre-entrypoint-script
if ! bash /configmaps/pre-entrypoint-script; then
exit 1
fi
# Start the runner
exec /entrypoint run --user=gitlab-runner \
--working-directory=/home/gitlab-runner
config.toml: |
concurrent = 10
check_interval = 30
log_level = "info"
listen_address = ':9252'
config.template.toml: |
[[runners]]
[runners.kubernetes]
image = "ubuntu:16.04"
configure: |
set -e
cp /init-secrets/* /secrets
register-the-runner: |
#!/bin/bash
MAX_REGISTER_ATTEMPTS=30
for i in $(seq 1 "${MAX_REGISTER_ATTEMPTS}"); do
echo "Registration attempt ${i} of ${MAX_REGISTER_ATTEMPTS}"
/entrypoint register \
--name="k8s-runner"\
--template-config /configmaps/config.template.toml \
--non-interactive
retval=$?
if [ ${retval} = 0 ]; then
break
elif [ ${i} = ${MAX_REGISTER_ATTEMPTS} ]; then
exit 1
fi
sleep 5
done
exit 0
check-live: |
#!/bin/bash
if /usr/bin/pgrep -f .*register-the-runner; then
exit 0
elif /usr/bin/pgrep gitlab.*runner; then
exit 0
else
exit 1
fi
pre-entrypoint-script: |
---
# Source: gitlab-runner/templates/role.yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: "Role"
metadata:
name: gitlab-runner-gitlab-runner
labels:
app: gitlab-runner-gitlab-runner
chart: gitlab-runner-0.28.0
release: "gitlab-runner"
heritage: "Helm"
namespace: "devops"
rules:
- apiGroups: [""]
resources: ["pods","pods/exec","secrets"]
verbs: ["get","list","watch","create","patch","delete"]
---
# Source: gitlab-runner/templates/role-binding.yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: "RoleBinding"
metadata:
name: gitlab-runner-gitlab-runner
labels:
app: gitlab-runner-gitlab-runner
chart: gitlab-runner-0.28.0
release: "gitlab-runner"
heritage: "Helm"
namespace: "devops"
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: "Role"
name: gitlab-runner-gitlab-runner
subjects:
- kind: ServiceAccount
name: gitlab-runner-gitlab-runner
namespace: "devops"
---
# Source: gitlab-runner/templates/deployment.yaml
apiVersion: apps/v1
kind: Deployment
metadata:
name: gitlab-runner-gitlab-runner
labels:
app: gitlab-runner-gitlab-runner
chart: gitlab-runner-0.28.0
release: "gitlab-runner"
heritage: "Helm"
spec:
replicas: 2
selector:
matchLabels:
app: gitlab-runner-gitlab-runner
template:
metadata:
labels:
app: gitlab-runner-gitlab-runner
chart: gitlab-runner-0.28.0
release: "gitlab-runner"
heritage: "Helm"
annotations:
checksum/configmap: a625bb61644e63277cc64a77700ee02512cadf0c4b8a83285b7696afc1014e39
checksum/secrets: de450275f834115986335a1244d26c4d7470e3023e9b29b59ed9aba94cfeefab
prometheus.io/scrape: 'true'
prometheus.io/port: '9252'
spec:
securityContext:
runAsUser: 100
fsGroup: 65533
terminationGracePeriodSeconds: 3600
initContainers:
- name: configure
command: ['sh', '/configmaps/configure']
image: gitlab/gitlab-runner:alpine-v13.11.0
imagePullPolicy: "IfNotPresent"
securityContext:
allowPrivilegeEscalation: false
env:
- name: CI_SERVER_URL
value: "http://i8023.icu/"
- name: CLONE_URL
value: ""
- name: RUNNER_REQUEST_CONCURRENCY
value: "1"
- name: RUNNER_EXECUTOR
value: "kubernetes"
- name: REGISTER_LOCKED
value: "false"
- name: RUNNER_TAG_LIST
value: "k8s-runner"
- name: KUBERNETES_IMAGE
value:
- name: KUBERNETES_PRIVILEGED
value: "true"
- name: KUBERNETES_NAMESPACE
value: "devops"
- name: KUBERNETES_CPU_LIMIT
value: "200m"
- name: KUBERNETES_CPU_LIMIT_OVERWRITE_MAX_ALLOWED
value: "400m"
- name: KUBERNETES_MEMORY_LIMIT
value: "256Mi"
- name: KUBERNETES_MEMORY_LIMIT_OVERWRITE_MAX_ALLOWED
value: "512Mi"
- name: KUBERNETES_CPU_REQUEST
value: "100m"
- name: KUBERNETES_CPU_REQUEST_OVERWRITE_MAX_ALLOWED
value: "200m"
- name: KUBERNETES_MEMORY_REQUEST
value: "128Mi"
- name: KUBERNETES_MEMORY_REQUEST_OVERWRITE_MAX_ALLOWED
value: "256Mi"
- name: KUBERNETES_SERVICE_ACCOUNT
value: ""
- name: KUBERNETES_SERVICE_CPU_LIMIT
value: "200m"
- name: KUBERNETES_SERVICE_MEMORY_LIMIT
value: "256Mi"
- name: KUBERNETES_SERVICE_CPU_REQUEST
value: "100m"
- name: KUBERNETES_SERVICE_MEMORY_REQUEST
value: "128Mi"
- name: KUBERNETES_HELPER_CPU_LIMIT
value: "200m"
- name: KUBERNETES_HELPER_MEMORY_LIMIT
value: "256Mi"
- name: KUBERNETES_HELPER_CPU_REQUEST
value: "100m"
- name: KUBERNETES_HELPER_MEMORY_REQUEST
value: "128Mi"
- name: KUBERNETES_HELPER_IMAGE
value: "gitlab/gitlab-runner-helper:x86_64-${CI_RUNNER_REVISION}"
- name: KUBERNETES_PULL_POLICY
value: "if-not-present"
volumeMounts:
- name: runner-secrets
mountPath: /secrets
readOnly: false
- name: configmaps
mountPath: /configmaps
readOnly: true
- name: init-runner-secrets
mountPath: /init-secrets
readOnly: true
resources:
limits:
cpu: 200m
memory: 256Mi
requests:
cpu: 100m
memory: 128Mi
serviceAccountName: gitlab-runner-gitlab-runner
containers:
- name: gitlab-runner-gitlab-runner
image: gitlab/gitlab-runner:alpine-v13.11.0
imagePullPolicy: "IfNotPresent"
securityContext:
allowPrivilegeEscalation: false
lifecycle:
preStop:
exec:
command: ["/entrypoint", "unregister", "--all-runners"]
command: ["/bin/bash", "/configmaps/entrypoint"]
env:
- name: CI_SERVER_URL
value: "http://i8023.icu/"
- name: CLONE_URL
value: ""
- name: RUNNER_REQUEST_CONCURRENCY
value: "1"
- name: RUNNER_EXECUTOR
value: "kubernetes"
- name: REGISTER_LOCKED
value: "false"
- name: RUNNER_TAG_LIST
value: "k8s-runner"
- name: KUBERNETES_IMAGE
value:
- name: KUBERNETES_PRIVILEGED
value: "true"
- name: KUBERNETES_NAMESPACE
value: "devops"
- name: KUBERNETES_CPU_LIMIT
value: "200m"
- name: KUBERNETES_CPU_LIMIT_OVERWRITE_MAX_ALLOWED
value: "400m"
- name: KUBERNETES_MEMORY_LIMIT
value: "256Mi"
- name: KUBERNETES_MEMORY_LIMIT_OVERWRITE_MAX_ALLOWED
value: "512Mi"
- name: KUBERNETES_CPU_REQUEST
value: "100m"
- name: KUBERNETES_CPU_REQUEST_OVERWRITE_MAX_ALLOWED
value: "200m"
- name: KUBERNETES_MEMORY_REQUEST
value: "128Mi"
- name: KUBERNETES_MEMORY_REQUEST_OVERWRITE_MAX_ALLOWED
value: "256Mi"
- name: KUBERNETES_SERVICE_ACCOUNT
value: ""
- name: KUBERNETES_SERVICE_CPU_LIMIT
value: "200m"
- name: KUBERNETES_SERVICE_MEMORY_LIMIT
value: "256Mi"
- name: KUBERNETES_SERVICE_CPU_REQUEST
value: "100m"
- name: KUBERNETES_SERVICE_MEMORY_REQUEST
value: "128Mi"
- name: KUBERNETES_HELPER_CPU_LIMIT
value: "200m"
- name: KUBERNETES_HELPER_MEMORY_LIMIT
value: "256Mi"
- name: KUBERNETES_HELPER_CPU_REQUEST
value: "100m"
- name: KUBERNETES_HELPER_MEMORY_REQUEST
value: "128Mi"
- name: KUBERNETES_HELPER_IMAGE
value: "gitlab/gitlab-runner-helper:x86_64-${CI_RUNNER_REVISION}"
- name: KUBERNETES_PULL_POLICY
value: "if-not-present"
livenessProbe:
exec:
command: ["/bin/bash", "/configmaps/check-live"]
initialDelaySeconds: 60
timeoutSeconds: 1
periodSeconds: 10
successThreshold: 1
failureThreshold: 3
readinessProbe:
exec:
command: ["/usr/bin/pgrep","gitlab.*runner"]
initialDelaySeconds: 10
timeoutSeconds: 1
periodSeconds: 10
successThreshold: 1
failureThreshold: 3
ports:
- name: metrics
containerPort: 9252
volumeMounts:
- name: runner-secrets
mountPath: /secrets
- name: etc-gitlab-runner
mountPath: /home/gitlab-runner/.gitlab-runner
- name: configmaps
mountPath: /configmaps
resources:
limits:
cpu: 200m
memory: 256Mi
requests:
cpu: 100m
memory: 128Mi
volumes:
- name: runner-secrets
emptyDir:
medium: "Memory"
- name: etc-gitlab-runner
emptyDir:
medium: "Memory"
- name: init-runner-secrets
projected:
sources:
- secret:
name: "gitlab-runner-gitlab-runner"
items:
- key: runner-registration-token
path: runner-registration-token
- key: runner-token
path: runner-token
- name: configmaps
configMap:
name: gitlab-runner-gitlab-runner
hostAliases:
- hostnames:
- hw10
ip: 192.168.0.10
- hostnames:
- hw11
ip: 192.168.0.11
- hostnames:
- hw12
ip: 192.168.0.12
4.3.2 官方安装
使用GItLab官方仓库安装
1. 添加官方仓库
# For Debian/Ubuntu/Mint
curl -L https://packages.gitlab.com/install/repositories/runner/gitlab-runner/script.deb.sh | sudo bash
# For RHEL/CentOS/Fedora
curl -L https://packages.gitlab.com/install/repositories/runner/gitlab-runner/script.rpm.sh | sudo bash
2. 安装最新版本
# For Debian/Ubuntu/Mint
sudo apt-get install gitlab-runner
# For RHEL/CentOS/Fedora
sudo yum install gitlab-runner
3. 安装指定版本
# for DEB based systems
apt-cache madison gitlab-runner
sudo apt-get install gitlab-runner=10.0.0
# for RPM based systems
yum list gitlab-runner --showduplicates | sort -r
sudo yum install gitlab-runner-10.0.0-1
4. 更新runner
# For Debian/Ubuntu/Mint
sudo apt-get update
sudo apt-get install gitlab-runner
# For RHEL/CentOS/Fedora
sudo yum update
sudo yum install gitlab-runner
4.3.3 RPM 安装
下载软件包
- 在https://gitlab-runner-downloads.s3.amazonaws.com/latest/index.html上找到最新的文件名和选项 。
- 选择一个版本并下载二进制文件,如文档所述,该文件用于下载任何其他标记的GitLab Runner发行版。
```bash
curl -LJO https://gitlab-runner-downloads.s3.amazonaws.com/latest/rpm/gitlab-runner_
.rpm
rpm -i gitlab-runner_
rpm -Uvh gitlab-runner_
> <a name="ylfZq"></a>
### 使用二进制文件
参考地址:<br />[https://mirror](https://mirror)s.tuna.tsinghua.edu.cn/gitlab-runner/yum/el7-x86_64/gitlab-runner-13.9.0-1.x86_64.rpm
```bash
# Linux x86-64
sudo curl -L --output /usr/local/bin/gitlab-runner https://gitlab-runner-downloads.s3.amazonaws.com/latest/binaries/gitlab-runner-linux-amd64
# 添加执行权限
sudo chmod +x /usr/local/bin/gitlab-runner
# 创建一个gitlab用户
sudo useradd gitlab-runner --comment 'GitLab Runner' --create-home gitlab-runner --shell /bin/bash
# 安装并作为服务运行
sudo gitlab-runner install --user=gitlab-runner --working-directory=/home/gitlab-runner
sudo gitlab-runner start
##### 更新 ######
#停止服务
sudo gitlab-runner stop
#下载新版本二进制包
sudo curl -L --output /usr/local/bin/gitlab-runner https://gitlab-runner-downloads.s3.amazonaws.com/latest/binaries/gitlab-runner-linux-amd64
#赋予执行权限
sudo chmod +x /usr/local/bin/gitlab-runner
#启动服务
sudo gitlab-runner start
4.3.4 docker 安装
docker run --rm -t -id \
-v ~/data/gitlab-runner/config:/etc/gitlab-runner \
gitlab/gitlab-runner:v12.6.0
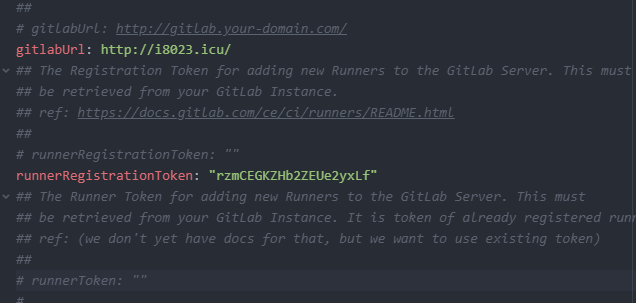
4.4 注册 runner
- 获取shared类型runner token
进入系统设置 -> Runners
- 获取group类型的runner token
进入group -> Settings -> CI/CD -> Runners -> Group Runners
- 获取specific类型的runner token
进入具体的项目 -> Settings -> CI/CD -> Runners -> Specific Runners
4.4.1 k8s 注册
4.4.2 docker 注册
# 方式1: 启动容器交互式注册
docker run --rm -it -v ~/data/gitlab-runner/config:/etc/gitlab-runner \
gitlab/gitlab-runner:v13.11.0 register
Runtime platform arch=amd64 os=linux pid=6 revision=ac8e767a version=13.11.0
Running in system-mode.
Please enter the gitlab-ci coordinator URL (e.g. https://gitlab.com/):
http://i8023.icu/
Please enter the gitlab-ci token for this runner:
rzmCEGKZHb2ZEUe2yxLf
Please enter the gitlab-ci description for this runner:
[00e4f023b5ae]: k8s-runner
Please enter the gitlab-ci tags for this runner (comma separated):
k8s-runner
Registering runner... succeeded runner=4tutaeWW
Please enter the executor: parallels, virtualbox, docker-ssh+machine, kubernetes, docker+machine, custom, docker, docker-ssh, shell, ssh:
shell
Runner registered successfully. Feel free to start it, but if it's running already the config should be automatically reloaded!
# 方式2:直接注册
docker run -itd --rm -v ~/data/gitlab-runner/config:/etc/gitlab-runner gitlab/gitlab-runner:v12.6.0 register \
--non-interactive \
--executor "shell" \
--url "http://i8023.icu/" \
--registration-token "rzmCEGKZHb2ZEUe2yxLf" \
--description "k8s-runner" \
--tag-list "k8s-runner" \
--run-untagged="true" \
--locked="false" \
--access-level="not_protected"
# 注册的选项
-c value, --config value 指定配置文件
--template-config value 指定模板配置文件
--tag-list value 指定runner的标签列表,逗号分隔
-n, --non-interactive 无交互进行runner注册
--leave-runner 如果注册失败,不用删除runner
-r value, --registration-token value runner的注册token
--run-untagged 注册运行未加标签的构建,默认当标签列表为空时值为true
--locked 锁定runner 默认true
--access-level value 设置访问等级 not_protected or ref_protected; 默认 not_protected
--maximum-timeout value 为作业设置最大运行超时时间 默认零 单位秒
--paused 设置runner为 paused,默认 'false'
--name value, --description value Runner 名称
--limit value 程序处理的最大构建数量default: "0"
--output-limit value 最大的构建大小单位kb default: "0"
--request-concurrency value 作业请求的最大并发数 default: "0"
-u value, --url value GitlabCI服务器地址
-t value, --token value GitlabCI服务器token
4.5 常用命令
### 启动命令
gitlab-runner --debug <command> #调试模式排查错误特别有用。
gitlab-runner <command> --help #获取帮助信息
gitlab-runner run # 普通用户模式 配置文件位置 ~/.gitlab-runner/config.toml
sudo gitlab-runner run # 超级用户模式 配置文件位置/etc/gitlab-runner/config.toml
### 注册命令
gitlab-runner register #默认交互模式下使用,非交互模式添加 --non-interactive
gitlab-runner list #此命令列出了保存在配置文件中的所有运行程序
gitlab-runner verify #此命令检查注册的runner是否可以连接,但不验证GitLab服务是否正在使用runner。 --delete 删除
gitlab-runner unregister #该命令使用GitLab取消已注册的runner。
#使用令牌注销
gitlab-runner unregister --url http://gitlab.example.com/ --token t0k3n
#使用名称注销(同名删除第一个)
gitlab-runner unregister --name test-runner
#注销所有
gitlab-runner unregister --all-runners
### 服务管理
gitlab-runner install --user=gitlab-runner --working-directory=/home/gitlab-runner
# --user指定将用于执行构建的用户
#`--working-directory 指定将使用**Shell** executor 运行构建时所有数据将存储在其中的根目录
gitlab-runner uninstall #该命令停止运行并从服务中卸载GitLab Runner。
gitlab-runner start #该命令启动GitLab Runner服务。
gitlab-runner stop #该命令停止GitLab Runner服务。
gitlab-runner restart #该命令将停止,然后启动GitLab Runner服务。
gitlab-runner status #此命令显示GitLab Runner服务的状态。当服务正在运行时,退出代码为零;而当服务未运行时,退出代码为非零。
https://www.yuque.com/braem/aac867/vt00s8
https://www.yuque.com/polaris-docs/knowledge/gitlab
https://www.xuliangwei.com/oldxu/803.html
https://www.cnblogs.com/sanduzxcvbnm/category/1036442.html